6WIND Vrouter Datasheet February 2020.Cdr
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Examining Factors of the NFV-I Impacting Performance and Portability
WHITE PAPER Examining Factors of the NFV-I Impacting Performance and Portability www.ixiacom.com 915-0953-01 Rev. A, May 2015 2 Table of Contents Introduction ................................................................................................. 4 Compute Platform ........................................................................................ 7 CPU/Motherboard and Storage .............................................................. 8 CPU Pinning ........................................................................................... 9 Logical Processor Support ................................................................... 11 QuickPath Interconnect (QPI) ...............................................................12 Packet Processing Enhancements and Acceleration ............................13 Storage .................................................................................................16 Network Interface Cards (NICs) .................................................................17 PCI Passthrough ...................................................................................18 Single Root I/O Virtualization (SR-IOV) ...............................................18 Host OS and Hypervisor ............................................................................21 Open Source NFV-I Platforms ............................................................. 23 Know the Performance Curve ............................................................. 24 Virtual Networking ................................................................................... -

2016 Mega NFV Report Pt. 1: MANO and NFVI
Market Report 2016 Mega NFV Report Pt. 1: MANO and NFVI The Trusted News and Resource Site for SDx, SDN, NFV, Cloud and Virtualization Infrastructure Market Report | 2016 Mega NFV Report Pt. 1: MANO and NFVI contents Table of Contents Introduction – NFV Platforms Grow Up . 1 Investment Benefits of NFV in NFVI and MANO . 3 NFV Architecture . 5 NFV Market Landscape . 11 NFV MANO Products. 16 NFVI Products . 16 NFV Monitoring and Testing Products . 17 Vendor Profiles . 18 MANO and NFVI Products [Featured] Brocade: Brocade SDN Controller . 21 Brocade: Brocade Vyatta Network OS . 22 Cisco Systems, Inc.: Cisco NFV Infrastructure . 23 Cisco Systems, Inc.: Cisco Network Services Orchestrator (NSO) enabled by Tail-f . 23 Cisco Systems, Inc.: Cisco Virtual Topology System (VTS) . 23 Cisco Systems, Inc.: Cisco Elastic Services Controller (ESC) . 23 Juniper Networks, Inc.: Juniper Networks Contrail . 24 Wind River: Titanium Server . .26 MANO ADVA Optical Networking: Ensemble Orchestrator . 27 Affirmed Networks: Affirmed Mobile Content Cloud . 27 Amartus: Chameleon SDS . .27 Anuta Networks, Inc.: Anuta Network NCX . .28 ATTO Research: Athena . 28 Avaya Inc.: Avaya SDN Fx Architecture . 28 Brocade: Brocade VNF Manager . .29 Canonical: Ubuntu OpenStack . 29 CA Technologies: CA Virtual Network Assurance . 29 CENX, Inc: Exanova Service Intelligence . 30 Ciena: Ciena Blue Planet . .30 Ericsson Network Manager & Ericsson Cloud Manager . 30 Fujitsu: Network Virtuora OM and Virtuora RV . 31 Huawei: Huawei FusionSphere . 31 MRV Communications: MRV Pro-Vision . 31 Nakina Systems: NI-CONTROLLER . 32 Nakina Systems: NI-FRAMEWORK . .32 NEC/Netcracker: NEC/Netcracker Orchestration . 32 Nokia: CloudBand . 33 © 2016 SDNCentral LLC. All Rights Reserved. Page ii Market Report | 2016 Mega NFV Report Pt. -

