Recommendation for Block Cipher Modes of Operation: Three Variants of Ciphertext Stealing for CBC Mode
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Classical Encryption Techniques
CPE 542: CRYPTOGRAPHY & NETWORK SECURITY Chapter 2: Classical Encryption Techniques Dr. Lo’ai Tawalbeh Computer Engineering Department Jordan University of Science and Technology Jordan Dr. Lo’ai Tawalbeh Fall 2005 Introduction Basic Terminology • plaintext - the original message • ciphertext - the coded message • key - information used in encryption/decryption, and known only to sender/receiver • encipher (encrypt) - converting plaintext to ciphertext using key • decipher (decrypt) - recovering ciphertext from plaintext using key • cryptography - study of encryption principles/methods/designs • cryptanalysis (code breaking) - the study of principles/ methods of deciphering ciphertext Dr. Lo’ai Tawalbeh Fall 2005 1 Cryptographic Systems Cryptographic Systems are categorized according to: 1. The operation used in transferring plaintext to ciphertext: • Substitution: each element in the plaintext is mapped into another element • Transposition: the elements in the plaintext are re-arranged. 2. The number of keys used: • Symmetric (private- key) : both the sender and receiver use the same key • Asymmetric (public-key) : sender and receiver use different key 3. The way the plaintext is processed : • Block cipher : inputs are processed one block at a time, producing a corresponding output block. • Stream cipher: inputs are processed continuously, producing one element at a time (bit, Dr. Lo’ai Tawalbeh Fall 2005 Cryptographic Systems Symmetric Encryption Model Dr. Lo’ai Tawalbeh Fall 2005 2 Cryptographic Systems Requirements • two requirements for secure use of symmetric encryption: 1. a strong encryption algorithm 2. a secret key known only to sender / receiver •Y = Ek(X), where X: the plaintext, Y: the ciphertext •X = Dk(Y) • assume encryption algorithm is known •implies a secure channel to distribute key Dr. -

GCM) for Confidentiality And
NIST Special Publication 800-38D Recommendation for Block DRAFT (April, 2006) Cipher Modes of Operation: Galois/Counter Mode (GCM) for Confidentiality and Authentication Morris Dworkin C O M P U T E R S E C U R I T Y Abstract This Recommendation specifies the Galois/Counter Mode (GCM), an authenticated encryption mode of operation for a symmetric key block cipher. KEY WORDS: authentication; block cipher; cryptography; information security; integrity; message authentication code; mode of operation. i Table of Contents 1 PURPOSE...........................................................................................................................................................1 2 AUTHORITY.....................................................................................................................................................1 3 INTRODUCTION..............................................................................................................................................1 4 DEFINITIONS, ABBREVIATIONS, AND SYMBOLS.................................................................................2 4.1 DEFINITIONS AND ABBREVIATIONS .............................................................................................................2 4.2 SYMBOLS ....................................................................................................................................................4 4.2.1 Variables................................................................................................................................................4 -

Mcoe: a Family of Almost Foolproof On-Line Authenticated Encryption Schemes
McOE: A Family of Almost Foolproof On-Line Authenticated Encryption Schemes Ewan Fleischmann Christian Forler Stefan Lucks Bauhaus-Universit¨atWeimar FSE 2012 Fleischmann, Forler, Lucks. FSE 2012. McOE: A Family . {1{ Overview Fleischmann, Forler, Lucks. FSE 2012. McOE: A Family . {2{ 1. Motivation I Goldwasser and Micali (1984): requirement: given 2 ciphertexts, adversary cannot even detect when the same plaintext has been encrypted twice consequence: encryption stateful or probabilitistic (or both) I Rogaway (FSE 2004): formalizes state/randomness by nonces Plaintext Header Key Nonce 01 02 03 ... Ciphertext Authentication Tag Fleischmann, Forler, Lucks. FSE 2012. McOE: A Family . {3{ Authenticated Encryption I first studied by Katz and Young (FSE 2000) and Bellare and Namprempre (Asiacrypt 2000) I since then many proposed schemes, I nonce based, Plaintext Header Key Nonce I and proven secure assuming a \nonce-respecting01 02 03 ... adversary" I any implementation allowing a nonce reuse is not our problem . but maybe it shouldCiphertext Authentication Tag Fleischmann, Forler, Lucks. FSE 2012. McOE: A Family . {4{ Nonce Reuse in Practice I IEEE 802.11 [Borisov, Goldberg, Wagner 2001] I PS3 [Hotz 2010] I WinZip Encryption [Kohno 2004] I RC4 in MS Word and Excel [Wu 2005] I ... application programmer other issues: mistakes: I restoring a file from a backup I cloning the virtual machine the application runs on I ... Fleischmann, Forler, Lucks. FSE 2012. McOE: A Family . {5{ Nonce Reuse { what to Expect? our reasonable (?) expectations I some plaintext information leaks: I identical plaintexts I common prefixes I ect. I but not too much damage: 1. authentication not affected 2. -

