Towards Automated Configuration of Cloud Storage
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Building a Cloud-Enabled File Storage Infrastructure
F5 White Paper Building a Cloud-Enabled File Storage Infrastructure A cloud-enabled infrastructure can help your organization seamlessly integrate cloud storage and maximize cost savings, while also offering significant benefits to your traditional file storage environments. by Renny Shen Product Marketing Manager White Paper Building a Cloud-Enabled File Storage Infrastructure Contents Introduction 3 What Makes a Cloud? 3 Types of Cloud Storage 4 What Makes Cloud Storage Different? 4 Accessing Files Remotely over the Network 5 Accessing Files on Object-Based Storage 5 Unique Cost Structure 6 Where Clouds Make Sense 7 Fitting the Cloud into a Tiered Storage Framework 7 Expanding the Parameters for Tiering with the Cloud 8 Defining Cloud-Enabled 9 Integrating Different Types of Storage 10 Non-Disruptive File Migration 11 Automated Storage Tiering 11 Benefits of a Cloud-Enabled Infrastructure 12 Reduced Storage Costs 12 Reduced Backup Times and Costs 13 Reduced Operational Costs 13 The F5 Cloud Storage Model 13 Creating a Private Cloud 15 Conclusion 18 2 White Paper Building a Cloud-Enabled File Storage Infrastructure Introduction Cloud storage offers enterprise organizations the opportunity to bring constantly rising file storage costs and management burden under control. By moving appropriate types of files to the cloud, organizations can reduce not only the amount of storage capacity that they need to purchase, but also the operational overhead involved in managing it. In addition, the cloud enables storage capacity to be increased on demand, while charging organizations only for the amount of storage that is actually utilized. Cloud storage will bring many changes to the way enterprises manage storage. -

Acronis Backup 12.5
Acronis Backup 12.5 BEST PRACTICES Revision: 12/12/2019 Table of contents 1 Introduction ....................................................................................................................5 2 Acronis Backup components and architecture ..................................................................5 2.1 Resource usage calculator ......................................................................................................... 8 2.2 Licensing .................................................................................................................................... 9 2.2.1 Policy ................................................................................................................................................................ 9 2.2.2 License Server ................................................................................................................................................ 10 2.2.3 Using Standard and Advanced on one Management Server ..................................................................... 10 3 Single and isolated machines.......................................................................................... 11 3.1 Preparing for deployment .......................................................................................................11 3.1.1 Software requirements for single and isolated machines ......................................................................... 11 3.1.2 Hardware requirements and sizing ............................................................................................................. -

