A Survey on Computational Propaganda Detection
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Evocative and Persuasive Power of Loaded Words in the Political Discourse on Drug Reform
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by OpenEdition Lexis Journal in English Lexicology 13 | 2019 Lexicon, Sensations, Perceptions and Emotions Conjuring up terror and tears: the evocative and persuasive power of loaded words in the political discourse on drug reform Sarah Bourse Electronic version URL: http://journals.openedition.org/lexis/3182 DOI: 10.4000/lexis.3182 ISSN: 1951-6215 Publisher Université Jean Moulin - Lyon 3 Electronic reference Sarah Bourse, « Conjuring up terror and tears: the evocative and persuasive power of loaded words in the political discourse on drug reform », Lexis [Online], 13 | 2019, Online since 14 March 2019, connection on 20 April 2019. URL : http://journals.openedition.org/lexis/3182 ; DOI : 10.4000/ lexis.3182 This text was automatically generated on 20 April 2019. Lexis is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License. Conjuring up terror and tears: the evocative and persuasive power of loaded w... 1 Conjuring up terror and tears: the evocative and persuasive power of loaded words in the political discourse on drug reform Sarah Bourse Introduction 1 In the last few years, the use of the adjective “post-truth” has been emerging in the media to describe the political scene. This concept has gained momentum in the midst of fake allegations during the Brexit vote and the 2016 American presidential election, so much so that The Oxford Dictionary elected it word of the year in 2016. Formerly referring to the lies at the core of political scandals1, the term “post-truth” now describes a situation where the objective facts have far less importance and impact than appeals to emotion and personal belief in order to influence public opinion2. -
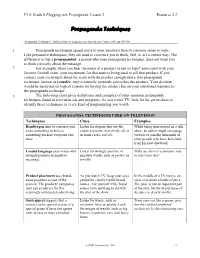
Lesson 2-Resource 2.2 Propaganda Techniques
ELA Grade 6 Plugging into Propaganda, Lesson 2 Resource 2.2 Propaganda Techniques “Propaganda Techniques,” Holt Literature & Language Arts, Introductory Course, 2003, pp. 643-645 1 Propaganda techniques appeal more to your emotions than to common sense or logic. Like persuasive techniques, they are used to convince you to think, feel, or act a certain way. The difference is that a propagandist, a person who uses propaganda techniques, does not want you to think critically about the message. 2 For example, when you hear the name of a product or see its logo* associated with your favorite football team, your excitement for that team is being used to sell that product. If you connect your excitement about the team with the product enough times, this propaganda technique, known as transfer, may eventually persuade you to buy the product. Your decision would be based not on logical reasons for buying the product but on your emotional response to the propaganda technique. 3 The following chart gives definitions and examples of other common propaganda techniques found in television ads and programs. As you watch TV, look for the given clues to identify these techniques in every kind of programming you watch. PROPAGANDA TECHNIQUES USED ON TELEVISION Techniques Clues Examples Bandwagon tries to convince you Listen for slogans that use the While being interviewed on a talk to do something or believe words everyone, everybody, all, or show, an author might encourage something because everyone else in some cases, nobody. viewers to join the thousands of does. other people who have benefited from his new diet book. -

