The Blockchain Blockbuster: Yapese Stones to Central Bank Digital Currencies
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Linking Wallets and Deanonymizing Transactions in the Ripple Network
Proceedings on Privacy Enhancing Technologies ; 2016 (4):436–453 Pedro Moreno-Sanchez*, Muhammad Bilal Zafar, and Aniket Kate* Listening to Whispers of Ripple: Linking Wallets and Deanonymizing Transactions in the Ripple Network Abstract: The decentralized I owe you (IOU) transac- 1 Introduction tion network Ripple is gaining prominence as a fast, low- cost and efficient method for performing same and cross- In recent years, we have observed a rather unexpected currency payments. Ripple keeps track of IOU credit its growth of IOU transaction networks such as Ripple [36, users have granted to their business partners or friends, 40]. Its pseudonymous nature, ability to perform multi- and settles transactions between two connected Ripple currency transactions across the globe in a matter of wallets by appropriately changing credit values on the seconds, and potential to monetize everything [15] re- connecting paths. Similar to cryptocurrencies such as gardless of jurisdiction have been pivotal to their suc- Bitcoin, while the ownership of the wallets is implicitly cess so far. In a transaction network [54, 55, 59] such as pseudonymous in Ripple, IOU credit links and transac- Ripple [10], users express trust in each other in terms tion flows between wallets are publicly available in an on- of I Owe You (IOU) credit they are willing to extend line ledger. In this paper, we present the first thorough each other. This online approach allows transactions in study that analyzes this globally visible log and charac- fiat money, cryptocurrencies (e.g., bitcoin1) and user- terizes the privacy issues with the current Ripple net- defined currencies, and improves on some of the cur- work. -

Beauty Is Not in the Eye of the Beholder
Insight Consumer and Wealth Management Digital Assets: Beauty Is Not in the Eye of the Beholder Parsing the Beauty from the Beast. Investment Strategy Group | June 2021 Sharmin Mossavar-Rahmani Chief Investment Officer Investment Strategy Group Goldman Sachs The co-authors give special thanks to: Farshid Asl Managing Director Matheus Dibo Shahz Khatri Vice President Vice President Brett Nelson Managing Director Michael Murdoch Vice President Jakub Duda Shep Moore-Berg Harm Zebregs Vice President Vice President Vice President Shivani Gupta Analyst Oussama Fatri Yousra Zerouali Vice President Analyst ISG material represents the views of ISG in Consumer and Wealth Management (“CWM”) of GS. It is not financial research or a product of GS Global Investment Research (“GIR”) and may vary significantly from those expressed by individual portfolio management teams within CWM, or other groups at Goldman Sachs. 2021 INSIGHT Dear Clients, There has been enormous change in the world of cryptocurrencies and blockchain technology since we first wrote about it in 2017. The number of cryptocurrencies has increased from about 2,000, with a market capitalization of over $200 billion in late 2017, to over 8,000, with a market capitalization of about $1.6 trillion. For context, the market capitalization of global equities is about $110 trillion, that of the S&P 500 stocks is $35 trillion and that of US Treasuries is $22 trillion. Reported trading volume in cryptocurrencies, as represented by the two largest cryptocurrencies by market capitalization, has increased sixfold, from an estimated $6.8 billion per day in late 2017 to $48.6 billion per day in May 2021.1 This data is based on what is called “clean data” from Coin Metrics; the total reported trading volume is significantly higher, but much of it is artificially inflated.2,3 For context, trading volume on US equity exchanges doubled over the same period. -

