Type-Safe Java Bytecode Modification Library Based on Javassist
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Oracle Application Server 10G R3 (10.1.3.1) New Features Overview
Oracle Application Server 10g R3 (10.1.3.1) New Features Overview An Oracle White Paper October 2006 Oracle Application Server 10gR3 New Features Overview 1.0 Introduction................................................................................................. 4 2.0 Standards Support: J2EE Infrastructure ................................................. 5 2.1 Presentation Tier – Java Server Pages and JavaServer Faces........... 6 2.2 Business Tier – Enterprise Java Beans................................................ 7 2.3 Persistence - TopLink............................................................................ 8 2.3.1 Oracle TopLink............................................................................... 8 2.3.2 EJB 3.0 Persistence......................................................................... 9 2.3.3 Object-XML.................................................................................... 9 2.4 Data Sources and Transactions ............................................................ 9 2.4.1 Data Sources.................................................................................... 9 2.4.2 Transactions................................................................................... 10 2.5 Java 2 Connector Architecture ........................................................... 10 2.6 Security................................................................................................... 11 2.6.1 Core Container............................................................................. -

Oracle® Toplink Release Notes Release 12C (12.1.2)
Oracle® TopLink Release Notes Release 12c (12.1.2) E40213-01 June 2013 This chapter describes issues associated with Oracle TopLink. It includes the following topics: ■ Section 1, "TopLink Object-Relational Issues" ■ Section 2, "Oracle Database Extensions with TopLink" ■ Section 3, "Allowing Zero Value Primary Keys" ■ Section 4, "Managed Servers on Sybase with JCA Oracle Database Service" ■ Section 5, "Logging Configuration with EclipseLink Using Container Managed JPA" ■ Section 6, "Documentation Accessibility" 1 TopLink Object-Relational Issues This section contains information on the following issues: ■ Section 1.1, "Cannot set EclipseLink log level in WLS System MBean Browser" ■ Section 1.2, "UnitOfWork.release() not Supported with External Transaction Control" ■ Section 1.3, "Returning Policy for UPDATE with Optimistic Locking" ■ Section 1.4, "JDBC Drivers returning Timestamps as Strings" ■ Section 1.5, "Unit of Work does not add Deleted Objects to Change Set" 1.1 Cannot set EclipseLink log level in WLS System MBean Browser Use Oracle Enterprise Manager to set the EclipseLink log level; do not use the WLS System MBean Browser to complete this action. 1.2 UnitOfWork.release() not Supported with External Transaction Control A unit of work synchronized with a Java Transaction API (JTA) will throw an exception if it is released. If the current transaction requires its changes to not be persisted, the JTA transaction must be rolled back. When in a container-demarcated transaction, call setRollbackOnly() on the EJB/session context: @Stateless public class MySessionBean { @Resource SessionContext sc; public void someMethod() { ... 1 sc.setRollbackOnly(); } } When in a bean-demarcated transaction then you call rollback() on the UserTransaction obtained from the EJB/session context: @Stateless @TransactionManagement(TransactionManagementType.BEAN) public class MySessionBean implements SomeInterface { @Resource SessionContext sc; public void someMethod() { sc.getUserTransaction().begin(); .. -

