Ethical Tools Report
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
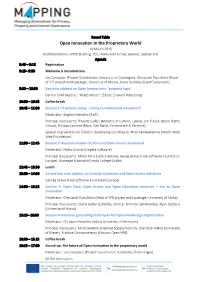
Open Innovation in the Proprietary World
Round Table Open Innovation in the Proprietary World 19 March 2015 DiploFoundation, WMO Building, 7bis, Avenue de la Paix, Geneva, Switzerland Agenda 8:45 – 9:15 Registration 9:15– 9:30 Welcome & Introductions Joe Cannataci (Project Coordinator; University of Groningen), Oleksandr Pastukhov (Head of IPR project work package; University of Malta), Jovan Kurbalija (DiploFoundation) 9:30 – 10:30 Key-note address on Open Innovation v. ‘property logic’ Darren Todd (Author, “Pirate Nation”; Editor, Evolved Publishing) 10:30 – 10:45 Coffee break 10:45 – 11:30 Session 1: IP policies today – failing to understand innovation? Moderator: Bogdan Manolea (ApTI) Principal discussants: Rihards Gulbis (Ministry of Culture, Latvia), Jim Killock (Open Rights Group), Philippe Laurent (Marx, Van Ranst, Vermeersch & Partners) Special intervention on F/OSS in developing countries by Nnenna Nwakanma (World Wide Web Foundation) 11:30 – 12:45 Session 2: Business models for the Free/Open Source movement Moderator: Pedro Gomez (Hoplite Software) Principal discussants: Mario Pena (Safe Creative), Georg Greve (Free Software Foundation Europe), Giuseppe Mazziotti (Trinity College Dublin) 12:45 – 13:30 Lunch 13:30 – 14:30 Second key-note address on Creative Commons and Open Access initiatives George Greve (Free Software Foundation Europe) 14:30 – 15:15 Session 3: Open Data, Open Access and Open Education resources – key to Open Innovation Moderator: Oleksandr Pastukhov (Head of IPR project work package; University of Malta) Principal discussants: Claire Gallon (Libertic), -

VALLATH NANDAKUMAR 3105 Eaneswood Dr, Austin, TX 78746 (512)-923-9658 (Cell); [email protected]
VALLATH NANDAKUMAR 3105 Eaneswood Dr, Austin, TX 78746 (512)-923-9658 (Cell); [email protected] EDUCATION • 1990 University of California, Berkeley, CA Ph.D. in Electrical Engineering. • 1985 University of California Berkeley, CA M.S. in Electrical Engineering. • 1982 Indian Institute of Technology, Madras, India BTech in Electrical Engineering (Electronics). EXPERIENCE • Teaching in the ECE and CS Department at the University of Texas, Austin (5 years) o C, C++, Java programming, Algorithm Design • Taught course modules at the graduate level in cell phone technology, VLSI testing, VLSI design, Internet hardware, technical writing, physics. (5 years) • Research and development activities in superconducting electronics, high-end optical communication, integrated circuit design methodologies, Computer-Aided Design tools, and cyber security software. • Published 6+ papers in IEEE journals on superconducting electronics. • Six patents granted in VLSI and superconductors. • Managed teams of 30+ people spanning multiple countries. • Have conducted computer programming contests with 400+ student participants from all over Asia coming together. EMPLOYMENT HISTORY AND EXPERIENCE Aug. 2013-Present Full-time Lecturer in the Departments of Computer Science, and Electrical and Computer Engineering, University of Texas, Austin • Courses taught: Algorithms, basic and advanced programming, Ethics of Computer Science, Writing for CS majors • Texas University Interscholastic League Director for Computer Science, 2013-2014. Mar 2012-Jun 2013 Substitute Teacher, Eanes Independent School District, Austin, TX • Substitute teacher for grades K-12 and all subjects. Mar 2012-Jun 2013 Tutor, Austin Community College, Austin, TX • Taught Algebra and Calculus, Business Economics, Statistics, Physics, English, German. Oct 2006-Jun 2013 Professor/Adjunct Professor, Amrita University, Amritapuri Campus, India (http://www.amrita.edu) • Director of Center of Excellence in Cyber Security • Taught courses in VLSI architecture, design and testing, and on Wireless systems. -