Cisco Live 2014
Introduction to Software-Defined Networking (SDN) and Network Programmability BRKSDN-1014 Jason Davis, Distinguished Engineer (Services) Abstract SDN is an exciting new approach to network IT Service Management. You may have questions about SDN, Controllers, APIs, Overlays, OpenFlow and ACI. You may also be wondering what products and services are SDN-enabled and how you can solve your unique business challenges and enhance your differentiated services by leveraging network programmability. In this introductory session we will cover the genesis of SDN, what it is, what it is not, and Cisco's involvement in this space. Cisco's SDN- enabled Products and Services will be explained enabling you to consider your own implementations. Since SDN extends network flexibility and functionality which impacts Network Engineering and Operations teams, we'll also cover the IT Service Management impact. Network engineers, network operation staff, IT Service Managers, IT personnel managers, and application/compute SMEs will benefit from this session. BRKSDN-1014 © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Public 3 Agenda • What is SDN & Network Programmability • What are the Use Cases and Problems Solved with SDN? • An Overview of OpenFlow • What Are Cisco's solutions? • An Overview of Network Overlays • An Overview of Network Controllers • An Overview of ACI • The Impact to IT Service Management • How to Get Ready BRKSDN-1014 © 2015 Cisco and/or its affiliates. All rights reserved. Cisco Public 4 What is Software-Defined Networking (SDN)? • An approach and architecture in networking where control and data planes are decoupled and intelligence and state are logically centralized • Enablement where underlying network infrastructure is abstracted from the applications [network virtualization] • A concept that leverages programmatic interfaces to enable external systems to influence network provisioning, control and operations BRKSDN-1014 © 2015 Cisco and/or its affiliates. -

Can Open-Source Projects (Re-)Shape the SDN/NFV-Driven Telecommunication Market?
DE GRUYTER OLDENBOURG it – Information Technology 2015; 57(5): 267–276 Special Issue Wouter Tavernier*, Bram Naudts, Didier Colle, Mario Pickavet, and Sofie Verbrugge Can open-source projects (re-)shape the SDN/NFV-driven telecommunication market? DOI 10.1515/itit-2015-0026 ACM CCS: Networks → Network services → Programmable Received June 30, 2015; revised July 17, 2015; accepted July 20, 2015 networks Abstract: Telecom network operators face rapidly chang- ing business needs. Due to their dependence on long prod- uct cycles they lack the ability to quickly respond to chang- 1 Introduction ing user demands. To spur innovation and stay competi- tive, network operators are investigating technological so- The increased softwarization and programmability have lutions with a proven track record in other application do- changed the telecom landscape significantly. Whereas mains such as open source software projects. Open source communication networks previously were under the rigid software enables parties to learn, use, or contribute to control of vendor-specific solutions or tightly standardized technology from which they were previously excluded. protocols, Software-Defined Networking (SDN) enabled OSS has reshaped many application areas including the network operators to configure the control of their net- landscape of operating systems and consumer software. works through their-own custom software. Network Func- The paradigm shift in telecommunication systems towards tion Virtualization (NFV) pushes this even further by mak- Software-Defined Networking introduces possibilities to ing it possible to code data plane behavior in software, en- benefit from open source projects. Implementing the con- abling it to run on general purpose server hardware rather trol part of networks in software enables speedier adap- than on expensive vendor-controlled hardware platforms. -