Freedom on the Net 2016
FREEDOM ON THE NET 2016 China 2015 2016 Population: 1.371 billion Not Not Internet Freedom Status Internet Penetration 2015 (ITU): 50 percent Free Free Social Media/ICT Apps Blocked: Yes Obstacles to Access (0-25) 18 18 Political/Social Content Blocked: Yes Limits on Content (0-35) 30 30 Bloggers/ICT Users Arrested: Yes Violations of User Rights (0-40) 40 40 TOTAL* (0-100) 88 88 Press Freedom 2016 Status: Not Free * 0=most free, 100=least free Key Developments: June 2015 – May 2016 • A draft cybersecurity law could step up requirements for internet companies to store data in China, censor information, and shut down services for security reasons, under the aus- pices of the Cyberspace Administration of China (see Legal Environment). • An antiterrorism law passed in December 2015 requires technology companies to cooperate with authorities to decrypt data, and introduced content restrictions that could suppress legitimate speech (see Content Removal and Surveillance, Privacy, and Anonymity). • A criminal law amendment effective since November 2015 introduced penalties of up to seven years in prison for posting misinformation on social media (see Legal Environment). • Real-name registration requirements were tightened for internet users, with unregistered mobile phone accounts closed in September 2015, and app providers instructed to regis- ter and store user data in 2016 (see Surveillance, Privacy, and Anonymity). • Websites operated by the South China Morning Post, The Economist and Time magazine were among those newly blocked for reporting perceived as critical of President Xi Jin- ping (see Blocking and Filtering). www.freedomonthenet.org FREEDOM CHINA ON THE NET 2016 Introduction China was the world’s worst abuser of internet freedom in the 2016 Freedom on the Net survey for the second consecutive year. -

Fake News Detection for the Russian Language
Fake news detection for the Russian language Gleb Kuzmin∗ Daniil Larionov∗ Moscow Institute of Physics and Technology Federal Research Center / Dolgoprudny, Russia ”Computer Science and Control” [email protected] / Moscow, Russia [email protected] Dina Pisarevskaya∗ Ivan Smirnov Federal Research Center Federal Research Center ”Computer Science and Control” ”Computer Science and Control” / Moscow, Russia / Moscow, Russia [email protected] [email protected] Abstract In this paper, we trained and compared different models for fake news detection in Russian. For this task, we used such language features as bag-of-n-grams and bag of Rhetorical Structure Theory features, and BERT embeddings. We also compared the score of our models with the human score on this task and showed that our models deal with fake news detection better. We investigated the nature of fake news by dividing it into two non-overlapping classes: satire and fake news. As a result, we obtained the set of models for fake news detection; the best of these models achieved 0.889 F1-score on the test set for 2 classes and 0.9076 F1-score on 3 classes task. 1 Introduction Fake news detection becomes a more significant task. It is connected with an increasing number of news in media and social media. To prevent rumors and misinformation from spreading in this news, we need to have a system able to detect fake news. It also could be useful because it’s hard for people to recognize fake news. Approaches to this task are being developed for English. However, fake news texts can be written originally in different ’source’ languages, i.e. -

Neural Architectures for Fine-Grained Propaganda Detection in News
Neural Architectures for Fine-Grained Propaganda Detection in News Pankaj Gupta1,2, Khushbu Saxena1, Usama Yaseen1,2, Thomas Runkler1, Hinrich Schutze¨ 2 1Corporate Technology, Machine-Intelligence (MIC-DE), Siemens AG Munich, Germany 2CIS, University of Munich (LMU) Munich, Germany [email protected] | [email protected] Abstract techniques in news articles at sentence and frag- ment level, respectively and thus, promotes ex- This paper describes our system (MIC-CIS) plainable AI. For instance, the following text is a details and results of participation in the propaganda of type ‘slogan’. fine-grained propaganda detection shared task Trump tweeted: ‘`BUILD THE WALL!" 2019. To address the tasks of sentence (SLC) | {z } and fragment level (FLC) propaganda detec- slogan tion, we explore different neural architectures Shared Task: This work addresses the two (e.g., CNN, LSTM-CRF and BERT) and ex- tasks in propaganda detection (Da San Mar- tract linguistic (e.g., part-of-speech, named en- tino et al., 2019) of different granularities: (1) tity, readability, sentiment, emotion, etc.), lay- Sentence-level Classification (SLC), a binary clas- out and topical features. Specifically, we have sification that predicts whether a sentence con- designed multi-granularity and multi-tasking tains at least one propaganda technique, and (2) neural architectures to jointly perform both the Fragment-level Classification (FLC), a token-level sentence and fragment level propaganda de- (multi-label) classification that identifies both the tection. Additionally, we investigate different ensemble schemes such as majority-voting, spans and the type of propaganda technique(s). relax-voting, etc. to boost overall system per- Contributions: (1) To address SLC, we de- formance. -