Edition No. 3 March 2019
GDPR Today Edition No. 3 March 2019 European Commission urged to investigate Romanian GDPR implementation GDPR loopholes facilitate data exploitation by political parties Uber drivers demand their data After Brexit, the EU must decide if UK data protection is adequate 2 GDPR in Numbers 6 European Commission urged to investigate Romanian GDPR implementation 8 Spain: DPA limits the use of data in political campaigning 10 Netherlands: DPA rules websites must allow people to refuse tracking cookies 12 GDPR loopholes facilitate data exploitation by political parties 14 Privacy policies for Internet of Things devices must comply with GDPR 15 Uber drivers demand their data New evidence in AdTech complaint 15 EDPB: e-Privacy and GDPR work together 16 to protect people’s data 18 German competition regulator demands changes to Facebook’s use of personal data 20 After Brexit, the EU must decide if UK data protection is adequate 22 EDPS 2018 Annual Report highlights the power and limitation of data protection 24 GDPR Tools 25 EU National Data Protection Authority Contact Details Editorial Welcome to GDPR Today – your online hub for staying Not all is positive progress. It is disappointing that the tuned to the (real) life of EU data protection law. As you European Commission has still not yet taken action to know, every two months we publish statistics showing how ensure that Romania properly implements the GDPR. the GDPR is being applied across Europe. We also share There are also several countries which have yet to relevant news, from legal guidelines and decisions to publish any GDPR data. -

Piracy Versus Privacy: an Analysis of Values Encoded in the Piratebrowser
International Journal of Communication 9(2015), 818–838 1932–8036/20150005 Piracy Versus Privacy: An Analysis of Values Encoded in the PirateBrowser BALÁZS BODÓ University of Amsterdam, Institute for Information Law The Netherlands The PirateBrowser is a Web browser that uses Tor privacy-enhancing technology to circumvent nationally implemented Internet filters blocking access to The Pirate Bay. This article analyzes the possible consequences of a mass influx of copyright pirates into the privacy domain. The article addresses the effects of the uptake of strong privacy technologies by pirates on copyright enforcement and on free speech and privacy technology domains. Also discussed are the norms and values reflected in the specific design choices taken by the developers of the PirateBrowser. Keywords: piracy, privacy, Tor, privacy-enhancing technologies, policy Introduction Tor (The Onion Router), “endorsed by Egyptian activists, WikiLeaks, NSA, GCHQ, Chelsea Manning, Snowden” (Dingledine & Appelbaum, 2013), is a volunteer network of computers that relays Web traffic through itself to provide anonymous, unobserved, and uncensored access to the Internet. It has about 4,000 relays and about 1,000 exit nodes. Tor users connect to the network, and their Web traffic is channeled through the internal relays to reach its final destination through one of the exit nodes. This arrangement makes the identification and surveillance of Tor users difficult. Anonymity is promised by the difficulty of tracing the Web traffic that appears on the exit node back to the individual who initiated the traffic, as long as there is a sufficient number of internal hops in between. Protection from surveillance is granted by the fact that each link in the communication chain is encrypted. -

Ofcom BBC DRM Consultation Response
Ofcom BBC DRM consultation response Organisational Signatories (see end for personal signatories): 1. Open Rights Group 2. Electronic Frontier Foundation 3. Consumer Focus 4. Free Software Foundation 5. Somethin' Else! 6. FriBit, Norway 7. Electronic Frontier, Norway 8. Open Source Initiative 9. Vrijschrift/Scriptum Libre 10. European Digital Rights 1. Summary Open Rights Group (ORG) was founded in 2005 by 1,000 digital activists. It has since become the UK’s leading voice defending freedom of expression, privacy, innovation, consumer rights and creativity on the net. ORG is pleased to contribute to this Ofcom consultation. ORG believes that the BBC has not made a case for adding DRM to its free-to-air broadcasts. The DRM proposed by the BBC (like all DRM systems) will not be adequate to prevent unauthorised redistribution of FTA broadcasts. Further, the existence of other, DRM-free versions of the same content (such as US FTA broadcasts) means that would-be redistributors can dispense with the bother of breaking the BBC's DRM and redistribute copies of the content that have originated from other sources, making the case for DRM even less sensible. However, this DRM failure will not have a material effect on the UK DTT rollout. The threats of unspecified copyright holders to boycott DTT without DRM are simply not credible; they are a re-hash of threats made over US broadcasts seven years ago, threats that rightsholders have not carried out. Furthermore, if access to the unspecified imperilled content is critical to DTT rollout, then this measure is inadequate to ensure that it will be present on DTT if the BBC gets its way, as the BBC has not produced any promises from rightsholders to the effect that they will license to DTT once DRM is in place. -

