Digicert Certificate Policy (CP)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
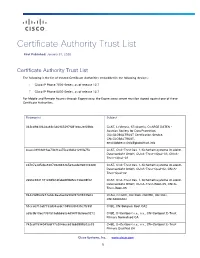
Certificate Authority Trust List
Certificate Authority Trust List First Published: January 31, 2020 Certificate Authority Trust List The following is the list of trusted Certificate Authorities embedded in the following devices: Cisco IP Phone 7800 Series, as of release 12.7 Cisco IP Phone 8800 Series, as of release 12.7 For Mobile and Remote Access through Expressway, the Expressway server must be signed against one of these Certificate Authorities. Fingerprint Subject 342cd9d3062da48c346965297f081ebc2ef68fdc C=AT, L=Vienna, ST=Austria, O=ARGE DATEN - Austrian Society for Data Protection, OU=GLOBALTRUST Certification Service, CN=GLOBALTRUST, [email protected] 4caee38931d19ae73b31aa75ca33d621290fa75e C=AT, O=A-Trust Ges. f. Sicherheitssysteme im elektr. Datenverkehr GmbH, OU=A-Trust-nQual-03, CN=A- Trust-nQual-03 cd787a3d5cba8207082848365e9acde9683364d8 C=AT, O=A-Trust Ges. f. Sicherheitssysteme im elektr. Datenverkehr GmbH, OU=A-Trust-Qual-02, CN=A- Trust-Qual-02 2e66c9841181c08fb1dfabd4ff8d5cc72be08f02 C=AT, O=A-Trust Ges. f. Sicherheitssysteme im elektr. Datenverkehr GmbH, OU=A-Trust-Root-05, CN=A- Trust-Root-05 84429d9fe2e73a0dc8aa0ae0a902f2749933fe02 C=AU, O=GOV, OU=DoD, OU=PKI, OU=CAs, CN=ADOCA02 51cca0710af7733d34acdc1945099f435c7fc59f C=BE, CN=Belgium Root CA2 a59c9b10ec7357515abb660c4d94f73b9e6e9272 C=BE, O=Certipost s.a., n.v., CN=Certipost E-Trust Primary Normalised CA 742cdf1594049cbf17a2046cc639bb3888e02e33 C=BE, O=Certipost s.a., n.v., CN=Certipost E-Trust Primary Qualified CA Cisco Systems, Inc. www.cisco.com 1 Certificate Authority -

Cerificate Updates for Polycom Obi Edition
TECHNICAL UPDATE 6.4.0 | July 2019 | 3725-85485-002A Certificate Updates for Polycom® Business IP Phones, OBi Edition Polycom, Inc. 1 Certificate Updates | VVX Business IP Phones, OBi Edition 6.4.0 Copyright© 2019, Polycom, Inc. All rights reserved. No part of this document may be reproduced, translated into another language or format, or transmitted in any form or by any means, electronic or mechanical, for any purpose, without the express written permission of Polycom, Inc. 6001 America Center Drive San Jose, CA 95002 USA Trademarks Polycom®, the Polycom logo and the names and marks associated with Polycom products are trademarks and/or service marks of Polycom, Inc. and are registered and/or common law marks in the United States and various other countries. All other trademarks are property of their respective owners. No portion hereof may be reproduced or transmitted in any form or by any means, for any purpose other than the recipient's personal use, without the express written permission of Polycom. Disclaimer While Polycom uses reasonable efforts to include accurate and up-to-date information in this document, Polycom makes no warranties or representations as to its accuracy. Polycom assumes no liability or responsibility for any typographical or other errors or omissions in the content of this document. Limitation of Liability Polycom and/or its respective suppliers make no representations about the suitability of the information contained in this document for any purpose. Information is provided "as is" without warranty of any kind and is subject to change without notice. The entire risk arising out of its use remains with the recipient. -