D2.1 Horizon 2020 – 732497 – 5GINFIRE
Deliverable D2.1 Horizon 2020 – 732497 – 5GINFIRE D2.1 - 5GinFIRE Experimental Infrastructure Architecture and 5G Automotive Use Case Editor: Riwal Kerherve, B-COM Deliverable nature: Report (R) Dissemination level: Public (PU) Date: planned | actual 30 April 2017 26 May 2017 Version | No. of pages 1.0 113 Keywords: State of the art, use cases, architecture, 5G, MANO, Automotive, Smart cities Abstract This deliverable is the first technical deliverable of the project. It is the result of the project work to establish the baseline of the state of the art in cloud computing, Software Defined Networking (SDN), Network Function Virtualisation (NFV) and Service Function Chaining (SFC). It captures a snapshot of available technologies and components. In addition this deliverable describes the use cases that will be demonstrated later in the project. Finally it describes the first draft 5GinFIRE architecture that will be deployed by the project. This deliverable is the basis for the future work of the project on Experimentation Architecture Tooling, Core MANO Service Management and Orchestration, as well as 5G Infrastructure Integration and Experimentation Enablement. Page 1 of (113) Horizon 2020 – 732497 – 5GINFIRE Deliverable D2.1 Disclaimer This document contains material, which is the copyright of certain 5GINFIRE consortium parties, and may not be reproduced or copied without permission. All 5GINFIRE consortium parties have agreed to full publication of this document. Neither the 5GINFIRE consortium as a whole, nor a certain part of the 5GINFIRE consortium, warrant that the information contained in this document is capable of use, nor that use of the information is free from risk, accepting no liability for loss or damage suffered by any person using this information. -
Prosupport Suite and Premium Support
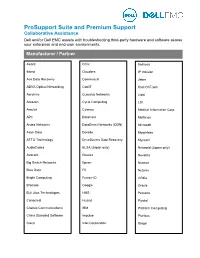
ProSupport Suite and Premium Support Collaborative Assistance Dell and/or Dell EMC assists with troubleshooting third-party hardware and software across your enterprise and end-user environments. Manufacturer / Partner 4ward Citrix Invincea 6wind Cloudera IP Infusion Ace Data Recovery Commvault Jabra ADVA Optical Networking CoolIT Kroll OnTrack Aerohive Cumulus Networks Liqid Amazon Cycle Computing LSI Amulet Cylance Medical Information Corp. APC DataCore Mellanox Aruba Networks DataDirect Networks (DDN) Microsoft Aster Data Dorado Morphlabs ATTO Technology DriveSavers Data Recovery Myricom AudioCodes ELSA (Japan only) Networld (Japan only) Avocent Emulex Nexenta Big Switch Networks Epson Nuance Blue Data F5 Nutanix Bright Computing Fusion-IO nVidia Brocade Google Oracle Bull Atos Technologies HMS Pentaho Canonical Huarui Pivotal Chelsio Communications IBM Platform Computing China Standard Software Impulse Pluribus Cisco Intel Corporation Qlogic QNAP Quantum Rackspace Red Hat SanDisk SAP1 Scality Silver Peak Software AG Solarflare Splunk StackIQ Stratus SUSE Symantec ThinkParq ThinLaunch Unicon/eLux Unidesk VeloCloud Versa Networks VMware Vormetric Wave 1. Customer must initiate case with SAP directly. SAP initiates collaboration requests with Dell and/or Dell EMC. Wind River Customer equipment and devices must be covered by manufacturer's warranty or customer provided maintenance contractXerox for Dell to engage with third-party vendor and to qualify for Dell collaborative assistance. Collaborative partners are subject to change without notice. Not all regions, products, and versions may be included in the scope of collaborative assistance. Product and service availability vary by country. Contact Dell for more information. Copyright © 2019 Dell Inc. or its subsidiaries. All Rights Reserved. Dell, EMC, and other trademarks are trademarks of Dell Inc. -

MANO-Deployed Virtual Router Simplifies Network Deployments
SOLUTION BRIEF Communications Service Providers Virtual Routers MANO-Deployed Virtual Router Simplifies Network Deployments 6WIND,* Advantech,* and Cloudify* create virtual routers with simplified deployment and lifecycle management to scale networks. Italian CommSP EOLO* utilizes this solution to create a backbone mesh connecting thousands of wireless base stations. Virtual routers provide the functionality of legacy, fixed-function routers with more flexibility and lower cost. The next step for communications service providers (CommSPs) who have embraced this technology and are deploying thousands of these virtual network functions (VNFs) throughout their network is to add management and network orchestration (MANO) features that can provide better configuration, deployment, and lifecycle management functions to all of the vRouters in a network. 6WIND,* Cloudify,* and Advantech*—all Intel® Network Builders ecosystem partners—have integrated their technologies to provide a MANO-deployed vRouter solution. vRouters Need MANO A virtual router is a virtual network function (VNF) application that runs on commercial off-the-shelf (COTS) server platforms and replaces legacy routers that run on fixed-function hardware appliances. The use of COTS servers typically makes vRouters less expensive to purchase, while the remote deployability and life cycle management of software-based vRouters reduces the cost to operate routed networks. Virtual router companies like 6WIND have made significant progress on evolving vRouter software. With new Intel® Xeon® Scalable processors and packet forwarding technology such as the open source Data Plane Development Kit (DPDK), vRouters can offer the outstanding performance that CommSPs require.¹ Now, 6WIND is tackling the challenge of mass deployment and management of vRouter networks by working with MANO software from Cloudify. -

