Dynamic Memory Management: Dlmalloc Secure Coding in C and C++
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Practical C/C++ Programming Part II
Practical C/C++ programming Part II Wei Feinstein HPC User Services Louisiana State University 7/11/18 Practical C/C++ programming II 1 Topics • Pointers in C • Use in functions • Use in arrays • Use in dynamic memory allocation • Introduction to C++ • Changes from C to C++ • C++ classes and objects • Polymorphism • Templates • Inheritance • Introduction to Standard Template Library (STL) 7/11/18 Practical C/C++ programming II 2 What is a pointer? • A pointer is essentially a variable whose value is the address of another variable. • Pointer “points” to a specific part of the memory. • Important concept in C programming language. Not recommended in C++, yet understanding of pointer is necessary in Object Oriented Programming • How to define pointers? int *i_ptr; /* pointer to an integer */ double *d_ptr; /* pointer to a double */ float *f_ptr; /* pointer to a float */ char *ch_ptr; /* pointer to a character */ int **p_ptr; /* pointer to an integer pointer */ 7/11/18 Practical C/C++ programming II 3 Pointer Operations (a) Define a pointer variable. (b) Assign the address of a variable to a pointer. & /* "address of" operator */ (c) Access the value pointed by the pointer by dereferencing * /* “dereferencing" operator */ Examples: int a = 6; int *ptr; ptr = &a; /* pointer p point to a */ *ptr = 10; /* dereference pointer p reassign a value*/ var_name var_address var_value ptr 0x22aac0 0xXXXX a 0xXXXX 6 7/11/18 Practical C/C++ programming II 4 Pointer Example int b = 17; int *p; /* initialize pointer p */ p = &b; /*pointed addr and value, -

Rational Purifyplus for UNIX
Develop Fast, Reliable Code Rational PurifyPlus for UNIX Customers and end-users demand that your Automatically Pinpoint code works reliably and offers adequate execu- Hard-To-Find Bugs tion performance. But the reality of your deliv- Reliability problems, such as runtime errors and ery schedule often forces you to sacrifice relia- memory leaks in C/C++, can kill a software bility or performance – sometimes both. And company’s reputation. These errors are hard to without adequate time for testing, you may not find, hard to reproduce, and hardest of all, to even know these issues exist. So you reluctant- explain to customers who discover them. No ly deliver your code before it’s ready, knowing one intentionally relies on their customer as good and well that the integrity of your work their "final QA." But without adequate tools, this may be suspect. is the inevitable outcome. Even the best pro- Rational Software has a solution for ensuring grammers make mistakes in their coding. that your code is both fast and reliable. Rational PurifyPlus for UNIX automatically finds HIGHLIGHTS Rational® PurifyPlus for UNIX combines runtime these reliability errors in C/C++ code that can’t error detection, application performance profil- Automatically finds runtime be found in any other way. It finds the errors ing, and code coverage analysis into a single, errors in C/C++ code even before visible symptoms occur (such as a complete package. Together, these functions system crash or other spurious behavior). And help developers ensure the highest reliability Quickly isolates application it shows you exactly where the error originated, and performance of their software from the very performance bottlenecks regardless of how remote from the visible first release. -

Lab 1: Programming in C 1 Lab 1: Programming in C CS 273 Monday, 8-24-20 Revision 1.2
Lab 1: Programming in C 1 Lab 1: Programming in C CS 273 Monday, 8-24-20 Revision 1.2 Preliminary material • Using manual pages. For example, % man gcc % man read % man 2 read Viewing online manual pages on a browser. • Similarities between C++ and C. C++ language shares most of its same basic syntax with C. Thus, simple variable declarations, assignments, loops, array access, function defini- tions/declarations/calls, etc. are written the essentially the same way in both languages. Much of the basic semantics is shared, also. Thus, a for loop behaves as expected, as does an expression statement, a function definition, etc.; also, operators have the same precedence and associativity. The two languages both use predefined types int, long, float, char, etc. In both languages, ASCII characters are represented as (8-bit) integer values, and simple strings are represented as arrays of characters terminated by nullbytes. Preprocessor directives (such as #include, #define, etc.) are used in both C and C++. • Differences between C++ and C. { C has no classes. Instead, you must use functions and variables to perform operations. It is still useful to use \interface modules" and \implementation modules" and to organize your program into packages that can be linked separately. However, there are no classes to define per se. C does provide struct (and union) for data structures. Unlike C++, a struct is not a class, but instead is a container for variables of various types. There are no methods, no constructors, no destructors, etc. { No overloading of functions or operators in C. Many conventional meanings of operators in C++ (such as <<) are no longer relevant. -

