Oracle Linux Operating System
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Oracle® Linux Administrator's Solutions Guide for Release 6
Oracle® Linux Administrator's Solutions Guide for Release 6 E37355-64 August 2017 Oracle Legal Notices Copyright © 2012, 2017, Oracle and/or its affiliates. All rights reserved. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, delivered to U.S. Government end users are "commercial computer software" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, use, duplication, disclosure, modification, and adaptation of the programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, shall be subject to license terms and license restrictions applicable to the programs. No other rights are granted to the U.S. -

Adaptive Android Kernel Live Patching
Adaptive Android Kernel Live Patching Yue Chen Yulong Zhang Zhi Wang Liangzhao Xia Florida State University Baidu X-Lab Florida State University Baidu X-Lab Chenfu Bao Tao Wei Baidu X-Lab Baidu X-Lab Abstract apps contain sensitive personal data, such as bank ac- counts, mobile payments, private messages, and social Android kernel vulnerabilities pose a serious threat to network data. Even TrustZone, widely used as the se- user security and privacy. They allow attackers to take cure keystore and digital rights management in Android, full control over victim devices, install malicious and un- is under serious threat since the compromised kernel en- wanted apps, and maintain persistent control. Unfortu- ables the attacker to inject malicious payloads into Trust- nately, most Android devices are never timely updated Zone [42, 43]. Therefore, Android kernel vulnerabilities to protect their users from kernel exploits. Recent An- pose a serious threat to user privacy and security. droid malware even has built-in kernel exploits to take Tremendous efforts have been put into finding (and ex- advantage of this large window of vulnerability. An ef- ploiting) Android kernel vulnerabilities by both white- fective solution to this problem must be adaptable to lots hat and black-hat researchers, as evidenced by the sig- of (out-of-date) devices, quickly deployable, and secure nificant increase of kernel vulnerabilities disclosed in from misuse. However, the fragmented Android ecosys- Android Security Bulletin [3] in recent years. In ad- tem makes this a complex and challenging task. dition, many kernel vulnerabilities/exploits are publicly To address that, we systematically studied 1;139 An- available but never reported to Google or the vendors, droid kernels and all the recent critical Android ker- let alone patched (e.g., exploits in Android rooting nel vulnerabilities. -

Fault-Tolerant Components on AWS
Fault-Tolerant Components on AWS November 2019 This paper has been archived For the latest technical information, see the AWS Whitepapers & Guides page: Archivedhttps://aws.amazon.com/whitepapers Notices Customers are responsible for making their own independent assessment of the information in this document. This document: (a) is for informational purposes only, (b) represents current AWS product offerings and practices, which are subject to change without notice, and (c) does not create any commitments or assurances from AWS and its affiliates, suppliers or licensors. AWS products or services are provided “as is” without warranties, representations, or conditions of any kind, whether express or implied. The responsibilities and liabilities of AWS to its customers are controlled by AWS agreements, and this document is not part of, nor does it modify, any agreement between AWS and its customers. © 2019 Amazon Web Services, Inc. or its affiliates. All rights reserved. Archived Contents Introduction .......................................................................................................................... 1 Failures Shouldn’t Be THAT Interesting ............................................................................. 1 Amazon Elastic Compute Cloud ...................................................................................... 1 Elastic Block Store ........................................................................................................... 3 Auto Scaling .................................................................................................................... -

Oracle Berkeley DB Installation and Build Guide Release 18.1
Oracle Berkeley DB Installation and Build Guide Release 18.1 Library Version 18.1.32 Legal Notice Copyright © 2002 - 2019 Oracle and/or its affiliates. All rights reserved. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. Berkeley DB, and Sleepycat are trademarks or registered trademarks of Oracle. All rights to these marks are reserved. No third- party use is permitted without the express prior written consent of Oracle. Other names may be trademarks of their respective owners. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, delivered to U.S. Government end users are "commercial computer software" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, use, duplication, disclosure, modification, and adaptation of the programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, shall be subject to license terms and license restrictions applicable to the programs. -