Recommendation for Block Cipher Modes of Operation Methods
NIST Special Publication 800-38A Recommendation for Block 2001 Edition Cipher Modes of Operation Methods and Techniques Morris Dworkin C O M P U T E R S E C U R I T Y ii C O M P U T E R S E C U R I T Y Computer Security Division Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899-8930 December 2001 U.S. Department of Commerce Donald L. Evans, Secretary Technology Administration Phillip J. Bond, Under Secretary of Commerce for Technology National Institute of Standards and Technology Arden L. Bement, Jr., Director iii Reports on Information Security Technology The Information Technology Laboratory (ITL) at the National Institute of Standards and Technology (NIST) promotes the U.S. economy and public welfare by providing technical leadership for the Nation’s measurement and standards infrastructure. ITL develops tests, test methods, reference data, proof of concept implementations, and technical analyses to advance the development and productive use of information technology. ITL’s responsibilities include the development of technical, physical, administrative, and management standards and guidelines for the cost-effective security and privacy of sensitive unclassified information in Federal computer systems. This Special Publication 800-series reports on ITL’s research, guidance, and outreach efforts in computer security, and its collaborative activities with industry, government, and academic organizations. Certain commercial entities, equipment, or materials may be identified in this document in order to describe an experimental procedure or concept adequately. Such identification is not intended to imply recommendation or endorsement by the National Institute of Standards and Technology, nor is it intended to imply that the entities, materials, or equipment are necessarily the best available for the purpose. -

Index-Of-Coincidence.Pdf
The Index of Coincidence William F. Friedman in the 1930s developed the index of coincidence. For a given text X, where X is the sequence of letters x1x2…xn, the index of coincidence IC(X) is defined to be the probability that two randomly selected letters in the ciphertext represent, the same plaintext symbol. For a given ciphertext of length n, let n0, n1, …, n25 be the respective letter counts of A, B, C, . , Z in the ciphertext. Then, the index of coincidence can be computed as 25 ni (ni −1) IC = ∑ i=0 n(n −1) We can also calculate this index for any language source. For some source of letters, let p be the probability of occurrence of the letter a, p be the probability of occurrence of a € b the letter b, and so on. Then the index of coincidence for this source is 25 2 Isource = pa pa + pb pb +…+ pz pz = ∑ pi i=0 We can interpret the index of coincidence as the probability of randomly selecting two identical letters from the source. To see why the index of coincidence gives us useful information, first€ note that the empirical probability of randomly selecting two identical letters from a large English plaintext is approximately 0.065. This implies that an (English) ciphertext having an index of coincidence I of approximately 0.065 is probably associated with a mono-alphabetic substitution cipher, since this statistic will not change if the letters are simply relabeled (which is the effect of encrypting with a simple substitution). The longer and more random a Vigenere cipher keyword is, the more evenly the letters are distributed throughout the ciphertext. -

Block Ciphers
BLOCK CIPHERS MTH 440 Block ciphers • Plaintext is divided into blocks of a given length and turned into output ciphertext blocks of the same length • Suppose you had a block cipher, E(x,k) where the input plaintext blocks,x, were of size 5-bits and a 4-bit key, k. • PT = 10100010101100101 (17 bits), “Pad” the PT so that its length is a multiple of 5 (we will just pad with 0’s – it doesn’t really matter) • PT = 10100010101100101000 • Break the PT into blocks of 5-bits each (x=x1x2x3x4) where each xi is 5 bits) • x1=10100, x2= 01010, x3=11001, x4=01000 • Ciphertext: c1c2c3c4 where • c1=E(x1,k1), c2=E(x2,k2), c3=E(x3,k3), c4=E(x4,k4) • (when I write the blocks next to each other I just mean concatentate them (not multiply) – we’ll do this instead of using the || notation when it is not confusing) • Note the keys might all be the same or all different What do the E’s look like? • If y = E(x,k) then we’ll assume that we can decipher to a unique output so there is some function, we’ll call it D, so that x = D(y,k) • We might define our cipher to be repeated applications of some function E either with the same or different keys, we call each of these applications “round” • For example we might have a “3 round” cipher: y Fk x E((() E E x, k1 , k 2)), k 3 • We would then decipher via 1 x Fk (,, y) D((() D D y, k3 k 2) k 1) S-boxes (Substitution boxes) • Sometimes the “functions” used in the ciphers are just defined by a look up table that are often referred to “S- boxes” •x1 x 2 x 3 S(x 1 x 2 x 3 ) Define a 4-bit function with a 3-bit key 000 -