The Developer's Guide to Debugging
The Developer’s Guide to Debugging Thorsten Grotker¨ · Ulrich Holtmann Holger Keding · Markus Wloka The Developer’s Guide to Debugging 123 Thorsten Gr¨otker Ulrich Holtmann Holger Keding Markus Wloka Internet: http://www.debugging-guide.com Email: [email protected] ISBN: 978-1-4020-5539-3 e-ISBN: 978-1-4020-5540-9 Library of Congress Control Number: 2008929566 c 2008 Springer Science+Business Media B.V. No part of this work may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, photocopying, microfilming, recording or otherwise, without written permission from the Publisher, with the exception of any material supplied specifically for the purpose of being entered and executed on a computer system, for exclusive use by the purchaser of the work. Printed on acid-free paper 987654321 springer.com Foreword Of all activities in software development, debugging is probably the one that is hated most. It is guilt-ridden because a technical failure suggests personal fail- ure; because it points the finger at us showing us that we have been wrong. It is time-consuming because we have to rethink every single assumption, every single step from requirements to implementation. Its worst feature though may be that it is unpredictable: You never know how much time it will take you to fix a bug - and whether you’ll be able to fix it at all. Ask a developer for the worst moments in life, and many of them will be related to debugging. It may be 11pm, you’re still working on it, you are just stepping through the program, and that’s when your spouse calls you and asks you when you’ll finally, finally get home, and you try to end the call as soon as possible as you’re losing grip on the carefully memorized observations and deductions. -

Object Oriented Programming in Objective-C 2501ICT/7421ICT Nathan
Subclasses, Access Control, and Class Methods Advanced Topics Object Oriented Programming in Objective-C 2501ICT/7421ICT Nathan René Hexel School of Information and Communication Technology Griffith University Semester 1, 2012 René Hexel Object Oriented Programming in Objective-C Subclasses, Access Control, and Class Methods Advanced Topics Outline 1 Subclasses, Access Control, and Class Methods Subclasses and Access Control Class Methods 2 Advanced Topics Memory Management Strings René Hexel Object Oriented Programming in Objective-C Subclasses, Access Control, and Class Methods Subclasses and Access Control Advanced Topics Class Methods Objective-C Subclasses Objective-C Subclasses René Hexel Object Oriented Programming in Objective-C Subclasses, Access Control, and Class Methods Subclasses and Access Control Advanced Topics Class Methods Subclasses in Objective-C Classes can extend other classes @interface AClass: NSObject every class should extend at least NSObject, the root class to subclass a different class, replace NSObject with the class you want to extend self references the current object super references the parent class for method invocations René Hexel Object Oriented Programming in Objective-C Subclasses, Access Control, and Class Methods Subclasses and Access Control Advanced Topics Class Methods Creating Subclasses: Point3D Parent Class: Point.h Child Class: Point3D.h #import <Foundation/Foundation.h> #import "Point.h" @interface Point: NSObject @interface Point3D: Point { { int x; // member variables int z; // add z dimension -

Heapmon: a Low Overhead, Automatic, and Programmable Memory Bug Detector ∗
Appears in the Proceedings of the First IBM PAC2 Conference HeapMon: a Low Overhead, Automatic, and Programmable Memory Bug Detector ∗ Rithin Shetty, Mazen Kharbutli, Yan Solihin Milos Prvulovic Dept. of Electrical and Computer Engineering College of Computing North Carolina State University Georgia Institute of Technology frkshetty,mmkharbu,[email protected] [email protected] Abstract memory bug detection tool, improves debugging productiv- ity by a factor of ten, and saves $7,000 in development costs Detection of memory-related bugs is a very important aspect of the per programmer per year [10]. Memory bugs are not easy software development cycle, yet there are not many reliable and ef- to find via code inspection because a memory bug may in- ficient tools available for this purpose. Most of the tools and tech- volve several different code fragments which can even be in niques available have either a high performance overhead or require different files or modules. The compiler is also of little help a high degree of human intervention. This paper presents HeapMon, in finding heap-related memory bugs because it often fails to a novel hardware/software approach to detecting memory bugs, such fully disambiguate pointers [18]. As a result, detection and as reads from uninitialized or unallocated memory locations. This new identification of memory bugs must typically be done at run- approach does not require human intervention and has only minor stor- time [1, 2, 3, 4, 6, 7, 8, 9, 11, 13, 14, 18]. Unfortunately, the age and execution time overheads. effects of a memory bug may become apparent long after the HeapMon relies on a helper thread that runs on a separate processor bug has been triggered. -