Vsphere Availability Vmware Vsphere 6.5 Vmware Esxi 6.5 Vcenter Server 6.5
vSphere Availability VMware vSphere 6.5 VMware ESXi 6.5 vCenter Server 6.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this document, see http://www.vmware.com/support/pubs. EN-002085-01 vSphere Availability You can ®nd the most up-to-date technical documentation on the VMware Web site at: http://www.vmware.com/support/ The VMware Web site also provides the latest product updates. If you have comments about this documentation, submit your feedback to: [email protected] Copyright © 2009–2017 VMware, Inc. All rights reserved. Copyright and trademark information. VMware, Inc. 3401 Hillview Ave. Palo Alto, CA 94304 www.vmware.com 2 VMware, Inc. Contents About vSphere Availability 5 Updated Information for vSphere Availability 7 1 Business Continuity and Minimizing Downtime 9 Reducing Planned Downtime 9 Preventing Unplanned Downtime 10 vSphere HA Provides Rapid Recovery from Outages 10 vSphere Fault Tolerance Provides Continuous Availability 11 Protecting the vCenter Server Appliance with vCenter High Availability 12 Protecting vCenter Server with VMware Service Lifecycle Manager 12 2 Creating and Using vSphere HA Clusters 13 How vSphere HA Works 13 vSphere HA Admission Control 21 vSphere HA Interoperability 26 Creating a vSphere HA Cluster 29 Configuring vSphere Availability Settings 31 Best Practices for vSphere HA Clusters 39 3 Providing Fault Tolerance for Virtual Machines 43 How Fault Tolerance -

Protecting Your Linux Systems with Oracle Ksplice
Staying Ahead of Cyberthreats: Protecting Your Linux Systems with Oracle Ksplice The Advantages Of Zero-Downtime Patching April 23, 2020 Copyright © 2020, Oracle and/or its affiliates Public TABLE OF CONTENTS Introduction 2 Why Patching Matters 2 About Oracle Ksplice 3 Other Benefits 3 Conclusion 4 Learn More 4 1 WHITE PAPER | Staying Ahead of Cyberthreats: Protecting Your Linux Systems Copyright © 2020, Oracle and/or its affiliates |Public INTRODUCTION IT systems require regular patching for security, performance, and compliance reasons. For Linux operating system (OS) kernel updates, which include “Availability requirements important new security enhancements and bug fixes, releases happen about 1 are on the rise for once per month. These updates help keep systems current with the latest organizations undergoing innovations. However, manually patching systems has many inherent digital transformations. challenges and difficulties which tends to delay their timely application. For this Downtimes are costly, reason, zero-downtime patching solutions for Linux, like Oracle Ksplice, are with unplanned becoming essential tools. In this paper, Oracle Ksplice’s capabilities and many infrastructure downtimes advantages are explained. costing $100,000 per hour on an average. With Why Patching Matters the possibility of every organization being a Inadequate patch management can leave loopholes in the IT infrastructure leading to target for cyberattacks various security and performance issues. Ideally, patches should be applied shortly after and attackers moving very release to ensure the latest system protections. Patching typically requires downtime quickly to exploit system which, depending on operations, can require weeks or months of advanced planning. vulnerabilities, IDC Most Linux patching also traditionally happens at the disk level for file systems, which has recommends several disadvantages. -

