Network Congestion Control Using Netflow
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ngenius Collector Appliance Scalable, High-Capacity Appliance for Collection of Cisco Netflow and Other Flow Data
l DATA SHEET l nGenius Collector Appliance Scalable, High-Capacity Appliance for Collection of Cisco NetFlow and Other Flow Data Product Overview HIGHLIGHTS Deployed at key traffic aggregation locations, nGenius® Collectors extend the reach of the nGeniusONE® Service Assurance solution and are used primarily to generate flow‑based • Measure service responsiveness across statistics (metadata) in memory for specific traffic types. This NETSCOUT data source collects the network with up to 500 Cisco IP SLA metadata on IP SLA and IPPING protocols, flow data from NetFlow routers, link‑level statistics, synthetic transaction tests and utilization data from MIB‑II routers. • Scalable collection of up to 2 million Cisco NetFlow, IPFIX, Juniper J-Flow, Huawei® Listening passively on an Ethernet wire, nGenius Collectors examine specific traffic collected NetStream and sFlow flows per minute from flow‑enabled routers and switches (e.g., Cisco® NetFlow, Juniper® J-Flow, sFlow®, ® • Captures and stores Flow datagrams for NetStream ) and from IP SLA test results to generate a variety of statistics. In addition, Collectors historical deep-dive analysis can be configured to capture datagrams from Flow‑enabled routers and analyze them via datagram capture, which allows users to perform in‑depth capture and filtering. • Collects Flow data from up to 5,000 flow‑enabled router or switch interfaces Metrics from nGenius Collectors are retrieved through a managing nGenius for Flows Server per appliance for analysis, enabling display of utilization metrics, quality of service (QoS) breakdowns, and • Supports both IPv4 and IPv6 environments application breakdowns in nGenius for Flows and other tools in the nGeniusONE Service • Purpose-built hardware and virtual Assurance Solution. -

Application Note Pre-Deployment and Network Readiness Assessment Is
Application Note Contents Title Six Steps To Getting Your Network Overview.......................................................... 1 Ready For Voice Over IP Pre-Deployment and Network Readiness Assessment Is Essential ..................... 1 Date January 2005 Types of VoIP Overview Performance Problems ...... ............................. 1 This Application Note provides enterprise network managers with a six step methodology, including pre- Six Steps To Getting deployment testing and network readiness assessment, Your Network Ready For VoIP ........................ 2 to follow when preparing their network for Voice over Deploy Network In Stages ................................. 7 IP service. Designed to help alleviate or significantly reduce call quality and network performance related Summary .......................................................... 7 problems, this document also includes useful problem descriptions and other information essential for successful VoIP deployment. Pre-Deployment and Network IP Telephony: IP Network Problems, Equipment Readiness Assessment Is Essential Configuration and Signaling Problems and Analog/ TDM Interface Problems. IP Telephony is very different from conventional data applications in that call quality IP Network Problems: is especially sensitive to IP network impairments. Existing network and “traditional” call quality Jitter -- Variation in packet transmission problems become much more obvious with time that leads to packets being the deployment of VoIP service. For network discarded in VoIP -

Netflow Traffic Analyzer Real-Time Network Utilization and Bandwidth Monitoring
DATASHEET NetFlow Traffic Analyzer Real-Time Network Utilization and Bandwidth Monitoring An add-on to Network Performance Monitor (NPM), SolarWinds® NetFlow DOWNLOAD FREE TRIAL Traffic Analyzer (NTA) is a multi-vendor flow analysis tool designed to proactively reduce network downtime. NTA delivers actionable insights Fully Functional to help IT pros troubleshoot and optimize spend on bandwidth by better for 30 Days understanding the who, what, and where of traffic consumption. Solve practical operational infrastructure problems with actionable insights and save money with informed network investments. WHY CHOOSE NETFLOW TRAFFIC ANALYZER? • NTA collects and analyzes flow data from multiple vendors, including NetFlow v5 and v9, Juniper® J-Flow™, sFlow®, Huawei® NetStream™, and IPFIX. • NTA alerts you to changes in application traffic or if a device stops sending flow data. • NTA supports advanced application recognition with Cisco® NBAR2. • NTA shows pre- and post-policy CBQoS class maps, so you can optimize your CBQoS policies. • NTA can help you identify malicious or malformed traffic with port 0 monitoring. • NTA includes WLC network traffic analysis so you can see what’s using your wireless bandwidth. • NTA supplements Network Performance Monitor by helping to identify the cause of high bandwidth. Built on the Orion® Platform, NTA provides the ability to purchase and fully integrate with additional network monitoring modules (config management, WAN management, VoIP, device tracking, IP address management), as well as systems, storage, and virtualization management in a single web console. page 1 DATASHEET: NETFLOW TRAFFIC ANALYZER FEATURES New! VMware vSphere Distributed Switch (VDS) Support Comprehensive support for the VMware VDS, providing visibility within the switch fabric to your east-west VM traffic to help IT pros avoid service impacts when moving workloads. -