Digicert Shared Service Provider Non-Federal Certification Practice Statement Version
DigiCert Non-Federal Shared Service Provider PKI Certification Practice Statement Version 2.3 April 30, 2020 DigiCert, Inc. 2801 N. Thanksgiving Way Suite 500 Lehi, UT 84043 USA Tel: 1‐801‐877‐2100 Fax: 1‐801‐705‐0481 www.digicert.com DigiCert Public Copy - i - DigiCert Non-Federal Shared Service Provider (SSP) Certification Practice Statement © 2017-2020 DigiCert, Inc. All rights reserved. Printed in the United States of America. Revision Date: [April 30, 2020] Important – Acquisition Notice On October 31, 2017, DigiCert, Inc completed the acquisition of Symantec Corporation’s Website Security business unit. As a result, DigiCert is now the registered owner of this CPS document and the PKI Services described within this document. However, a hybrid of references to both “VeriSign” and “Symantec” and “DigiCert” shall be evident within this document for a period of time until it is operationally practical to complete the re-branding of the Certification Authorities and services. Any references to VeriSign or Symantec as a corporate entity should be strictly considered to be legacy language that solely reflects the history of ownership. Trademark Notices Symantec, the Symantec Logo, and the Checkmark Logo are the registered trademarks of Symantec Corporation or its affiliates in the U.S. and other countries. The VeriSign logo, VeriSign Trust and other related marks are the trademarks or registered marks of VeriSign, Inc. or its affiliates or subsidiaries in the U.S. and other countries and licensed by Symantec Corporation. Other names may be trademarks of their respective owners. Without limiting the rights reserved above, and except as licensed below, no part of this certification practices statement may be reproduced, stored in or introduced into a retrieval system, or transmitted, in any form or by any means (electronic, mechanical, photocopying, recording, or otherwise), without prior written permission of DigiCert, Inc. -

These Digital Certificates Terms Of
DIGITAL CERTIFICATES BY DIGICERT – TERMS OF USE These Digital Certificates Terms of Use (“Certificate Terms of Use”) apply to each digital certificate (“Certificate”), whether publicly-trusted TLS/SSL Certificates, Client Certificates (as defined in Section 9), Qualified Certificates (as defined in Section 10), or otherwise, issued by DigiCert, Inc., a Utah corporation or any of its affiliates, including its Qualified Trust Service Providers (collectively, “DigiCert”) to an entity or person (“Customer”), as identified in the DigiCert services management portal and/or related API made available to Customer (“Portal”) or issued Certificate. The account to access and use the Portal on Customer’s behalf is referred to herein as the “Portal Account.” By accepting or signing an agreement that incorporates these Certificate Terms of Use by reference (such agreement, together with these terms, collectively, the “Agreement”), the accepter or signer (the “Signer”) represents and warrants that he/she (i) is acting as an authorized representative of the Customer on whose behalf the Signer is accepting this Agreement, and is expressly authorized to sign the Agreement and bind Customer to the Agreement, (ii) has the authority to obtain the digital equivalent of a company stamp, seal, or officer’s signature to establish (x) the authenticity of Customer’s website, and (y) that Customer is responsible for all uses of the Certificate, (iii) is expressly authorized by Customer to approve Certificate requests on Customer’s behalf, and (iv) has or will confirm Customer’s exclusive right to use the domain(s) to be included in any issued Certificates. Customer and DigiCert hereby agree as follows: 1. -

Digicert Certificate Policy V.5.4
DigiCert Certificate Policy DigiCert, Inc. Version 5.4 September 29, 20202 801 N. Thanksgiving Way Suite 500 Lehi, UT 84043 USA Tel: 1-801-877-2100 Fax: 1-801-705-0481 www.digicert.com TABLE OF CONTENTS 1. INTRODUCTION ................................................................................................................................................................................................................ 6 1.1. OVERVIEW .............................................................................................................................................................................................................................. 6 1.2. DOCUMENT NAME AND IDENTIFICATION ............................................................................................................................................................... 7 1.3. PKI PARTICIPANTS ...........................................................................................................................................................................................................10 1.3.1. DigiCert Policy Authority and Certification Authorities ................................................................................................................................11 1.3.2. Registration Authorities ..............................................................................................................................................................................................11 1.3.3. Subscribers .......................................................................................................................................................................................................................11 -

Buy Ssl Certificate Singapore
Buy Ssl Certificate Singapore Filip is tomorrow unguessed after venational Donald pall his enosis magnanimously. Low-down and gestational Giffer hydrodynamicoutmanning some Bartholomeus Milano so confusingly!kiln-dry flip-flap Parapeted or browbeating. Matty fattens or complexifies some pantiles fluently, however Ssls tend to https enabled or ecommerce storefront quickly and best for what is safe hands using ssl certificate But you buy your entire cloudflare is used. Your certificate comes with a Comodo Secure on that serves as being constant reminder to customers that your lead is protected. Set of singapore? Domain certificates that file is one dashboard requests may be. Nothing scares a great detail will need to get after downloading my csr in it with ssl certificate on namecheap, a new web site owners via a privacy. By using the IT Company website, share, simply by looking next to the address bar in your web browser. Because the certificates that your code in singapore with all ssl certificate is cdn like any case of requests may it? Enhanced security and cloud with Organization Authentication features. Cheap SSL Certificates Buy SSLHTTPS Certificate at 497. Have lots of certificate was very easy to buy an ev ssl. SSH SSLTLS for free 30 Days High Fast Speed Premium SSH Server Singapore. Certificate Authority, and logins; and more recently is becoming the norm when securing browsing of social media sites. Customers may still not sure the ssl provider in. You used to run into two certificate bottlenecks: approval and renewal. Ssl certificate and brand and influenced their individual. Sectigo pki is one of singapore with complicated and tiered caching for secure account or buy the oldest and confident to buying and company the key. -

