Ethical Implications of the Snowden Revelations
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Case Study of NETRA
Network Protocols and Algorithms ISSN 1943-3581 2016, Vo l . 8, No. 4 Internet Traffic Surveillance & Network Monitoring in India: Case Study of NETRA Rajan Gupta Dept. of Computer Science, Faculty of Mathematical Sciences, University of Delhi 1st Floor, North Campus, Delhi – 110007, India E-mail: [email protected], [email protected] Sunil Kumar Muttoo Dept. of Computer Science, Faculty of Mathematical Sciences, University of Delhi 1st Floor, North Campus, Delhi – 110007, India Received: October 20, 2016 Accepted: December 30, 2016 Published: December 31, 2016 DOI: 10.5296/npa.v8i4.10179 URL: http://dx.doi.org/10.5296/npa.v8i4.10179 Abstract Internet traffic surveillance is gaining importance in today’s digital world. Lots of international agencies are putting in efforts to monitor the network around their countries to see suspicious activities and illegal or illegitimate transmission of messages. India, being a center of attraction for terrorist activities, is also working towards development of such surveillance systems. NETRA or Network Traffic Analysis is one such effort being taken by the Indian Government to filter suspicious keywords from messages in the network. But is it good enough to be used at highest level for security analysis or does the system design needs to be improved as compared to other similar systems around the world; this question is answered through this study. The comparison of NETRA is done against Dish Fire, Prism and Echelon. The design of the NETRA scheme and implementation level analysis of the system shows few weaknesses like limited memory options, limited channels for monitoring, pre-set filters, ignoring big data demands, security concerns, social values breach and ignoring ethical issues. -

Cinema of the Dark Side Atrocity and the Ethics of Film Spectatorship
Cinema of the Dark Side Atrocity and the Ethics of Film Spectatorship Shohini Chaudhuri CHAUDHURI 9780748642632 PRINT.indd 1 26/09/2014 16:33 © Shohini Chaudhuri, 2014 Edinburgh University Press Ltd The Tun – Holyrood Road 12 (2f) Jackson’s Entry Edinburgh EH8 8PJ www.euppublishing.com Typeset in Monotype Ehrhardt by Servis Filmsetting Ltd, Stockport, Cheshire, and printed and bound in Great Britain by CPI Group (UK) Ltd, Croydon CR0 4YY A CIP record for this book is available from the British Library ISBN 978 0 7486 4263 2 (hardback) ISBN 978 1 4744 0042 8 (paperback) ISBN 978 0 7486 9461 7 (webready PDF) ISBN 978 1 4744 0043 5 (epub) The right of Shohini Chaudhuri to be identified as author of this work has been asserted in accordance with the Copyright, Designs and Patents Act 1988 and the Copyright and Related Rights Regulations 2003 (SI No. 2498). CHAUDHURI 9780748642632 PRINT.indd 2 26/09/2014 16:33 Contents Acknowledgements iv List of Figures viii Introduction 1 1 Documenting the Dark Side: Fictional and Documentary Treatments of Torture and the ‘War On Terror’ 22 2 History Lessons: What Audiences (Could) Learn about Genocide from Historical Dramas 50 3 The Art of Disappearance: Remembering Political Violence in Argentina and Chile 84 4 Uninvited Visitors: Immigration, Detention and Deportation in Science Fiction 115 5 Architectures of Enmity: the Israeli–Palestinian Conflict through a Cinematic Lens 146 Conclusion 178 Bibliography 184 Index 197 CHAUDHURI 9780748642632 PRINT.indd 3 26/09/2014 16:33 Introduction n the science fiction film Children of Men (2006), set in a future dystopian IBritain, a propaganda film plays on a TV screen on a train. -

