Forcepoint Supported File Formats and Size Limits
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
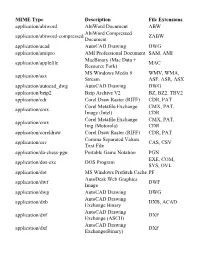
MIME Type Description File Extensions Application/Abiword
MIME Type Description File Extensions application/abiword AbiWord Document ABW AbiWord Compressed application/abiword-compressed ZABW Document application/acad AutoCAD Drawing DWG application/amipro AMI Professional Document SAM, AMI MacBinary (Mac Data + application/applefile MAC Resource Fork) MS Windows Media 9 WMV, WMA, application/asx Stream ASF, ASR, ASX application/autocad_dwg AutoCAD Drawing DWG application/bzip2 Bzip Archive V2 BZ, BZ2, TBV2 application/cdr Corel Draw Raster (RIFF) CDR, PAT Corel Metafile Exchange CMX, PAT, application/cmx Image (Intel) CDR Corel Metafile Exchange CMX, PAT, application/cmx Img (Motorola) CDR application/coreldraw Corel Draw Raster (RIFF) CDR, PAT Comma Separated Values application/csv CAS, CSV Text File application/da-chess-pgn Portable Game Notation PGN EXE, COM, application/dos-exe DOS Program SYS, OVL application/dot MS Windows Prefetch Cache PF AutoDesk Web Graphics application/dwf DWF Image application/dwg AutoCAD Drawing DWG AutoCAD Drawing application/dxb DXB, ACAD Exchange Binary AutoCAD Drawing application/dxf DXF Exchange (ASCII) AutoCAD Drawing application/dxf DXF Exchange(Binary) EMF, TMP, EMF, TMP, application/emf Windows Enhanced Metafile WMF application/envoy Envoy Document EVY, ENV Comma Separated Values application/excel CAS, CSV Text File MS Excel XLS, XLA, application/excel Worksheet/Add-In/Template XLT, XLB EXE, COM, application/exe DOS Program SYS, OVL EXE, VXD, application/exe MS Windows Driver (16 bit) SYS, DRV, 386 MS Windows Program (16 application/exe EXE, MOD, BIN bit) -

Portable Paper
Volume 2, Number 2 The HP Portable/Portable Plus Users Newsletter March / April, 1987 PortableTHE Paper Special Feature: Database Software Management Publisher's Message ...................... I Special Feature: Database Management Letters Software Charge Portable Off Car Lighter .............. 2 Introduction ............................ 16 Portable To Macintosh ..................... 4 Database Management Product Summary ...... 16 110% Lotus As A Database Manager . 18 New HP Portable? ......................... '; Executive Card Manager ................... 18 Updates on Personalized Software Products ..... 5 dBASE II ............................... 22 Buying Disks ............................ 6 Turbo Pascal Toolbox ..................... 2-} X-rays And The Portable .................... 6 PC File III .............................. 24 More Info On Backlighting ................. 33 T/Master ............................... 25 HP-IL Link Program ........ .............. 33 Condor Junior .......................... 25 Foundations Conclusion ............................. 25 Built-in Self-Test .......................... 8 PLUS Notes Six Ways To Restart Your Portable ............. 8 Lotus 2.01 and HAL ...................... 25 Getting Program To Run . ..... 8 B Drive RAM Cards With Greater Capacity ........... 26 EPROM Update .......................... 26 DOS AID Software Drawer & SPC ................ 27 Bypassing PAM ............................ 11 1erminal Through The Looking Glass ............ 27 CompuServe Autologon, Uploading Revisited .... -