Rethinking Database High Availability with RDMA Networks
Rethinking Database High Availability with RDMA Networks Erfan Zamanian1, Xiangyao Yu2, Michael Stonebraker2, Tim Kraska2 1 Brown University 2 Massachusetts Institute of Technology [email protected], fyxy, stonebraker, [email protected] ABSTRACT copy propagate to all the backup copies synchronously such that Highly available database systems rely on data replication to tol- any failed primary server can be replaced by a backup server. erate machine failures. Both classes of existing replication algo- The conventional wisdom of distributed system design is that rithms, active-passive and active-active, were designed in a time the network is a severe performance bottleneck. Messaging over when network was the dominant performance bottleneck. In essence, a conventional 10-Gigabit Ethernet within the same data center, these techniques aim to minimize network communication between for example, delivers 2–3 orders of magnitude higher latency and replicas at the cost of incurring more processing redundancy; a lower bandwidth compared to accessing the local main memory of trade-off that suitably fitted the conventional wisdom of distributed a server [3]. Two dominant high availability approaches, active- database design. However, the emergence of next-generation net- passive and active-active, both adopt the optimization goal of min- works with high throughput and low latency calls for revisiting imizing network overhead. these assumptions. With the rise of the next-generation networks, however, conven- In this paper, we first make the case that in modern RDMA- tional high availability protocol designs are not appropriate any- enabled networks, the bottleneck has shifted to CPUs, and there- more, especially in a setting of Local Area Network (LAN). -

Oracle Solaris 11 Cheat Sheet Dtrace
Oracle Solaris 11 Administrator's Cheat Sheet for DTrace Oracle Solaris 11 Cheat Sheet DTrace What is DTrace? DTrace Command Components Oracle Solaris DTrace is a comprehensive, advanced tracing tool for troubleshooting A typical DTrace command has several components: systematic problems in real time. Administrators, integrators and developers can use DTrace to dynamically and safely observe live production systems for performance issues, A 4-tuple identifier provider:module:function:name, where module is a kernel including both applications and the operating system itself. DTrace allows you to explore • module or application library, and function and name are the routines that are to be your system to understand how it works, track down problems across many layers of software, and locate the cause of any aberrant behavior. Whether it’s at a high level global instrumented. If any of these are left black, it is equivalent to a wildcard match. For overview like memory consumption or CPU time, to much finer grained information like what example, to fire all entry routines in the syscall provider we would use the following: specific function calls are being made, DTrace gives the operational insights that have long syscall:::entry been missing in the data center. • A predicate, or relational expression, that determines whether any action should be Understanding DTrace providers and probes taken. For example, to check whether the process name matches bash we would use the following: /execname == “bash”/ Oracle Solaris 11 is littered with many different points of instrumentation – places of interest • An action for what should happen if the probe fires and the predicate is satisfied. -

SUSE Linux Enterprise Server 15 SP2 Autoyast Guide Autoyast Guide SUSE Linux Enterprise Server 15 SP2
SUSE Linux Enterprise Server 15 SP2 AutoYaST Guide AutoYaST Guide SUSE Linux Enterprise Server 15 SP2 AutoYaST is a system for unattended mass deployment of SUSE Linux Enterprise Server systems. AutoYaST installations are performed using an AutoYaST control le (also called a “prole”) with your customized installation and conguration data. Publication Date: September 24, 2021 SUSE LLC 1800 South Novell Place Provo, UT 84606 USA https://documentation.suse.com Copyright © 2006– 2021 SUSE LLC and contributors. All rights reserved. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or (at your option) version 1.3; with the Invariant Section being this copyright notice and license. A copy of the license version 1.2 is included in the section entitled “GNU Free Documentation License”. For SUSE trademarks, see https://www.suse.com/company/legal/ . All other third-party trademarks are the property of their respective owners. Trademark symbols (®, ™ etc.) denote trademarks of SUSE and its aliates. Asterisks (*) denote third-party trademarks. All information found in this book has been compiled with utmost attention to detail. However, this does not guarantee complete accuracy. Neither SUSE LLC, its aliates, the authors nor the translators shall be held liable for possible errors or the consequences thereof. Contents 1 Introduction to AutoYaST 1 1.1 Motivation 1 1.2 Overview and Concept 1 I UNDERSTANDING AND CREATING THE AUTOYAST CONTROL FILE 4 2 The AutoYaST Control -
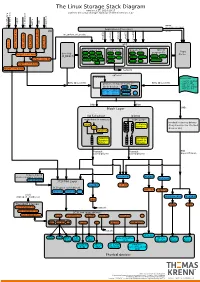
The Linux Storage Stack Diagram
The Linux Storage Stack Diagram version 3.17, 2014-10-17 outlines the Linux storage stack as of Kernel version 3.17 ISCSI USB mmap Fibre Channel Fibre over Ethernet Fibre Channel Fibre Virtual Host Virtual FireWire (anonymous pages) Applications (Processes) LIO malloc vfs_writev, vfs_readv, ... ... stat(2) read(2) open(2) write(2) chmod(2) VFS tcm_fc sbp_target tcm_usb_gadget tcm_vhost tcm_qla2xxx iscsi_target_mod block based FS Network FS pseudo FS special Page ext2 ext3 ext4 proc purpose FS target_core_mod direct I/O NFS coda sysfs Cache (O_DIRECT) xfs btrfs tmpfs ifs smbfs ... pipefs futexfs ramfs target_core_file iso9660 gfs ocfs ... devtmpfs ... ceph usbfs target_core_iblock target_core_pscsi network optional stackable struct bio - sector on disk BIOs (Block I/O) BIOs (Block I/O) - sector cnt devices on top of “normal” - bio_vec cnt block devices drbd LVM - bio_vec index - bio_vec list device mapper mdraid dm-crypt dm-mirror ... dm-cache dm-thin bcache BIOs BIOs Block Layer BIOs I/O Scheduler blkmq maps bios to requests multi queue hooked in device drivers noop Software (they hook in like stacked ... Queues cfq devices do) deadline Hardware Hardware Dispatch ... Dispatch Queue Queues Request Request BIO based Drivers based Drivers based Drivers request-based device mapper targets /dev/nullb* /dev/vd* /dev/rssd* dm-multipath SCSI Mid Layer /dev/rbd* null_blk SCSI upper level drivers virtio_blk mtip32xx /dev/sda /dev/sdb ... sysfs (transport attributes) /dev/nvme#n# /dev/skd* rbd Transport Classes nvme skd scsi_transport_fc network -