Netflow Optimizer™
NetFlow Optimizer™ Installation and Administration Guide Version 2.4.7 (Build 2.4.7.0.23) January 2017 © Copyright 2013-2017 NetFlow Logic Corporation. All rights reserved. Patents both issued and pending. Contents Overview ....................................................................................................................................................................... 3 How NetFlow Optimizer Works .................................................................................................................................. 3 How NFO Updater Works .......................................................................................................................................... 3 NetFlow Optimizer Installation Guide ......................................................................................................................... 4 Before You Install NFO ................................................................................................................................................ 4 Pre-Installation Checklist ........................................................................................................................................... 4 Minimum Requirements ............................................................................................................................................. 4 Supported Platforms .............................................................................................................................................. 4 Virtual Hardware -

Latency and Throughput Optimization in Modern Networks: a Comprehensive Survey Amir Mirzaeinnia, Mehdi Mirzaeinia, and Abdelmounaam Rezgui
READY TO SUBMIT TO IEEE COMMUNICATIONS SURVEYS & TUTORIALS JOURNAL 1 Latency and Throughput Optimization in Modern Networks: A Comprehensive Survey Amir Mirzaeinnia, Mehdi Mirzaeinia, and Abdelmounaam Rezgui Abstract—Modern applications are highly sensitive to com- On one hand every user likes to send and receive their munication delays and throughput. This paper surveys major data as quickly as possible. On the other hand the network attempts on reducing latency and increasing the throughput. infrastructure that connects users has limited capacities and These methods are surveyed on different networks and surrond- ings such as wired networks, wireless networks, application layer these are usually shared among users. There are some tech- transport control, Remote Direct Memory Access, and machine nologies that dedicate their resources to some users but they learning based transport control, are not very much commonly used. The reason is that although Index Terms—Rate and Congestion Control , Internet, Data dedicated resources are more secure they are more expensive Center, 5G, Cellular Networks, Remote Direct Memory Access, to implement. Sharing a physical channel among multiple Named Data Network, Machine Learning transmitters needs a technique to control their rate in proper time. The very first congestion network collapse was observed and reported by Van Jacobson in 1986. This caused about a I. INTRODUCTION thousand time rate reduction from 32kbps to 40bps [3] which Recent applications such as Virtual Reality (VR), au- is about a thousand times rate reduction. Since then very tonomous cars or aerial vehicles, and telehealth need high different variations of the Transport Control Protocol (TCP) throughput and low latency communication. -

Lab 6: Understanding Traditional TCP Congestion Control (HTCP, Cubic, Reno)
NETWORK TOOLS AND PROTOCOLS Lab 6: Understanding Traditional TCP Congestion Control (HTCP, Cubic, Reno) Document Version: 06-14-2019 Award 1829698 “CyberTraining CIP: Cyberinfrastructure Expertise on High-throughput Networks for Big Science Data Transfers” Lab 6: Understanding Traditional TCP Congestion Control Contents Overview ............................................................................................................................. 3 Objectives............................................................................................................................ 3 Lab settings ......................................................................................................................... 3 Lab roadmap ....................................................................................................................... 3 1 Introduction to TCP ..................................................................................................... 3 1.1 TCP review ............................................................................................................ 4 1.2 TCP throughput .................................................................................................... 4 1.3 TCP packet loss event ........................................................................................... 5 1.4 Impact of packet loss in high-latency networks ................................................... 6 2 Lab topology............................................................................................................... -

Adaptive Method for Packet Loss Types in Iot: an Naive Bayes Distinguisher
electronics Article Adaptive Method for Packet Loss Types in IoT: An Naive Bayes Distinguisher Yating Chen , Lingyun Lu *, Xiaohan Yu * and Xiang Li School of Computer and Information Technology, Beijing Jiaotong University, Beijing 100044, China; [email protected] (Y.C.); [email protected] (X.L.) * Correspondence: [email protected] (L.L.); [email protected] (X.Y.) Received: 31 December 2018; Accepted: 23 January 2019; Published: 28 January 2019 Abstract: With the rapid development of IoT (Internet of Things), massive data is delivered through trillions of interconnected smart devices. The heterogeneous networks trigger frequently the congestion and influence indirectly the application of IoT. The traditional TCP will highly possible to be reformed supporting the IoT. In this paper, we find the different characteristics of packet loss in hybrid wireless and wired channels, and develop a novel congestion control called NB-TCP (Naive Bayesian) in IoT. NB-TCP constructs a Naive Bayesian distinguisher model, which can capture the packet loss state and effectively classify the packet loss types from the wireless or the wired. More importantly, it cannot cause too much load on the network, but has fast classification speed, high accuracy and stability. Simulation results using NS2 show that NB-TCP achieves up to 0.95 classification accuracy and achieves good throughput, fairness and friendliness in the hybrid network. Keywords: Internet of Things; wired/wireless hybrid network; TCP; naive bayesian model 1. Introduction The Internet of Things (IoT) is a new network industry based on Internet, mobile communication networks and other technologies, which has wide applications in industrial production, intelligent transportation, environmental monitoring and smart homes. -

