Virtual Machines
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Running Telecom/TT-Link and Trafman Under Windows 7 (And Up) Using Dosbox
Running Telecom/TT-Link and Trafman under Windows 7 (and up) using DOSbox 3/31/2014 Documentation written for: Telecom/TT-Link V3.97 or later. TrafMan V6.43 or later. DOSbox V0.74 or later. COM/IP V4.9.5 or later. TrafMan & Telecom/TT-Link on Windows 7 Page 1 of 10 I. Introduction and Initial Emulator Setup Microsoft discontinued support for MS-DOS level programs starting with Windows 7. This has made the operation of Telecom/TT-Link and TrafMan on systems with a Windows 7 or later operating systems problematical, to say the least. However, it is possible to achieve functionality (with some limits) even on a Windows 7 computer by using what is known as a “DOS Emulator”. Emulator’s simulate the conditions of an earlier operating system on a later one. For example, one of the most common emulators is called DOSbox (http://sourceforge.net/projects/dosbox/ ) and it is available as a free download for both PC and Mac computers. DOSbox creates an artificial MS-DOS level environment on a Windows 7 computer. Inside this environment you can run most DOS programs, including TrafMan and Telecom/TT-Link. This document describes how to utilize the DOSbox emulator for running Telecom/TT-Link and TrafMan. It should be noted, however, that other emulators may also work and this document can serve as a guide for setting up and using similar DOS emulators as they are available. Initial DOSbox Emulator Setup: 1) Download the latest release of DOSbox (0.74 or later) to your PC and install it. -

Virtualization Technologies Overview Course: CS 490 by Mendel
Virtualization technologies overview Course: CS 490 by Mendel Rosenblum Name Can boot USB GUI Live 3D Snaps Live an OS on mem acceleration hot of migration another ory runnin disk alloc g partition ation system as guest Bochs partially partially Yes No Container s Cooperati Yes[1] Yes No No ve Linux (supporte d through X11 over networkin g) Denali DOSBox Partial (the Yes No No host OS can provide DOSBox services with USB devices) DOSEMU No No No FreeVPS GXemul No No Hercules Hyper-V iCore Yes Yes No Yes No Virtual Accounts Imperas Yes Yes Yes Yes OVP (Eclipse) Tools Integrity Yes No Yes Yes No Yes (HP-UX Virtual (Integrity guests only, Machines Virtual Linux and Machine Windows 2K3 Manager in near future) (add-on) Jail No Yes partially Yes No No No KVM Yes [3] Yes Yes [4] Yes Supported Yes [5] with VMGL [6] Linux- VServer LynxSec ure Mac-on- Yes Yes No No Linux Mac-on- No No Mac OpenVZ Yes Yes Yes Yes No Yes (using Xvnc and/or XDMCP) Oracle Yes Yes Yes Yes Yes VM (manage d by Oracle VM Manager) OVPsim Yes Yes Yes Yes (Eclipse) Padded Yes Yes Yes Cell for x86 (Green Hills Software) Padded Yes Yes Yes No Cell for PowerPC (Green Hills Software) Parallels Yes, if Boot Yes Yes Yes DirectX 9 Desktop Camp is and for Mac installed OpenGL 2.0 Parallels No Yes Yes No partially Workstati on PearPC POWER Yes Yes No Yes No Yes (on Hypervis POWER 6- or (PHYP) based systems, requires PowerVM Enterprise Licensing) QEMU Yes Yes Yes [4] Some code Yes done [7]; Also supported with VMGL [6] QEMU w/ Yes Yes Yes Some code Yes kqemu done [7]; Also module supported -

International Journal for Scientific Research & Development
IJSRD - International Journal for Scientific Research & Development| Vol. 2, Issue 02, 2014 | ISSN (online): 2321-0613 Virtualization : A Novice Approach Amithchand Sheety1 Mahesh Poola2 Pradeep Bhat3 Dhiraj Mishra4 1,2,3,4 Padmabhushan Vasantdada Patil Pratishthan’s College of Engineering, Eastern Express Highway, Near Everard Nagar, Sion-Chunabhatti, Mumbai-400 022, India. Abstract— Virtualization provides many benefits – greater as CPU. Although hardware is consolidated, typically efficiency in CPU utilization, greener IT with less power OS are not. Instead, each OS running on a physical consumption, better management through central server becomes converted to a distinct OS running inside environment control, more availability, reduced project a virtual machine. The large server can "host" many such timelines by eliminating hardware procurement, improved "guest" virtual machines. This is known as Physical-to- disaster recovery capability, more central control of the Virtual (P2V) transformation. desktop, and improved outsourcing services. With these 2) Consolidating servers can also have the added benefit of benefits, it is no wondered that virtualization has had a reducing energy consumption. A typical server runs at meteoric rise to the 2008 Top 10 IT Projects! This white 425W [4] and VMware estimates an average server paper presents a brief look at virtualization, its benefits and consolidation ratio of 10:1. weaknesses, and today’s “best practices” regarding 3) A virtual machine can be more easily controlled and virtualization. inspected from outside than a physical one, and its configuration is more flexible. This is very useful in I. INTRODUCTION kernel development and for teaching operating system Virtualization, in computing, is a term that refers to the courses. -