Es Fluttert Gewaltig René Jahn, SIB Visions Gmbh
Es Fluttert gewaltig René Jahn, SIB Visions GmbH Wer eine App für mobile Geräte entwickeln möchte, as JVx Framework [1] ermöglicht die Erstellung von Daten- steht zumindest vor einer wichtigen Frage: Mit D bank-Applikationen für unterschiedlichste GUI-Technologien welcher Technologie soll die App realisiert werden? mit einer einzigen Source-Basis. Es ist sowohl eine GUI-Abstraktion als auch ein Full-Stack Application Framework. Die damit erstell- Da es aktuell verschiedenste Möglichkeiten gibt, ist ten Applikationen laufen ohne Änderungen im Browser mittels Ja- die Antwort nicht sofort klar. Mit diesem Problem vaScript/CSS, am Desktop mit Swing oder JavaFX und auf mobilen war das Framework-Team von SIB Visions ebenfalls Geräten mithilfe nativer Apps. Mit JVx können Applikationen unter- schiedlichster Größe und Komplexität realisiert werden. Zwei Pro- konfrontiert, als es darum ging, einen Client für dukte, die mit JVx entwickelt wurden, sind beispielsweise SNOWsat das Open Source Application Framework JVx zu Maintain [3] und VisionX [4]. entwickeln. Wie es zu einer Entscheidung kam und vor allem was umgesetzt wurde, wird in diesem Wie soeben erwähnt, werden für die Ausführung auf mobilen Gerä- ten native Apps eingesetzt. Es gibt eine App für iOS und eine andere Artikel erklärt. für Android. Erfahrene App-Entwickler werden vermuten, dass die- iii iii 30 www.ijug.eu iiiiii se Apps unabhängig voneinander entwickelt wurden. Das ist auch Gesamteindruck war nicht zufriedenstellend. So blieb am Ende also genauso. Die iOS-App wurde mit Objective-C und die Android-App Flutter übrig. Doch nicht, weil es der letzte Kandidat war, sondern mit Java entwickelt. Das war im Jahr 2014 auch ein gangbarer Weg, weil man von Anfang an den Eindruck hatte, dass es sich um die da es nur wenige Lösungen gab, die eine Entwicklung mit nur einer richtige Technologie handelt. -

Full Document
R&D Centre for Mobile Applications (RDC) FEE, Dept of Telecommunications Engineering Czech Technical University in Prague RDC Technical Report TR-13-4 Internship report Evaluation of Compressibility of the Output of the Information-Concealing Algorithm Julien Mamelli, [email protected] 2nd year student at the Ecole´ des Mines d'Al`es (N^ımes,France) Internship supervisor: Luk´aˇsKencl, [email protected] August 2013 Abstract Compression is a key element to exchange files over the Internet. By generating re- dundancies, the concealing algorithm proposed by Kencl and Loebl [?], appears at first glance to be particularly designed to be combined with a compression scheme [?]. Is the output of the concealing algorithm actually compressible? We have tried 16 compression techniques on 1 120 files, and the result is that we have not found a solution which could advantageously use repetitions of the concealing method. Acknowledgments I would like to express my gratitude to my supervisor, Dr Luk´aˇsKencl, for his guidance and expertise throughout the course of this work. I would like to thank Prof. Robert Beˇst´akand Mr Pierre Runtz, for giving me the opportunity to carry out my internship at the Czech Technical University in Prague. I would also like to thank all the members of the Research and Development Center for Mobile Applications as well as my colleagues for the assistance they have given me during this period. 1 Contents 1 Introduction 3 2 Related Work 4 2.1 Information concealing method . 4 2.2 Archive formats . 5 2.3 Compression algorithms . 5 2.3.1 Lempel-Ziv algorithm . -

February 2005)
TechNews November 2006 TechNews is a technology, news and analysis service aimed at those in the education sector keen to stay informed about technology developments, trends and issues. Please navigate the newsletter by clicking on items within the table of contents. Networking and wireless ........................................................................................................... 2 Analysis: Trusted Computing and Network Access Control............................................................................. 2 Networking and wireless news ................................................................................................. 4 Becta Infrastructure Services Framework ............................................................................................................... 4 802.11n update ....................................................................................................................................................... 4 Predicted growth in GPS-based services................................................................................................................ 4 Mobile WiMAX......................................................................................................................................................... 5 Short range wireless developments ........................................................................................................................ 5 4G progress ........................................................................................................................................................... -

ARC File Revision 3.0 Proposal
ARC file Revision 3.0 Proposal Steen Christensen, Det Kongelige Bibliotek <ssc at kb dot dk> Michael Stack, Internet Archive <stack at archive dot org> Edited by Michael Stack Revision History Revision 1 09/09/2004 Initial conversion of wiki working doc. [http://crawler.archive.org/cgi-bin/wiki.pl?ArcRevisionProposal] to docbook. Added suggested edits suggested by Gordon Mohr (Others made are still up for consideration). This revision is what is being submitted to the IIPC Framework Group for review at their London, 09/20/2004 meeting. Table of Contents 1. Introduction ............................................................................................................................2 1.1. IIPC Archival Data Format Requirements .......................................................................... 2 1.2. Input ...........................................................................................................................2 1.3. Scope ..........................................................................................................................3 1.4. Acronyms, Abbreviations and Definitions .......................................................................... 3 2. ARC Record Addressing ........................................................................................................... 4 2.1. Reference ....................................................................................................................4 2.2. The ari Scheme ............................................................................................................ -