On the Relationship of Cryptocurrency Price with US Stock and Gold Price Using Copula Models
mathematics Article On the Relationship of Cryptocurrency Price with US Stock and Gold Price Using Copula Models Jong-Min Kim 1 , Seong-Tae Kim 2 and Sangjin Kim 3,* 1 Statistics Discipline, University of Minnesota at Morris, Morris, MN 56267, USA; [email protected] 2 Department of Mathematics, North Carolina A&T State University, Greensboro, NC 27411, USA; [email protected] 3 Department of Management and Information Systems, Dong-A University, Busan 49236, Korea * Correspondence: [email protected] Received: 15 September 2020; Accepted: 20 October 2020; Published: 23 October 2020 Abstract: This paper examines the relationship of the leading financial assets, Bitcoin, Gold, and S&P 500 with GARCH-Dynamic Conditional Correlation (DCC), Nonlinear Asymmetric GARCH DCC (NA-DCC), Gaussian copula-based GARCH-DCC (GC-DCC), and Gaussian copula-based Nonlinear Asymmetric-DCC (GCNA-DCC). Under the high volatility financial situation such as the COVID-19 pandemic occurrence, there exist a computation difficulty to use the traditional DCC method to the selected cryptocurrencies. To solve this limitation, GC-DCC and GCNA-DCC are applied to investigate the time-varying relationship among Bitcoin, Gold, and S&P 500. In terms of log-likelihood, we show that GC-DCC and GCNA-DCC are better models than DCC and NA-DCC to show relationship of Bitcoin with Gold and S&P 500. We also consider the relationships among time-varying conditional correlation with Bitcoin volatility, and S&P 500 volatility by a Gaussian Copula Marginal Regression (GCMR) model. The empirical findings show that S&P 500 and Gold price are statistically significant to Bitcoin in terms of log-return and volatility. -

Evmpatch: Timely and Automated Patching of Ethereum Smart Contracts
EVMPatch: Timely and Automated Patching of Ethereum Smart Contracts Michael Rodler Wenting Li Ghassan O. Karame University of Duisburg-Essen NEC Laboratories Europe NEC Laboratories Europe Lucas Davi University of Duisburg-Essen Abstract some of these contracts hold, smart contracts have become an appealing target for attacks. Programming errors in smart Recent attacks exploiting errors in smart contract code had contract code can have devastating consequences as an attacker devastating consequences thereby questioning the benefits of can exploit these bugs to steal cryptocurrency or tokens. this technology. It is currently highly challenging to fix er- rors and deploy a patched contract in time. Instant patching is Recently, the blockchain community has witnessed several especially important since smart contracts are always online incidents due smart contract errors [7, 39]. One especially due to the distributed nature of blockchain systems. They also infamous incident is the “TheDAO” reentrancy attack, which manage considerable amounts of assets, which are at risk and resulted in a loss of over 50 million US Dollars worth of often beyond recovery after an attack. Existing solutions to Ether [31]. This led to a highly debated hard-fork of the upgrade smart contracts depend on manual and error-prone pro- Ethereum blockchain. Several proposals demonstrated how to defend against reentrancy vulnerabilities either by means of cesses. This paper presents a framework, called EVMPATCH, to instantly and automatically patch faulty smart contracts. offline analysis at development time or by performing run-time validation [16, 23, 32, 42]. Another infamous incident is the EVMPATCH features a bytecode rewriting engine for the pop- ular Ethereum blockchain, and transparently/automatically parity wallet attack [39]. -