Advocating for Basic Constitutional Search Protections to Apply to Cell Phones from Eavesdropping and Tracking by Government and Corporate Entities
University of Central Florida STARS HIM 1990-2015 2013 Brave New World Reloaded: Advocating for Basic Constitutional Search Protections to Apply to Cell Phones from Eavesdropping and Tracking by Government and Corporate Entities Mark Berrios-Ayala University of Central Florida Part of the Legal Studies Commons Find similar works at: https://stars.library.ucf.edu/honorstheses1990-2015 University of Central Florida Libraries http://library.ucf.edu This Open Access is brought to you for free and open access by STARS. It has been accepted for inclusion in HIM 1990-2015 by an authorized administrator of STARS. For more information, please contact [email protected]. Recommended Citation Berrios-Ayala, Mark, "Brave New World Reloaded: Advocating for Basic Constitutional Search Protections to Apply to Cell Phones from Eavesdropping and Tracking by Government and Corporate Entities" (2013). HIM 1990-2015. 1519. https://stars.library.ucf.edu/honorstheses1990-2015/1519 BRAVE NEW WORLD RELOADED: ADVOCATING FOR BASIC CONSTITUTIONAL SEARCH PROTECTIONS TO APPLY TO CELL PHONES FROM EAVESDROPPING AND TRACKING BY THE GOVERNMENT AND CORPORATE ENTITIES by MARK KENNETH BERRIOS-AYALA A thesis submitted in partial fulfillment of the requirements for the Honors in the Major Program in Legal Studies in the College of Health and Public Affairs and in The Burnett Honors College at the University of Central Florida Orlando, Florida Fall Term 2013 Thesis Chair: Dr. Abby Milon ABSTRACT Imagine a world where someone’s personal information is constantly compromised, where federal government entities AKA Big Brother always knows what anyone is Googling, who an individual is texting, and their emoticons on Twitter. -

Lonworks® Platform Revision 2
Introduction to the LonWorks® Platform revision 2 ® 078-0183-01B Echelon, LON, LonWorks, LonMark, NodeBuilder, , LonTalk, Neuron, 3120, 3150, LNS, i.LON, , ShortStack, LonMaker, the Echelon logo, and are trademarks of Echelon Corporation registered in the United States and other countries. LonSupport, , , OpenLDV, Pyxos, LonScanner, LonBridge, and Thinking Inside the Box are trademarks of Echelon Corporation. Other trademarks belong to their respective holders. Neuron Chips, Smart Transceivers, and other OEM Products were not designed for use in equipment or systems which involve danger to human health or safety or a risk of property damage and Echelon assumes no responsibility or liability for use of the Neuron Chips in such applications. Parts manufactured by vendors other than Echelon and referenced in this document have been described for illustrative purposes only, and may not have been tested by Echelon. It is the responsibility of the customer to determine the suitability of these parts for each application. ECHELON MAKES AND YOU RECEIVE NO WARRANTIES OR CONDITIONS, EXPRESS, IMPLIED, STATUTORY OR IN ANY COMMUNICATION WITH YOU, AND ECHELON SPECIFICALLY DISCLAIMS ANY IMPLIED WARRANTY OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior written permission of Echelon Corporation. Printed in the United States of America. Copyright -