Metadefender Core V4.12.2
MetaDefender Core v4.12.2 © 2018 OPSWAT, Inc. All rights reserved. OPSWAT®, MetadefenderTM and the OPSWAT logo are trademarks of OPSWAT, Inc. All other trademarks, trade names, service marks, service names, and images mentioned and/or used herein belong to their respective owners. Table of Contents About This Guide 13 Key Features of Metadefender Core 14 1. Quick Start with Metadefender Core 15 1.1. Installation 15 Operating system invariant initial steps 15 Basic setup 16 1.1.1. Configuration wizard 16 1.2. License Activation 21 1.3. Scan Files with Metadefender Core 21 2. Installing or Upgrading Metadefender Core 22 2.1. Recommended System Requirements 22 System Requirements For Server 22 Browser Requirements for the Metadefender Core Management Console 24 2.2. Installing Metadefender 25 Installation 25 Installation notes 25 2.2.1. Installing Metadefender Core using command line 26 2.2.2. Installing Metadefender Core using the Install Wizard 27 2.3. Upgrading MetaDefender Core 27 Upgrading from MetaDefender Core 3.x 27 Upgrading from MetaDefender Core 4.x 28 2.4. Metadefender Core Licensing 28 2.4.1. Activating Metadefender Licenses 28 2.4.2. Checking Your Metadefender Core License 35 2.5. Performance and Load Estimation 36 What to know before reading the results: Some factors that affect performance 36 How test results are calculated 37 Test Reports 37 Performance Report - Multi-Scanning On Linux 37 Performance Report - Multi-Scanning On Windows 41 2.6. Special installation options 46 Use RAMDISK for the tempdirectory 46 3. Configuring Metadefender Core 50 3.1. Management Console 50 3.2. -

Metadefender Core V4.13.1
MetaDefender Core v4.13.1 © 2018 OPSWAT, Inc. All rights reserved. OPSWAT®, MetadefenderTM and the OPSWAT logo are trademarks of OPSWAT, Inc. All other trademarks, trade names, service marks, service names, and images mentioned and/or used herein belong to their respective owners. Table of Contents About This Guide 13 Key Features of Metadefender Core 14 1. Quick Start with Metadefender Core 15 1.1. Installation 15 Operating system invariant initial steps 15 Basic setup 16 1.1.1. Configuration wizard 16 1.2. License Activation 21 1.3. Scan Files with Metadefender Core 21 2. Installing or Upgrading Metadefender Core 22 2.1. Recommended System Requirements 22 System Requirements For Server 22 Browser Requirements for the Metadefender Core Management Console 24 2.2. Installing Metadefender 25 Installation 25 Installation notes 25 2.2.1. Installing Metadefender Core using command line 26 2.2.2. Installing Metadefender Core using the Install Wizard 27 2.3. Upgrading MetaDefender Core 27 Upgrading from MetaDefender Core 3.x 27 Upgrading from MetaDefender Core 4.x 28 2.4. Metadefender Core Licensing 28 2.4.1. Activating Metadefender Licenses 28 2.4.2. Checking Your Metadefender Core License 35 2.5. Performance and Load Estimation 36 What to know before reading the results: Some factors that affect performance 36 How test results are calculated 37 Test Reports 37 Performance Report - Multi-Scanning On Linux 37 Performance Report - Multi-Scanning On Windows 41 2.6. Special installation options 46 Use RAMDISK for the tempdirectory 46 3. Configuring Metadefender Core 50 3.1. Management Console 50 3.2. -

On the Interoperability of Ebook Formats
It is widely seen as a serious problem that European as well as international customers who have bought an ebook from one of the international ebook retailers implicitly subscribe to this retailer as their sole future ebook On the Interoperability supplier, i.e. in effect, they forego buying future ebooks from any other supplier. This is a threat to the qualified European book distribution infrastructure and hence the European book culture, since subscribers to one of these of eBook Formats ebook ecosystems cannot buy future ebooks from privately owned community-located bricks & mortar booksellers engaging in ebook retailing. This view is completely in line with the Digital Agenda of the European Commission calling in Pillar II for “an effective interoperability Prof. Christoph Bläsi between IT products and services to build a truly digital society. Europe must ensure that new IT devices, applications, data repositories and services interact seamlessly anywhere – just like the Internet.” Prof. Franz Rothlauf This report was commissioned from Johannes Gutenberg University Johannes Gutenberg-Universität Mainz – Germany Mainz by the European and International Booksellers Federation. EIBF is very grateful to its sponsors, namely the Booksellers Association of Denmark, the Booksellers Association of the Netherlands and the Booksellers Association of the UK & Ireland, whose financial contribution made this project possible. April 2013 European and International Booksellers Federation rue de la Science 10 – 1000 Brussels – Belgium – [email protected] -