ARK Whitepaper
ARK Whitepaper A Platform for Consumer Adoption v.1.0.3 The ARK Crew ARK Whitepaper v.1.0.3 Table Of Contents Overview………………………………………………………………...……………………………….……………….………………………………………………………….….3 Purpose of this Whitepaper………………………………………………………………………………………………………………………..….……….3 Why?…………………………………………………………………………………………………………………….…………………………………………………….…………..4 ARK…………………………………………………………………………………………………….……………….…………………………………………………………………..5 ARK IS………………………………………………………………………………………………....……………….………………………………………………………………..5 ARK: Technical Details……………………………………….…….…..…………………………...……………….………………...…………………………...6 - Delegated Proof of Stake…………………………….……………...………………………….……………………………………….………...…...6 - Hierarchical Deterministic (HD) Wallets (BIP32)…………………………………………………….....…………………..…..8 - Fees……………………………………………………………………………………………………………….……………….…...………………………………..……...8 - ARK Delegates and Delegate Voting.…………………………………………………………………………………...………………….9 - Bridged Blockchains (SmartBridges)....................………………………………………………………………….………...…….10 - POST ARK-TEC Token Distribution …………………..…………………………………….………………….………..……..…..……….11 - Testnet Release……………………………………………….…………………………………………………………………….………...….....12 And Beyond?…………………………………………………………………….………...……………………………………….………………………...……….…12 Addendum 1: ARK IS…(Cont.)...……..……..…………....…..………...………………………………………...………………………......……12 -

Metamask Pre-Assignment
MMS 562F: Tech Driven Transformation MetaMask Pre-Assignment Campbell R. Harvey Duke University and NBER February 2021 Setup • Metamask is a cryptocurrency wallet that is used to interface with the Ethereum-based Apps • We will be setting up this Wallet on your mobile device (iOS or Android only) – If you are unable to use a mobile device, the end of this deck has a web browser tutorial (Page 19) – If you already have MetaMask on your browser, the end of this deck has a tutorial to link your Web Account to the Mobile App (Page 25) Campbell R. Harvey 2021 2 Setup • Download the Metamask app from the App Store or Google Play Store • Click Get Started • Click Create a new wallet • Create a new account by typing in a password of your choosing and pressing “Create” • Go through the prompts to secure your wallet • Store Secret Backup Phrase in a secure location, ideally paper or a password manager – not on your phone or computer. • Type in secret backup phrase Campbell R. Harvey 2021 3 1 Using MetaMask 1. Network • This determines which Ethereum Network you are using. Click on this to see all network options in a 2 dropdown. For this class we will only discuss or use the Main Ethereum Network and the Ropsten Test Network. 3 Campbell R. Harvey 2021 4 1 Using MetaMask 1. Network • The Ethereum Mainnet is where live ether (ETH) with real value exists and is 2 used for payment and applications. I will refer to this as the “main network” or the “mainnet” 3 Campbell R. -

Central Banks and Alternative Monetary Alternative Monetary
Central Banks and Alternative Monetary Systems Christopher J. Neely AittViPAssistant Vice Presid idtent, Federal Reserve Bank of St. Louis Annual Educators Conference October 19, 2011 The opinions expressed are my own and not necessarily those of the Federal Reserve Bank of Saint Louis or the Federal Reserve System. 2 Today’sTopics s Topics Central Banks and Alternative Money Systems o What is Money? o Methods of Monetary Policy o ClBkCentral Banks o Central Banks vs. Commodity Standard 3 What is Money? Money • Money: That which can be exchanged for goods and services. – Functions: • Medium of exchange • Store of value • Unit of measure Why Do We Need Money? • Money solves the mutual coincidence of wants problem. • Greatly reduces transactions costs/shopping time. – My grocer does not want a lecture on economics in exchange for Cheerios. Historical Forms of Money • Commodities: cigarettes, furs, gold, Rai stones (Yap island) • Fiat money: Money whose vvuesoalue is not intrins sc.ic. – Introduced during wartime in the United States • Charac ter is tics of usef ul money – Durable, transportable, divisible, homogenous, easily produced (?) Historical Forms of Money Rai stone Historical Forms of Money • What are the advantages and disadvantages of having a currency that is easily produced? Money Supply • Monetary base: Currency and reserves with the central bank. • Narrow to broad definitions of money – Currency – Demand deposits – Time deposits, CDs, – Shor t-tbdterm bonds • Money and bonds are close to a continuum now – M0, M1, MZM, M2 Money Supply Monetary Base 3000 2500 ars ll 2000 1500 ns of US Dol 1000 Billio 500 Monetary Base (BASE) 0 2/1/1984 2/1/1989 2/1/1994 2/1/1999 2/1/2004 2/1/2009 Money Supply Money supply levels go up and up. -