MX-19.2 Users Manual
MX-19.2 Users Manual v. 20200801 manual AT mxlinux DOT org Ctrl-F = Search this Manual Ctrl+Home = Return to top Table of Contents 1 Introduction...................................................................................................................................4 1.1 About MX Linux................................................................................................................4 1.2 About this Manual..............................................................................................................4 1.3 System requirements..........................................................................................................5 1.4 Support and EOL................................................................................................................6 1.5 Bugs, issues and requests...................................................................................................6 1.6 Migration............................................................................................................................7 1.7 Our positions......................................................................................................................8 1.8 Notes for Translators.............................................................................................................8 2 Installation...................................................................................................................................10 2.1 Introduction......................................................................................................................10 -

Download the Index
41_067232945x_index.qxd 10/5/07 1:09 PM Page 667 Index NUMBERS 3D video, 100-101 10BaseT Ethernet NIC (Network Interface Cards), 512 64-bit processors, 14 100BaseT Ethernet NIC (Network Interface Cards), 512 A A (Address) resource record, 555 AbiWord, 171-172 ac command, 414 ac patches, 498 access control, Apache web server file systems, 536 access times, disabling, 648 Accessibility module (GNOME), 116 ACPI (Advanced Configuration and Power Interface), 61-62 active content modules, dynamic website creation, 544 Add a New Local User screen, 44 add command (CVS), 583 address books, KAddressBook, 278 Administrator Mode button (KDE Control Center), 113 Adobe Reader, 133 AFPL Ghostscript, 123 41_067232945x_index.qxd 10/5/07 1:09 PM Page 668 668 aggregators aggregators, 309 antispam tools, 325 aKregator (Kontact), 336-337 KMail, 330-331 Blam!, 337 Procmail, 326, 329-330 Bloglines, 338 action line special characters, 328 Firefox web browser, 335 recipe flags, 326 Liferea, 337 special conditions, 327 Opera web browser, 335 antivirus tools, 331-332 RSSOwl, 338 AP (Access Points), wireless networks, 260, 514 aKregator webfeeder (Kontact), 278, 336-337 Apache web server, 529 album art, downloading to multimedia dynamic websites, creating players, 192 active content modules, 544 aliases, 79 CGI programming, 542-543 bash shell, 80 SSI, 543 CNAME (Canonical Name) resource file systems record, 555 access control, 536 local aliases, email server configuration, 325 authentication, 536-538 allow directive (Apache2/httpd.conf), 536 installing Almquist shells -

Challenges in Firmware Re-Hosting, Emulation, and Analysis
Challenges in Firmware Re-Hosting, Emulation, and Analysis CHRISTOPHER WRIGHT, Purdue University WILLIAM A. MOEGLEIN, Sandia National Laboratories SAURABH BAGCHI, Purdue University MILIND KULKARNI, Purdue University ABRAHAM A. CLEMENTS, Sandia National Laboratories System emulation and firmware re-hosting have become popular techniques to answer various security and performance related questions, such as, does a firmware contain security vulnerabilities or meet timing requirements when run on a specific hardware platform. While this motivation for emulation and binary analysis has previously been explored and reported, starting to either work or research in the field is difficult. To this end, we provide a comprehensive guide for the practitioner or system emulation researcher. We layout common challenges faced during firmware re-hosting, explaining successive steps and surveying common tools used to overcome these challenges. We provide classification techniques on five different axes, including emulator methods, system type, fidelity, emulator purpose, and control. These classifications and comparison criteria enable the practitioner to determine the appropriate tool for emulation. We use our classifications to categorize popular works in the field and present 28 common challenges faced when creating, emulating and analyzing a system, from obtaining firmwares to post emulation analysis. CCS Concepts: • Computer systems organization → Embedded and cyber-physical systems; Firmware; Embedded hardware; Embedded software; Real-time systems; • Hardware → Simulation and emulation. Additional Key Words and Phrases: Firmware re-hosting, system emulation, embedded systems, emulation fidelity, emulator classification, binary analysis, reverse engineering, emulation challenges ACM Reference Format: Christopher Wright, William A. Moeglein, Saurabh Bagchi, Milind Kulkarni, and Abraham A. Clements. 2020. Challenges in Firmware Re-Hosting, Emulation, and Analysis. -