A Failure of Intelligence: the Echelon Interception System & the Fundamental Right to Privacy in Europe
Pace International Law Review Volume 14 Issue 2 Fall 2002 Article 7 September 2002 Post-Sept. 11th International Surveillance Activity - A Failure of Intelligence: The Echelon Interception System & the Fundamental Right to Privacy in Europe Kevin J. Lawner Follow this and additional works at: https://digitalcommons.pace.edu/pilr Recommended Citation Kevin J. Lawner, Post-Sept. 11th International Surveillance Activity - A Failure of Intelligence: The Echelon Interception System & the Fundamental Right to Privacy in Europe, 14 Pace Int'l L. Rev. 435 (2002) Available at: https://digitalcommons.pace.edu/pilr/vol14/iss2/7 This Article is brought to you for free and open access by the School of Law at DigitalCommons@Pace. It has been accepted for inclusion in Pace International Law Review by an authorized administrator of DigitalCommons@Pace. For more information, please contact [email protected]. POST-SEPT. 11TH INTERNATIONAL SURVEILLANCE ACTIVITY - A FAILURE OF INTELLIGENCE: THE ECHELON INTERCEPTION SYSTEM & THE FUNDAMENTAL RIGHT TO PRIVACY IN EUROPE Kevin J. Lawner* I. Introduction ....................................... 436 II. Communications Intelligence & the United Kingdom - United States Security Agreement ..... 443 A. September 11th - A Failure of Intelligence .... 446 B. The Three Warning Flags ..................... 449 III. The Echelon Interception System .................. 452 A. The Menwith Hill and Bad Aibling Interception Stations .......................... 452 B. Echelon: The Abuse of Power .................. 454 IV. Anti-Terror Measures in the Wake of September 11th ............................................... 456 V. Surveillance Activity and the Fundamental Right to Privacy in Europe .............................. 460 A. The United Nations International Covenant on Civil and Political Rights and the Charter of Fundamental Rights of the European Union... 464 B. -
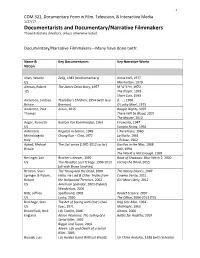
Documentarists and Documentary/Narrative Filmmakers Those Listed Are Directors, Unless Otherwise Noted
1 COM 321, Documentary Form in Film, Television, & Interactive Media 1/27/17 Documentarists and Documentary/Narrative Filmmakers Those listed are directors, unless otherwise noted. Documentary/Narrative Filmmakers—Many have done both: Name & Key Documentaries Key Narrative Works Nation Allen, Woody Zelig, 1983 (mockumentary) Annie Hall, 1977 US Manhattan, 1979 Altman, Robert The James Dean Story, 1957 M*A*S*H, 1970 US The Player, 1992 Short Cuts, 1993 Anderson, Lindsay Thursday’s Children, 1954 (with Guy if. , 1968 Britain Brenton) O Lucky Man!, 1973 Anderson, Paul Junun, 2015 Boogie Nights, 1997 Thomas There Will be Blood, 2007 The Master, 2012 Anger, Kenneth Kustom Kar Kommandos, 1963 Fireworks, 1947 US Scorpio Rising, 1964 Antonioni, Ragazze in bianco, 1949 L’Avventura, 1960 Michelangelo Chung Kuo – Cina, 1972 La Notte, 1961 Italy L'Eclisse, 1962 Apted, Michael The Up! series (1970‐2012 so far) Gorillas in the Mist, 1988 Britain Nell, 1994 The World is Not Enough, 1999 Berlinger, Joe Brother’s Keeper, 1992 Book of Shadows: Blair Witch 2, 2000 US The Paradise Lost Trilogy, 1996-2011 Facing the Wind, 2015 (all with Bruce Sinofsky) Berman, Shari The Young and the Dead, 2000 The Nanny Diaries, 2007 Springer & Pulcini, Hello, He Lied & Other Truths from Cinema Verite, 2011 Robert the Hollywood Trenches, 2002 Girl Most Likely, 2012 US American Splendor, 2003 (hybrid) Wanderlust, 2006 Blitz, Jeffrey Spellbound, 2002 Rocket Science, 2007 US Lucky, 2010 The Office, 2006-2013 (TV) Brakhage, Stan The Act of Seeing with One’s Own Dog Star Man, -

A Public Accountability Defense for National Security Leakers and Whistleblowers
A Public Accountability Defense For National Security Leakers and Whistleblowers The Harvard community has made this article openly available. Please share how this access benefits you. Your story matters Citation Yochai Benkler, A Public Accountability Defense For National Security Leakers and Whistleblowers, 8 Harv. L. & Pol'y Rev. 281 (2014). Published Version http://www3.law.harvard.edu/journals/hlpr/files/2014/08/ HLP203.pdf Citable link http://nrs.harvard.edu/urn-3:HUL.InstRepos:12786017 Terms of Use This article was downloaded from Harvard University’s DASH repository, and is made available under the terms and conditions applicable to Open Access Policy Articles, as set forth at http:// nrs.harvard.edu/urn-3:HUL.InstRepos:dash.current.terms-of- use#OAP A Public Accountability Defense for National Security Leakers and Whistleblowers Yochai Benkler* In June 2013 Glenn Greenwald, Laura Poitras, and Barton Gellman be- gan to publish stories in The Guardian and The Washington Post based on arguably the most significant national security leak in American history.1 By leaking a large cache of classified documents to these reporters, Edward Snowden launched the most extensive public reassessment of surveillance practices by the American security establishment since the mid-1970s.2 Within six months, nineteen bills had been introduced in Congress to sub- stantially reform the National Security Agency’s (“NSA”) bulk collection program and its oversight process;3 a federal judge had held that one of the major disclosed programs violated the -