Vulnerability of Blockchain Technologies to Quantum Attacks
Vulnerability of Blockchain Technologies to Quantum Attacks Joseph J. Kearneya, Carlos A. Perez-Delgado a,∗ aSchool of Computing, University of Kent, Canterbury, Kent CT2 7NF United Kingdom Abstract Quantum computation represents a threat to many cryptographic protocols in operation today. It has been estimated that by 2035, there will exist a quantum computer capable of breaking the vital cryptographic scheme RSA2048. Blockchain technologies rely on cryptographic protocols for many of their essential sub- routines. Some of these protocols, but not all, are open to quantum attacks. Here we analyze the major blockchain-based cryptocurrencies deployed today—including Bitcoin, Ethereum, Litecoin and ZCash, and determine their risk exposure to quantum attacks. We finish with a comparative analysis of the studied cryptocurrencies and their underlying blockchain technologies and their relative levels of vulnerability to quantum attacks. Introduction exist to allow the legitimate owner to recover this account. Blockchain systems are unlike other cryptosys- tems in that they are not just meant to protect an By contrast, in a blockchain system, there is no information asset. A blockchain is a ledger, and as central authority to manage users’ access keys. The such it is the asset. owner of a resource is by definition the one hold- A blockchain is secured through the use of cryp- ing the private encryption keys. There are no of- tographic techniques. Notably, asymmetric encryp- fline backups. The blockchain, an always online tion schemes such as RSA or Elliptic Curve (EC) cryptographic system, is considered the resource— cryptography are used to generate private/public or at least the authoritative description of it. -
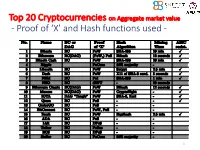
Proof of 'X' and Hash Functions Used
Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 1 ISI Kolkata BlockChain Workshop, Nov 30th, 2017 CRYPTOGRAPHY with BlockChain - Hash Functions, Signatures and Anonymization - Hiroaki ANADA*1, Kouichi SAKURAI*2 *1: University of Nagasaki, *2: Kyushu University Acknowledgements: This work is supported by: Grants-in-Aid for Scientific Research of Japan Society for the Promotion of Science; Research Project Number: JP15H02711 Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 3 Table of Contents 1. Cryptographic Primitives in Blockchains 2. Hash Functions a. Roles b. Various Hash functions used for Proof of ‘X’ 3. Signatures a. Standard Signatures (ECDSA) b. Ring Signatures c. One-Time Signatures (Winternitz) 4. Anonymization Techniques a. Mixing (CoinJoin) b. Zero-Knowledge proofs (zk-SNARK) 5. Conclusion 4 Brief History of Proof of ‘X’ 1992: “Pricing via Processing or Combatting Junk Mail” Dwork, C. and Naor, M., CRYPTO ’92 Pricing Functions 2003: “Moderately Hard Functions: From Complexity to Spam Fighting” Naor, M., Foundations of Soft. Tech. and Theoretical Comp. Sci. 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 5 Brief History of Proof of ‘X’ 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 2012: “Peercoin” Proof of Stake (& Proof of Work) ~ : Delegated Proof of Stake, Proof of Storage, Proof of Importance, Proof of Reserves, Proof of Consensus, ... 6 Proofs of ‘X’ 1. Proof of Work 2. Proof of Stake Hash-based Proof of ‘X’ 3. Delegated Proof of Stake 4. Proof of Importance 5. -