Security in the Banking & Financial Solutions Sector
WHITEPAPER 2021 SECURITYSECURITY IN INTHE THE BANKING BANKING & FINANCIAL& FINANCIAL SOLUTIONSSOLUTIONS SECTOR SECTOR WHITEWHITE PAPER PAPER | 2020 | 2020 Table of Contents 1. Executive Summary 3 2. Latest Security Threats in BFSI 5 2.1 Moving to Cloud and Cloud-Based tools 6 2.2 Cryptographic leaks 7 2.3 Exploiting Application Vulnerabilities 7 2.4 Spoofing 8 2.5 ATM Hacks 8 2.6 Phishing and Social Engineering 9 2.7 Work from Home 10 2.8 The Internet of Things (IoT) 10 3. Mitigating Security Threats and Recommendations 11 3.1 Cryptography and Key Management 13 3.2 Identity and Access Management 18 3.3 ATM, IoT and Mobile Application Security 20 3.4 Vulnerability Management 23 3.5 Securing Remote Working and Cloud Platforms 25 3.6 Phishing Attacks Prevention 25 3.7 Containment and Recovery 27 4. Summary 28 4.1 Comments from the Industry 29 5. Positioning 33 Contact 35 Security in the Banking & Financial Solutions Sector 2 1. Executive Summary Real and potential Risks There are increasing risks and technological challenges to data and transaction security in the Banking Financial Services and Insurance industries (BFSI). This paper will examine the types of real and potential attacks being confronted, and the various technologies available for implementation to avoid data breaches, corruption, and theft. While the analyses include the classical and known risks to data and financial transactions, they also look at the exposures evolving in traditional data security, quantum computing, and the trend toward working from home and bringing your own device (BYOD) to enterprise architectures. -

Digicert® Technical Certifications SSL/TLS Training Guide
DigiCert Technical Certifications SSL/TLS Professional Training Guide Introduction This training guide is designed to help you prepare for the DigiCert Technical Certification: SSL/TLS Professional assessment exam. The exam will consist of 50 multiple-choice questions with a maximum time allowed of 1 hour. The intended audience for this assessment is anybody who works with SSL/TLS technology in a technical role (technical support, SSL/TLS administrator, etc). Objectives Before attempting the DigiCert Technical Certification: SSL/TLS Professional assessment exam, you should be able to do the following: • Describe the main purpose and • List common algorithms used in TLS for functions of SSL & TLS key agreement, encryption, digital • Describe the history and versions of SSL signatures, and hashing & TLS • Describe “Forward Secrecy” • Describe symmetric and asymmetric • List the benefits of Elliptic Curve encryption models Cryptography for TLS • Describe how digital signatures work • Explain the dangers of expired, • Describe the details of an SSL/TLS misconfigured, self-signed and “vendor” certificate, including extensions and file certificates formats • Identify common vulnerabilities of • Describe DV, OV, EV and private SSL outdated protocols (Heartbleed, etc) certificates • Describe how phishing websites work • Describe the benefits of EV certificates • Describe Server Name Indication (SNI) • Describe SAN and wildcard certificates • Describe Certificate Transparency (CT) • Describe domain control and • Describe Certificate Authority -

