MALICIOUS Threat Names: Agent Tesla V3 IL:Trojan.Msilzilla.1773
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Cache Files Detect and Eliminate Privacy Threats
Award-Winning Privacy Software for OS X Every time you surf the web or use your computer, bits of Recover Disk Space data containing sensitive information are left behind that Over time, the files generated by web browsers can start could compromise your privacy. PrivacyScan provides to take up a large amount of space on your hard drive, protection by scanning for these threats and offers negatively impacting your computer’s performance. multiple removal options to securely erase them from PrivacyScan can locate and removes these space hogs, your system. freeing up valuable disk space and giving your system a speed boost in the process. PrivacyScan can seek and destroy internet files used for tracking your online whereabouts, including browsing history, cache files, cookies, search history, and more. Secure File Shredding Additionally, PrivacyScan can eliminate Flash Cookies, PrivacyScan utilizes advanced secure delete algorithms which are normally hidden away on your system. that meet and exceed US Department of Defense recommendations to ensure complete removal of Privacy Threat: Cookies sensitive data. Cookies can be used to track your usage of websites, determining which pages you visited and the length Intuitive Interface of time you spent on each page. Advertisers can use PrivacyScan’s award-winning design makes it easy to cookies to track you across multiple sites, building up track down privacy threats that exist on your system and a “profile” of who you are based on your web browsing quickly eliminate them. An integrated setup assistant and habits. tip system provide help every step of the way to make file cleaning a breeze. -

Download Fact Sheet
Intella Process l Search l Filter l Produce. Simple. Fact Sheet Intella®: Smarter eDiscovery and Forensic Investigations Innovative, powerful, and simple – exactly the tools you need to conquer today’s data challenges and deliver world class results. Process. Search. Filter. Produce. Simple. Exponential Market Leading Industry’s Best Productivity Power Value & Pricing Key Features Customer Use Examples • Highly user-friendly interface and market-leading Intella has helped some of the world’s best known indexing speeds organizations to dramatically reduce the time, expense and • Insight Analysis feature lists the most notable user, personnel needed for their case loads. system and Internet artifacts, simplifying finding • A Fortune 500 retailer was able to bring e-discovery important data and improving examination time and functions in-house and save millions odue to Intella’s thoroughness of any investigation easy-to-use functionality. • Batch documents and assign to reviewers for subjective • The compliance department of a global financial coding for legal review institution conducts internal reviews of employee emails • Built-in instant messaging so co-workers can discuss and and files with surprising ease because of Intella’s low share documents within the tool during investigations resource/highly efficient architecture. • Automatic extraction of notable registry artifacts. This • A major international accounting and consulting firm can save the examiner many hours of manual artifact increased customer satisfaction by providing their -

Free Email Software Download Best Free Email Client 2021
free email software download Best Free Email Client 2021. This article is all about best free email clients and how they can help you be more productive. We also talk about Clean Email, an easy-to-use email cleaner compatible with virtually all major email services. But before we go over the best email clients for 2021, we believe that we should first explain what advantages email clients have over web-based interfaces of various email services. Clean Email. Take control of your mailbox. What Is an Email Client and Why Should I Use One? If you’re like most people, you probably check your email at least once every day. And if you’re someone whose work involves communication with customers, clients, and coworkers, the chances are that you deal with emails all the time. Even though we spend so much time writing, forwarding, and managing emails, we hardly ever pause for a moment and think about how we could improve our emailing experience. We use clunky web interfaces that are not meant for professional use, we accept outdated applications as if alternatives didn’t exist, and we settle for the default email apps on our mobile devices even though app stores are full of excellent third-party email apps. Broadly speaking, an email client is a computer program used to access and manage a user’s email. But when we use the term email client in this article, we only mean those email clients that can be installed on a desktop computer or a mobile device—not web-based email clients that are hosted remotely and are accessible only from a web browser. -

