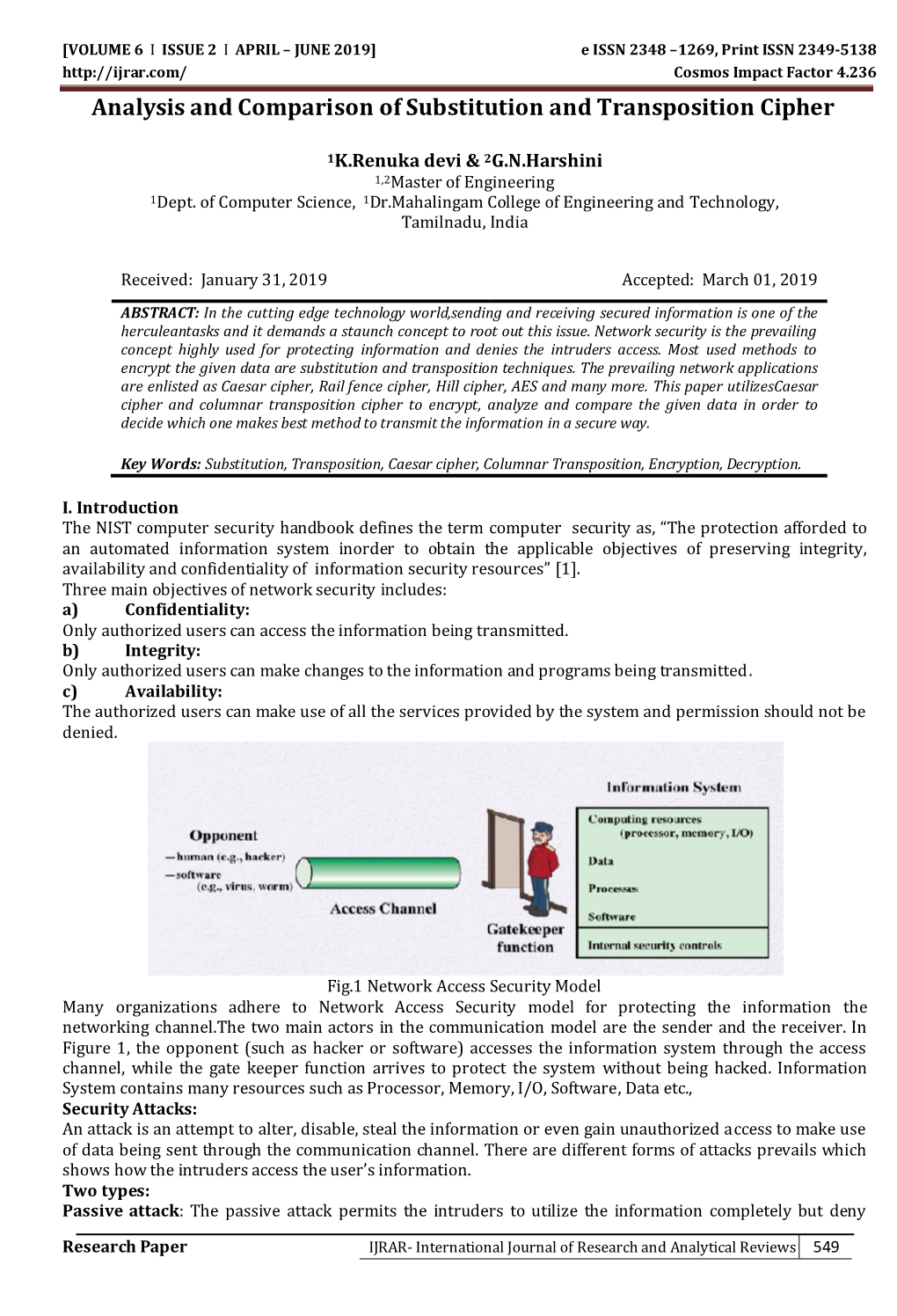
Analysis and Comparison of Substitution and Transposition Cipher
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Cipher Based on the Random Sequence of Digits in Irrational Numbers
https://doi.org/10.48009/1_iis_2016_14-25 Issues in Information Systems Volume 17, Issue I, pp. 14-25, 2016 A CIPHER BASED ON THE RANDOM SEQUENCE OF DIGITS IN IRRATIONAL NUMBERS J. L. González-Santander, [email protected], Universidad Católica de Valencia “san Vicente mártir” G. Martín González. [email protected], Universidad Católica de Valencia “san Vicente mártir” ABSTRACT An encryption method combining a transposition cipher with one-time pad cipher is proposed. The transposition cipher prevents the malleability of the messages and the randomness of one-time pad cipher is based on the normality of "almost" all irrational numbers. Further, authentication and perfect forward secrecy are implemented. This method is quite suitable for communication within groups of people who know one each other in advance, such as mobile chat groups. Keywords: One-time Pad Cipher, Transposition Ciphers, Chat Mobile Groups Privacy, Forward Secrecy INTRODUCTION In cryptography, a cipher is a procedure for encoding and decoding a message in such a way that only authorized parties can write and read information about the message. Generally speaking, there are two main different cipher methods, transposition, and substitution ciphers, both methods being known from Antiquity. For instance, Caesar cipher consists in substitute each letter of the plaintext some fixed number of positions further down the alphabet. The name of this cipher came from Julius Caesar because he used this method taking a shift of three to communicate to his generals (Suetonius, c. 69-122 AD). In ancient Sparta, the transposition cipher entailed the use of a simple device, the scytale (skytálē) to encrypt and decrypt messages (Plutarch, c. -