Flow-Tools Tutorial
Flow-tools Tutorial SANOG 6 Bhutan Agenda • Network flows • Cisco / Juniper implementation – NetFlow • Cisco / Juniper Configuration • flow-tools programs overview and examples from Abilene and Ohio- Gigapop Network Flows • Packets or frames that have a common attribute. • Creation and expiration policy – what conditions start and stop a flow. • Counters – packets,bytes,time. • Routing information – AS, network mask, interfaces. Network Flows • Unidirectional or bidirectional. • Bidirectional flows can contain other information such as round trip time, TCP behavior. • Application flows look past the headers to classify packets by their contents. • Aggregated flows – flows of flows. Unidirectional Flow with Source/Destination IP Key % telnet 10.0.0.2 10.0.0.1 login: 10.0.0.2 Active Flows Flow Source IP Destination IP 1 10.0.0.1 10.0.0.2 2 10.0.0.2 10.0.0.1 Unidirectional Flow with Source/Destination IP Key % telnet 10.0.0.2 % ping 10.0.0.2 login: 10.0.0.1 10.0.0.2 ICMP echo reply Active Flows Flow Source IP Destination IP 1 10.0.0.1 10.0.0.2 2 10.0.0.2 10.0.0.1 Unidirectional Flow with IP, Port,Protocol Key % telnet 10.0.0.2 % ping 10.0.0.2 login: 10.0.0.1 10.0.0.2 ICMP echo reply Active Flows Flow Source IP Destination IP prot srcPort dstPort 1 10.0.0.1 10.0.0.2 TCP 32000 23 2 10.0.0.2 10.0.0.1 TCP 23 32000 3 10.0.0.1 10.0.0.2 ICMP 0 0 4 10.0.0.2 10.0.0.1 ICMP 0 0 Bidirectional Flow with IP, Port,Protocol Key % telnet 10.0.0.2 % ping 10.0.0.2 login: 10.0.0.1 10.0.0.2 ICMP echo reply Active Flows Flow Source IP Destination IP prot srcPort -

Brocade Vyatta Network OS Data Sheet
DATA SHEET Brocade Vyatta Network OS HIGHLIGHTS A Network Operating System for the Way Forward • Offers a proven, modern network The Brocade® Vyatta® Network OS lays the foundation for a flexible, easy- operating system that accelerates the adoption of next-generation to-use, and high-performance network services architecture capable of architectures meeting current and future network demands. The operating system was • Creates an open, programmable built from the ground up to deliver robust network functionality that can environment to enhance be deployed virtually or as an appliance, and in concert with solutions differentiation, service quality, and from a large ecosystem of vendors, to address various Software-Defined competitiveness Networking (SDN) and Network Functions Virtualization (NFV) use cases. • Supports a broad ecosystem for With the Brocade Vyatta Network OS, organizations can bridge the gap optimal customization and service between traditional and new architectures, as well as leverage existing monetization investments and maximize operational efficiencies. Moreover, they can • Simplifies and automates network compose and deploy unique, new services that will drive differentiation functions to improve time to service, increase operational efficiency, and and strengthen competitiveness. reduce costs • Delivers breakthrough performance flexibility, performance, and operational and scale to meet the needs of any A Proven, Modern Operating efficiency, helping organizations create deployment System The Brocade Vyatta Network OS new service offerings and value. Since • Provides flexible deployment options separates the control and data planes in 2012, the benefits of this operating to support a wide variety of use cases software to fit seamlessly within modern system have been proven by the Brocade SDN and NFV environments. -