Manual Aberto De TIC E Libreoffice Capa: Miguel Vale 3ª Edição Editor: ISCTE – Instituto Universitário De Lisboa, Lisboa 2014 ISBN: 978-989-732-237-2 Suporte: E-Book
Manual de Tecnologias de Informação e Comunicação e LibreOffice [ 3ª edição ] Comunidade LibreOffice Portugal Direitos de autor Este trabalho foi licenciado com uma Licença Creative Commons - Atribuição 3.0 Não Adaptada ou superior em conjunto com GNU General Public License v3+ ou superior. Todas as restantes marcas registadas presentes neste manual pertencem às respectivas entidades. Ficha Técnica Título: Manual Aberto de TIC e LibreOffice Capa: Miguel Vale 3ª Edição Editor: ISCTE – Instituto Universitário de Lisboa, Lisboa 2014 ISBN: 978-989-732-237-2 Suporte: e-book Autor(es) Os autores de cada capítulo estão descritos em cada uma das respectivas fichas técnicas. Feedback Envie os seus comentários ou sugestões sobre este documento para: http://wiki.documentfoundation.org/PT/Main_Page http://wiki.documentfoundation.org/PT/Documentation Acordo Ortográfico Cada capítulo deste documento foi redigido no acordo ortográfico definido pelo(s) seu(s) autor(es) na respectiva ficha técnica. Este capítulo foi redigido ao abrigo do Acordo Ortográfico de 1990. A toda a Comunidade LibreOffice Portugal. A todos os movimentos de Software Livre e Creative Commons em Portugal. A todos os Professores, Formadores e alunos e formandos que fizerem uso deste manual. A todos aqueles que apoiaram e acreditaram neste projecto. Caixa Mágica, Novell Portugal, Associação Ensino Livre, Associação Nacional de Software Livre, Associação de Apoio Social da Portugal Telecom, Ângulo Sólido, OpenLab-ESEV Laboratório de Software Livre da Escola Superior de Educação de Viseu, Instituto Superior de Ciências Educativas, Portal Forma-te e em especial ao ISCTE – Instituto Universitário de Lisboa. Aos nossos pais e família que agora poderão usufruir de mais tempo connosco. -

DVD-Ofimática 2014-02
(continuación 2) CamStudio 2.7.316 - CamStudio Codec 1.5 - CDex 1.70 beta 4 - CDisplayEx 1.9.09 - cdrTools FrontEnd 1.5.1 - Classic Shell 3.6.8 - Clavier+ 10.6.7 - Clementine 1.2.1 - Cobian Backup 8.4.0.202 - Comical 0.8 - ComiX 0.2.1.24 - CoolReader 3.0.56.42 - CubicExplorer 0.95.1 - Daphne 1.55 - Data Crow 3.12.5 - DejaVu Fonts 2.34 - DVD-Ofimática Deluge 1.3.6 - DeSmuME 0.9.10 - Dia 0.97.2.2 - Diashapes 0.2.2 - digiKam 3.4.0 - Disk Imager 1.4 - DiskCryptor 1.0.802.118 - Ditto 3.18.46.0 - DjVuLibre 3.5.25.4 - DocFetcher 1.1.9 - DoISO 2.0.0.6 - DOSBox 0.74 - DosZip Commander 3.21 - Double Commander 0.5.8 2014-02 beta - DrawPile 0.8.0 - DrawPile 0.8.3 actualización - DVD Flick 1.3.0.7 - DVDStyler 2.6.1 - DVDx 4.1.1.0 - Eagle Mode 0.84.0 - EasyTAG 2.1 - Ekiga 4.0.1 2013.08.20 - Electric Sheep 2.7.b35 - eLibrary 2.5.13 - emesene 2.12.9 2012.09.13 - eMule 0.50.a - Eraser 6.0.10 - DVD-Ofimática es una recopilación de programas libres para Windows eSpeak 1.47.11 - Eudora OSE 1.0 - eViacam 1.7.0 - Evince 2.32.0.145 - Exodus 0.10.0.0 - dirigidos a la ofimática en general (ofimática, sonido, gráficos y vídeo, Explore2fs 1.08 beta9 - Ext2Fsd 0.51 - FBReader 0.12.10 - FileBot 3.8 - FileVerifier++ 0.6.3 - Internet y utilidades). -