Civil Society Statement to the E-G8 and G8 the Signatories of This
Civil Society Statement to the e-G8 and G8 The signatories of this statement are representatives of civil society from around the world working towards the promotion of Internet freedom, digital rights, and open communication. We understand that the French Presidency of the G8 is holding a G8 internet meeting -- the "e- G8 Forum" -- immediately before the G8 Summit in Deauville, with a view to shaping the agenda of the G8 Summit regarding key global internet policy issues. This meeting is significant in that this is the first year that the internet’s role in society and the economy is explicitly on the G8 agenda. As key world leaders, your policies have a major influence on internet policy globally. Regrettably, certain policies being implemented in the most developed economies are undermining the open and neutral internet -- the very qualities that represent the essence of its democratic and economic potential. We believe that G8 Member States should use the e-G8 meeting as an opportunity to publicly commit to expanding internet access for all, combating digital censorship and surveillance, limiting online intermediary liability, and upholding principles of net neutrality. Internet Access for All We are particularly concerned about the increasing trend of nations cutting off citizens’ access to the Internet and mobile networks in times of crisis, as Egypt, Libya, Iran, China, Nepal, and Burma have all done. In many if not all of these countries, we see how important access to the Internet is as a gateway to a plethora of others civil, political, and fundamental human rights. Many G8 countries are actively pursuing policies that would similarly seek to restrict and control access; these policies legitimize actions of repressive regimes and threaten the core of the internet economy. -

— Samizdat. Between Practices and Representations Lecture Series at Open Society Archives, Budapest
— Samizdat. Between Practices and Representations Lecture Series at Open Society Archives, Budapest, No February-June . Publications IAS — Samizdat. Between Practices and Representations Lecture Series at Open Society Archives, Budapest, February-June 2013. edited by valentina parisi — Co-sponsored by the Central European University Institute for Advanced Study and eurias — Colophon Parisi, Valentina (ed.) Samizdat. Between Practices and Representations Lecture Series at Open Society Archives, Budapest, February-June 2013. ias Publications No 1 © Central European University, Institute for Advanced Study 2015 Includes bibliographical references and index. isbn 978-615-5547-00-3 First published: February 2015 Proofreading: Christopher Ryan Graphic design: Ákos Polgárdi Typefaces: Adobe Jenson & Arquitecta — Contents Acknowledgements p. 005 Preface p. 007 The common pathways of samizdat and piracy p. 019 Balázs Bodó “Music on ribs”. Samizdat as a medium p. 035 Tomáš Glanc The media dimension of samizdat. p. 047 The Präprintium exhibition project Sabine Hänsgen The dispersed author. The problem of literary authority p. 063 in samizdat textual production Valentina Parisi Movement, enterprise, network. The political economy p. 073 of the Polish underground press Piotr Wciślik Samizdat as social practice and communication circuit p. 087 Olga Zaslavskaya Authors p. 101 Index of names p. 105 — 3 — 4 — Acknowledgements This volume brings together the texts of all the lectures delivered at the Open Society Archives (OSA) in Budapest in the -