Media Bias, the Social Sciences, and NLP: Automating Frame Analyses to Identify Bias by Word Choice and Labeling
Media Bias, the Social Sciences, and NLP: Automating Frame Analyses to Identify Bias by Word Choice and Labeling Felix Hamborg Dept. of Computer and Information Science University of Konstanz, Germany [email protected] Abstract Even subtle changes in the words used in a news text can strongly impact readers’ opinions (Pa- Media bias can strongly impact the public per- pacharissi and de Fatima Oliveira, 2008; Price et al., ception of topics reported in the news. A dif- 2005; Rugg, 1941; Schuldt et al., 2011). When re- ficult to detect, yet powerful form of slanted news coverage is called bias by word choice ferring to a semantic concept, such as a politician and labeling (WCL). WCL bias can occur, for or other named entities (NEs), authors can label example, when journalists refer to the same the concept, e.g., “illegal aliens,” and choose from semantic concept by using different terms various words to refer to it, e.g., “immigrants” or that frame the concept differently and conse- “aliens.” Instances of bias by word choice and label- quently may lead to different assessments by ing (WCL) frame the referred concept differently readers, such as the terms “freedom fighters” (Entman, 1993, 2007), whereby a broad spectrum and “terrorists,” or “gun rights” and “gun con- trol.” In this research project, I aim to devise of effects occurs. For example, the frame may methods that identify instances of WCL bias change the polarity of the concept, i.e., positively and estimate the frames they induce, e.g., not or negatively, or the frame may emphasize specific only is “terrorists” of negative polarity but also parts of an issue, such as the economic or cultural ascribes to aggression and fear. -

Classification of Propaganda on Fragment Level: Using Logistic Regression with Handcrafted Contextual Features
Classification of Propaganda on Fragment Level: Using Logistic Regression with Handcrafted Contextual Features Author Supervisor S. (Sylvain) Maissan Dong Nguyen Second Examiner Frans Adriaans June 26, 2020 1 Abstract Propaganda in the media has become a rising problem, especially after automation. The ease of which propaganda can be created and spread is astonishing. A way to combat this is an automated propaganda detection system. The goal of fine-grained propaganda detection is to determine whether a given sentence uses a propaganda technique, or to recognize which techniques are used on the fragment level. In this paper we try to analyze the effects of contextual features on the fragment level when training a propaganda classifier. Using a logistic regression model I created some handcrafted features that solely depend on contextual information. The results showed no significant impact on the performance. The features based on the propagandistic fragment itself prove to be the top features in this setting. In future research it is recommended to create either more complex contextual features or to create features that are able to discern whether the fragment is Loaded Language or Name Calling. Keywords: Propaganda Classification, Fragment Level, Contextual Features, 2 Contents 1. Introduction 4 2. Related Work 6 3. Datasets 8 4. Methods 11 4.1. Preprocessing 11 4.2. Features 12 4.3. Baseines 14 4.4. Evaluation 15 5. Results 16 6. Discussion 18 7. Conclusion 19 3 1 Introduction Propaganda aims at influencing people’s mindset with the purpose of advancing a specific agenda. It uses psychological and rhetorical techniques to persuade the public. -