The Black Art of DOS Emulation on Raspberry Pi
The Black Art of DOS emulation on Raspberry Pi Using FastDOSBox. By : [email protected] www.norisc-nofun.co.uk Version 1.0 – May 2013, Author : Franck / NoRiscNoFun , [email protected] – twitter : @Noriscnofun1 Table of Contents What is DOS emulation for who and for what ?..................................................................................3 Why choosing FastDOSBox for DOS emulation on the Rpi ?............................................................4 Installing FastDOSBox on the Raspberry Pi........................................................................................5 For RISC OS....................................................................................................................................5 For Raspbian....................................................................................................................................5 Recommended Raspberry Pi CPU settings for FastDOSBox..............................................................6 Recommended configuration settings for FastDOSBox......................................................................7 [dosbox] Section..............................................................................................................................7 [render] Section................................................................................................................................7 [cpu] Section....................................................................................................................................7 -
Running DOS on the Raspberry Pi Differing CPU Architectures Mean Running DOS on Raspberry Pi Isn't Effortless, but It's Not Very Complicated, Either
LOG IN SIGN UP Main menu Articles Resources About Community The Open Org Running DOS on the Raspberry Pi Differing CPU architectures mean running DOS on Raspberry Pi isn't effortless, but it's not very complicated, either. ( /1u3s Merasr /2ji0m18-h |a Jlli)m Hall (/users/jim-hall) | 10 Image credits : FreeDOS You may be familiar with The FreeDOS Project (http://www.freedos.org/). FreeDOS is a complete, free, DOS-compatible operating system that you can use to play classic DOS games, run legacy business software, or develop embedded PC applications. Any program that works on MS-DOS should also run on FreeDOS. As the founder and project coordinator of the FreeDOS Project, I'm often the go-to person when users ask questions. And one question I seem to get a lot lately is: "Can you run FreeDOS on the Raspberry Pi?" This question isn't surprising. After all, Linux runs great on the Raspberry Pi, and FreeDOS is an older operating system that requires fewer resources than Linux, so why shouldn't FreeDOS run on the Raspberry Pi. [Enter our Raspberry Pi week giveaway (https://opensource.com/article/18/3/raspberry-pi-week-giveaway) for a chance at this arcade gaming kit.] The simple answer is that FreeDOS cannot run on a Raspberry Pi by itself because of the CPU architecture. Like any DOS, FreeDOS requires an Intel x86 CPU and a BIOS to provide basic runtime services. But the Raspberry Pi is a completely different architecture. The Raspberry Pi runs an ARM CPU, which is not binary compatible with the Intel CPU and does not include a BIOS. -
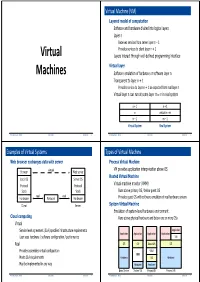
Virtual Machines Dr
Virtual Machine (VM) Layered model of computation Software and hardware divided into logical layers Layer n Receives services from server layer n – 1 Provides services to client layer n + 1 Virtual Layers interact through well-defined programming interface Virtual layer Machines Software emulation of hardware or software layer n Transparent to layer n + 1 Provides service to layer n + 1 as expected from real layer n Virtual layer n can run at some layer m ≠ n in real system n + 1 n + 1 n virtual n = m n –1 m –1 Virtual System Real System Modern Microprocessors — Fall 2012 Virtual Machines Dr. Martin Land 1 Modern Microprocessors — Fall 2012 Virtual Machines Dr. Martin Land 2 Examples of Virtual Systems Types of Virtual Machine Web browser exchanges data with server Process Virtual Machine VM provides application interpretation above OS Browser virtual Web server Hosted Virtual Machine Local OS Server OS Protocol Protocol Virtual machine monitor (VMM) Stack Stack Runs above primary OS / below guest OS real real Hardware Network Hardware Provides guest OS with software emulation of real hardware system Client Server System Virtual Machine Emulation of system-level hardware environment Cloud computing Runs above physical hardware and below one or more OSs Virtual Service level agreement (SLA) specifies infrastructure requirements Application Application Application Application Application User sees hardware / software configuration / performance VM Real OS OS Guest OS OS Provider assembles virtual configuration VMM VMM Meets SLA requirements Hardware OS Hardware May be implemented in any way Hardware Hardware Basic System System VM Hosted VM Process VM Modern Microprocessors — Fall 2012 Virtual Machines Dr. -

