Comodo Certificate Manager Version 5.4
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Analysis Report Blackenergy
Analysis Report iTrust-Analysis-001 May 2016 BlackEnergy - Malware for Cyber-Physical Attacks About iTrust iTrust is a multidisciplinary research centre located in the Singapore University of Technology and Design (SUTD), established collaboratively by SUTD and the Ministry of Defence, Singapore (MINDEF). The focus of iTrust is on cyber security, spanning across three research areas: a. Cyber Physical System (CPS); b. Enterprise Networking / Security; and c. Internet of Things (IoT). iTrust researchers focus on the development of advanced tools and methodologies to ensure security and safety of current and future cyber physical systems and Internet of Things (IoT) systems. Systems of interest include large infrastructure of national importance such as power grid, water treatment, and oil refineries as well as cyber-devices such as smart watches, pacemakers, defibrillators, insulin pumps, and VNS implants. Cyber physical systems is one of the many areas we are working on. The focus of the proposed research is to improve our understanding of cyber threats to CPSs and to develop and experiment with strategies to mitigate such threats. Our approach is based on well understood technical foundations borrowed from the interdisciplinary fields of control theory, artificial intelligence, game theory, networking, and software engineering. The techniques propose will be evaluated against, and demonstrated in our Secure Water Treatment (SWaT) Testbed, Water Distribution System (WADI) testbed, and Electric Power and Intelligent Control (EPIC) testbed. Similarly, shielded room laboratory for IoT research. iTrust researchers are drawn from across SUTD and with a strong collaboration with Massachusetts Institute of Technology (MIT), enrich the depth, breadth, and quality of research. -

Giant List of Web Browsers
Giant List of Web Browsers The majority of the world uses a default or big tech browsers but there are many alternatives out there which may be a better choice. Take a look through our list & see if there is something you like the look of. All links open in new windows. Caveat emptor old friend & happy surfing. 1. 32bit https://www.electrasoft.com/32bw.htm 2. 360 Security https://browser.360.cn/se/en.html 3. Avant http://www.avantbrowser.com 4. Avast/SafeZone https://www.avast.com/en-us/secure-browser 5. Basilisk https://www.basilisk-browser.org 6. Bento https://bentobrowser.com 7. Bitty http://www.bitty.com 8. Blisk https://blisk.io 9. Brave https://brave.com 10. BriskBard https://www.briskbard.com 11. Chrome https://www.google.com/chrome 12. Chromium https://www.chromium.org/Home 13. Citrio http://citrio.com 14. Cliqz https://cliqz.com 15. C?c C?c https://coccoc.com 16. Comodo IceDragon https://www.comodo.com/home/browsers-toolbars/icedragon-browser.php 17. Comodo Dragon https://www.comodo.com/home/browsers-toolbars/browser.php 18. Coowon http://coowon.com 19. Crusta https://sourceforge.net/projects/crustabrowser 20. Dillo https://www.dillo.org 21. Dolphin http://dolphin.com 22. Dooble https://textbrowser.github.io/dooble 23. Edge https://www.microsoft.com/en-us/windows/microsoft-edge 24. ELinks http://elinks.or.cz 25. Epic https://www.epicbrowser.com 26. Epiphany https://projects-old.gnome.org/epiphany 27. Falkon https://www.falkon.org 28. Firefox https://www.mozilla.org/en-US/firefox/new 29. -

Ant Download Manager (Antdm) V.2.3.2
English Ant Download Manager (AntDM) v.2.4.0 Some of the contents in this manual may differ from the software, as software development continues. User Guide 2021 Table of Contents Overview ....................................................................................................................................................4 System Requirements .........................................................................................................................5 Installation ..................................................................................................................................................6 Uninstall .............................................................................................................................................11 Premium Link Generators (Debrids) .......................................................................................................12 Torrents ....................................................................................................................................................14 Browser Integration ..................................................................................................................................15 Google Chrome .................................................................................................................................16 Chromium Clones ........................................................................................................................17 Mozilla Firefox ....................................................................................................................................18 -

Internet Security 6.3 Software Version 6.3
Comodo Internet Security 6.3 Software Version 6.3 User Guide Guide Version 6.3.111114 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 United States Comodo Internet Security 6.3 - User Guide Table of Contents 1.Introduction to Comodo Internet Security...............................................................................................................................6 1.1.Special Features...............................................................................................................................................................10 1.2.System Requirements.......................................................................................................................................................13 1.3.Installation.........................................................................................................................................................................13 1.3.1.CIS Premium - Installation........................................................................................................................................14 1.3.2.CIS Pro - Installation and Activation.........................................................................................................................27 1.3.3.CIS Complete - Installation and Activation...............................................................................................................39 1.3.4.Activating CIS Pro/Complete Services after Installation...........................................................................................52 -