C++ for C Programmers BT120
C++ for C Programmers BT120 40 Academic Hours C++ for C Programmers Outline C++ is undoubtedly one of the most popular programming languages for software development. It brings language enhancements and object-oriented programming support to C. However, C++ is a large and sometimes difficult language, and even with a C background, a programmer needs to understand C++ programming style as well as C++ constructs to get the best out of itl. For experienced C programmers, the course will illustrate how to get the benefits of good software engineering and code reuse by using standard C++ and object-oriented programming techniques in real-world programming situations. This is a hand on course with a mix of tuition and practical sessions for each technical chapter which reinforce the C++ syntax and object-oriented programming techniques covered in the course. Target Audience C Programmers wishing to learn or improve in C++ Prerequisites Delegates should have a working knowledge of C, and some knowledge of ו Embedded/Real Time programming. Delegates must have solid experience of C including structures (i.e. struct and/or ו class); declaration and use of pointers; function declaration, definition and use with call by value or call by pointer; dynamic memory allocation (i.e. malloc and free, or new and delete); multiple source file projects (requiring project files or makes files) Objectives On completion, Delegates will be able to: .The core C++ syntax and semantics ו Object Oriented Advantages, and Principles ו How to write safe, efficient C++ -

Debugging and Tuning Linux for EDA
Debugging and Tuning Linux for EDA Fabio Somenzi [email protected] University of Colorado at Boulder Outline Compiling gcc icc/ecc Debugging valgrind purify ddd Profiling gcov, gprof quantify vtl valgrind Compiling Compiler options related to static checks debugging optimization Profiling-driven optimization Compiling with GCC gcc -Wall -O3 -g reports most uses of potentially uninitialized variables -O3 (or -O6) necessary to trigger dataflow analysis can be fooled by if (cond) x = VALUE; ... if (cond) y = x; Uninitialized variables not considered for register allocation may escape Achieving -Wall-clean code is not too painful and highly desirable Compiling C code with g++ is more painful, but has its rewards Compiling with GCC gcc -mcpu=pentium4 -malign-double -mcpu=pentium4 optimizes for the Pentium 4, but produces code that runs on any x86 -march=pentium4 uses Pentium 4-specific instructions -malign-double forces alignment of double’s to double-word boundary Use either for all files or for none gcc -mfpmath=sse Controls the use of SSE instructions for floating point For complete listing, check gcc’s info page under Invoking gcc ! Submodel Options Compiling with ICC ICC is the Intel compiler for IA-32 systems. http://www.intel.com/software/products/ icc -O3 -g -ansi -w2 -Wall Aggressive optimization Retain debugging info Strict ANSI conformance Display remarks, warnings, and errors Enable all warnings Remarks tend to be a bit overwhelming Fine grain control over diagnostic: see man page Compiling with ICC icc -tpp7 Optimize instruction scheduling -
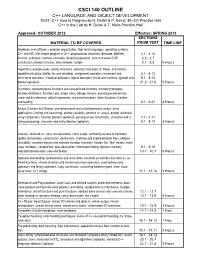
CSCI 140 OUTLINE C++ LANGUAGE and OBJECT DEVELOPMENT TEXT: C++ How to Program by H
CSCI 140 OUTLINE C++ LANGUAGE AND OBJECT DEVELOPMENT TEXT: C++ How to Program by H. Deitel & P. Deitel, 8th ED Prentice Hall C++ in the Lab by H. Deitel & T. Nieto Prentice Hall Approved: OCTOBER 2012 Effective: SPRING 2013 SECTIONS MATERIAL TO BE COVERED FROM TEXT TIME LINE Hardware and software, computer organization, high level languages, operating systems, C++ and IDE, first simple program in C++, preprocessor directives (#include, #define), 1.1 - 1.14 macros, arithmetic, memory concepts, relational operators, intro to classes OOP, 2.2 - 2.7 constructor, member function, data member, set/get 3.1 - 3.8 5 Hours Algorithms, pseudo-code, control structures, selection structures (if, if/else, and switch), repetition structure (whilte, for, and do/while), assignment operators, increment and 4.1 - 4.12 decrement operators, relational operators, logical operators, break and continue, typedef and 5.1 - 5.10 bitwise operators 21.2 - 21.6 5 Hours Functions: standard library functions and user-defined functions, function prototypes, function definitions, function calls, scope rules, storage classes, passing parameters by value and by reference, default arguments, recursive functions, inline functions, function overloading 6.1 - 6.21 4 Hours Arrays, Pointers and Strings: one-dimensional and multidimensional arrays, array applications (sorting and searching), pointer variables, pointers vs. arrays, pointer arithmetic, arrays of pointers, function pointers (optional), passing arrays to functions, character and C- 7.1 - 7.11 string processing, character -