Taking Control of SDN-Based Cloud Systems Via the Data Plane
Taking Control of SDN-based Cloud Systems via the Data Plane Kashyap Thimmaraju Bhargava Shastry Tobias Fiebig Felicitas Hetzelt Security in Security in Faculty of Technology, Security in Telecommunications Telecommunications Policy and Management Telecommunications TU Berlin TU Berlin TU Delft TU Berlin Berlin, Germany Berlin, Germany Delft, Netherlands Berlin, Germany kash@sect:tu-berlin:de bshastry@sect:tu-berlin:de t:fiebig@tudelft:nl file@sect:tu-berlin:de Jean-Pierre Seifert Anja Feldmann Stefan Schmid∗† Security in Internet Network Faculty of Computer Telecommunications Architectures Science TU Berlin TU Berlin University of Vienna Berlin, Germany Berlin, Germany Vienna, Austria jpseifert@sect:tu-berlin:de anja@inet:tu-berlin:de schmiste@univie:ac:at ABSTRACT KEYWORDS Virtual switches are a crucial component of SDN-based cloud sys- Network Isolation; Network Virtualization; Data Plane Security; tems, enabling the interconnection of virtual machines in a flexible Packet Parsing; MPLS; Virtual Switches; Open vSwitch; Cloud Se- and “software-defined” manner. This paper raises the alarm onthe curity; OpenStack; Attacker Models; ROP; SDN; NFV security implications of virtual switches. In particular, we show that virtual switches not only increase the attack surface of the cloud, 1 INTRODUCTION but virtual switch vulnerabilities can also lead to attacks of much higher impact compared to traditional switches. Modern cloud systems such as OpenStack [1], Microsoft Azure [2] We present a systematic security analysis and identify four de- and Google Cloud Platform [3] are designed for programmabil- sign decisions which introduce vulnerabilities. Our findings moti- ity, (logically) centralized network control and global visibility. vate us to revisit existing threat models for SDN-based cloud setups, These tenets also lie at the heart of Software-defined Networking and introduce a new attacker model for SDN-based cloud systems (SDN) [4, 5] which enables cloud providers to efficiently utilize their using virtual switches. -

6WIND Boosts Ipsec with Intel® Xeon® Scalable Processors
SOLUTION BRIEF Communications Service Providers IP Security 6WIND Boosts IPsec with Intel® Xeon® Scalable Processors Tests of 6WIND Turbo IPsec show up to a 50% performance improvement when run on a server powered by the Intel® Xeon® Platinum 8170 processor.1 Introduction IP security (IPsec) is a critical element for every IP network to help protect against cyberattacks and provide data confidentiality, privacy, and security. Mobile network operators (MNO) and data centers are adopting bare metal and virtualized IPsec solutions on Intel servers to realize scalability and efficiency while lowering costs. Server performance is a critical issue in effective bare metal and virtualized IPsec solutions, and the Intel® Xeon® Scalable processors offer new options for next-generation networks. To test the new processors, Intel® Network Builders ecosystem member 6WIND set up two use cases for its 6WIND Turbo IPsec™ virtualized software. The Challenge To evaluate the performance of Intel Xeon Scalable processors, 6WIND selected its two most popular customer use cases to test the 6WIND Turbo IPsec VNF. Security-Enabled Site-to-Site Virtual Private Networks (VPNs): IPsec virtual private networks (VPNs) are critical to wide area network infrastructure to create security-enabled, high-speed communications tunnels between trusted endpoints. Examples include linking data centers and remote sites in a corporate network. Since IP WANs should be considered inherently insecure, IPsec VPNs maintain data confidentiality and integrity through encryption techniques, and they must provide scalable throughput to avoid bottlenecks that can force data centers to choose performance over security. For example, poor performance can translate to a loss of customers in multi-tenant data centers. -