Comodo Internet Security User Guide
Comodo IceDragon Software Version 21.0 User Guide Guide Version 21.0.060713 Comodo Security Solutions 1255 Broad Street STE 100 Clifton, NJ 07013 Comodo IceDragon – User Guide Table of Contents 1. Comodo IceDragon – Introduction........................................................................................................................................... 4 2. System Requirements............................................................................................................................................................... 6 3. Downloading And Installing Comodo IceDragon...................................................................................................................6 4. The Basics............................................................................................................................................................................... 11 4.1.Starting Comodo IceDragon.............................................................................................................................................. 11 4.2.Setting IceDragon as your Default Browser.......................................................................................................................12 4.3.Setting up Your Homepage............................................................................................................................................... 13 4.4.Searching the Internet...................................................................................................................................................... -

E D G E the Outer
September 2012 The Outer Edge Page 1 25th Anniversary Event issue The Outer E Whole No. 304 ISSN 1055-4399 September 2012 Vol. 26, No. 2 d g e The Friendly Computer Club Helping Make Computers Friendly. On the Web at www.cipcug.org COMMAND.COM Attendance at the By Jim Brown, President August general meeting: “Promoting the Harmony of Computer Education, and Camaraderie” 54 members and guests. We welcome two new members. am writing this column with much joy and anticipation as we ap- proach our September meeting date and our 25 (+1) Anniversary Cele- bration. Because of the dedication and hard work of a small group of To Contact CIPCUG individuals and families our computer group has evolved to the largest Icomputer group in this area and has received many awards and recognition The Outer Edge......................805-485-7121 General Information………...805-289-3960 from computer associations — all due to the dedication, focus, and hard work Mailing Address...P.O. Box 51354, Oxnard, CA of our members. We will honor the early members who had the foresight and 93031-1354 dedication to succeed. On the Web: cipcug.org Our September meeting is a time to remember and cele- On Facebook: Facebook.com/groups/cipcug brate our history and success. This is an event that you bring your family members and friends to for the entertainment and ambiance as we remember where the computer club has been and what its future may be. Brown Consider this event as a family event. TOE wins a top Here is what you should know. -

Comodo Internet Security User Guide
Comodo IceDragon Software Version 38.0 User Guide Guide Version 38.0.070315 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Comodo IceDragon - User Guide Table of Contents 1. Comodo IceDragon – Introduction........................................................................................................................................... 4 2. System Requirements............................................................................................................................................................... 6 3. Downloading And Installing Comodo IceDragon....................................................................................................................6 4. The Basics................................................................................................................................................................................ 11 4.1.Starting Comodo IceDragon.............................................................................................................................................. 11 4.2.Setting IceDragon as your Default Browser.......................................................................................................................12 4.3.Setting up Your Homepage............................................................................................................................................... 13 4.4.Searching the Internet...................................................................................................................................................... -