DOSEMU and Freedos: Past, Present and Future
DOSEMU and FreeDOS: past, present and future Bart Oldeman <[email protected]> Maintained DOSEMU (2001-2013) Maintained the FreeDOS kernel and FreeDOS’ MEM utility (2000-2004). FreeDOS slides based on those from FreeDOS project coordinator Jim Hall <[email protected]> https://upload.wikimedia.org/wikipedia/commons/b/b7/Commodore_PC20.jpg Commodore PC-20 III (1990) image: https://flic.kr/p/74CmCF (CC ShareAlike) Microsoft MS-DOS DOSEMU Originally: using the Linux vm86() syscall to run DOS and DOS programs in a lightweight virtual machine ● Sept 3, 1992: Matthias Lautner (Linux was only a little over 1 year old.) Version 0.1: “DOS EMULATOR for LINUX 0.97 pl2 This is a pre alpha version. This means there are some bugs and lots of things aren't implemented such as screen attributes, some video interrupts, some other bios calls, any port io, …” ● 1993: Robert Sanders (0.47-0.49) ● 1993-1997: James MacLean (0.49pl2-0.64.3) ○ DOS Protected Mode Interface (DPMI) support using modify_ldt() syscall added early 1994. ● 1997-2001: Hans Lermen (0.64.4-1.1.1) ● 2001-2013: Bart Oldeman ● DOSEMU2: 2013- Stas Sergeev This is the dumb terminal mode; S-Lang (terminal), SDL, and X outputs are available. SimCity 2000 Running Win3.1 Netscape with network (T.P. Reitzel) DOSEMU’s other uses Asked around on mailing list and github and received the following replies: ● Running very old specialized cross compilers, all setup with wrappers so from the user’s point of view they are just Linux programs. ● A yearly ephemeris for astrologers with a QuickBasic IDE. -

Roland LAPC-1 SNK Neo Geo Pocket Color Ferien Auf Monkey Island
something wonderful has happened Nr. 1/Juni 2002 interviews mit usern von damals und heute Commodore 64 1982-2002 Seite 3 charles bernstein: Play It Again, Pac-Man Teil 1 Seite 15 das vergessene betriebssystem CP/M Plus am C128 ab Seite 12 windows doch nicht ganz nutzlos: Llamasoft-Remakes am PC Seite 6/7 die rueckkehr der metagalaktischen computer steht bevor Amiga One/Commodore One [email protected] www.lotek64.com Lotek64 Juni 2002 Seite 6/7 Lotek64 2 C0MMODORE-PREISLISTE 1987 Zum 5. März 1987 hat Commodore eine neue Preisliste herausgebracht. Die aufgeführten Preise sind Listenpreise und verstehen sich in Mark inklusive Mehrwertsteuer. PC l0 II ................................................................... 2995,00 PC 20 II .................................................................. 3995,00 PC 40/AT ............................................................... 6995,00 PC 40/AT 40MB .................................................... o. A. Bürosystem S ....................................................... 4995,00 Bürosystem DL..................................................... 6495,00 Bürosystem TTX ................................................ 13695,00 MPS 2000 .............................................................. 1695,00 MPS 2000 C........................................................... 1995,00 Einzelblatt2000 ...................................................... 980,40 Traktor 2000............................................................ 437,76 Liebe Loteks! MPS 2010 ............................................................. -

LINUX Virtualization
LINUX Virtualization Running other code under LINUX Environment Virtualization • Citrix/MetaFrame – Virtual desktop under Windows NT. aka Windows Remote Desktop Protocol • VNC, Dameware – virtual console. • XWindows – virtual console • Mac OS RDP – same as Windows. • WUBI.EXE Hardware Emulation • IBM – Virtual Machine (VM) OS Also using code: • Processor virtualization • Instruction set virtualization. • Slow. Usually requires OS (re-)installation • Examples: KVM (uses QEMU), Solaris Domains, DOSBox, DOSEmu, WINE Processor Virtualization • “Native” or full virtualization: virtual machine that mediates between the guest operating systems and the native hardware. Certain protected instructions must be trapped and handled within the hypervisor because the underlying hardware isn't owned by an operating system but is instead shared by it through the hypervisor. • This form usually requires specially virtualization CPU processors (Intel, AMD) for performance. The only constraint is that the operating system must support the underlying hardware. Close to hardware-level performance. • The biggest advantage of full virtualization is that a guest OS can run unmodified. OS is usually “ported” to the hypervisor machine. VmWare, Microsoft HyperV. • Examples: VMWare. Processor Virtualization • Paravirtualization: uses a hypervisor for shared access to the underlying hardware but integrates virtualization-aware code into the operating system itself. Obviates the need for any recompilation or trapping because the operating systems themselves cooperate