Oracle® Solaris 11.4 Dtrace
® Oracle Solaris 11.4 DTrace (Dynamic Tracing) Guide Part No: E61035 November 2020 Oracle Solaris 11.4 DTrace (Dynamic Tracing) Guide Part No: E61035 Copyright © 2011, 2020, Oracle and/or its affiliates. License Restrictions Warranty/Consequential Damages Disclaimer This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. Warranty Disclaimer The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. Restricted Rights Notice If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs (including any operating system, integrated software, any programs embedded, installed or activated on delivered hardware, and modifications of such programs) and Oracle computer documentation or other Oracle data delivered to or accessed by U.S. Government end users are "commercial computer software" -

Effective Cache Apportioning for Performance Isolation Under
Effective Cache Apportioning for Performance Isolation Under Compiler Guidance Bodhisatwa Chatterjee Sharjeel Khan Georgia Institute of Technology Georgia Institute of Technology Atlanta, USA Atlanta, USA [email protected] [email protected] Santosh Pande Georgia Institute of Technology Atlanta, USA [email protected] Abstract cache partitioning to divide the LLC among the co-executing With a growing number of cores per socket in modern data- applications in the system. Ideally, a cache partitioning centers where multi-tenancy of a diverse set of applications scheme obtains overall gains in system performance by pro- must be efficiently supported, effective sharing of the last viding a dedicated region of cache memory to high-priority level cache is a very important problem. This is challenging cache-intensive applications and ensures security against because modern workloads exhibit dynamic phase behaviour cache-sharing attacks by the notion of isolated execution in - their cache requirements & sensitivity vary across different an otherwise shared LLC. Apart from achieving superior execution points. To tackle this problem, we propose Com- application performance and improving system throughput CAS, a compiler guided cache apportioning system that pro- [7, 20, 31], cache partitioning can also serve a variety of pur- vides smart cache allocation to co-executing applications in a poses - improving system power and energy consumption system. The front-end of Com-CAS is primarily a compiler- [6, 23], ensuring fairness in resource allocation [26, 36] and framework equipped with learning mechanisms to predict even enabling worst case execution-time analysis of real-time cache requirements, while the backend consists of allocation systems [18].