AWS Storage Gateway Fred Hutch - Partly Cloudy Conference
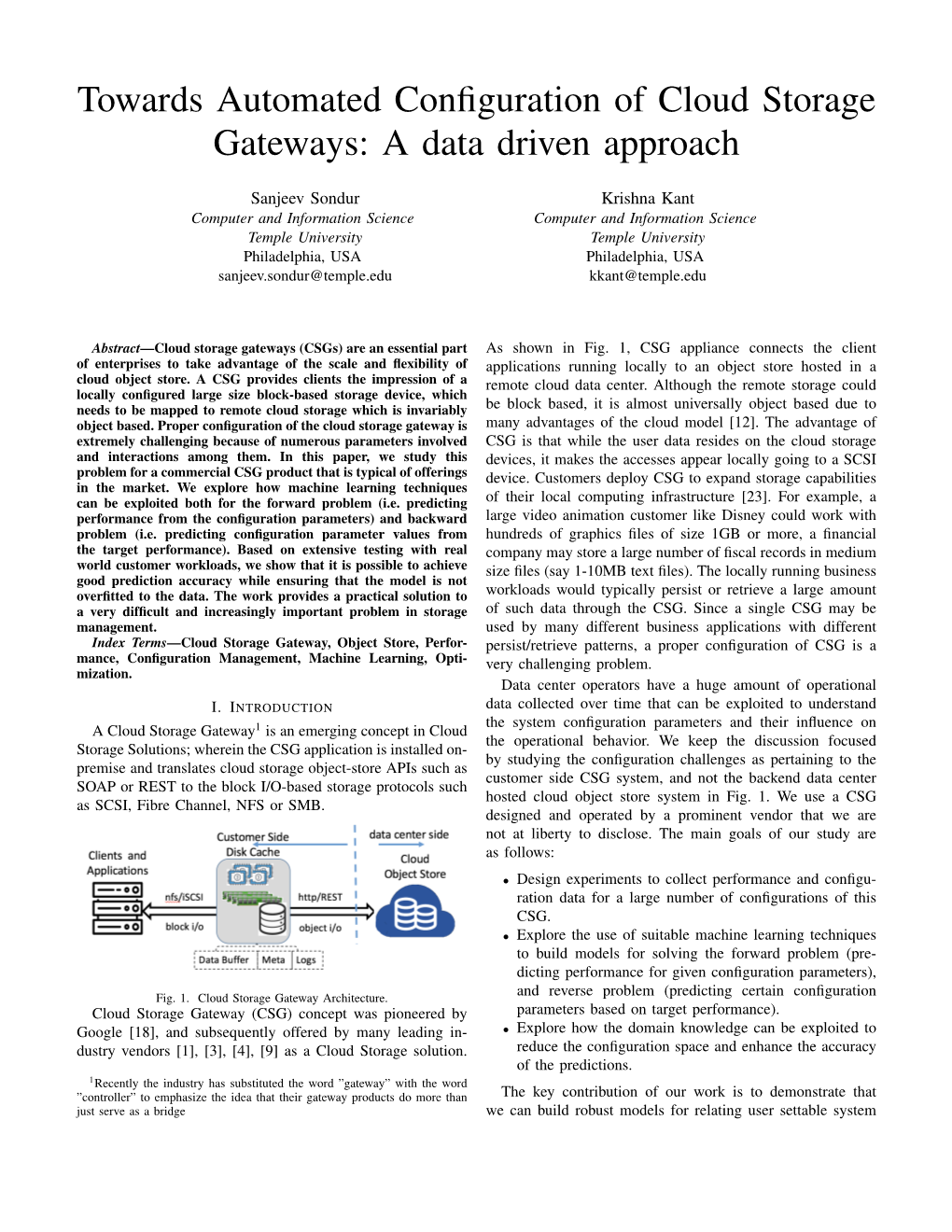
AWS Storage Gateway Fred Hutch - Partly Cloudy Conference Jeff Bartley | Storage Solutions Architect | [email protected] October 25th, 2018 © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Enabling a spectrum of hybrid use cases Analytics | File Services | Production Tiering | Data Processing Data Distribution | Backup | DR | Archive | Migration Amazon Amazon Amazon Amazon Amazon Amazon AWS Amazon EMR Athena S3 Glacier EBS EC2 Lambda CloudFront AWS Storage Gateway Enterprise Data Centers Remote Offices Research Sites Small-Medium Businesses Multimedia content File servers Databases App. servers Devices Users Backup servers © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. AWS Storage Gateway Family Hybrid storage service enabling applications to seamlessly use AWS storage File Gateway Store and access objects in Amazon S3 from file-based applications with local caching Volume Gateway Block storage on-premises backed by cloud storage with local caching, EBS snapshots, and clones Tape Gateway Drop-in replacement for physical tape infrastructure backed by cloud storage with local caching © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. AWS Storage Gateway Family Files Amazon S3 (NFS or SMB) AWS Storage Gateway Amazon EBS Volumes snapshots (iSCSI) HTTPS Gateway Service Amazon Glacier Tapes AWS Identity and Access (iSCSI VTL) AWS CloudTrail Management (IAM) Amazon AWS Key Management Service Customer Premises CloudWatch (AWS KMS) Gateway provides applications Native storage in AWS • Protocol conversion and device emulation • Objects in S3 (file) • Caching (read-through / write-back) • Snapshots in EBS (volume) • Optimized data transfer • Archives in Glacier (tape) © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. -

Hybrid Cloud Storage Products
Build aHybridStorageCloud services and possible pitfalls. This guide can help you make thosedecisions. services make pitfalls.Thisguidecanhelpyou andpossible products, ontheavailable choicesandeducate themselves tomake require users data bothofthesemethodsstoring ofusingthecloudforstorage; common way couldbecomethemost Combining publiccloudservices andon-premisesstorage VIRTUALIZATION CLOUD APPLICATION DEVELOPMENT NETWORKING STORAGE ARCHITECTURE DATA CENTER MANAGEMENT BUSINEss INTELLIGENCE/APPLICATIONS DISASTER RECOVERY/COMPLIANCE SECURITY S MOD HYBRID CLOUD 4 PROS A HYBRID CLOUD 3 S HYBRID CLOUD 2 NoT EDITor’s 1 Guide An Essential TILL HASW TORAG N E D CO PRODU E N E AK S SP C TS OTS E L EDITor’S NOTE 1 Building the Bridge: Making Hybrid Clouds a Reality IT managers who want to take advantage of com- awareness and bandwidth issues are among the items Home petitive cloud pricing, and the promise of elasticity that will factor into the decision process. While pub- that comes with public clouds, will almost always be- lic cloud storage brings the potential for big savings, it Editor’s Note gin their journey to the cloud with a hybrid model. A also presents latency problems; private cloud storage hybrid cloud model is not only the most likely start- is limited to private data centers and it requires the IT Hybrid Cloud ing point for an organization, but it is also often the manager to guarantee scalability at a time when unprec- Storage Products framework they decide on as a lasting strategy. That’s edented volumes of unstructured data are produced. because it allows a combination of on-site cloud storage this Essential Guide to building a hybrid storage cloud Hybrid Cloud Pros and Cons and public cloud storage to accommodate varying needs offers sophisticated analysis, discusses hybrid cloud throughout an organization for data access and speed of storage models for various needs, and answers key Hybrid Cloud Model delivery. -