Windows NT® 4 for Dummies® File:///P|/VSCAN/TOSCAN/MT/NT4DUM/NT4.HTM
Table of contents Windows NT® 4 For Dummies® file:///P|/VSCAN/TOSCAN/MT/NT4DUM/NT4.HTM Table of Contents Windows NT® 4 For Dummies® Introduction About This Book How to Use This Book And What about You? How This Book Is Organized Part I: Introducing Windows NT (Bare-Bones Stuff) Part II: Making Windows NT Do Something Part III: Using Windows NT Applications Part IV: Been There, Done That: Quick References for Moving to Windows NT Part V: Getting Help Part VI: The Part of Tens Icons Used in This Book Where to Go from Here Part I: Intro to Windows NT (Bare Bones Stuff) Chapter 1: What Is Windows NT? What Is This "Windows" Stuff, Anyway? What Does Windows NT 4 Do? Why Should I Bother Using Windows NT? Will I Like Windows NT 4 Better than Windows NT 3.51? What's the Difference between Windows NT Workstation and Windows NT Server? Bracing Yourself for Windows NT 4 Chapter 2: Boring Information, Bothersome Computer Parts The Computer Microprocessor Floppy Disks, Compact Discs (CDs), and Disk Drives Floppy disk flipping What disk drives does Windows NT like? What does "write-protected" mean? Driving with compact discs The Mouse and That Double-Click Stuff Cards and Monitors Keyboards Groups of keys More key principles Print Screen: the one fun, weird code key Modems Printers Networks Sound Cards (Disgusting Bioactive Noises) Parts Required by Windows NT Chapter 3: Windows NT Stuff Everybody Thinks You Already Know Backing Up Your Work Clicking 1 of 9 07/14/99 08:29:14 Table of contents Windows NT® 4 For Dummies® file:///P|/VSCAN/TOSCAN/MT/NT4DUM/NT4.HTM -

GNU CPIO GNU Cpio 2.5 June 2002
GNU CPIO GNU cpio 2.5 June 2002 by Robert Carleton Copyright c 1995, 2001, 2002 Free Software Foundation, Inc. This is the first edition of the GNU cpio documentation, and is consistent with GNU cpio 2.5. Published by the Free Software Foundation 59 Temple Place - Suite 330, Boston, MA 02111-1307, USA Permission is granted to make and distribute verbatim copies of this manual provided the copyright notice and this permission notice are preserved on all copies. Permission is granted to copy and distribute modified versions of this manual under the con- ditions for verbatim copying, provided that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. Permission is granted to copy and distribute translations of this manual into another lan- guage, under the above conditions for modified versions, except that this permission notice may be stated in a translation approved by the Free Software Foundation. Chapter 2: Tutorial 1 1 Introduction GNU cpio copies files into or out of a cpio or tar archive, The archive can be another file on the disk, a magnetic tape, or a pipe. GNU cpio supports the following archive formats: binary, old ASCII, new ASCII, crc, HPUX binary, HPUX old ASCII, old tar, and POSIX.1 tar. The tar format is provided for compatability with the tar program. By default, cpio creates binary format archives, for compatibility with older cpio programs. When extracting from archives, cpio automatically recognizes which kind of archive it is reading and can read archives created on machines with a different byte-order. -

Renaissance Receptions of Ovid's Tristia Dissertation
RENAISSANCE RECEPTIONS OF OVID’S TRISTIA DISSERTATION Presented in Partial Fulfillment of the Requirements for the Degree Doctor of Philosophy in the Graduate School of The Ohio State University By Gabriel Fuchs, M.A. Graduate Program in Greek and Latin The Ohio State University 2013 Dissertation Committee: Frank T. Coulson, Advisor Benjamin Acosta-Hughes Tom Hawkins Copyright by Gabriel Fuchs 2013 ABSTRACT This study examines two facets of the reception of Ovid’s Tristia in the 16th century: its commentary tradition and its adaptation by Latin poets. It lays the groundwork for a more comprehensive study of the Renaissance reception of the Tristia by providing a scholarly platform where there was none before (particularly with regard to the unedited, unpublished commentary tradition), and offers literary case studies of poetic postscripts to Ovid’s Tristia in order to explore the wider impact of Ovid’s exilic imaginary in 16th-century Europe. After a brief introduction, the second chapter introduces the three major commentaries on the Tristia printed in the Renaissance: those of Bartolomaeus Merula (published 1499, Venice), Veit Amerbach (1549, Basel), and Hecules Ciofanus (1581, Antwerp) and analyzes their various contexts, styles, and approaches to the text. The third chapter shows the commentators at work, presenting a more focused look at how these commentators apply their differing methods to the same selection of the Tristia, namely Book 2. These two chapters combine to demonstrate how commentary on the Tristia developed over the course of the 16th century: it begins from an encyclopedic approach, becomes focused on rhetoric, and is later aimed at textual criticism, presenting a trajectory that ii becomes increasingly focused and philological.