Maelstrom Web Browser Free Download
maelstrom web browser free download 11 Interesting Web Browsers (That Aren’t Chrome) Whether it’s to peruse GitHub, send the odd tweetstorm or catch-up on the latest Netflix hit — Chrome’s the one . But when was the last time you actually considered any alternative? It’s close to three decades since the first browser arrived; chances are it’s been several years since you even looked beyond Chrome. There’s never been more choice and variety in what you use to build sites and surf the web (the 90s are back, right?) . So, here’s a run-down of 11 browsers that may be worth a look, for a variety of reasons . Brave: Stopping the trackers. Brave is an open-source browser, co-founded by Brendan Eich of Mozilla and JavaScript fame. It’s hoping it can ‘save the web’ . Available for a variety of desktop and mobile operating systems, Brave touts itself as a ‘faster and safer’ web browser. It achieves this, somewhat controversially, by automatically blocking ads and trackers. “Brave is the only approach to the Web that puts users first in ownership and control of their browsing data by blocking trackers by default, with no exceptions.” — Brendan Eich. Brave’s goal is to provide an alternative to the current system publishers employ of providing free content to users supported by advertising revenue. Developers are encouraged to contribute to the project on GitHub, and publishers are invited to become a partner in order to work towards an alternative way to earn from their content. Ghost: Multi-session browsing. -

Spybot - Search & Destroy Can Detect and Remove Spyware of Different Kinds from Your Computer
Description Spybot - Search & Destroy can detect and remove spyware of different kinds from your computer. Spyware is a relatively new kind of threat that common anti-virus applications do not cover yet. If you see new toolbars in your Internet Explorer that you didn't intentionally install, if your browser crashes, or if you browser start page has changed without your knowing, you most probably have spyware. But even if you don't see anything, you may be infected, because more and more spyware is emerging that is silently tracking your surfing behaviour to create a marketing profile of you that will be sold to advertisement companies. Spybot-S&D; is free, so there's no harm in trying to see if something snooped into your computer, too :) Spybot-S&D; can also clean usage tracks, an interesting function if you share your computer with other users and don't want them to see what you worked on. And for professional users, it allows to fix some registry inconsistencies and offers some extended reporting features. License Spybot-S&D; comes under the Dedication Public License. Requirements Microsoft Windows 95, 98, ME, NT, 2000 or XP (32 and 64 bit), 2003, Vista. Compatible with bootable PE disks (e.g. BartPE) and Wine. Minimum of 10 MB free hard disk space, more recommended for updates and backups. Usage We recommend that you continue by reading the tutorial next. © 2000-2008 Safer Networking Ltd. All rights reserved. I. Freeware First of all, the reasons why Spybot-S&D; is free: I.a. Dedication Spybot-S&D; is dedicated to the most wonderful girl on earth :) I.b. -

What the Floc?
Security Now! Transcript of Episode #811 Page 1 of 30 Transcript of Episode #811 What the FLoC? Description: This week we briefly, I promise, catch up with ProxyLogon news regarding Windows Defender and the Black Kingdom. We look at Firefox's next release which will be changing its Referer header policy for the better. We look at this week's most recent RCE disaster, a critical vulnerability in the open source MyBB forum software, and China's new CAID (China Anonymization ID). We then conclude by taking a good look at Google's plan to replace tracking with explicit recent browsing history profiling, which is probably the best way to understand FLoC (Federated Learning of Cohorts). And as a special bonus we almost certainly figure out why they named it something so awful. High quality (64 kbps) mp3 audio file URL: http://media.GRC.com/sn/SN-811.mp3 Quarter size (16 kbps) mp3 audio file URL: http://media.GRC.com/sn/sn-811-lq.mp3 SHOW TEASE: It's time for Security Now!. Steve Gibson is here. We've got a new fix for the Microsoft Exchange Server flaw. This one's automatic, thanks to Microsoft. We'll also take a look at some nice new features in Firefox 87. You can get it right now. And then, what the FLoC? We'll take a look at Google's proposal for replacing third-party cookies. Is it better? It's all coming up next on Security Now!. Leo Laporte: This is Security Now! with Steve Gibson, Episode 811, recorded Tuesday, March 23rd, 2021: What the FLoC? It's time for Security Now!, the show where we cover your privacy, your security, your safety online with this guy right here, Steve Gibson from GRC.com. -