The Public Domain: Enclosing the Commons of the Mind
37278_u00.qxd 8/28/08 11:04 AM Page i The Public Domain ___-1 ___0 ___ 1 37278_u00.qxd 8/28/08 11:04 AM Page ii Thomas Jefferson to Isaac McPherson, August 13, 1813, p. 6. -1 ___ 0 ___ 1 ___ 37278_u00.qxd 8/28/08 11:04 AM Page iii James Boyle The Public Domain Enclosing the Commons of the Mind Yale University Press ___-1 New Haven & London ___0 ___ 1 37278_u00.qxd 8/28/08 11:04 AM Page iv A Caravan book. For more information, visit www.caravanbooks.org. Copyright © 2008 by James Boyle. All rights reserved. The author has made an online version of this work available under a Creative Commons Attribution-Noncommercial-Share Alike 3.0 License. It can be accessed through the author’s website at http://james-boyle.com. Printed in the United States of America. ISBN: 978-0-300-13740-8 Library of Congress Control Number: 2008932282 A catalogue record for this book is available from the British Library. This paper meets the requirements of ANSI/NISO Z39.48–1992 (Permanence of Paper). It contains 30 percent postconsumer waste (PCW) and is certified by the Forest Stewardship Council (FSC) -1 ___ 0 ___ 1 ___ 37278_u00.qxd 8/28/08 11:04 AM Page v Contents Acknowledgments, vii Preface: Comprised of at Least Jelly?, xi 1 Why Intellectual Property?, 1 2 Thomas Jefferson Writes a Letter, 17 3 The Second Enclosure Movement, 42 4 The Internet Threat, 54 5 The Farmers’ Tale: An Allegory, 83 6 I Got a Mashup, 122 7 The Enclosure of Science and Technology: Two Case Studies, 160 8 A Creative Commons, 179 9 An Evidence-Free Zone, 205 10 An Environmentalism for Information, 230 ___-1 Notes and Further Readings, 249 ___0 Index, 297 ___ 1 v 37278_u00.qxd 8/28/08 11:04 AM Page vi -1 ___ 0 ___ 1 ___ 37278_u00.qxd 8/28/08 11:04 AM Page vii Acknowledgments The ideas for this book come from the theoretical and practical work I have been doing for the last ten years. -

Open Data and Privacy Workshop Reader
ODP primer reader Open Data and Privacy Workshop reader Table of Contents Introduction ..................................................................................................................................... 2 Regulatory frameworks ................................................................................................................ 3 Licensing ..................................................................................................................................................... 3 Freedom of Information (FOI) ............................................................................................................. 4 Europe .......................................................................................................................................................... 4 EU Data Protection .................................................................................................................................................. 5 EU PSI directive ........................................................................................................................................................ 6 PECR .............................................................................................................................................................................. 6 US privacy laws ......................................................................................................................................... 7 Market self-regulation .......................................................................................................................... -

Being Digital Citizens, Second Edition OPEN ACCESS PDF from Rowman
Being Digital Citizens, Second Edition OPEN ACCESS PDF from Rowman & Littlefield Being Digital Citizens, Second Edition OPEN ACCESS PDF from Rowman & Littlefield Being Digital Citizens, Second Edition OPEN ACCESS PDF from Rowman & Littlefield Being Digital Citizens Being Digital Citizens, Second Edition OPEN ACCESS PDF from Rowman & Littlefield Being Digital Citizens, Second Edition OPEN ACCESS PDF from Rowman & Littlefield Being Digital Citizens Second Edition Engin Isin and Evelyn Ruppert London • New York Being Digital Citizens, Second Edition OPEN ACCESS PDF from Rowman & Littlefield Published by Rowman & Littlefield International, Ltd. 6 Tinworth Street, London SE11 5AL, United Kingdom www.rowmaninternational.com Rowman & Littlefield International, Ltd. is an affiliate of Rowman & Littlefield 4501 Forbes Boulevard, Suite 200, Lanham, Maryland 20706, USA With additional offices in Boulder, New York, Toronto (Canada), and London (UK) www.rowman.com Copyright © 2020 by Engin Isin and Evelyn Ruppert All rights reserved. No part of this book may be reproduced in any form or by any electronic or mechanical means, including information storage and retrieval systems, without written permission from the publisher, except by a reviewer who may quote passages in a review. British Library Cataloguing in Publication Information A catalogue record for this book is available from the British Library ISBN: HB 978-1-78661-447-6 ISBN: PB 978-1-78661-448-3 Library of Congress Cataloging-in-Publication Data Names: Isin, Engin F. (Engin Fahri), 1959- | Ruppert, Evelyn Sharon, 1959- author. Title: Being digital citizens / Engin Isin and Evelyn Ruppert. Description: Second edition. | London ; New York : Rowman & Littlefield, [2020] | Includes biblio- graphical references and index. -