State of the Art: the Monero Cryptocurrency Mining Malware Detection Using Supervised Machine Learning Algorithms
International Journal of Applied Science and Engineering State of the art: The monero cryptocurrency mining malware detection using supervised machine learning algorithms Wilfridus Bambang Triadi Handaya1*, Mohd Najwadi Yusoff 2, Aman Jantan2 1 Department of Informatics, Universitas Atma Jaya Yogyakarta, Daerah Istimewa Yogyakarta, Indonesia 2 School of Computer Sciences, Universiti Sains Malaysia, Penang, Malaysia ABSTRACT Today’s evolving information technology trend is fuelling increasingly various cybercrime. Various cybercrime types, such as malware attacks and data breach activities, organizations, and countries, occur every day. Malware is one of the biggest cyber threats on the Internet today. Every year, the number of data breaches continues to increase. Mining is a complete cryptocurrency network’s computing process to verify transaction records, called blockchains, and receive digital coins in return. This mining process requires severe hardware and significant CPU resources to create cryptocurrencies. A statistic published by Statista in mid-2020 about the most detected crypto-mining malware types influencing corporate networks global from January to June 2020, it can be seen that cryptocurrency mining activity leading to the pool of Monero amounts to 46% derived from the use of XMRig. Malware detection is like an endless war between malware authors and malware prevention vendors. This trend change also makes the procedures and forms of analysis must adapt. From previously done manually with various tools for static analysis, to be OPEN ACCESS subsequently replaced with automatic analysis through the application of machine learning algorithms. Received: October 9, 2020 Revised: December 20, 2020 Keywords: Malware detection, XMRig, Monero, Cryptocurrencies, Mining. Accepted: January 6, 2021 Corresponding Author: Wilfridus Bambang Triadi Handaya 1. -

Using Blockchain Technology to Secure the Internet of Things
Using Blockchain Technology to Secure the Internet of Things Presented by the Blockchain/ Distributed Ledger Working Group © 2018 Cloud Security Alliance – All Rights Reserved. You may download, store, display on your computer, view, print, and link to Using Blockchain Technology to Secure the Internet of Things subject to the following: (a) the Document may be used solely for your personal, informational, non- commercial use; (b) the Report may not be modified or altered in any way; (c) the Document may not be redistributed; and (d) the trademark, copyright or other notices may not be removed. You may quote portions of the Document as permitted by the Fair Use provisions of the United States Copyright Act, provided that you attribute the portions to the Using Blockchain Technology to Secure the Internet of Things paper. Blockchain/Distributed Ledger Technology Working Group | Using Blockchain Technology to Secure the Internet of Things 2 © Copyright 2018, Cloud Security Alliance. All rights reserved. ABOUT CSA The Cloud Security Alliance is a not-for-profit organization with a mission to promote the use of best practices for providing security assurance within Cloud Computing, and to provide education on the uses of Cloud Computing to help secure all other forms of computing. The Cloud Security Alliance is led by a broad coalition of industry practitioners, corporations, associations and other key stakeholders. For further information, visit us at www.cloudsecurityalliance.org and follow us on Twitter @cloudsa. Blockchain/Distributed Ledger Technology Working Group | Using Blockchain Technology to Secure the Internet of Things 3 © Copyright 2018, Cloud Security Alliance. All rights reserved. -

CY19 January a Collection of Bitcoin Commentary from the Brightest
CY19 January A collection of Bitcoin commentary from the brightest minds in the crypto community. Crypto Words CY19 January Contents Goals and Scope ......................................................................................................................................................................... 2 Support Crypto Words .......................................................................................................................................................... 3 Cryptocurrency: The Canary in the Coal Mine.................................................................................................. 4 Tweetstorm: Bitcoin’s 10 Year Anniversary ......................................................................................................... 6 Bitcoin: Two Parts Math, One Part Biology .......................................................................................................... 8 Planting Bitcoin - Season (2/4) .................................................................................................................................... 12 Planting Bitcoin - Gardening (4/4) ............................................................................................................................ 18 Planting Bitcoin — Soil (3/4) .......................................................................................................................................... 25 Planting Bitcoin — Species (1/4) ...............................................................................................................................