Actors at Work Issue Date: 2016-12-15 Actors at Work Behrooz Nobakht
Cover Page The handle http://hdl.handle.net/1887/45620 holds various files of this Leiden University dissertation Author: Nobakht, Behrooz Title: Actors at work Issue Date: 2016-12-15 actors at work behrooz nobakht 2016 Leiden University Faculty of Science Leiden Institute of Advanced Computer Science Actors at Work Actors at Work Behrooz Nobakht ACTORS AT WORK PROEFSCHRIFT ter verkrijging van de graad van doctor aan de Universiteit Leiden op gezag van de Rector Magnificus prof. dr. C. J. J. M. Stolker, volgens besluit van het College voor Promoties te verdedigen op donderdag 15 december 2016 klokke 11.15 uur door Behrooz Nobakht geboren te Tehran, Iran, in 1981 Promotion Committee Promotor: Prof. Dr. F.S. de Boer Co-promotor: Dr. C. P. T. de Gouw Other members: Prof. Dr. F. Arbab Dr. M.M. Bonsangue Prof. Dr. E. B. Johnsen University of Oslo, Norway Prof. Dr. M. Sirjani Reykjavik University, Iceland The work reported in this thesis has been carried out at the Center for Mathematics and Computer Science (CWI) in Amsterdam and Leiden Institute of Advanced Computer Science at Leiden University. This research was supported by the European FP7-231620 project ENVISAGE on Engineering Virtualized Resources. Copyright © 2016 by Behrooz Nobakht. All rights reserved. October, 2016 Behrooz Nobakht Actors at Work Actors at Work, October, 2016 ISBN: 978-94-028-0436-2 Promotor: Prof. Dr. Frank S. de Boer Cover Design: Ehsan Khakbaz <[email protected]> Built on 2016-11-02 17:00:24 +0100 from 397717ec11adfadec33e150b0264b0df83bdf37d at https://github.com/nobeh/thesis using: This is pdfTeX, Version 3.14159265-2.6-1.40.16 (TeX Live 2015/Debian) kpathsea version 6.2.1 Leiden University Leiden Institute of Advanced Computer Science Faculty of Science Niels Bohrweg 1 2333 CA and Leiden Contents I Introduction1 1 Introduction 3 1.1 Objectives and Architecture . -

1 Shounak Roychowdhury, Ph.D
Shounak Roychowdhury, Ph.D. 10213 Prism Dr., Austin, TX, 78726 || 650-504-8365 || email: [email protected] Profile • Software development and research experience at Oracle and LG Electronics. • Deep understanding of data science methods: machine learning; probability and statistics. • 5 US patents and 40+ peer reviewed publications in international conferences and top refereed journals Research Interests • Published research papers on computational intelligence, neural networks and fuzzy theory, numerical optimization, and natural language processing, and information theory. Education • Ph.D. (Computer Engineering), University of Texas at Austin, Austin, TX, (Dec. 2013) o Dissertation: A Mixed Approach to Spectrum-based Fault Localization Using Information Theoretic Foundations. (Machine Learning in Software Engineering) • M.S. (Computer Science), University of Tulsa, Tulsa, OK, (May 1997) o Thesis: Encoding and Decoding of Fuzzy Rules Patents • Chaos washing systems and a method of washing thereof (US Patent #5,560,230) • System and method for generating fuzzy decision trees (US Patent #7,197,504) • Method for extracting association rules from transactions in a database (U.S. Patent # 7,370,033) • Expediting K-means cluster analysis data mining using subsample elimination preprocessing (U.S. Patent # 8,229,876) • Bayes-like classifier with fuzzy likelihood (U.S. Patent # 8,229,875) Computer Languages • Python, Java, C/C++, MATLAB, R, SQL, PL/SQL, Perl, Ruby, Tcl/Tk Teaching Experience Adjunct Faculty Texas State University 2017- Present Professional Experience Hewlett Packard Enterprise, Austin, TX (Oct 2018 - present) Expert Technologist • Executed software development processes for composable rack team of HPE’s OneView cloud management system. • Developed a Python-based system to test the scalability of OneView connections across multiple layers of Plexxi switches. -

Oracle Glassfish Server Application Development Guide Release 3.1.2 E24930-01
Oracle GlassFish Server Application Development Guide Release 3.1.2 E24930-01 February 2012 This Application Development Guide describes how to create and run Java Platform, Enterprise Edition (Java EE platform) applications that follow the open Java standards model for Java EE components and APIs in the Oracle GlassFish Server environment. Topics include developer tools, security, and debugging. This book is intended for use by software developers who create, assemble, and deploy Java EE applications using Oracle servers and software. Oracle GlassFish Server Application Development Guide, Release 3.1.2 E24930-01 Copyright © 2012, Oracle and/or its affiliates. All rights reserved. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable: U.S. GOVERNMENT RIGHTS Programs, software, databases, and related documentation and technical data delivered to U.S. Government customers are "commercial computer software" or "commercial technical data" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. -