Automating the Development of Chosen Ciphertext Attacks
Automating the Development of Chosen Ciphertext Attacks Gabrielle Beck∗ Maximilian Zinkus∗ Matthew Green Johns Hopkins University Johns Hopkins University Johns Hopkins University [email protected] [email protected] [email protected] Abstract In this work we consider a specific class of vulner- ability: the continued use of unauthenticated symmet- In this work we investigate the problem of automating the ric encryption in many cryptographic systems. While development of adaptive chosen ciphertext attacks on sys- the research community has long noted the threat of tems that contain vulnerable format oracles. Unlike pre- adaptive-chosen ciphertext attacks on malleable en- vious attempts, which simply automate the execution of cryption schemes [17, 18, 56], these concerns gained known attacks, we consider a more challenging problem: practical salience with the discovery of padding ora- to programmatically derive a novel attack strategy, given cle attacks on a number of standard encryption pro- only a machine-readable description of the plaintext veri- tocols [6,7, 13, 22, 30, 40, 51, 52, 73]. Despite repeated fication function and the malleability characteristics of warnings to industry, variants of these attacks continue to the encryption scheme. We present a new set of algo- plague modern systems, including TLS 1.2’s CBC-mode rithms that use SAT and SMT solvers to reason deeply ciphersuite [5,7, 48] and hardware key management to- over the design of the system, producing an automated kens [10, 13]. A generalized variant, the format oracle attack strategy that can entirely decrypt protected mes- attack can be constructed when a decryption oracle leaks sages. -

Elastic Block Ciphers: the Basic Design
Elastic Block Ciphers: The Basic Design ∗ † Debra Cook Angelos Keromytis Moti Yung Bell Labs Columbia University RSA Labs, EMC Corp, and Murray Hill, NJ, USA Dept. of Computer Science Columbia University [email protected] New York, NY, USA Dept. of Computer Science [email protected] [email protected] ABSTRACT We introduce the concept of an elastic block cipher, which We introduce the concept of an elastic block cipher, which allows us to ”stretch” the supported block size of a block refers to stretching the supported block size of a block ci- cipher up to a length double the original block size, while pher to any length up to twice the original block size while increasing the computational workload proportionally to the incurring a computational workload that is proportional to block size. This, together with modes of operation, permits the block size. We define a method for converting any ex- block sizes to be set based on an application’s requirements, isting block cipher into an elastic block cipher and mention allowing, for example, a non-traditional block size to be used our analysis of the construction. for all blocks, or a traditional block size to be used for all but the last block in a given mode of operation. We pro- Categories and Subject Descriptors pose a general method for creating an elastic block cipher E.0 [General]: Data Encryption from an existing block cipher. Our intent is not to design a new ad-hoc cipher, but to systematically build upon existing General Terms block ciphers. Our method consists of a network structure block ciphers, algorithms, encryption that uses the round function from an existing block cipher, allowing us to treat the round function of the original ci- Keywords pher as a black box and reuse its properties. -