Patent-Based Open Science
Maine Law Review Volume 59 Number 2 Symposium: Closing in on Open Science: Article 6 Trends in Intellectual Property & Scientific Research June 2007 Road Map to Revolution? Patent-Based Open Science Lee Petherbridge Follow this and additional works at: https://digitalcommons.mainelaw.maine.edu/mlr Part of the Intellectual Property Law Commons, and the Science and Technology Law Commons Recommended Citation Lee Petherbridge, Road Map to Revolution? Patent-Based Open Science, 59 Me. L. Rev. 339 (2007). Available at: https://digitalcommons.mainelaw.maine.edu/mlr/vol59/iss2/6 This Article is brought to you for free and open access by the Journals at University of Maine School of Law Digital Commons. It has been accepted for inclusion in Maine Law Review by an authorized editor of University of Maine School of Law Digital Commons. For more information, please contact [email protected]. ROAD MAP TO REVOLUTION? PATENT-BASED OPEN SCIENCE Lee Petherbridge, Ph.D I. INTRODUCTION II. A TOPOGRAPHY OF INNOVATION AND LAW IN THE LIFE SCIENCES A. The Industrial Infrastructure: Integrating Public and Private Science B. The Legal Infrastructure: A Proprietary Approach I. The Innovation Suppressive Cost of Monopoly 2. Additional Innovation Suppressive Costs III. A THEORY OF OPEN LIFE SCIENCE A. Open Science B. To Open Science from Open Source I. Addressing Fixed Costs 2. Peer Worker Potential 3. Issues of Modularity and Granularity 4. Subsequent (Mis)appropriation IV. TOWARD A PATENT-BASED OPEN SCIENCE FRAMEWORK A. Establishing a Patent Servitude B. Patent Servitudes in Operation C. Additional Considerations V. CONCLUDING REMARKS HeinOnline -- 59 Me. L. Rev. 339 2007 340 MAINE LAW REVIEW [Vol. -

Open Data Study New Technologies
Open data study New technologies Becky Hogge For more information contact: Transparency & Accountability Initiative c/o Open Society Foundation 4th floor, Cambridge House 100 Cambridge Grove London, W6 0LE, UK Tel: +44 (0)20 7031 0200 www.transparency-initiative.org Copyright 2010. Creative Commons License. This work is licensed under a Creative Commons Attribution 3.0 Licence: http://creativecommons.org/licenses/by/3.0/us/ TAI New Technology /Open data study 3 Contents Introduction 4 The UK – data.gov.uk 5 The US – data.gov 7 The three-tiered approach 9 Civil Society 10 The push from the middle 12 Top-level drive 15 Utility not Users – the absent driver? 17 International perspectives 18 The relationship between FOI and Open Data 19 Questions over impact 21 Data characteristics 21 The three-tiered approach: top level drivers 25 The three-tiered approach: the middle layer 27 The three-tiered approach: civil society 29 Donors: a fourth tier? 30 Issues for developing and middle income country users 32 Complementary strategies for open data 33 An aside: advice for funders 34 Avenues for further research 35 An open data strategy checklist 36 Status of FOI 37 Current data collection activities 37 Potential end-users 37 Tier 1: Civil society 37 Tier 2: The middle layer 37 Tier 3: The top-level 38 Tier 4: Donor drivers 38 Conclusion 39 Annexes 41 Annexes I: Methodology 42 Annexes II: List of interviewees 43 Bibliography 44 Acknowledgements 45 About the author 45 4 TAI New Technology /Open data study Introduction There are substantial social and economic gains to be made from opening government data to the public.