Advanced-Java.Pdf
Advanced java i Advanced java Advanced java ii Contents 1 How to create and destroy objects 1 1.1 Introduction......................................................1 1.2 Instance Construction.................................................1 1.2.1 Implicit (Generated) Constructor.......................................1 1.2.2 Constructors without Arguments.......................................1 1.2.3 Constructors with Arguments........................................2 1.2.4 Initialization Blocks.............................................2 1.2.5 Construction guarantee............................................3 1.2.6 Visibility...................................................4 1.2.7 Garbage collection..............................................4 1.2.8 Finalizers...................................................5 1.3 Static initialization..................................................5 1.4 Construction Patterns.................................................5 1.4.1 Singleton...................................................6 1.4.2 Utility/Helper Class.............................................7 1.4.3 Factory....................................................7 1.4.4 Dependency Injection............................................8 1.5 Download the Source Code..............................................9 1.6 What’s next......................................................9 2 Using methods common to all objects 10 2.1 Introduction...................................................... 10 2.2 Methods equals and hashCode........................................... -

Jpype Documentation Release 0.7.0
JPype Documentation Release 0.7.0 Steve Menard, Luis Nell and others Jul 22, 2019 Contents 1 Parts of the documentation 3 1.1 Installation................................................3 1.2 User Guide................................................6 1.3 QuickStart Guide............................................. 17 1.4 API Reference.............................................. 27 1.5 JImport.................................................. 34 1.6 Changelog................................................ 36 1.7 Developer Guide............................................. 40 2 Indices and tables 53 Python Module Index 55 Index 57 i ii JPype Documentation, Release 0.7.0 JPype is a Python module to provide full access to Java from within Python. It allows Python to make use of Java only libraries, exploring and visualization of Java structures, development and testing of Java libraries, scientific computing, and much more. By gaining the best of both worlds using Python for rapid prototyping and Java for strong typed production code, JPype provides a powerful environment for engineering and code development. This is achieved not through re-implementing Python, as Jython/JPython has done, but rather through interfacing at the native level in both virtual machines. This shared memory based approach achieves decent computing preformance, while providing the access to the entirety of CPython and Java libraries. Contents 1 JPype Documentation, Release 0.7.0 2 Contents CHAPTER 1 Parts of the documentation 1.1 Installation JPype is available either as a pre-compiled binary for Anaconda, or may be build from source though several methods. 1.1.1 Binary Install JPype can be installed as pre-compiled binary if you are using the Anaconda Python stack. Binaries are available for Linux, OSX, ad windows are available on conda-forge. -