Intel and Red Hat Demonstrate SDN Service-Chaining Solutions
White Paper Intel® Open Network Platform Software Defined Networking Division Going Virtual: Intel and Red Hat Demonstrate SDN Service-Chaining Solutions As software-defined networking (SDN) and network function virtualization (NFV) have gained traction in the marketplace, many organizations—from enterprise IT to cloud and telecommunications service providers—have discovered the benefits of virtualizing compute and networking components. Enterprises and service providers face intense pressure to support the rapid deployment of new services, and this is one of the key factors driving the industry shift to SDN and NFV solutions. Service chaining adds another dimension to virtualization possibilities: added flexibility in integrating virtual appliances into the mix to handle routing, switching, and other functions as part of the service chain. Service chaining provides a flexible means of managing network traffic more intelligently—with greater agility—when moving from physical networking machines, such as routers and switches, to virtual network appliances that implement multiple virtual machines on each standard high-volume server (SHVS). To advance this technology further, the Intel® Open Network Platform (Intel® ONP) reference architecture and Red Hat’s Enterprise Linux* OpenStack* platform, combined with open-source components and virtual appliances from Intel® Network Builders partners, form the basis of a powerful demonstration that shows the practical capabilities of service chaining in action. This paper explains the concepts that characterize service chaining and discusses the multi-vendor demo that illustrates the benefits of this technology to enterprises, cloud, and telecommunications companies. Going Virtual: Intel and Red Hat Demonstrate SDN Service-Chaining Solutions Table of Contents What is the Intel ONP Dynamic service chaining offers a Reference Architecture? means to improve efficiency and What is the Intel ONP systematically direct packets, flows, Developed to streamline the design, Reference Architecture? . -

6WIND* Support for Intel® Data Plane Development Kit Presentation
6WIND Support for Intel® Data Plane Development Kit (DPDK) V1.5 / 1 V1.6 | ©6WIND 2014. All rights reserved. All brand names, trademarks and copyright information cited in this presentation shall remain the property of its registered owners. Topics Introduction DPDK.org open-source project Intel® DPDK library from 6WIND Baseline features Optional add-ons Support Business model Integrated packet processing solution: 6WINDGate™ plus Intel® DPDK Features and benefits Performance Support Use cases Summary ©6WIND 2014 V1.6 | 2 Topics Introduction DPDK.org open-source project Intel® DPDK library from 6WIND Baseline features Optional add-ons Support Business model Integrated packet processing solution: 6WINDGate™ plus Intel® DPDK Features and benefits Performance Support Use cases Summary ©6WIND 2014 V1.6 | 3 Introduction: 6WIND and Intel® DPDK Long-term strategic partnership First high performance networking software on Intel processors, introduced before Intel® DPDK First commercial networking software with Intel® DPDK support, demonstrated at Intel Developer Forum September 2011 6WINDGate deployed on IA platforms by tier-1 networking and telecom equipment OEMs Launched dpdk.org in April 2013 ©6WIND 2014 V1.6 | 4 Your Three Options for Obtaining Intel® DPDK 1. From Intel • As direct Intel customer • Latest version of Intel® DPDK • www.intel/com/go/dpdk Baseline Intel® DPDK Code Sync of git tree dpdk.org 2. From dpdk.org • Latest version of Intel DPDK • Community patches Open-Source • Community support Community -

6WIND* and Intel®: Delivering High-Performance Software-Based IP and Ipsec Routing
WHITE PAPER 6WIND* and Intel®: Delivering High-Performance Software-Based IP and IPsec Routing Introduction Communications service providers, cloud service providers, and enterprises are in the midst of a significant network architecture transformation as they increase the amount of IP routing and security they use, while at the same time reducing their costs. To do that, they are increasingly adopting software-based routing. While the economic advantage of this approach is substantial – Intel® architecture servers replace dedicated hardware and can drive down the cost per gigabit by up to 80% 1 – many first-generation software routers didn’t offer the performance needed for today’s network applications. In fact, the performance from Linux*- based routers wasn’t enough to fill a 10 Gbps network connection.2 That’s why 6WIND* developed the Speed Series* for Intel platforms – a 200 Gbps IP router, the industry’s first 100 Gbps IPsec software solution, and a software platform for wire speed virtual infrastructure acceleration. The Speed Series is based on 6WINDGate*, a high-performance packet processing software solution. 6WIND also leverages the power of Intel® Xeon® servers and collaborated with Intel on technologies such as the Data Plane Development Kit (DPDK) that are instrumental to achieving these performance levels. More IP Networks Drives Need for More Routing and Security From advanced wireless networks to the Internet of Things, the demand for IP routing and network security is growing at a very fast pace. For example, in the market for service provider routers, 2014 was a record year for the industry with aggregate revenues hitting $10 billion according the research by Dell’Oro Group.