Cloud Storage Using Amazon Storage Gateway with Drobo Iscsi SAN
Drobo How-To Guide Cloud Storage Using Amazon Storage Gateway with Drobo iSCSI SAN The Amazon Web Services (AWS) Storage Gateway uses an on-premises virtual appliance to replicate a portion of your local Drobo iSCSI SAN (Drobo B1200i, left below, and Drobo B800i, right below) to cloud- based storage. This solution provides an option for redundant backup and disaster recovery in the cloud for critical data, particularly for users that may not have a secondary site with IT equipment. The AWS Storage Gateway is installed on a VMware host that is linked to an AWS account—providing an on-ramp to cloud storage. Volumes of up to 1TB in size (12 volumes per gateway maximum) are created and mounted by on-premises servers as iSCSI devices. Based on functionality available in the Beta version of AWS Storage Gateway, data written to your gateway-stored volumes is recorded on Drobo storage and asynchronously stored in Amazon S3 (Simple Storage Service) in the form of Amazon EBS (Elastic Block Store) snapshots. This guide provides the tested steps to sync data on Drobo iSCSI storage to the cloud for offsite backup using gateway-stored volumes. The information in this guide can be the foundation for leveraging other Amazon Web Services (AWS) for recovery in the cloud. For example, Amazon Route 53 service enables DNS updating so that users are pointed to the instance running in the cloud. It is also possible to create an Amazon EBS instance from an S3 backup, mount it with an Amazon EC2 instance, and restart the application completely from the cloud. -

Cloud Storage Gateway
Cloud Storage Gateway Overview Cloud Storage Gateway Overview Overview Product overview Cloud Storage Gateway (CSG) is a gateway that can be deployed in your IDC and on your Alibaba Cloud products. It uses Alibaba Cloud Object Storage Service (OSS) buckets as backend storage devices and provides on- and off-cloud applications with standard file services through the Network File System (NFS) and Common Internet File System (CIFS) protocol and block storage services through the Internet Small Computer Systems Interface (iSCSI) protocol. CSG supports two types of gateways: • File gateway File gateway uses OSS buckets as backend storage devices and maps the object directory structure of OSS buckets to the file system of Network Attached Storage (NAS). The CSG client can read and write all objects in an OSS bucket through the standard NFS and CIFS protocols. In addition, CSG provides higher bandwidth and lower latency, especially for the read/write performance of small files, and improves the compatibilities with the Portable Operating System Interface (POSIX) and third-party backup software. This type of gateway applies to enterprises with high performance and enterprise compatibility requirements. • Block gateway Block gateway creates storage volumes in OSS buckets and support block-level access through the iSCSI protocol. Local applications can access the volumes as the iSCSI targets. Block gateway provides the write-through and cache modes. In write-through mode, the data in block volumes is sliced and synchronized to the cloud. This mode applies to users who use high-speed links such as leased lines. In cache mode, ephemeral disks can be created for read/write acceleration and for asynchronization of data to the cloud. -