I. an Investigation of the Organic Compounds in the Media and Mycelium of Naucoria Confragosa
Scholars' Mine Masters Theses Student Theses and Dissertations 1965 I. An investigation of the organic compounds in the media and mycelium of Naucoria confragosa. II. Study of the extra-cellular pigments of an unknown fungus Yueh-Tsun Chen Follow this and additional works at: https://scholarsmine.mst.edu/masters_theses Part of the Chemistry Commons Department: Recommended Citation Chen, Yueh-Tsun, "I. An investigation of the organic compounds in the media and mycelium of Naucoria confragosa. II. Study of the extra-cellular pigments of an unknown fungus" (1965). Masters Theses. 5238. https://scholarsmine.mst.edu/masters_theses/5238 This thesis is brought to you by Scholars' Mine, a service of the Missouri S&T Library and Learning Resources. This work is protected by U. S. Copyright Law. Unauthorized use including reproduction for redistribution requires the permission of the copyright holder. For more information, please contact [email protected]. 7 ( . I. A!J Il!VESTIGATIOU OF THE OaGAHIC CO:·~OUHDS Irr THZ ECDIA JJ!D ::YCELIUH OF IrAUCORIA . CON'FRAG00A II. STUDY OF THE EXTRA-CELLULAR PIG!!ENTS OF A...'l UI-Jt:NQ;;N ::!'tU!GUS BY YUEH TSUU CHEN1ttt31 A THESIS submitted to the faculty of the illv"IVERSITY OF HISSOUill: AT ROLLA in partial fulfillment of the requirement for the ' ·; Degree of !'..ASTER OF SCIENCE IN · CHE1-1ISTRY ROLLA, IliSSOURI 1965 T!1e funeal r:etabol1:~es excreted. into the cuture fluid by ba::;i- diom.ycetes zro,rl.ng on synthetic zlucose media as \'lOll as fol'·med in the ~.. cella of t::e orgaJl.is.~G uere investi~ated in this thesis. -