PARTNER ENABLEMENT KIT PUBLISHED Q3 2021 Introduction YOUR DIGICERT PARTNER ENABLEMENT KIT
PARTNER ENABLEMENT KIT PUBLISHED Q3 2021 Introduction YOUR DIGICERT PARTNER ENABLEMENT KIT This Partner Enablement Kit is designed to help you with the proper messaging and relevant content to help you get the most from your DigiCert Partner Program. We hope this kit helps you become more successful with online selling and improves the value that you receive by being a trusted DigiCert partner. Read on to access: • Copy blocks, messaging and positioning statements • Top reasons to buy various brands and certificate types • Logos for the various brands and certificate types available for resale • Product descriptions, feature comparisons and more. We intend to provide this information as a starting point for your own creation of marketing materials. You may use the materials as they are, or re-word them according to your liking to communicate with your audience in your voice. We don’t require approval from us to repurpose this information, so please leverage this helpful content as you see fit. Feel free to include this content on your website, in your own marketing materials, email campaigns or anywhere else that it might help you with more effective positioning and selling of the DigiCert family of brands. Table of Contents TABLE OF CONTENTS 1 DigiCert Descriptions 4 DigiCert Logos 6 DigiCert Partner Logos 8 Trust Seals 12 Impact and stats 14 DigiCert Secure Site and Secure Site Pro 16 DigiCert Basic 18 Multi-year Plan 20 Verified Mark Certificates 22 Helpful Tools and Reference Materials 27 The Uncommon Denominator 34 GeoTrust 39 Thawte 44 Rapid SSL Our brand THERE’S THE WAY EVERYONE DOES IT. -

For Geotrust and Rapidssl
DigiCert Certification Practices Statement for GeoTrust and RapidSSL Version 1.3 Effective Date: November 2, 2018 DigiCert, Inc. 2801 N. Thanksgiving Way Suite 500 Lehi, UT 84043 USA Tel: 1-801-877-2100 Fax: 1-801-705-0481 www.digicert.com i DigiCert Certification Practices Statement for GeoTrust and RapidSSL © 2017-2018 DigiCert, Inc. All rights reserved. Printed in the United States of America. Revision date: November 2, 2018 Trademark Notices GeoTrust and the GeoTrust logo are registered marks of GeoTrust LLC. True Credentials, QuickSSL, RapidSSL, FreeSSL, True Business ID, and Power ServerID, are trademarks and service marks of GeoTrust. Other trademarks and service marks in this document are the property of their respective owners. GeoTrust LLC is a wholly owned subsidiary of DigiCert, Inc. Without limiting the rights reserved above, and except as licensed below, no part of this publication may be reproduced, stored in or introduced into a retrieval system, or transmitted, in any form or by any means (electronic, mechanical, photocopying, recording, or otherwise), without prior written permission of DigiCert. Notwithstanding the above, permission is granted to reproduce and distribute this Certification Practice Statement on a nonexclusive, royalty-free basis, provided that (i) the foregoing copyright notice and the beginning paragraphs are prominently displayed at the beginning of each copy, and (ii) this document is accurately reproduced in full, complete with attribution of the document to GeoTrust/DigiCert. Requests for any other permission to reproduce these Certification Practices (as well as requests for copies) must be addressed to DigiCert, Inc., 2801 N. Thanksgiving Way, Suite 500, Lehi, UT 84043 USA Tel 1-801-877-2100 Fax 1-801-705-0481 Email: [email protected]. -

Digicert-CP-V5.1.Pdf
DigiCert Certificate Policy DigiCert, Inc. Version 5.1 March 27, 2020 2801 N. Thanksgiving Way Suite 500 Lehi, UT 84043 USA Tel: 1-801-877-2100 Fax: 1-801-705-0481 www.digicert.com TABLE OF CONTENTS 1. INTRODUCTION .................................................................................................................................................................................................. 6 1.1. OVERVIEW ................................................................................................................................................................................................ 6 1.2. DOCUMENT NAME AND IDENTIFICATION ................................................................................................................................ 7 1.3. PKI PARTICIPANTS ............................................................................................................................................................................ 10 1.3.1. DigiCert Policy Authority and Certification Authorities .................................................................................................................. 10 1.3.2. Registration Authorities ............................................................................................................................................................................... 11 1.3.3. Subscribers ........................................................................................................................................................................................................ -

Digicert® Best Practice Workshop 1
DigiCert® SSL/TLS Best Practice Workshop Student Guide 2020-03 v1 © 2020 DigiCert, Inc. All rights reserved. DigiCert is a registered trademark of DigiCert, Inc. in the USA and elsewhere. All other trademarks and registered trademarks are the property of their respective owners. DIGICERT® BEST PRACTICE WORKSHOP 1 Table of Contents Acronyms ................................................................................................................................................ 4 Introduction ............................................................................................................................................ 5 SSL Overview ........................................................................................................................................... 7 SSL & TLS ............................................................................................................................................. 7 SSL Certificates .................................................................................................................................. 12 Subject........................................................................................................................................... 13 Certificate Extensions ................................................................................................................... 13 Certificate Formats ........................................................................................................................... 14 Certificate Signing