The Rule of the Big Five
C++11: The Rule of the Big Five Resource Management The dynamic creation and destruction of objects was always one of the bugbears of C. It required the programmer to (manually) control the allocation of memory for the object, handle the object’s initialisation, then ensure that the object was safely cleaned-up after use and its memory returned to the heap. Because many C programmers weren’t educated in the potential problems (or were just plain lazy or delinquent in their programming) C got a reputation in some quarters for being an unsafe, memory-leaking language. C++ improved matters significantly by introducing an idiom known (snappily) as RAII/RRID – Resource Acquisition Is Initialisation / Resource Release Is Destruction*. The idiom makes use of the fact that every time an object is created a constructor is called; and when that object goes out of scope a destructor is called. The constructor/destructor pair can be used to create an object that automatically allocates and initialises another object (known as the managed object) and cleans up the managed object when it (the manager) goes out of scope. This mechanism is generically referred to as resource management. A resource could be any object that required dynamic creation/deletion – memory, files, sockets, mutexes, etc. Resource management frees the client from having to worry about the lifetime of the managed object, potentially eliminating memory leaks and other problems in C++ code. However, RAII/RRID doesn’t come without cost (to be fair, what does?) Introducing a ‘manager’ object can lead to potential problems – particularly if the ‘manager’ class is passed around the system (it is just another object, after all). -

Copyrighted Material 23 Chapter 2: Data, Variables, and Calculations 25
CONTENTS INTRODUCTION xxxv CHAPTER 1: PROGRAMMING WITH VISUAL C++ 1 Learning with Visual C++ 1 Writing C++ Applications 2 Learning Desktop Applications Programming 3 Learning C++ 3 Console Applications 4 Windows Programming Concepts 4 What Is the Integrated Development Environment? 5 The Editor 6 The Compiler 6 The Linker 6 The Libraries 6 Using the IDE 7 Toolbar Options 8 Dockable Toolbars 9 Documentation 10 Projects and Solutions 10 Defi ning a Project 10 Debug and Release Versions of Your Program 15 Executing the Program 16 Dealing with Errors 18 Setting Options in Visual C++ 19 Creating and Executing Windows Applications 20 Creating an MFC Application 20 Building and Executing the MFC Application 22 Summary COPYRIGHTED MATERIAL 23 CHAPTER 2: DATA, VARIABLES, AND CALCULATIONS 25 The Structure of a C++ Program 26 Program Comments 31 The #include Directive — Header Files 32 Namespaces and the Using Declaration 33 The main() Function 34 Program Statements 34 fftoc.inddtoc.indd xxviivii 224/08/124/08/12 88:01:01 AAMM CONTENTS Whitespace 37 Statement Blocks 37 Automatically Generated Console Programs 37 Precompiled Header Files 38 Main Function Names 39 Defi ning Variables 39 Naming Variables 39 Keywords in C++ 40 Declaring Variables 41 Initial Values for Variables 41 Fundamental Data Types 42 Integer Variables 42 Character Data Types 44 Integer Type Modifi ers 45 The Boolean Type 46 Floating-Point Types 47 Fundamental Types in C++ 47 Literals 48 Defi ning Synonyms for Data Types 49 Basic Input/Output Operations 50 Input from the Keyboard 50 -

IBM Rational Purifyplus for AIX Helps Developers and Testers Deliver Applications Faster and with Fewer Errors
IBM Europe, Middle East, and Africa Software Announcement ZP09-0129, dated May 12, 2009 IBM Rational PurifyPlus for AIX helps developers and testers deliver applications faster and with fewer errors Table of contents 1 At a glance 4 Publications 1 Overview 4 Technical information 2 Key prerequisites 5 Ordering information 2 Planned availability dates 7 Terms and conditions 2 Product positioning 9 IBM Electronic Services 3 Program number 10 Prices 3 Offering Information 10 Announcement countries At a glance tm IBM® Rational® PurifyPlus for AIX® is the newest member of an award-winning family of products that provide a dynamic analysis solution designed to help developers write faster, more reliable code. It includes four basic capabilities: • Memory debugging: Pinpoints hard to find memory errors such as uninitialized memory access, buffer overflow, and improper freeing of memory. • Memory leak detection: Identifies memory blocks that no longer have a valid pointer. • Application performance profiling: Highlights application performance bottlenecks and improves application understanding with a graphical representation of function calls. • Code coverage analysis: Identifies untested code with line-level precision. Overview IBM Rational PurifyPlus for AIX is a set of dynamic analysis tools designed for improving application reliability and performance on the IBM System p® platform. The PurifyPlus software combines the following capabilities into a single, complete package: • Memory debugging • Memory leak detection • Application performance profiling • Code coverage analysis Together, these capabilities help developers and testers to realize high reliability and performance of their software from its very first release. IBM Rational PurifyPlus for AIX allows developers and testers to monitor an entire application or just a subset of an application's modules.