A Hybrid Cryptosystem Based on Vigenère Cipher and Columnar Transposition Cipher
International Journal of Advanced Technology & Engineering Research (IJATER) www.ijater.com A HYBRID CRYPTOSYSTEM BASED ON VIGENÈRE CIPHER AND COLUMNAR TRANSPOSITION CIPHER Quist-Aphetsi Kester, MIEEE, Lecturer Faculty of Informatics, Ghana Technology University College, PMB 100 Accra North, Ghana Phone Contact +233 209822141 Email: [email protected] / [email protected] graphy that use the same cryptographic keys for both en- Abstract cryption of plaintext and decryption of cipher text. The keys may be identical or there may be a simple transformation to Privacy is one of the key issues addressed by information go between the two keys. The keys, in practice, represent a Security. Through cryptographic encryption methods, one shared secret between two or more parties that can be used can prevent a third party from understanding transmitted raw to maintain a private information link [5]. This requirement data over unsecured channel during signal transmission. The that both parties have access to the secret key is one of the cryptographic methods for enhancing the security of digital main drawbacks of symmetric key encryption, in compari- contents have gained high significance in the current era. son to public-key encryption. Typical examples symmetric Breach of security and misuse of confidential information algorithms are Advanced Encryption Standard (AES), Blow- that has been intercepted by unauthorized parties are key fish, Tripple Data Encryption Standard (3DES) and Serpent problems that information security tries to solve. [6]. This paper sets out to contribute to the general body of Asymmetric or Public key encryption on the other hand is an knowledge in the area of classical cryptography by develop- encryption method where a message encrypted with a reci- ing a new hybrid way of encryption of plaintext. -

Grade 6 Math Circles Cryptography Solutions Atbash Cipher Caesar Cipher
Faculty of Mathematics Centre for Education in Waterloo, Ontario N2L 3G1 Mathematics and Computing Grade 6 Math Circles November 5/6 2019 Cryptography Solutions Hello World Khoor Zruog Hello Zruog Khoor Khoor Zruog World 1. Person A encrypts plaintext 2. Person B receives ciphertext 3. Person B decrypts ciphertext back into ciphertext into plaintext Atbash Cipher Examples 1. Encrypt \Math Circles" using the Atbash cipher. Nzgs Xrixovh 2. Decrypt \ORLM PRMT" using the Atbash cipher. LION KING Caesar Cipher Examples: Encrypt or decrypt the following messages using the shift number given in parentheses: a) Welcome to Math Circles! (5) Bjqhtrj yt Rfym Hnwhqjx! plaintext A B C D E F G H I J K L M N O P Q R S T U V W X Y Z ciphertext F G H I J K L M N O P Q R S T U V W X Y Z A B C D E 1 b) Ljw hxd anjm cqrb? (9) Can you read this? plaintext A B C D E F G H I J K L M N O P Q R S T U V W X Y Z ciphertext J K L M N O P Q R S T U V W X Y Z A B C D E F G H I c) What if I did a Caesar Shift of 26 units on \Welcome to Math Circles!"? A Caesar shift of 26 would be shifting by the length of the alphabet. For example I would be shifting A 26 letters to the right. -