Block Ciphers II
Block Ciphers II Martin Stanek Department of Computer Science Comenius University [email protected] Cryptology 1 (2021/22) Block Ciphers 1 / 26 , Content Confidentiality modes – ECB, CBC, OFB, CFB, CTR Padding Padding oracle attack Ciphertext stealing Authenticated encryption – CCM, GCM Other constructions Format-preserving encryption Encryption of block devices Theoretical security of block ciphers Block Ciphers 2 / 26 , Modes of operation I plaintext usually much longer than the block length I modes of operation can provide: I confidentiality (and not authenticity) ...“traditional” modes I authenticity (and not confidentiality) I confidentiality & authenticity (authenticated encryption) I confidentiality for block-oriented storage devices (e.g. disks) I key wrapping I format-preserving encryption, ... I varying requirements (speed, security properties, ability to parallelize, availability of RNG, etc.) ) different modes Block Ciphers 3 / 26 , Confidentiality modes I the most important confidentiality modes: ECB, CBC, OFB, CFB, CTR I e.g. see NIST SP 800-38A: Recommendation for Block Cipher Modes of Operation: Methods and Techniques I None of these modes provide protection against accidental or adversarial modifications of ciphertext! I however, the effect of ciphertext modification on resulting plaintext varies among modes Block Ciphers 4 / 26 , ECB (Electronic Codebook) P1 P2 P1 P2 Ek Ek Dk Dk C1 C2 C1 C2 encrypt: Ci = Ek (Pi) decrypt: Pi = Dk (Ci) I the simplest mode I data leaks: Ci = Cj , Pi = Pj I easy to rearrange the ciphertexts blocks (permute, duplicate, ...) I encryption and decryption trivially parallelizable I easy to perform a seek (random access) I bit changes do not propagate (single block affected) Block Ciphers 5 / 26 , CBC (Cipher Block Chaining) 1 P1 P2 P1 P2 IV IV (C0) (C0) Ek Ek Dk Dk C1 C2 C1 C2 encrypt: Ci = Ek (Pi Ci 1) decrypt: Pi = Dk (Ci) Ci 1 ⊕ − ⊕ − I IV (initialization vector) – secrecy not required, usually appended as C0 I popular mode (e.g. -
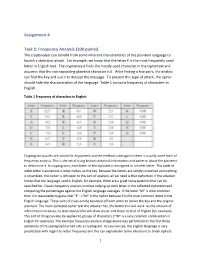
Assignment 4 Task 1: Frequency Analysis (100 Points)
Assignment 4 Task 1: Frequency Analysis (100 points) The cryptanalyst can benefit from some inherent characteristics of the plaintext language to launch a statistical attack. For example, we know that the letter E is the most frequently used letter in English text. The cryptanalyst finds the mostly-used character in the ciphertext and assumes that the corresponding plaintext character is E. After finding a few pairs, the analyst can find the key and use it to decrypt the message. To prevent this type of attack, the cipher should hide the characteristics of the language. Table 1 contains frequency of characters in English. Table 1 Frequency of characters in English Cryptogram puzzles are solved for enjoyment and the method used against them is usually some form of frequency analysis. This is the act of using known statistical information and patterns about the plaintext to determine it. In cryptograms, each letter of the alphabet is encrypted to another letter. This table of letter-letter translations is what makes up the key. Because the letters are simply converted and nothing is scrambled, the cipher is left open to this sort of analysis; all we need is that ciphertext. If the attacker knows that the language used is English, for example, there are a great many patterns that can be searched for. Classic frequency analysis involves tallying up each letter in the collected ciphertext and comparing the percentages against the English language averages. If the letter "M" is most common then it is reasonable to guess that "E"-->"M" in the cipher because E is the most common letter in the English language. -

Chap 2. Basic Encryption and Decryption
Chap 2. Basic Encryption and Decryption H. Lee Kwang Department of Electrical Engineering & Computer Science, KAIST Objectives • Concepts of encryption • Cryptanalysis: how encryption systems are “broken” 2.1 Terminology and Background • Notations – S: sender – R: receiver – T: transmission medium – O: outsider, interceptor, intruder, attacker, or, adversary • S wants to send a message to R – S entrusts the message to T who will deliver it to R – Possible actions of O • block(interrupt), intercept, modify, fabricate • Chapter 1 2.1.1 Terminology • Encryption and Decryption – encryption: a process of encoding a message so that its meaning is not obvious – decryption: the reverse process • encode(encipher) vs. decode(decipher) – encoding: the process of translating entire words or phrases to other words or phrases – enciphering: translating letters or symbols individually – encryption: the group term that covers both encoding and enciphering 2.1.1 Terminology • Plaintext vs. Ciphertext – P(plaintext): the original form of a message – C(ciphertext): the encrypted form • Basic operations – plaintext to ciphertext: encryption: C = E(P) – ciphertext to plaintext: decryption: P = D(C) – requirement: P = D(E(P)) 2.1.1 Terminology • Encryption with key If the encryption algorithm should fall into the interceptor’s – encryption key: KE – decryption key: K hands, future messages can still D be kept secret because the – C = E(K , P) E interceptor will not know the – P = D(KD, E(KE, P)) key value • Keyless Cipher – a cipher that does not require the -

Chapter 4 Symmetric Encryption
Chapter 4 Symmetric Encryption The symmetric setting considers two parties who share a key and will use this key to imbue communicated data with various security attributes. The main security goals are privacy and authenticity of the communicated data. The present chapter looks at privacy, Chapter ?? looks at authenticity, and Chapter ?? looks at providing both together. Chapters ?? and ?? describe tools we shall use here. 4.1 Symmetric encryption schemes The primitive we will consider is called an encryption scheme. Such a scheme speci¯es an encryption algorithm, which tells the sender how to process the plaintext using the key, thereby producing the ciphertext that is actually transmitted. An encryption scheme also speci¯es a decryption algorithm, which tells the receiver how to retrieve the original plaintext from the transmission while possibly performing some veri¯cation, too. Finally, there is a key-generation algorithm, which produces a key that the parties need to share. The formal description follows. De¯nition 4.1 A symmetric encryption scheme SE = (K; E; D) consists of three algorithms, as follows: ² The randomized key generation algorithm K returns a string K. We let Keys(SE) denote the set of all strings that have non-zero probability of be- ing output by K. The members of this set are called keys. We write K Ã$ K for the operation of executing K and letting K denote the key returned. ² The encryption algorithm E takes a key K 2 Keys(SE) and a plaintext M 2 f0; 1g¤ to return a ciphertext C 2 f0; 1g¤ [ f?g.