Analysis Report Blackenergy
Analysis Report iTrust-Analysis-001 May 2016 BlackEnergy - Malware for Cyber-Physical Attacks About iTrust iTrust is a multidisciplinary research centre located in the Singapore University of Technology and Design (SUTD), established collaboratively by SUTD and the Ministry of Defence, Singapore (MINDEF). The focus of iTrust is on cyber security, spanning across three research areas: a. Cyber Physical System (CPS); b. Enterprise Networking / Security; and c. Internet of Things (IoT). iTrust researchers focus on the development of advanced tools and methodologies to ensure security and safety of current and future cyber physical systems and Internet of Things (IoT) systems. Systems of interest include large infrastructure of national importance such as power grid, water treatment, and oil refineries as well as cyber-devices such as smart watches, pacemakers, defibrillators, insulin pumps, and VNS implants. Cyber physical systems is one of the many areas we are working on. The focus of the proposed research is to improve our understanding of cyber threats to CPSs and to develop and experiment with strategies to mitigate such threats. Our approach is based on well understood technical foundations borrowed from the interdisciplinary fields of control theory, artificial intelligence, game theory, networking, and software engineering. The techniques propose will be evaluated against, and demonstrated in our Secure Water Treatment (SWaT) Testbed, Water Distribution System (WADI) testbed, and Electric Power and Intelligent Control (EPIC) testbed. Similarly, shielded room laboratory for IoT research. iTrust researchers are drawn from across SUTD and with a strong collaboration with Massachusetts Institute of Technology (MIT), enrich the depth, breadth, and quality of research. -
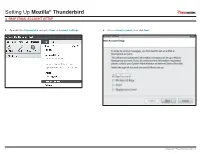
Setting up Mozilla® Thunderbird IMAP EMAIL ACCOUNT SETUP
Setting Up Mozilla® Thunderbird IMAP EMAIL ACCOUNT SETUP 1. Open Mozilla Thunderbird and go to Tools -> Account Settings. 2. Choose Email account; then click Next. 1 Copyright © EmailHosting.com LLC Setting Up Mozilla® Thunderbird IMAP EMAIL ACCOUNT SETUP (cont.) 3. In the Identity window type your name as you want it to appear on outgoing emails. 4. In the Server Information window select the radio button labeled IMAP. • Then, type your email address in the field labeled Email Address. • Enter imap.emailhosting.com in the field labeled Incoming Server. • Click Next to continue. • Enter smtp.emailhosting.com in the field labeled Outgoing Server. • Click Next to continue. John Smith imap.emailhosting.com [email protected] smtp.emailhosting.com Note: If you have already used Thunderbird in the past the Outgoing Server will not be listed. 2 Copyright © EmailHosting.com LLC Setting Up Mozilla® Thunderbird IMAP EMAIL ACCOUNT SETUP (cont.) 5. In the User Names window, the fields should already be filled out correctly. 6. Click Next on the Account Name page to accept the default Account Name. • Confirm that both fields match your EmailHosting username. • In the Congratulations window, verify that all information is correct. • Click Next to continue. • Then click Finish. [email protected] [email protected] [email protected] [email protected] 7. You will be prompted for your password. If you’d like to save your password, make sure Use Password Manager to remember this password is checked before clicking on OK to continue. Note: The field Outgoing Server is only visible during the setup of Mozilla Thunderbird’s first email account. -

Giant List of Web Browsers
Giant List of Web Browsers The majority of the world uses a default or big tech browsers but there are many alternatives out there which may be a better choice. Take a look through our list & see if there is something you like the look of. All links open in new windows. Caveat emptor old friend & happy surfing. 1. 32bit https://www.electrasoft.com/32bw.htm 2. 360 Security https://browser.360.cn/se/en.html 3. Avant http://www.avantbrowser.com 4. Avast/SafeZone https://www.avast.com/en-us/secure-browser 5. Basilisk https://www.basilisk-browser.org 6. Bento https://bentobrowser.com 7. Bitty http://www.bitty.com 8. Blisk https://blisk.io 9. Brave https://brave.com 10. BriskBard https://www.briskbard.com 11. Chrome https://www.google.com/chrome 12. Chromium https://www.chromium.org/Home 13. Citrio http://citrio.com 14. Cliqz https://cliqz.com 15. C?c C?c https://coccoc.com 16. Comodo IceDragon https://www.comodo.com/home/browsers-toolbars/icedragon-browser.php 17. Comodo Dragon https://www.comodo.com/home/browsers-toolbars/browser.php 18. Coowon http://coowon.com 19. Crusta https://sourceforge.net/projects/crustabrowser 20. Dillo https://www.dillo.org 21. Dolphin http://dolphin.com 22. Dooble https://textbrowser.github.io/dooble 23. Edge https://www.microsoft.com/en-us/windows/microsoft-edge 24. ELinks http://elinks.or.cz 25. Epic https://www.epicbrowser.com 26. Epiphany https://projects-old.gnome.org/epiphany 27. Falkon https://www.falkon.org 28. Firefox https://www.mozilla.org/en-US/firefox/new 29.