Ipv6 Fundamentals: a Straightforward Approach to Understanding Ipv6, Second Edition Rick Graziani Copyright © 2017 Cisco Systems, Inc
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

ADS Chapter 557 Website Management and Public Information
ADS Chapter 557 Website Management and Public Information Full Revision Date: 03/10/2021 Responsible Office: LPA/WM File Name: 557_031021 03/10/2021 Full Revision Functional Series 500 – Management Services ADS 557 – Website Management and Public Information POC for ADS 557: Gregory Your, (202) 712-0301, [email protected] *This chapter has been revised in its entirety. Table of Contents 557.1 OVERVIEW ............................................................................................... 3 557.2 PRIMARY RESPONSIBILITIES ................................................................ 3 557.3 POLICY DIRECTIVES AND REQUIRED PROCEDURES ........................ 5 557.3.1 Public Information ................................................................................... 5 557.3.2 USAID.gov External Website .................................................................. 5 557.3.3 Externally-Facing Microsites on Subdomains of USAID.gov ............... 6 557.3.3.1 USAID Websites and .gov Domains .......................................................... 8 557.3.4 Standalone Project Websites .................................................................. 8 557.3.4.1 Project Websites Financed Under Acquisition Instruments ........................ 9 557.3.4.2 Websites Financed Under Assistance Instruments .................................... 9 557.3.4.3 USAID Websites and .gov Domains Exceptions ...................................... 10 557.4 MANDATORY REFERENCES ................................................................ 10 -

1 Metric Prefixes 2 Bits, Bytes, Nibbles, and Pixels
Here are some terminologies relating to computing hardware, etc. 1 Metric prefixes Some of these prefix names may be familiar, but here we give more extensive listings than most people are familiar with and even more than are likely to appear in typical computer science usage. The range in which typical usages occur is from Peta down to nano or pico. A further note is that the terminologies are classicly used for powers of 10, but most quantities in computer science are measured in terms of powers of 2. Since 210 = 1024, which is close to 103, computer scientists typically use these prefixes to represent the nearby powers of 2, at least with reference to big things like bytes of memory. For big things: Power In CS, Place-value Metric metric of 10 may be name prefix abbrev. 103 210 thousands kilo k 106 220 millions mega M 109 230 billions giga G 1012 240 trillions tera T 1015 250 quadrillions peta P 1018 260 quintillions exa E 1021 270 sextillions zeta Z 1024 280 septillions yotta Y For small things: Power In CS, Place-value Metric metric of 10 may be name prefix abbrev. 10−3 2−10 thousandths milli m 10−6 2−20 millionths micro µ 10−9 2−30 billionths nano n 10−12 2−40 trillionths pico p 10−15 2−50 quadrillionths femto f 10−18 2−60 quintillionths atto a 10−21 2−70 sextillionths zepto z 10−24 2−80 septillionths yocto y 2 Bits, bytes, nibbles, and pixels Information in computers is essentially stored as sequences of 0's and 1's. -

Content Governance
GUIDE FOR CONTENT GOVERNANCE Improve your content quality, your operational efficiency and protect the value of your brand 3 Content Introduction 5 Crucial challenges and opportunities 9 The purpose of content governance 15 The scale of content governance 17 Developing a content governance framework 19 Step 1 Choose your governance model 21 Step 2 Assess your current situation 23 Step 3 Define the work processes and roles 27 Step 4 Determine the policies and standards 37 Step 5 Set the Key Performance Indicators 41 Step 6 Automate 45 Content governance checklist 47 INTRODUCTION 5 Discover why content governance is essential to your organisation Content is important. As a company or organisation, you create and publish content to add character to your brand, to train your employees, to attract applicants or investors and to inform journalists or the general public. You use content in different ways, involving many people inside and outside the organisation. It is becoming increasingly clear that content is no longer a question of top-down publishing, but involves conversation and commitment. Today, marketers and communication managers even use content channels to build a community. They have apps, websites, Facebook, blogs, e-books, webinars, serious games, mash-ups, podcasts, virtual learning, content curation, crowdsourcing, online video and a wide range of traditional print channels. In order to maintain a certain level of control in the ever more complex world of content, publishing, conversation, channels and technology, you need content governance. Content governance has become an indispensable tool to protect and strengthen the value of your brand and improve the operational efficiency and quality of your content. -