Battling the Internet Water Army: Detection of Hidden Paid Posters
Battling the Internet Water Army: Detection of Hidden Paid Posters Cheng Chen Kui Wu Venkatesh Srinivasan Xudong Zhang Dept. of Computer Science Dept. of Computer Science Dept. of Computer Science Dept. of Computer Science University of Victoria University of Victoria University of Victoria Peking University Victoria, BC, Canada Victoria, BC, Canada Victoria, BC, Canada Beijing, China Abstract—We initiate a systematic study to help distinguish on different online communities and websites. Companies are a special group of online users, called hidden paid posters, or always interested in effective strategies to attract public atten- termed “Internet water army” in China, from the legitimate tion towards their products. The idea of online paid posters ones. On the Internet, the paid posters represent a new type of online job opportunity. They get paid for posting comments is similar to word-of-mouth advertisement. If a company hires and new threads or articles on different online communities enough online users, it would be able to create hot and trending and websites for some hidden purposes, e.g., to influence the topics designed to gain popularity. Furthermore, the articles opinion of other people towards certain social events or business or comments from a group of paid posters are also likely markets. Though an interesting strategy in business marketing, to capture the attention of common users and influence their paid posters may create a significant negative effect on the online communities, since the information from paid posters is usually decision. In this way, online paid posters present a powerful not trustworthy. When two competitive companies hire paid and efficient strategy for companies. -

Euphemism and Language Change: the Sixth and Seventh Ages
Lexis Journal in English Lexicology 7 | 2012 Euphemism as a Word-Formation Process Euphemism and Language Change: The Sixth and Seventh Ages Kate Burridge Electronic version URL: http://journals.openedition.org/lexis/355 DOI: 10.4000/lexis.355 ISSN: 1951-6215 Publisher Université Jean Moulin - Lyon 3 Electronic reference Kate Burridge, « Euphemism and Language Change: The Sixth and Seventh Ages », Lexis [Online], 7 | 2012, Online since 25 June 2012, connection on 30 April 2019. URL : http:// journals.openedition.org/lexis/355 ; DOI : 10.4000/lexis.355 Lexis is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License. Lexis 7: “Euphemism as a Word-Formation Process” 65 Euphemism and Language Change: The Sixth and Seventh Ages Kate Burridge1 Abstract No matter which human group we look at, past or present, euphemism and its counterpart dysphemism are powerful forces and they are extremely important for the study of language change. They provide an emotive trigger for word addition, word loss, phonological distortion and semantic shift. Word taBoo plays perpetual havoc with the methods of historical comparative linguistics, even undermining one of the cornerstones of the discipline – the arBitrary nature of the word. When it comes to taBoo words, speakers Behave as if there were a very real connection Between the physical shape of words and their taBoo sense. This is why these words are so unstaBle and why they are so powerful. This paper reviews the various communicative functions of euphemisms and the different linguistic strategies that are used in their creation, focusing on the linguistic creativity that surrounds the topic of ‘old age’ in Modern English (Shakespeare’s sixth and seventh ages). -

Sentiment Patterns in Videos from Left- and Right-Wing Youtube News Channels
Uphill from here: Sentiment patterns in videos from left- and right-wing YouTube news channels Felix Soldner1, Justin Chun-ting Ho2, Mykola Makhortykh3, Isabelle van der Vegt1, Maximilian Mozes1;4 and Bennett Kleinberg1;3 1University College London 2University of Edinburgh 3University of Amsterdam 4Technical University of Munich 1{felix.soldner, isabelle.vandervegt, bennett.kleinberg}@ucl.ac.uk [email protected], [email protected], [email protected] Abstract Netherlands) (Newman et al., 2018). The reasons for the growing online consumption of news are News consumption exhibits an increasing shift many: digital outlets provide higher interactivity towards online sources, which bring platforms such as YouTube more into focus. Thus, the and greater freedom of choice for news readers distribution of politically loaded news is eas- (Van Aelst et al., 2017), and the possibility to ac- ier, receives more attention, but also raises the cess them through mobile devices enables more concern of forming isolated ideological com- flexibility and convenience in consuming news munities. Understanding how such news is content (Schrøder, 2015). communicated and received is becoming in- Despite the multiple benefits associated with creasingly important. To expand our under- standing in this domain, we apply a linguistic "the digital turn" in news consumption, it also temporal trajectory analysis to analyze senti- raises concerns regarding possible changes in the ment patterns in English-language videos from societal role of news media (Coddington, 2015). news channels on YouTube. We examine tran- It has been established that there is a relationship scripts from videos distributed through eight between news consumption and the formation of channels with pro-left and pro-right political public agendas, including political attitudes of the leanings. -