Java Optimizations Using Bytecode Templates
FACULDADE DE ENGENHARIA DA UNIVERSIDADE DO PORTO Java Optimizations Using Bytecode Templates Rubén Ramos Horta Mestrado Integrado em Engenharia Informática e Computação Supervisor: Professor Doutor João Manuel Paiva Cardoso July 28, 2016 c Rubén Ramos Horta, 2016 Java Optimizations Using Bytecode Templates Rubén Ramos Horta Mestrado Integrado em Engenharia Informática e Computação July 28, 2016 Resumo Aplicações móveis e embebidas funcionam em ambientes com poucos recursos e que estão sujeitos a constantes mudanças no seu contexto operacional. Estas características dificultam o desenvolvi- mento deste tipo de aplicações pois a volatilidade e as limitações de recursos levam muitas vezes a uma diminuição do rendimento e a um potencial aumento do custo computacional. Além disso, as aplicações que têm como alvo ambientes móveis e embebidos (por exemplo, Android) necessitam de adaptações e otimizações para fiabilidade, manutenção, disponibilidade, segurança, execução em tempo real, tamanho de código, eficiência de execução e também consumo de energia. Esta dissertação foca-se na otimização, em tempo de execução, de programas Java, com base na aplicação de otimizações de código baseadas na geração de bytecodes em tempo de execução, usando templates. Estes templates, fornecem geração de bytecodes usando informação apenas disponível em tempo de execução. Este artigo propõe uma estratégia para o desenvolvimento desses templates e estuda o seu impacto em diferentes plataformas. i ii Resumen Las aplicaciones móviles y embedded trabajan en entornos limitados de recursos y están sujetas a constantes cambios de escenario. Este tipo de características desafían el desarrollo de este tipo de aplicaciones en términos de volatibilidad y limitación de recursos que acostumbran a afec- tar al rendimiento y también producen un incremento significativo en el coste computacional. -

Oracle® Fusion Middleware Solutions Guide for Oracle Toplink 12C (12.1.2) E28610-02
Oracle® Fusion Middleware Solutions Guide for Oracle TopLink 12c (12.1.2) E28610-02 August 2013 This document describes a number of scenarios, or use cases, that illustrate TopLink features and typical TopLink development processes. Oracle Fusion Middleware Solutions Guide for Oracle TopLink, 12c (12.1.2) E28610-02 Copyright © 2013, Oracle and/or its affiliates. All rights reserved. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable: U.S. GOVERNMENT RIGHTS Programs, software, databases, and related documentation and technical data delivered to U.S. Government customers are "commercial computer software" or "commercial technical data" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, the use, duplication, disclosure, modification, and adaptation shall be subject to the restrictions and license terms set forth in the applicable Government contract, and, to the extent applicable by the terms of the Government contract, the additional rights set forth in FAR 52.227-19, Commercial Computer Software License (December 2007). -

Chargeurs De Classes Java (Classloader)
http://membres-liglab.imag.fr/donsez/cours Chargeurs de classes Java (ClassLoader) Didier Donsez Université Joseph Fourier - Grenoble 1 PolyTech’Grenoble - LIG/ADELE [email protected] [email protected] 06/06/2009 Licence Cette présentation est couverte par le contrat Creative Commons By NC ND http://creativecommons.org/licenses/by-nc-nd/2.0/fr/ Didier Donsez, 2002-2009, ClassLoaders Donsez,2002-2009, Didier 2 06/06/2009 Kequoi ca un chargeur de classes ? Son rôle est 1) de charger le bytecode d’une classe depuis un artéfact (archive Java, répertoire distant …) 2) communiquer le bytecode à la machine virtuelle Didier Donsez, 2002-2009, ClassLoaders Donsez,2002-2009, Didier 4 06/06/2009 Pourquoi utiliser les chargeurs de classes Classes non présentes dans le CLASSPATH URLClassLoader, AppletClassLoader, … ex: WEB-INF/classes et WEB-INF/lib d’une WebApp ex: CODEBASE d’une applet, … Déchargement et Mise à jour du bytecode lors de l’exécution de la VM (runtime) Chargeurs de OSGi Modification du ByteCode à la volée au chargement Instrumentation AOP (Aspect Oriented Programming) BCEL, ASM Protection Chargement de ressources associées à la classe properties, images, … Recherche de Service Providers ou de Drivers META-INF/services (java.util.ServiceLoader de 6.0) Didier Donsez, 2002-2009, ClassLoaders Donsez,2002-2009, Didier 5 06/06/2009 Principe de la délégation (Java 2) Tout chargeur a un chargeur parent sauf le chargeur primordial Tout chargeur vérifie si la classe à charger n’a pas déjà été chargée par un chargeur -