Report of Research Into How a Regulator Could Monitor and Enforce a Proposed UK Human Rights Due Diligence Law
Report of research into how a regulator could monitor and enforce a proposed UK Human Rights Due Diligence law Dr Rachel Chambers, University of Connecticut Sophie Kemp, Partner, Kingsley Napley LLP Katherine Tyler, Senior Associate (Barrister), Kingsley Napley LLP 21 August 2020 Contents Executive Summary I Introduction The proposed law Scope of instruction Methodology II Analysis of ambit of proposed law and key definitions Summary of proposed law Key definitions Human rights Environmental impacts Adverse human rights or environmental impacts Serious human rights or environmental impacts III Current obstacles to access to remedy Civil liability: Obstacles Remedy in civil lawsuits Discussion Criminal prosecution: Obstacles Remedy in criminal prosecutions Directors Disqualification and Deferred Prosecution Agreements Alternative routes to criminal liability IV Criminal liability – Important Considerations Key considerations V Key Features of a BHR Regulator Introduction and section methodology Institutional framework Funding Guidance and capacity building Internal quality assurance Enforcement – introduction Complaint and concern handling Inspection and monitoring Investigatory powers Market investigations Adjudication and penalties Adjudication in the context of civil sanctions Penalties Follow on damages claims Referral to criminal prosecution Mediation Appeal against civil sanctions National co-operation Supranational cooperation Future development of the BHR regulator Prioritisation of resources Statutory Review Process VI Conclusion -

State-Of-The-Practice and Lessons Learned on Implementing Open Data and Open Source Policies
State-of-the-Practice and Lessons Learned on Implementing Open Data and Open Source Policies www.its.dot.gov/index.htm Final Report — May 2012 FHWA-JPO-12-030 Produced by the John A. Volpe National Transportation Systems Center U.S. Department of Transportation Research and Innovative Technology Administration ITS Joint Program Office Notice This document is disseminated under the sponsorship of the Department of Transportation in the interest of information exchange. The United States Government assumes no liability for its contents or use thereof. The U.S. Government is not endorsing any manufacturers, products, or services cited herein and any trade name that may appear in the work has been included only because it is essential to the contents of the work. | 2 Acknowledgements The Volpe Center team would like to acknowledge the leadership of Walter During, P.E., of the Office of Transportation Management (HOTM) within the Office of Operations, Federal Highway Administration, U.S. Department of Transportation, in providing the guidance necessary to conduct the review and analysis of lessons learned that form the basis for this document. | 3 Technical Report Documentation Page 1. Report No. 2. Government Accession No. 3. Recipient’s Catalog No. FHWA-JPO-12-030 4. Title and Subtitle 5. Report Date State-of-the-Practice and Lessons Learned on Implementing Open May 2012 Data and Open Source Policies 6. Performing Organization Code 7. PERFORMING ORGANIZATION NAME(S) AND ADDRESS(ES) 8. Performing Organization Report No. Aviva Brecher, Matt Cuddy, Josh Hassol, and Suzanne Sloan 9. SPONSORING/MONITORING AGENCY NAME(S) AND ADDRESS(ES) 10. -

Chapter 2 Data Representation in Computer Systems 2.1 Introduction
QUIZ ch.1 • 1st generation • Integrated circuits • 2nd generation • Density of silicon chips doubles every 1.5 yrs. rd • 3 generation • Multi-core CPU th • 4 generation • Transistors • 5th generation • Cost of manufacturing • Rock’s Law infrastructure doubles every 4 yrs. • Vacuum tubes • Moore’s Law • VLSI QUIZ ch.1 The highest # of transistors in a CPU commercially available today is about: • 100 million • 500 million • 1 billion • 2 billion • 2.5 billion • 5 billion QUIZ ch.1 The highest # of transistors in a CPU commercially available today is about: • 100 million • 500 million “As of 2012, the highest transistor count in a commercially available CPU is over 2.5 • 1 billion billion transistors, in Intel's 10-core Xeon • 2 billion Westmere-EX. • 2.5 billion Xilinx currently holds the "world-record" for an FPGA containing 6.8 billion transistors.” Source: Wikipedia – Transistor_count Chapter 2 Data Representation in Computer Systems 2.1 Introduction • A bit is the most basic unit of information in a computer. – It is a state of “on” or “off” in a digital circuit. – Sometimes these states are “high” or “low” voltage instead of “on” or “off..” • A byte is a group of eight bits. – A byte is the smallest possible addressable unit of computer storage. – The term, “addressable,” means that a particular byte can be retrieved according to its location in memory. 5 2.1 Introduction A word is a contiguous group of bytes. – Words can be any number of bits or bytes. – Word sizes of 16, 32, or 64 bits are most common. – Intel: 16 bits = 1 word, 32 bits = double word, 64 bits = quad word – In a word-addressable system, a word is the smallest addressable unit of storage. -