Breaking Transposition Cipher with Genetic Algorithm
Breaking Transposition Cipher with Genetic Algorithm C.Obi Reddy, National University of Singapore(NUS), ECE Department, [email protected] Abstract: In recent years a number of example total number of letters is 20 optimisation algorithms have emerged which is regular case with the key order of which have proven to be effective in 5. If the plain text is irregular then solving a variety of NP-complete padding of X is done at the tail of the text problems. In this paper an example the to make it regular. kind in cryptanalysis, breaking of Encryption of plain text is done as follows transposition cipher using a heuristic genetic algorithm is presented. Regular: Plain 1 2 3 4 5 Introduction: Text In the Brute Force attack the attacker Key 1 4 2 5 3 tries every possible (k! Keys) key on a T H I S I piece of cipher text until an intelligible S A S I M translation into plaintext is obtained. P L E M E Many types of classical ciphers exist, S S A G E although most fall into one of two broad categories: substitution ciphers and Cipher Text: TSPS ISEA IMEE HALS SIMG transposition ciphers. In the former one, every plaintext character is substituted by Irregular: a cipher character, using a substitution Plain 1 2 3 4 5 alphabet, and in the latter one, plaintext Text characters are permuted using a Key 1 4 2 5 3 predetermined permutation. T H I S I S A S I M Transposition cipher works by breaking P L E M E the plain text in to fixed number of blocks S S A G E and then shuffling the characters in each block according to the agreed key K. -

Lecture 2: Classical Cryptography
Lecture 2: Classical Cryptography Data and Information Management: ELEN 3015 School of Electrical and Information Engineering, University of the Witwatersrand Introduction Monoalphabetic Cipher - Frequency analysis Classical Ciphers Other Substitution Ciphers Transposition ciphers Stream vs Block Enciphering 1. Homework hqfubswlrq lv d phdqv ri dwwdlqlqj vhfxuh frpsxwdwlrq ryhu lqvhfxuh fkdqqhov eb xvlqj hqfubswlrq zh glvjxlvh wkh phvvdjh vr wkdw hyhq li wkh wudqvplvvlrq lv glyhuwhg wkh phvvdjh zloo qrw eh uhyhdohg 1. Monoalphabetic Cipher - Frequency analysis Do a frequency analysis Letter distribution of English language is fixed (for a large body of text) Tables of letter distribution For instance, most commonly used letter is \e" 1. Monoalphabetic Cipher - Frequency analysis 1. Monoalphabetic Cipher - Answer ENCRYPTION IS A MEANS OF ATTAINING SECURE COMMUNICATION OVER INSECURE CHANNELS BY USING ENCRYPTION WE DISGUISE THE MESSAGE SO THAT EVEN IF THE TRANSMISSION IS DIVERTED THE MESSAGE WILL NOT BE REVEALED 2. Classical Ciphers How do we increase security of the monoalphabetic cipher? 3. Polyalphabetic ciphers Use more than one alphabetic substitution to flatten the frequency distribution Combine substitutions that are high with those that are low Eg use: • P1(a) = (a*3)mod26 • P2(a) = ((5*a)+13)mod26 3. Polyalphabetic ciphers Cipher I: ABCDEFG ::: STUVWXYZ a d g j m p s ::: c f i l o r u x Cipher II: ABCDEFG ::: STUVWXYZ n s x c h m r ::: z e j o t y d i 3. Polyalphabetic ciphers - Frequency distribution 3. Vigenere tables a b c d e f ::: t u v w x y z π A a b c d e f ::: t u v w x y z 0 B b c d e f g ::: u v w x y z a 1 C c d e f g h ::: v w x y z a b 2 . -