Privacy and Civil Liberties Oversight Board
PRIVACY AND CIVIL LIBERTIES OVERSIGHT BOARD Semi-Annual Report February 2020 1 2 The Honorable Carolyn B. Maloney Report Distribution Chairwoman U.S. House of Representatives Committee In accordance with Section 801 of the on Oversight and Reform Implementing Recommendations of the 9/11 Commission Act of 2007, the Privacy and Civil The Honorable Jim Jordan Liberties Oversight Board (PCLOB or the Ranking Member Board) is providing this Semi-Annual Report, U.S. House of Representatives Committee which covers the period from August 2019 - on Oversight and Reform January 2020, to the President and the Members of Congress listed below. The Honorable Jerrold Nadler Chairman The Honorable Richard Shelby U.S. House of Representatives Chairman Committee on the Judiciary U.S. Senate Committee on Appropriations The Honorable Doug Collins The Honorable Patrick Leahy Ranking Member Vice Chairman U.S. House of Representatives U.S. Senate Committee on Appropriations Committee on the Judiciary The Honorable Ron Johnson The Honorable Nita M. Lowey Chairman Chairwoman U.S. Senate Committee on Homeland Security and U.S. House of Representatives Committee Governmental Affairs on Appropriations The Honorable Gary C. Peters The Honorable Kay Granger Ranking Member Ranking Member U.S. Senate Committee on Homeland Security and U.S. House of Representatives Committee Governmental Affairs on Appropriations The Honorable Richard Burr The Honorable Bennie G. Thompson Chairman Chairman U.S. Senate Select Committee on Intelligence U.S. House of Representatives Committee on Homeland Security The Honorable Mark Warner Vice Chairman The Honorable Mike Rogers U.S. Senate Select Committee on Intelligence Ranking Member U.S. -

An Interview with James Bamford
Investigating the Puzzle Palace: An Interview with James Bamford BONNIE BRENNAN AND KATHERINE GILBERT QUESTION: Do you consider clandestine intelligence gathering a legitimate activity for a modern nation-state? BAMFORD: I think it is very legitimate; I ju.st think that it should be directed externally. It is unrealistic not to have clandestine activities, though to some extent NSA isn't even really engaged in clandestine collection. Thousands of signals are just falling down outside right now, and all they're doing is putting out a dish and collecting them. There's not really anything clandestine about it. A listening post is a large thing with big antennae that can be seen from the road. It's just technical collection gathering, and I don't think there's anything really wrong with that as long as they're concentrating on foreign countries. We assume foreign countries can do the same thing to the United States. The Soviet Union, I'm sure, has a big listening post in Cuba. I don't see anything wrong with that. QUESTION: In his book, The Codebreakers, David Kahn shows that intelligence gathering by nations is as old as civilization. In the nineteenth century, Clausewitz described "intelligence" as the "basis . of our own plans and operations" and posited that "unreliable and transient intelligence results in a flimsy structure that can easily collapse and bury us in its ruins." What, in your opinion, is the role of intelligence today? BAMFORD: The role of intelligence is to provide a government with a third eye to see what is going on in places where it can't otherwise see; it has expanded tremendously from thirty years ago when the concentration was on human intelligence. -

Enclosed Is the Header; the Next Three Posts Contain the 517K Flat-Text of the "1984" Polemic
Enclosed is the header; the next three posts contain the 517K flat-text of the "1984" polemic. For hardcore details on ECHELON, see Part 1 from 'Wild Conspiracy Theory' through the end of Part 1. ---guy ****************************************************************************** An Indictment of the U.S. Government and U.S. Politics Cryptography Manifesto ---------------------- By [email protected] 7/4/97-M version "The law does not allow me to testify on any aspect of the National Security Agency, even to the Senate Intelligence Committee" ---General Allen, Director of the NSA, 1975 "You bastards!" ---guy ****************************************************************************** This is about much more than just cryptography. It is also about everyone in the U.S.A. being fingerprinted for a defacto national ID card, about massive illegal domestic spying by the NSA, about the Military being in control of key politicians, about always being in a state of war, and about cybernetic control of society. ****************************************************************************** Part 1: Massive Domestic Spying via NSA ECHELON ---- - ------- -------- ------ --- --- ------- o The NSA Admits o Secret Court o Wild Conspiracy Theory o Over the Top o BAM-BAM-BAM o Australian ECHELON Spotted o New Zealand: Unhappy Campers Part 2: On Monitoring and Being Monitored ---- - -- ---------- --- ----- --------- o On Monitoring - Driver's Seat - Five Months Statistics - The FBI Investigations - I Can See What You Are Thinking - Why I Monitor o On Being -