Technical Report
Technology Analysis Report Cloud Storage Gateways Kiran Srinivasan, ATG, CTO Office Shwetha Krishnan, ATG, CTO Office Monika Doshi, SPT, CTO Office Chris Busick, V-series product group Sonali Sahu, V-series product group Kaladhar Voruganti, ATG, CTO Office TABLE OF CONTENTS 1 Style examples (HEADING LEVEL 1, Arial bold 13 pt blue) Error! Bookmark not defined. 1.1 subsection (heading level 2, arial bold 11 pt black) Error! Bookmark not defined. 1.2 subsection (heading level 2) Error! Bookmark not defined. 1.3 subsection (heading level 2) Error! Bookmark not defined. 1.4 subsection (heading level 2) Error! Bookmark not defined. 2 Template use Error! Bookmark not defined. 2.1 Applying paragraph styles Error! Bookmark not defined. 2.2 Adding Graphics Error! Bookmark not defined. 2.3 Adding New Tables Error! Bookmark not defined. 2.4 styling Unformatted Tables Error! Bookmark not defined. 3 Appendices Error! Bookmark not defined. 3.1 Appendix title Error! Bookmark not defined. 3.2 Appendix title Error! Bookmark not defined. 4 References Error! Bookmark not defined. 5 Styles lists Error! Bookmark not defined. LIST OF TABLES Table 1) Example NetApp table with caption. ............................................... Error! Bookmark not defined. Table 2) Single-use styles............................................................................. Error! Bookmark not defined. Table 3) Authoring styles. ............................................................................. Error! Bookmark not defined. LIST OF FIGURES Figure 1) Insert name -

What Are the Benefits of Cloud Computing?
What is Cloud Computing? Cloud computing is essentially infrastructure as a service. Using resources from distributed servers/computers, cloud computing frees you from the configuration of local servers. The cloud is another movement towards making computing a service that can be adjusted based on the needs of a business. For example, for a business in retail that might need to utilize a large number of servers during the holiday seasons, but not nearly as many after the holiday seasons, cloud computing is helpful by allowing the business to aggregate server usage based on their needs. Cloud computing has been gaining momentum, particularly in the SaaS environment. Organizations are quickly realizing the value in cutting costs through monthly subscriptions to software, rather than outright purchasing it and having it become obsolete. When newer versions of software become available, companies need to repurchase and sometimes increase the amount of infrastructure needed to support the new software. With cloud- hosted services, it is possible to utilize enterprise-level software through subscription, without worrying about the cost of infrastructure or upgrading to the latest version of software.. What are the benefits of Cloud Computing? Cloud Computing is helpful in multiple ways. The primary benefits are that: 1) Time to market is significantly reduced. 2) Overall cost savings in maintenance costs from having business-owned servers to maintain. Cloud computing services also generally have a much higher guarentee for up- time that a smaller company running its own servers usually cannot match. 3) Organizations can cut software licensing and administrative costs through utilizing online services in the cloud, such as SharePoint, Exchange Server, and Office Communications Server. -

QNAP QTS 4.4.1 FILE/BLOCK CLOUD GATEWAY the FAST LANE CONNECTING ON-PREMISES and CLOUD DATA STORAGE Digital Transformation
QTS 4.4.1 Cloud Storage Digital Transformation Gateway Outline 1 Demand And Problem of Hybrid Cloud Solution 2 QNAP’s Cloud Storage Gateway 3 File-based Cloud Gateway – HybridMount 4 Block-based Cloud Gateway – VJBOD Cloud 5 Use Scenario 6 Recommended NAS Models Hot data storage trends More hot data is accessed from the cloud • 80%+ organizations has hybrid-cloud environment and • Most businesses use multiple clouds More data is stored on the cloud • Backup, remote backup to the cloud • Cloud computing services The demand for cloud data backup Low latency access Integrate multiple 1 • Near-LAN access speeds 2 clouds • Use the same • Access different clouds using applications and standard the same mothod protocols Efficient Management Cost Saving 3 • Centrally manage multi clouds 4 • Centrally manage access • Reduce cloud storage used permission settings • Minimize network usage Benefits of cloud storage gateway Support more access protocols Near-LAN access speed Featuring protocol conversion, the Keep the frequently-accessed data in NAS Cloud Gateway allows you to access the cache space, allowing you to enjoy low-latency cloud storage using standard SMB, FTP, NFS, access to cached cloud files with near-LAN AFP, iSCSI protocols. Windows, MAC, Linux speeds via the Internet. users can all easily access the cloud. Cloud usage efficiency Minimize network usage cost Cloud Storage Gateway fully integrates with When many users need to access the same public cloud storage to centrally store data file, they can access the cached file instead of generated from multiple locations with the each downloading a copy, greatly reducing flexibility and convenience of cloud storage network usage charges. -