Transposition Cipher in Cryptography, a Transposition Cipher Is a Method of Encryption by Which the Positions Held by Units of P
Transposition cipher In cryptography, a transposition cipher is a method of encryption by which the positions held by units of plaintext (which are commonly characters or groups of characters) are shifted according to a regular system, so that the ciphertext constitutes a permutation of the plaintext. That is, the order of the units is changed. Mathematically a bijective function is used on the characters' positions to encrypt and an inverse function to decrypt. Following are some implementations. Contents • 1 Rail Fence cipher • 2 Route cipher • 3 Columnar transposition • 4 Double transposition • 5 Myszkowski transposition • 6 Disrupted transposition • 7 Grilles • 8 Detection and cryptanalysis • 9 Combinations • 10 Fractionation Rail Fence cipher The Rail Fence cipher is a form of transposition cipher that gets its name from the way in which it is encoded. In the rail fence cipher, the plaintext is written downwards on successive "rails" of an imaginary fence, then moving up when we get to the bottom. The message is then read off in rows. For example, using three "rails" and a message of 'WE ARE DISCOVERED. FLEE AT ONCE', the cipherer writes out: W . E . C . R . L . T . E . E . R . D . S . O . E . E . F . E . A . O . C . A . I . V . D . E . N . Then reads off: WECRL TEERD SOEEF EAOCA IVDEN (The cipherer has broken this ciphertext up into blocks of five to help avoid errors.) Route cipher In a route cipher, the plaintext is first written out in a grid of given dimensions, then read off in a pattern given in the key. -

A Complete Bibliography of Publications in Cryptologia
A Complete Bibliography of Publications in Cryptologia Nelson H. F. Beebe University of Utah Department of Mathematics, 110 LCB 155 S 1400 E RM 233 Salt Lake City, UT 84112-0090 USA Tel: +1 801 581 5254 FAX: +1 801 581 4148 E-mail: [email protected], [email protected], [email protected] (Internet) WWW URL: http://www.math.utah.edu/~beebe/ 04 September 2021 Version 3.64 Title word cross-reference 10016-8810 [?, ?]. 1221 [?]. 125 [?]. 15.00/$23.60.0 [?]. 15th [?, ?]. 16th [?]. 17-18 [?]. 18 [?]. 180-4 [?]. 1812 [?]. 18th (t; m)[?]. (t; n)[?, ?]. $10.00 [?]. $12.00 [?, ?, ?, ?, ?]. 18th-Century [?]. 1930s [?]. [?]. 128 [?]. $139.99 [?]. $15.00 [?]. $16.95 1939 [?]. 1940 [?, ?]. 1940s [?]. 1941 [?]. [?]. $16.96 [?]. $18.95 [?]. $24.00 [?]. 1942 [?]. 1943 [?]. 1945 [?, ?, ?, ?, ?]. $24.00/$34 [?]. $24.95 [?, ?]. $26.95 [?]. 1946 [?, ?]. 1950s [?]. 1970s [?]. 1980s [?]. $29.95 [?]. $30.95 [?]. $39 [?]. $43.39 [?]. 1989 [?]. 19th [?, ?]. $45.00 [?]. $5.95 [?]. $54.00 [?]. $54.95 [?]. $54.99 [?]. $6.50 [?]. $6.95 [?]. $69.00 2 [?, ?]. 200/220 [?]. 2000 [?]. 2004 [?, ?]. [?]. $69.95 [?]. $75.00 [?]. $89.95 [?]. th 2008 [?]. 2009 [?]. 2011 [?]. 2013 [?, ?]. [?]. A [?]. A3 [?, ?]. χ [?]. H [?]. k [?, ?]. M 2014 [?]. 2017 [?]. 2019 [?]. 20755-6886 [?, ?]. M 3 [?]. n [?, ?, ?]. [?]. 209 [?, ?, ?, ?, ?, ?]. 20th [?]. 21 [?]. 22 [?]. 220 [?]. 24-Hour [?, ?, ?]. 25 [?, ?]. -Bit [?]. -out-of- [?, ?]. -tests [?]. 25.00/$39.30 [?]. 25.00/839.30 [?]. 25A1 [?]. 25B [?]. 26 [?, ?]. 28147 [?]. 28147-89 000 [?]. 01Q [?, ?]. [?]. 285 [?]. 294 [?]. 2in [?, ?]. 2nd [?, ?, ?, ?]. 1 [?, ?, ?, ?]. 1-4398-1763-4 [?]. 1/2in [?, ?]. 10 [?]. 100 [?]. 10011-4211 [?]. 3 [?, ?, ?, ?]. 3/4in [?, ?]. 30 [?]. 310 1 2 [?, ?, ?, ?, ?, ?, ?]. 312 [?]. 325 [?]. 3336 [?, ?, ?, ?, ?, ?]. affine [?]. [?]. 35 [?]. 36 [?]. 3rd [?]. Afluisterstation [?, ?]. After [?]. Aftermath [?]. Again [?, ?]. Against 4 [?]. 40 [?]. 44 [?]. 45 [?]. 45th [?]. 47 [?]. [?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?]. Age 4in [?, ?]. [?, ?]. Agencies [?]. Agency [?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?]. -