Introduction to Netflow
Introduction to Netflow Campus Network Design & Operations Workshop These materials are licensed under the Creative Commons Attribution-NonCommercial 4.0 International license (http://creativecommons.org/licenses/by-nc/4.0/) Last updated 14th December 2018 Agenda • Netflow – What it is and how it works – Uses and applications • Generating and exporting flow records • Nfdump and NfSen – Architecture – Usage • Lab What is a Network Flow • A set of related packets • Packets that belong to the same transport connection. e.g. – TCP, same src IP, src port, dst IP, dst port – UDP, same src IP, src port, dst IP, dst port – Some tools consider "bidirectional flows", i.e. A->B and B->A as part of the same flow http://en.wikipedia.org/wiki/Traffic_flow_(computer_networking) Simple flows = Packet belonging to flow X = Packet belonging to flow Y Cisco IOS Definition of a Flow • Unidirectional sequence of packets sharing: – Source IP address – Destination IP address – Source port for UDP or TCP, 0 for other protocols – Destination port for UDP or TCP, type and code for ICMP, or 0 for other protocols – IP protocol – Ingress interface (SNMP ifIndex) – IP Type of Service IOS: which of these six packets are in the same flows? Src IP Dst IP Protocol Src Port Dst Port A 1.2.3.4 5.6.7.8 6 (TCP) 4001 22 B 5.6.7.8 1.2.3.4 6 (TCP) 22 4001 C 1.2.3.4 5.6.7.8 6 (TCP) 4002 80 D 1.2.3.4 5.6.7.8 6 (TCP) 4001 80 E 1.2.3.4 8.8.8.8 17 (UDP) 65432 53 F 8.8.8.8 1.2.3.4 17 (UDP) 53 65432 IOS: which of these six packets are in the same flows? Src IP Dst IP Protocol Src Port Dst Port A 1.2.3.4 5.6.7.8 6 (TCP) 4001 22 B 5.6.7.8 1.2.3.4 6 (TCP) 22 4001 C 1.2.3.4 5.6.7.8 6 (TCP) 4002 80 D 1.2.3.4 5.6.7.8 6 (TCP) 4001 80 E 1.2.3.4 8.8.8.8 17 (UDP) 65432 53 F 8.8.8.8 1.2.3.4 17 (UDP) 53 65432 What about packets “C” and “D”? Flow Accounting • A summary of all the packets seen in a flow (so far): – Flow identification: protocol, src/dst IP/port.. -
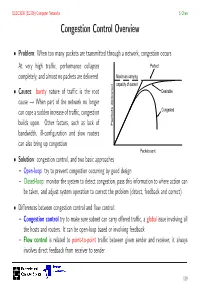
Congestion Control Overview
ELEC3030 (EL336) Computer Networks S Chen Congestion Control Overview • Problem: When too many packets are transmitted through a network, congestion occurs At very high traffic, performance collapses Perfect completely, and almost no packets are delivered Maximum carrying capacity of subnet • Causes: bursty nature of traffic is the root Desirable cause → When part of the network no longer can cope a sudden increase of traffic, congestion Congested builds upon. Other factors, such as lack of Packets delivered bandwidth, ill-configuration and slow routers can also bring up congestion Packets sent • Solution: congestion control, and two basic approaches – Open-loop: try to prevent congestion occurring by good design – Closed-loop: monitor the system to detect congestion, pass this information to where action can be taken, and adjust system operation to correct the problem (detect, feedback and correct) • Differences between congestion control and flow control: – Congestion control try to make sure subnet can carry offered traffic, a global issue involving all the hosts and routers. It can be open-loop based or involving feedback – Flow control is related to point-to-point traffic between given sender and receiver, it always involves direct feedback from receiver to sender 119 ELEC3030 (EL336) Computer Networks S Chen Open-Loop Congestion Control • Prevention: Different policies at various layers can affect congestion, and these are summarised in the table • e.g. retransmission policy at data link layer Transport Retransmission policy • Out-of-order caching -

The Effects of Different Congestion Control Algorithms Over Multipath Fast Ethernet Ipv4/Ipv6 Environments
Proceedings of the 11th International Conference on Applied Informatics Eger, Hungary, January 29–31, 2020, published at http://ceur-ws.org The Effects of Different Congestion Control Algorithms over Multipath Fast Ethernet IPv4/IPv6 Environments Szabolcs Szilágyi, Imre Bordán Faculty of Informatics, University of Debrecen, Hungary [email protected] [email protected] Abstract The TCP has been in use since the seventies and has later become the predominant protocol of the internet for reliable data transfer. Numerous TCP versions has seen the light of day (e.g. TCP Cubic, Highspeed, Illinois, Reno, Scalable, Vegas, Veno, etc.), which in effect differ from each other in the algorithms used for detecting network congestion. On the other hand, the development of multipath communication tech- nologies is one today’s relevant research fields. What better proof of this, than that of the MPTCP (Multipath TCP) being integrated into multiple operating systems shortly after its standardization. The MPTCP proves to be very effective for multipath TCP-based data transfer; however, its main drawback is the lack of support for multipath com- munication over UDP, which can be important when forwarding multimedia traffic. The MPT-GRE software developed at the Faculty of Informatics, University of Debrecen, supports operation over both transfer protocols. In this paper, we examine the effects of different TCP congestion control mechanisms on the MPTCP and the MPT-GRE multipath communication technologies. Keywords: congestion control, multipath communication, MPTCP, MPT- GRE, transport protocols. 1. Introduction In 1974, the TCP was defined in RFC 675 under the Transmission Control Pro- gram name. Later, the Transmission Control Program was split into two modular Copyright © 2020 for this paper by its authors.