United States District Court Eastern District of Michigan Southern Division
UNITED STATES DISTRICT COURT EASTERN DISTRICT OF MICHIGAN SOUTHERN DIVISION AMERICAN CIVIL LIBERTIES UNION; AMERICAN CIVIL LIBERTIES UNION FOUNDATION; AMERICAN CIVIL LIBERTIES Case No. 2:06-cv-10204 UNION OF MICHIGAN; COUNCIL ON AMERICAN-ISLAMIC RELATIONS; COUNCIL Hon. Anna Diggs Taylor ON AMERICAN-ISLAMIC RELATIONS MICHIGAN; GREENPEACE, INC.; NATIONAL ASSOCIATION OF CRIMINAL DEFENSE LAWYERS; JAMES BAMFORD; LARRY DIAMOND; CHRISTOPHER HITCHENS; TARA MCKELVEY; and BARNETT R. RUBIN, Plaintiffs, v. NATIONAL SECURITY AGENCY / CENTRAL SECURITY SERVICE; and LIEUTENANT GENERAL KEITH B. ALEXANDER, in his official capacity as Director of the National Security Agency and Chief of the Central Security Service, Defendants. Larry J. Saylor (P28165) Peter T. Barbur (Admission Pending) MILLER, CANFIELD, PADDOCK AND STONE, PLC CRAVATH, SWAINE & MOORE LLP 150 West Jefferson, Suite 2500 Worldwide Plaza Detroit, Michigan 48226 825 Eighth Avenue (313) 963-6420 New York, NY 10019 [email protected] (212) 474-1000 Sidney S. Rosdeitcher (Admission pending) Attorneys for Amicus Curiae The Association Chair, Committee on Civil Rights of the Bar of the City of New York THE ASSOCIATION OF THE BAR OF THE CITY OF NEW YORK 1285 Avenue of the Americas New York, NY 10019-6064 (212) 373-3238 MEMORANDUM OF LAW OF AMICUS CURIAE THE ASSOCIATION OF THE BAR OF THE CITY OF NEW YORK IN SUPPORT OF PLAINTIFFS’ MOTION FOR PARTIAL SUMMARY JUDGMENT TABLE OF CONTENTS Page TABLE OF AUTHORITIES……………………………………………………………………... ii I. STATEMENT OF INTEREST OF AMICUS CURIAE. ....................................................1 II. SUMMARY OF ARGUMENT...........................................................................................2 III. THE RELEVANT BACKGROUND..................................................................................3 IV. THE NSA SURVEILLANCE PROGRAM IMPERMISSIBLY IMPEDES ATTORNEY-CLIENT COMMUNICATIONS IN VIOLATION OF THE FIRST AND SIXTH AMENDMENTS...........................................................................................4 A. -

Against Authority
AGAINST AUTHORITY Freedom and The Rise of the Surveillance States by John Twelve Hawks for Thomas Pynchon ©2014 by John Twelve Hawks. All Rights Reserved. A LITTLE BOY IN A ROOM OF MIRRORS Both dogs and humans know when we’ve been caged. We sense instinctually when some other person—or an institution—has the power to direct or control our lives. And our first awareness of this reality occurs at an early age. The older kids on the schoolyard are bigger and stronger. They have the power to knock us down and tell us what to do. When I was growing up in the 1950s, I was quite aware of my own powerlessness. I couldn’t tell anyone what to do—not even a first grader. Although my brain was crammed with a great many words, I had a terrible stutter and couldn’t get the words out. Everyone in my elementary school class laughed when I struggled to speak, and sometimes even my teacher had to conceal her smile. By the time I was eight years old, I started to believe that a demon with a perverse sense of humor was in charge of my lips and tongue. On some days, he was a lazy demon, and I could talk on the phone or answer questions in class. Then the demon would get annoyed with me and I would spit and sputter over every word. On Sundays my family attended a Scotch Presbyterian church headed by a conservative pastor who preached about infant damnation. I was confused about the power of baptism, but I definitely understood the concept of hell.