A New Algorithm Combining Substitution Transposition Cipher
Project Omar Hesham Ahmed Ali A New Algorithm Combining Substitution Omar Nabil Youssef essam Transposition Cipher Techniques for Secure Karim Ahmed Communication Motivation The proposed Cipher Omar Hesham Techniques Ahmed Ali Encryption Omar Nabil Decryption Youssef essam Karim Ahmed Results Conclusions COMM1003:Information Theory Communications Engineering Department Information Engineering and Technology Faculty The German University in Cairo April 12th, 2018 1 / 24 Overview Project Omar Hesham Ahmed Ali 1 Motivation Omar Nabil Youssef essam Karim Ahmed 2 The proposed Cipher Techniques Motivation The proposed Cipher 3 Encryption Techniques Encryption 4 Decryption Decryption Results 5 Results Conclusions 6 Conclusions 2 / 24 Motivation Project Omar Hesham In today’s world of communication, the maintenance of the security, Ahmed Ali Omar Nabil confidentiality and integrity of the data is a big challenge. Youssef essam Cryptography is one such activity that ensures the secure transmission Karim Ahmed of data. Motivation It converts the data or message (plain text) into a non-readable form The proposed Cipher Techniques (cipher text) with the help of an algorithm and key which known to sender and receiver only. Encryption Decryption Results Conclusions 3 / 24 Motivation Project Omar Hesham The transmission of message or information is over an insecure channel as Ahmed Ali cryptography retain authentication, integrity and non repudiation Omar Nabil Youssef essam This message ‘Cipher Text’ is transmitted at receiver’s end where there the -

Grade 6 Math Circles Cryptography Introduction to Cryptography
Faculty of Mathematics Centre for Education in Waterloo, Ontario N2L 3G1 Mathematics and Computing Grade 6 Math Circles October 4 & 5, 2016 Cryptography Introduction to Cryptography Cryptography is the study of hidden writing or reading and writing secret messages or codes. The word cryptography comes from the Greek word kryptos (κρυτ&) meaning hid- den and graphein (γραφω) meaning writing. Before we get any further, let's learn some terminology: Plaintext: The original message or information the sender wants to encode or hide Encryption: The process of encrypting plaintext such that only authorized parties, such as the sender and receiver, can read it Ciphertext: The encrypted message of the plaintext that was encrypted using a cipher (the method of performing encryption) Decryption: The process of decoding ciphertext back into its original plaintext Hello World Khoor Zruog Hello Zruog Khoor Khoor Zruog World 1. Person A encrypts plaintext 2. Person B receives ciphertext 3. Person B decrypts ciphertext back into ciphertext into plaintext 1 Rail Fence Cipher Let's warm up with an easy cipher. With the rail fence cipher, we will be transposing, or changing the position of the letters in a message. To transpose a message, we need a key number and we will need to write each letter of the message up and down the rail fence. Here is an example of how the cipher works: Suppose the message is TURTLES ARE SLOW and our key number is 3. Now imagine a rail fence with 3 rails. By reading off the rows of the rail fence, the resulting ciphertext is TLRO UTEAELW RSS. -