Ccleaner - Version History
CCleaner - Version History For Home For Business Download Support Company Home Products CCleaner Version History CCleaner Version History v5.02.5101 (26 Jan 2015) Download - Improved Firefox Local Storage and Cookie cleaning. Features - Improved Google Chrome 64-bit support. FAQ - Improved Firefox Download History analysis and cleaning. Screenshots - Optimized Disk Analyzer scanning process. Reviews - Improved detection and cleaning of portable browsers. Update - Updated various translations. - Minor GUI Improvements. Help - Minor bug fixes. v5.01.5075 (18 Dec 2014) Products - New Disk Analyzer tool. - Improved Firefox 34 cleaning. CCleaner - Improved Opera History cleaning. - Optimized Memory and CPU usage. CCleaner Network Edition - Improved localization support. Defraggler - Minor GUI Improvements. - Minor bug fixes. Recuva Speccy v5.00.5050 (25 Nov 2014) - New improved GUI. - Improved internal architecture for better performance. - Added Google Chrome plugin management. Email Newsletter - Improved Google Chrome Startup item detection. - Optimized automatic updates for Pro version. - Improved system restore detection routine. - Updated exception handling and reporting architecture. - Optimized 64-bit builds on Windows 8, 8.1 and 10. - Updated various translations. Product News - Many performance improvements and bug fixes. v4.19.4867 (24 Oct 2014) February 3, 2015 - Added Windows 10 Preview compatibility. CCleaner for Android v1.07 - Improved Opera 25 Cache cleaning. Now with root uninstall! - Improved exception handling and reporting architecture. - Improved Auto-Update checking process. January 26, 2015 - Updated various translations. CCleaner v5.02 - Minor GUI Improvements. Improved Firefox local storage and - Minor bug fixes. cookie cleaning! v4.18.4844 (26 Sep 2014) January 21, 2015 - Added Active System Monitoring for Free users Speccy v1.28 - Improved Firefox Saved Password cleaning. -
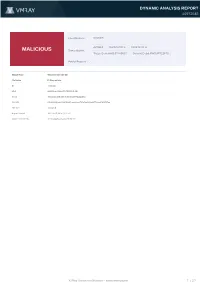
MALICIOUS Threat Names: Trojan.Generickd.37460607 Generic.Delph.PWS.FF722F75
DYNAMIC ANALYSIS REPORT #6972548 Classifications: Spyware AZORult Mal/Generic-S C2/Generic-A MALICIOUS Threat Names: Trojan.GenericKD.37460607 Generic.Delph.PWS.FF722F75 Verdict Reason: - Sample Type Windows Exe (x86-32) File Name Pi Request.exe ID #2651190 MD5 040026c9c18e8dc7ffc73f3790dbdf3b SHA1 70716c50c283b59eb9fd3137c68f9ff8a8824f56 SHA256 0768f66b3f6ee8f9f32520837cee96da8d725c789d82ba16771bbad740b737ee File Size 456.00 KB Report Created 2021-08-23 14:07 (UTC+2) Target Environment win10_64_th2_en_mso2016 | exe X-Ray Vision for Malware - www.vmray.com 1 / 37 DYNAMIC ANALYSIS REPORT #6972548 OVERVIEW VMRay Threat Identifiers (23 rules, 99 matches) Score Category Operation Count Classification 5/5 YARA Malicious content matched by YARA rules 1 Spyware • Rule "Azorult_Generic" from ruleset "Malware" has matched on a memory dump for (process #2) pi request.exe. 5/5 Data Collection Tries to read cached credentials of various applications 1 Spyware • Tries to read sensitive data of: Chromium, Sputnik, FileZilla, Pidgin, Comodo Dragon, Vivaldi, Torch, WinSCP, CocCoc, Chrome Canar... ...t Explorer / Edge, Google Chrome, Chedot, Comodo IceDragon, Cyberfox, Orbitum, Amigo, Mozilla Firefox, Kometa, CentBrowser, 7Star. 4/5 Antivirus Malicious content was detected by heuristic scan 2 - • Built-in AV detected the sample itself as "Trojan.GenericKD.37460607". • Built-in AV detected a memory dump of (process #2) pi request.exe as "Generic.Delph.PWS.FF722F75". 4/5 Reputation Known malicious file 1 - • Reputation analysis labels the sample itself as "Mal/Generic-S". 4/5 Reputation Contacts known malicious URL 1 - • Reputation analysis labels the URL "208.167.239.179/index.php" which was contacted by (process #2) pi request.exe as "C2/Generic-A". 2/5 Data Collection Reads sensitive browser data 23 - • (Process #2) pi request.exe tries to read sensitive data of web browser "Mozilla Firefox" by file. -
Download Ice Dragon Browser for Windows 7 Get to Know Comodo Ice Dragon
download ice dragon browser for windows 7 Get to Know Comodo Ice Dragon. Authentication is at the heart of trust � it's the process of confirming that something or someone is genuine. Extended Validation SSL Certificates � provide the highest level of business authentication available according to standards set forth by the CA/Browser Forum. The green HTTPS browser address bar assures visitors they are interacting with a verified business on a secured domain Secure E-Mail � provides assurance of who e-mail really came from and that it has not been read or altered during transmission. Two-Factor Authentication � provides stronger authentication of people attempting to log in to systems, such as electronic banking, webmail or collaboration applications. Code-Signing Certificates � provide assurance of a software publisher's identity and that a software program being installed has not been modified or altered since creation. Verification Engine � provides visual verification that a website is a legitimate, rather than an impersonated/phishing site, and that the site's SSL certificate includes business validation. Content Verification Certificates � provide authentication of company logos, login boxes, order forms, authorized to accept credit card indicators, rate and price information, and other critical website content. Encrypting sensitive information at all stages of its lifecycle is a proven method of keeping it safe from hackers. Strong Public Key Infrastructure (PKI) encryption through digital certificates ensures that the encrypted information can only be used by authorized parties. Digital Certificates Servers of all types exchanging information over the Internet use SSL/Digital Certificates to create a private, encrypted channel of communications with those accessing them, preventing unauthorized access of that information by hackers. -