Literature and Propaganda in George Orwell's Essays
LITERATURE AND PROPAGANDA IN GEORGE ORWELL'S ESSAYS Nina Sirkovi ć University of Split, Croatia [email protected] Abstract The paper explores the idea of manipulating language for the purpose of sending emotional messages and creating impressions in order to frame the reality to one's intentions. Among many other writers, George Orwell pointed out the social and political determination of literary writing and the author's responsibility in shaping the public opinion. In his essays, Orwell challenges the position of literature and art in general, concerning the society and political situation of his age. He questions the role of the writer in the age of totalitarianism, when the attitude to art is politically coloured and the integrity of the artist is threatened. The aim of the paper is to analyse several of Orwell's essays written between 1940 and 1949 in order to determine to what extent the relationship between art and politics is possible, provided that the artists still preserve their own sincerity and, as Orwell calls it “honest language“. Key-words: loaded language,literature, art, propaganda, totalitarianism. Introduction The world we live in is highly determined by the politics which influences our way of living, not only in a materialistic sense, but also determining in a great proportion our thinking, decision making and consequently, acting. Although loaded language is present in almost every aspect of human communication, politically loaded language can be dangerous since politics affects viewpoints of an enormous number of people, sometimes whole nations. Freely and Steinberg claim that loaded language provides many possibilities for obstacles to clear thinking. -

An Analysis of the Linguistic Techniques of Propaganda in Marketing and Politics
International Journal of English Learning and Teaching Skills; Vol. 2, No. 2; ISSN : 2639-7412 (Print) ISSN : 2638-5546 (Online) Running head: AN ANALYSIS OF THE LINGUISTIC TECHNIQUES 1 AN ANALYSIS OF THE LINGUISTIC TECHNIQUES OF PROPAGANDA IN MARKETING AND POLITICS Hanan Khaja Mohammad Irfan Institute of Engineering & Management, Kolkata 1181 International Journal of English Learning and Teaching Skills; Vol. 2, No. 2; ISSN : 2639-7412 (Print) ISSN : 2638-5546 (Online) AN ANALYSIS OF THE LINGUISTIC TECHNIQUES 2 Abstract Propaganda may be defined as the deliberate use of manipulation techniques in order to persuade the audience towards a biased opinion which helps a greater power or authority to develop the desirable perspective/choice in the target group. Though initially recognised with positive connotations, “propaganda” today is recognised as corrupt means frequently applied in politics and advertisements to subtly influence public opinion on a large scale which appear seemingly stochastic. This paper intends to explore the various linguistics techniques applied in order to promulgate propaganda and the effects they tend to have on the audience. Amongst the techniques varying from auditory to visual modes of propagation, this paper analyses the modes of establishing rhetoric through the use of language, standard parlance, prosody and other semiotic modalities in a public discourse. Keywords: Propaganda, manipulation, linguistic, techniques, language, parlance, prosody, semiotic modalities. 1182 International Journal of English Learning and Teaching Skills; Vol. 2, No. 2; ISSN : 2639-7412 (Print) ISSN : 2638-5546 (Online) AN ANALYSIS OF THE LINGUISTIC TECHNIQUES 3 AN ANALYSIS OF THE LINGUISTIC TECHNIQUES OF PROPAGANDA IN MARKETING AND POLITICS WHAT IS PROPAGANDA The origins of the semantics of propaganda are rooted in promulgation of “ideas that would not occur naturally, but only via a cultivated or artificial generation” by the Roman Catholic Church.