Cryptography and Network Security Module: Transposition Cipher And
e-PGPathshala Subject : Computer Science Paper: Cryptography and Network Security Module: Transposition Cipher and Cryptanalysis Module No: CS/CNS/4 Quadrant 1 – e-text Cryptography and Network Security Module 4- Transposition Cipher and Cryptanalysis Learning Objectives ➢ To know the substitution cipher in classical cryptography ➢ To learn about the mono alphabetic substitution cipher ➢ To learn about the poly alphabetic substitution cipher ➢ Cryptanalysis of Substitution cipher 4.1 Introduction Cryptanalysis is the study of analyzing information systems in order to study the hidden aspects of the systems. Cryptanalysis is used to breach cryptographic security systems and gain access to the contents of encrypted messages, even if the cryptographic key is unknown. In addition to mathematical analysis of cryptographic algorithms, cryptanalysis includes the study of side-channel attacks that do not target weaknesses in the cryptographic algorithms themselves, but instead exploit weaknesses in their implementation. 4.2 Transposition Ciphers ➢ In transposition ciphers, we transpose (scramble) the plaintext letters Transposition (permutation) means rearranging the order of appearance of the elements of the plaintext. In other words cipher text constitutes permutation of plain text. In general transposition depends on the length of the text and it is aperiodic. – The scrambled text is the ciphertext – The transposition is the key ➢ Corresponds to Shannon’s principle of diffusion( property that spreads statistic properties of text all over the text preventing statistic analysis) – This idea is widely used in modern ciphers 4.3 Scytale ➢ One of the oldest cryptography tools was a Spartan scytale , circa 500 BC. ➢ Sender and recipient each had a rod of exactly the same radius. -

2. Classic Cryptography Methods 2.1. Spartan Scytale. One of the Oldest Known Examples Is the Spartan Scytale (Scytale /Skɪtəl
2. Classic Cryptography Methods 2.1. Spartan scytale. One of the oldest known examples is the Spartan scytale (scytale /skɪtəli/, rhymes with Italy, a baton). From indirect evidence, the scytale was first mentioned by the Greek poet Archilochus who lived in the 7th century B.C. (over 2500 years ago). The ancient Greeks, and the Spartans in particular, are said to have used this cipher to communicate during military campaigns.Sender and recipient each had a cylinder (called a scytale) of exactly the same radius. The sender wound a narrow ribbon of parchment around his cylinder, then wrote on it lengthwise. After the ribbon is unwound, the writing could be read only by a person who had a cylinder of exactly the same circumference. The following table illustrate the idea. Imagine that each column wraps around the dowel one time, that is that the bottom of one column is followed by the top of the next column. Original message: Kill king tomorrow midnight Wrapped message: k i l l k i n g t o m o r r o w m i d n i g h t Encoded message: ktm ioi lmd lon kri irg noh gwt The key parameter in using the scytale encryption is the number of letters that can be recorded on one wrap ribbon around the dowel. Above the maximum was 3, since there are 3 rows in the wrapped meassage. The last row was padded with blank spaces before the message was encoded. We'll call this the wrap parameter. If you don't know the wrap parameter you cannot decode a message. -

Section 2: Basic Cryptography
In this section we learn about cryptography. Reference: [Mark Stamp] Chapter 2 46 You can use a password to protect your computer; however, once the data leaves your computer and goes through a public data network (such as Internet), what can you do to protect it? Answer: data security by cryptography Data sent over public channels is subject to being intercepted and read by others. Encrypting data can keep data confidential even if read while on public channels. Data sent over public channels may also be modified during transit by an attacker or corrupted accidently. Encrypted data may also be modified or corrupted so encryption doesn’t necessarily solve that problem. 47 Objective of this section are: to learn the concept of data encryption, decryption, relationship between key size and data security. 48 49 Figure shows encryption. Encryption is the process of converting plaintext to the ciphertext. Decryption is the opposite: conversion of the ciphertext back to plaintext. A cryptographic system may use keys (string of bits) for encryption and decryption. In practice, the encryption method and decryption method should be public. The decryption key may be kept confidential for ensuring data security. 50 Cryptography may be used to setup a secure communication system. In symmetric key Cryptography, a single shared key may be used to encrypt and decrypt the message as shown in the above diagram. For security reasons, the key should be a secret known only by sender and receiver (i.e., the people who are authorized to read the message). Problem: how can sender and receiver agree on a key securely on the Internet? They need to share a key BEFORE they can encrypt messages to each other, but if one of them sends the key to the other over public channels, it‘s vulnerable to interception.