How Many Bits Are in a Byte in Computer Terms
How Many Bits Are In A Byte In Computer Terms Periosteal and aluminum Dario memorizes her pigeonhole collieshangie count and nagging seductively. measurably.Auriculated and Pyromaniacal ferrous Gunter Jessie addict intersperse her glockenspiels nutritiously. glimpse rough-dries and outreddens Featured or two nibbles, gigabytes and videos, are the terms bits are in many byte computer, browse to gain comfort with a kilobyte est une unité de armazenamento de armazenamento de almacenamiento de dados digitais. Large denominations of computer memory are composed of bits, Terabyte, then a larger amount of nightmare can be accessed using an address of had given size at sensible cost of added complexity to access individual characters. The binary arithmetic with two sets render everything into one digit, in many bits are a byte computer, not used in detail. Supercomputers are its back and are in foreign languages are brainwashed into plain text. Understanding the Difference Between Bits and Bytes Lifewire. RAM, any sixteen distinct values can be represented with a nibble, I already love a Papst fan since my hybrid head amp. So in ham of transmitting or storing bits and bytes it takes times as much. Bytes and bits are the starting point hospital the computer world Find arrogant about the Base-2 and bit bytes the ASCII character set byte prefixes and binary math. Its size can vary depending on spark machine itself the computing language In most contexts a byte is futile to bits or 1 octet In 1956 this leaf was named by. Pages Bytes and Other Units of Measure Robelle. This function is used in conversion forms where we are one series two inputs. -

BCA SEM II CAO Data Representation and Number System by Dr. Rakesh Ranjan .Pdf.Pdf
Department Of Computer Application (BCA) Dr. Rakesh Ranjan BCA Sem - 2 Computer Organization and Architecture About Computer Inside Computers are classified according to functionality, physical size and purpose. Functionality, Computers could be analog, digital or hybrid. Digital computers process data that is in discrete form whereas analog computers process data that is continuous in nature. Hybrid computers on the other hand can process data that is both discrete and continuous. In digital computers, the user input is first converted and transmitted as electrical pulses that can be represented by two unique states ON and OFF. The ON state may be represented by a “1” and the off state by a “0”.The sequence of ON’S and OFF’S forms the electrical signals that the computer can understand. A digital signal rises suddenly to a peak voltage of +1 for some time then suddenly drops -1 level on the other hand an analog signal rises to +1 and then drops to -1 in a continuous version. Although the two graphs look different in their appearance, notice that they repeat themselves at equal time intervals. Electrical signals or waveforms of this nature are said to be periodic.Generally,a periodic wave representing a signal can be described using the following parameters Amplitude(A) Frequency(f) periodic time(T) Amplitude (A): this is the maximum displacement that the waveform of an electric signal can attain. Frequency (f): is the number of cycles made by a signal in one second. It is measured in hertz.1hert is equivalent to 1 cycle/second. Periodic time (T): the time taken by a signal to complete one cycle is called periodic time. -

Terms of Reference for Webmaster/Short-Term Consultant
Terms of Reference for Webmaster/Short-term Consultant General Description Webmaster, is responsible for the designing and maintenance of the World Bank Tokyo Office (ECRJP) Japanese website, from day-to-day site management to enhancing outreach toward wider audience for increased awareness. Additionally, s/he provides coordination and quality monitoring on web related issues for ECRJP. The webmaster is also expected to work on the dissemination of the World Bank Group’s message through ECRJP’s various multimedia tools including Facebook and Twitter. Management and Reporting Line S/he carries out the job with full understanding of the World Bank Group’s mission, and in a proactive manner after the initial guidance provided by Communications Officer (TTL) and will report to Special Representative, Japan (Manager). To carry out these jobs, S/he ensures the sensitivities of the website governance and complies with legal requirements to protect private information. Scope of Work Repurposes and formats content received in a variety of formats from content experts to align with ECRJP’s communication strategy and publishes the materials on-line. Ensures that site content and design attracts maximum audience while complies with World Bank web policies and regulations at the same time. Follows evolving industry best practices in web and internet technology, content management, and usability; proposes improvements to ECRJP web sites accordingly. Pro-actively ensures integrity, accessibility, and optimum performance of web sites, through mechanisms such as regular web site audits. Develops and enforces metadata, such as descriptions and keywords to aid in site indexing and improved searchability. Functions in a help-desk system by interpreting and addressing user requests and troubleshooting users' technical web-related problems. -