Comodo Icedragon Keyboard Shortcut Keys {120+Complete List}
4/23/2021 Comodo IceDragon keyboard shortcut keys {120+Complete List} Shortcut Buzz Menu Comodo IceDragon Keyboard Shortcut Keys {120+Complete List} April 21, 2021 by Martha Jonas Comodo IceDragon: It is a Firefox-based open-source web browser developed by Comodo Group. Comodo IceDragon aims to be faster and more secure than Firefox. From the article, we learn the detailed Comodo IceDragon keyboard shortcut keys. Let’s get into this article!! Comodo IceDragon Logo Last updated on April 19, 2021. Download Comodo IceDragon Shortcuts for Ofine Study Here: Comodo IceDragon.pdf Navigate Through Webpages shortcuts: Shortcut Function Alt + ← It is used for arrow back. https://shortcutbuzz.com/comodo-icedragon-keyboard-shortcut-keys/ 1/16 4/23/2021 Comodo IceDragon keyboard shortcut keys {120+Complete List} Shortcut Function Backspace Helps with the back option. Alt + → Use this key for arrow forward. Shift + Backspace It will forward. Alt + Home Takes to home. Ctrl + O This key will open the le. F5 Helps to Reload. or Ctrl + R Ctrl + F5 Used for Reload (Override cache). or Ctrl + Shift + R Esc It will stop loading. View, Print, and Save Current Page shortcuts: Shortcut Function End Helps to go to the Bottom of the Page. Home It will go to Top of the Page. https://shortcutbuzz.com/comodo-icedragon-keyboard-shortcut-keys/ 2/16 4/23/2021 Comodo IceDragon keyboard shortcut keys {120+Complete List} Shortcut Function F6 This key will Move to the Next Frame. Shift + F6 Helps to Move to the Previous Frame. Ctrl + P Used to print. Ctrl + S It will Save Page As. -
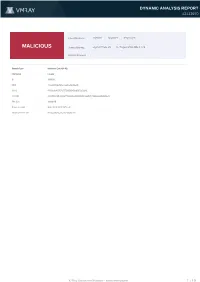
MALICIOUS Threat Names: Agent Tesla V3 IL:Trojan.Msilzilla.1773
DYNAMIC ANALYSIS REPORT #2113970 Classifications: Injector Spyware Keylogger MALICIOUS Threat Names: Agent Tesla v3 IL:Trojan.MSILZilla.1773 Verdict Reason: - Sample Type Windows Exe (x86-32) File Name mn.exe ID #839089 MD5 4fbbb9db49ac6bfeddeaf2ac8a43ae38 SHA1 4780eb9b403787e75759363f8e5ba65b72b588e1 SHA256 2d61556b631b4920af773904a0ae5011f0103be9effb7c7292e4ebe3e39f1ad5 File Size 304.69 KB Report Created 2021-08-09 22:57 (UTC+2) Target Environment win10_64_th2_en_mso2016 | exe X-Ray Vision for Malware - www.vmray.com 1 / 19 DYNAMIC ANALYSIS REPORT #2113970 OVERVIEW VMRay Threat Identifiers (26 rules, 76 matches) Score Category Operation Count Classification 5/5 YARA Malicious content matched by YARA rules 2 Spyware • Rule "AgentTesla_StringDecryption_v3" from ruleset "Malware" has matched on a memory dump for (process #1) mn.exe. • Rule "AgentTesla_StringDecryption_v3" from ruleset "Malware" has matched on a memory dump for (process #2) msbuild.exe. 5/5 Data Collection Tries to read cached credentials of various applications 1 Spyware • Tries to read sensitive data of: Flock, Pocomail, WinSCP, FileZilla, OpenVPN, CoreFTP, Opera Mail, Postbox, Ipswitch WS_FTP, The B... ...on, Comodo IceDragon, Opera, Internet Explorer, TigerVNC, SeaMonkey, FTP Navigator, Internet Explorer / Edge, Mozilla Thunderbird. 4/5 System Modification Modifies network configuration 1 - • (Process #2) msbuild.exe modifies the host.conf file, probably to redirect network traffic. 4/5 Reputation Known malicious file 1 - • The sample itself is a known malicious file. 4/5 Antivirus Malicious content was detected by heuristic scan 1 - • Built-in AV detected a memory dump of (process #1) mn.exe as "IL:Trojan.MSILZilla.1773". 4/5 Injection Writes into the memory of another process 1 Injector • (Process #1) mn.exe modifies memory of (process #2) msbuild.exe.