How Java Works JIT, Just in Time Compiler Loading .Class Files The
How Java works JIT, Just In Time Compiler ● The java compiler takes a .java file and generates a .class file ● JVM ultimately translates bytecode into native code, each time ➤ The .class file contains Java bytecodes, the assembler the same bytecodes are processed, the translation into native language for Java programs code must be made ➤ Bytecodes are executed in a JVM (java virtual machine), ➤ If we can cache translated code we can avoid re-translating the valid bytecodes are specified by Sun the same bytecode sequence • What if third parties create platform/OS specific codes? ➤ Why not just translate the entire .java program into native code? ● The JVM interprets the bytecodes ➤ JVM is platform/OS specific, must ultimately run the code ● Still need the JVM, the JIT works in conjunction with the JVM, not in place of it ➤ Different JVMs will have different performance, JITs are part of the overall JDK/Java performance ● How are classes loaded into the JVM? Can this be thwarted? Duke CPS 108 14.1 Duke CPS 108 14.2 Loading .class files The ClassLoader ● The bytecode verifier “proves theorems” about the bytecodes ● The “Primordial” loader is built-in to the JVM being loaded into the JVM ➤ Sometimes called the “default” loader, but it’s not ➤ These bytecodes may come from a non-Java source, e.g., extensible or customizable the way other loaders are compile Ada into bytecodes (why?) ➤ Loads classes from the platform on which the JVM runs ● This verification is a static analysis of properties such as: (what are loader and JVM written in?) ➤ -
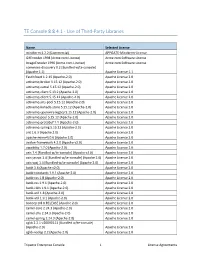
TE Console 8.8.4.1 - Use of Third-Party Libraries
TE Console 8.8.4.1 - Use of Third-Party Libraries Name Selected License mindterm 4.2.2 (Commercial) APPGATE-Mindterm-License GifEncoder 1998 (Acme.com License) Acme.com Software License ImageEncoder 1996 (Acme.com License) Acme.com Software License commons-discovery 0.2 [Bundled w/te-console] (Apache 1.1) Apache License 1.1 FastInfoset 1.2.15 (Apache-2.0) Apache License 2.0 activemQ-broker 5.15.12 (Apache-2.0) Apache License 2.0 activemQ-camel 5.15.12 (Apache-2.0) Apache License 2.0 activemQ-client 5.13.2 (Apache-2.0) Apache License 2.0 activemQ-client 5.15.12 (Apache-2.0) Apache License 2.0 activemQ-jms-pool 5.15.12 (Apache-2.0) Apache License 2.0 activemQ-kahadb-store 5.15.12 (Apache-2.0) Apache License 2.0 activemQ-openwire-legacy 5.15.12 (Apache-2.0) Apache License 2.0 activemQ-pool 5.15.12 (Apache-2.0) Apache License 2.0 activemQ-protobuf 1.1 (Apache-2.0) Apache License 2.0 activemQ-spring 5.15.12 (Apache-2.0) Apache License 2.0 ant 1.6.3 (Apache 2.0) Apache License 2.0 apache-mime4j 0.6 (Apache 2.0) Apache License 2.0 avalon-framework 4.2.0 (Apache v2.0) Apache License 2.0 awaitility 1.7.0 (Apache-2.0) Apache License 2.0 axis 1.4 [Bundled w/te-console] (Apache v2.0) Apache License 2.0 axis-jaxrpc 1.4 [Bundled w/te-console] (Apache 2.0) Apache License 2.0 axis-saaj 1.4 [Bundled w/te-console] (Apache 2.0) Apache License 2.0 batik 1.6 (Apache v2.0) Apache License 2.0 batik-constants 1.9.1 (Apache-2.0) Apache License 2.0 batik-css 1.8 (Apache-2.0) Apache License 2.0 batik-css 1.9.1 (Apache-2.0) Apache License 2.0 batik-i18n 1.9.1 (Apache-2.0)