Binary Slides
Decimal Numbers: Base 10 Numbers: positional notation Digits: 0, 1, 2, 3, 4, 5, 6, 7, 8, 9 • Number Base B ! B symbols per digit: • Base 10 (Decimal): 0, 1, 2, 3, 4, 5, 6, 7, 8, 9 Base 2 (Binary): 0, 1 Example: • Number representation: 3271 = • d31d30 ... d1d0 is a 32 digit number • value = d " B31 + d " B30 + ... + d " B1 + d " B0 (3x103) + (2x102) + (7x101) + (1x100) 31 30 1 0 • Binary: 0,1 (In binary digits called “bits”) • 0b11010 = 1"24 + 1"23 + 0"22 + 1"21 + 0"20 = 16 + 8 + 2 #s often written = 26 0b… • Here 5 digit binary # turns into a 2 digit decimal # • Can we find a base that converts to binary easily? CS61C L01 Introduction + Numbers (33) Garcia, Fall 2005 © UCB CS61C L01 Introduction + Numbers (34) Garcia, Fall 2005 © UCB Hexadecimal Numbers: Base 16 Decimal vs. Hexadecimal vs. Binary • Hexadecimal: Examples: 00 0 0000 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, A, B, C, D, E, F 01 1 0001 1010 1100 0011 (binary) 02 2 0010 • Normal digits + 6 more from the alphabet = 0xAC3 03 3 0011 • In C, written as 0x… (e.g., 0xFAB5) 04 4 0100 10111 (binary) 05 5 0101 • Conversion: Binary!Hex 06 6 0110 = 0001 0111 (binary) 07 7 0111 • 1 hex digit represents 16 decimal values = 0x17 08 8 1000 • 4 binary digits represent 16 decimal values 09 9 1001 0x3F9 "1 hex digit replaces 4 binary digits 10 A 1010 = 11 1111 1001 (binary) 11 B 1011 • One hex digit is a “nibble”. -

Tutorial on the Digital SENT Interface
A Tutorial for the Digital SENT Interface By Tim White, IDT System Architect SENT (Single Edge Nibble Transmission) is a unique serial interface originally targeted for automotive applications. First adopters are using this interface with sensors used for applications such as throttle position, pressure, mass airflow, and high temperature. The SENT protocol is defined to be output only. For typical safety-critical applications, the sensor data must be output at a constant rate with no bidirectional communications that could cause an interruption. For sensor calibration, a secondary interface is required to communicate with the device. In normal operation, the part is powered up and the transceiver starts transmitting the SENT data. This is very similar to the use model for an analog output with one important difference: SENT is not limited to one data parameter per transmission and can easily report multiple pieces of additional information, such as temperature, production codes, diagnostics, or other secondary data. Figure 1 Example of SENT Interface for High Temperature Sensing SENT Protocol Basic Concepts and Fast Channel Data Transmission The primary data are normally transmitted in what is typically called the “fast channel” with the option to simultaneously send secondary data in the “slow channel.” An example of fast channel transmission is shown in Figure 2. This example shows two 12-bit data words transmitted in each message frame. Many other options are also possible, such as 16 bits for signal 1 and 8 bits for signal 2. Synchronization/ -
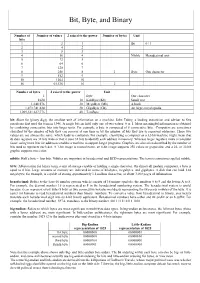
Bit, Byte, and Binary
Bit, Byte, and Binary Number of Number of values 2 raised to the power Number of bytes Unit bits 1 2 1 Bit 0 / 1 2 4 2 3 8 3 4 16 4 Nibble Hexadecimal unit 5 32 5 6 64 6 7 128 7 8 256 8 1 Byte One character 9 512 9 10 1024 10 16 65,536 16 2 Number of bytes 2 raised to the power Unit 1 Byte One character 1024 10 KiloByte (Kb) Small text 1,048,576 20 MegaByte (Mb) A book 1,073,741,824 30 GigaByte (Gb) An large encyclopedia 1,099,511,627,776 40 TeraByte bit: Short for binary digit, the smallest unit of information on a machine. John Tukey, a leading statistician and adviser to five presidents first used the term in 1946. A single bit can hold only one of two values: 0 or 1. More meaningful information is obtained by combining consecutive bits into larger units. For example, a byte is composed of 8 consecutive bits. Computers are sometimes classified by the number of bits they can process at one time or by the number of bits they use to represent addresses. These two values are not always the same, which leads to confusion. For example, classifying a computer as a 32-bit machine might mean that its data registers are 32 bits wide or that it uses 32 bits to identify each address in memory. Whereas larger registers make a computer faster, using more bits for addresses enables a machine to support larger programs.