Storage Spectacular!
content provided by STORAGE SPECTACULAR! A comprehensive look at virtual storage from Virtualization Review and Redmond magazine, plus a Storage Buyer’s Guide. > The Storage Infrastruggle Page 1 > Do You Really Need Storage Management Software? Page 17 > Storage: Virtualized vs. Software-DefinedPage 27 > Storage Disruptors Page 36 > In the Cloud Era, the Era of Convergence Is Upon Us Page 49 > The 2014 Virtualization Review Buyers Guide Page 56 SPONSORS Storage Spectacular The Storage Infrastruggle Vendors are battling for the future of your storage spend, but are they sidestepping the key drivers of storage cost? By Jon Toigo hile touting “new,” flash-heavy “server-side” topologies and so-called “software-defined architec- tures” as evolutionary replacements for the “legacy” W SANs and NAS appliances that companies deployed in their previous refresh cycles, the industry continues to ignore the more fundamental drivers of storage inefficiency and cost: lack of management both of infrastructure and of data. 1 Storage Spectacular You would think from news reports that the storage industry was on its last legs. Vendor revenues from sales of everything from hard disk drives to external storage arrays, storage area networks (SANs) and network attached storage (NAS) appliances are either flat or declining ever so slightly. Seagate and Western Digital have hit a patch of dol- drums in which the trends of prior years—the doubling of drive capacities every 18 months and the halving of cost per GB every year—have frozen in their tracks. Even the redoubtable EMC, NetApp and IBM are experiencing purchasing slowdowns at customer shops that shouldn’t be happening if the capacity demand explosion that analysts say accompanies server virtualization is to be believed. -

Alibaba Cloud
AAlliibbaabbaa CClloouudd Alibaba Cloud 云存云储存网储关 网关 UUsseerr GGuuiiddee (O (nO-Pnr-ePmriesems)ises) Document Version: 20210510 Document Version: 20210510 User Guide (On-Premises)·Legal disc 云存储网关 laimer Legal disclaimer Alibaba Cloud reminds you t o carefully read and fully underst and t he t erms and condit ions of t his legal disclaimer before you read or use t his document . If you have read or used t his document , it shall be deemed as your t ot al accept ance of t his legal disclaimer. 1. You shall download and obt ain t his document from t he Alibaba Cloud websit e or ot her Alibaba Cloud- aut horized channels, and use t his document for your own legal business act ivit ies only. The cont ent of t his document is considered confident ial informat ion of Alibaba Cloud. You shall st rict ly abide by t he confident ialit y obligat ions. No part of t his document shall be disclosed or provided t o any t hird part y for use wit hout t he prior writ t en consent of Alibaba Cloud. 2. No part of t his document shall be excerpt ed, t ranslat ed, reproduced, t ransmit t ed, or disseminat ed by any organizat ion, company or individual in any form or by any means wit hout t he prior writ t en consent of Alibaba Cloud. 3. The cont ent of t his document may be changed because of product version upgrade, adjust ment , or ot her reasons. Alibaba Cloud reserves t he right t o modify t he cont ent of t his document wit hout not ice and an updat ed version of t his document will be released t hrough Alibaba Cloud-aut horized channels from t ime t o t ime. -

Hitachi Content Platform Architecture Fundamentals
WHITE PAPER Hitachi Content Platform Architecture Fundamentals Secure, Simple and Smart Web-Scale Object Storage Platform Delivers Superior Security, Efficiency and Interoperability By Hitachi Vantara June 2020 Contents Executive Summary 4 Introduction 5 Hitachi Vantara Content Portfolio Overview 5 Common Use Cases 7 Key HCP Values and Differentiators 9 Architecture Overview 10 Access Layer 10 Storage Layer 11 Load Balancing Layers 11 Search Layer 12 Global Access Topology and Multisite Consistency 12 Deployment Options 13 Flexible: Start Small, Scale Big 13 The Power of Shared Storage 15 Management 15 Management API and Programmatic Monitoring 16 System-Level Dashboards and Notifications 17 Tenant-Level Dashboards and Notifications 18 Chargeback Reporting 18 Object Storage Software Architecture 19 Object Container Structure 19 Store Objects 20 Read Objects 20 Open Protocols 20 HCP Data Services 21 Autonomic Tech Refresh (ATR) 22 HCP Replication Topologies and Content Fencing 23 2 Geodistributed Erasure Coding 24 Search 24 Multiple Metadata Annotations 25 Hardware Overview 25 Access Nodes (HCP G Nodes) 25 HCP S Series Storage 26 Extended Storage (NFS and Public Cloud) 27 Networking 28 Configurations Using Only HCP G Nodes 28 HCP SAN-Attached Configurations 29 Capacity Scaling With HCP S Node 30 HCP Racking Options 31 Security 32 System Availability and Data Integrity 33 Conclusion 33 Additional Resources 34 3 Executive Summary Organizations are swiftly assessing and adopting new technologies and information management practices to defend against and ultimately transcend digital disruptors that are emerging across every industry. Pressure is mounting from internal and external influences alike. IT is in the position to define and lead the digital transformation strategy for the organization.