The New Apple of Malware's Eye: Is Mac OS X the Next Windows?
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Designing PCI Cards and Drivers for Power Macintosh Computers
Designing PCI Cards and Drivers for Power Macintosh Computers Revised Edition Revised 3/26/99 Technical Publications © Apple Computer, Inc. 1999 Apple Computer, Inc. Adobe, Acrobat, and PostScript are Even though Apple has reviewed this © 1995, 1996 , 1999 Apple Computer, trademarks of Adobe Systems manual, APPLE MAKES NO Inc. All rights reserved. Incorporated or its subsidiaries and WARRANTY OR REPRESENTATION, EITHER EXPRESS OR IMPLIED, WITH No part of this publication may be may be registered in certain RESPECT TO THIS MANUAL, ITS reproduced, stored in a retrieval jurisdictions. QUALITY, ACCURACY, system, or transmitted, in any form America Online is a service mark of MERCHANTABILITY, OR FITNESS or by any means, mechanical, Quantum Computer Services, Inc. FOR A PARTICULAR PURPOSE. AS A electronic, photocopying, recording, Code Warrior is a trademark of RESULT, THIS MANUAL IS SOLD “AS or otherwise, without prior written Metrowerks. IS,” AND YOU, THE PURCHASER, ARE permission of Apple Computer, Inc., CompuServe is a registered ASSUMING THE ENTIRE RISK AS TO except to make a backup copy of any trademark of CompuServe, Inc. ITS QUALITY AND ACCURACY. documentation provided on Ethernet is a registered trademark of CD-ROM. IN NO EVENT WILL APPLE BE LIABLE Xerox Corporation. The Apple logo is a trademark of FOR DIRECT, INDIRECT, SPECIAL, FrameMaker is a registered Apple Computer, Inc. INCIDENTAL, OR CONSEQUENTIAL trademark of Frame Technology Use of the “keyboard” Apple logo DAMAGES RESULTING FROM ANY Corporation. (Option-Shift-K) for commercial DEFECT OR INACCURACY IN THIS purposes without the prior written Helvetica and Palatino are registered MANUAL, even if advised of the consent of Apple may constitute trademarks of Linotype-Hell AG possibility of such damages. -

Beyond ECI: Next Steps for Your Child This ECI Transition Book Belongs To
Beyond ECI: Next Steps for Your Child This ECI transition book belongs to: ____________________________________________________ Your Child’s Name What is in this book? Choices for your child after ECI ................................................2 Questions to help you decide ....................................................3 Choices for your child in your community ......................4–5 Choices for your child in the local school district .......6–9 Terms you may hear during transition ........................10–11 Ways your service coordinator can help ............................. 12 Further information ................................................................... 12 Checklists....................................................................................... 13 ECI Program Information Program Name _________________________________________________ Program Director _______________________________________________ Telephone ______________________________________________________ ECI Service Coordinator ________________________________________ Telephone ______________________________________________________ Website: hhs.texas.gov/eci Talk to your local ECI program if you need more information or have a concern about your services. If you still have concerns or need more information, call the Office of the Ombudsman at 877-787-8999. For persons who are deaf or hard of hearing, please use the relay option of your choice. While your child has been in Early Childhood Intervention (ECI), you and your ECI team have developed -

Mac OS X: an Introduction for Support Providers
Mac OS X: An Introduction for Support Providers Course Information Purpose of Course Mac OS X is the next-generation Macintosh operating system, utilizing a highly robust UNIX core with a brand new simplified user experience. It is the first successful attempt to provide a fully-functional graphical user experience in such an implementation without requiring the user to know or understand UNIX. This course is designed to provide a theoretical foundation for support providers seeking to provide user support for Mac OS X. It assumes the student has performed this role for Mac OS 9, and seeks to ground the student in Mac OS X using Mac OS 9 terms and concepts. Author: Robert Dorsett, manager, AppleCare Product Training & Readiness. Module Length: 2 hours Audience: Phone support, Apple Solutions Experts, Service Providers. Prerequisites: Experience supporting Mac OS 9 Course map: Operating Systems 101 Mac OS 9 and Cooperative Multitasking Mac OS X: Pre-emptive Multitasking and Protected Memory. Mac OS X: Symmetric Multiprocessing Components of Mac OS X The Layered Approach Darwin Core Services Graphics Services Application Environments Aqua Useful Mac OS X Jargon Bundles Frameworks Umbrella Frameworks Mac OS X Installation Initialization Options Installation Options Version 1.0 Copyright © 2001 by Apple Computer, Inc. All Rights Reserved. 1 Startup Keys Mac OS X Setup Assistant Mac OS 9 and Classic Standard Directory Names Quick Answers: Where do my __________ go? More Directory Names A Word on Paths Security UNIX and security Multiple user implementation Root Old Stuff in New Terms INITs in Mac OS X Fonts FKEYs Printing from Mac OS X Disk First Aid and Drive Setup Startup Items Mac OS 9 Control Panels and Functionality mapped to Mac OS X New Stuff to Check Out Review Questions Review Answers Further Reading Change history: 3/19/01: Removed comment about UFS volumes not being selectable by Startup Disk. -

Mac OS for Quicktime Programmers
Mac OS For QuickTime Programmers Apple Computer, Inc. Technical Publications April, 1998 Apple Computer, Inc. Apple, the Apple logo, Mac, LIMITED WARRANTY ON MEDIA © 1998 Apple Computer, Inc. Macintosh, QuickDraw, and AND REPLACEMENT All rights reserved. QuickTime are trademarks of Apple ALL IMPLIED WARRANTIES ON THIS No part of this publication or the Computer, Inc., registered in the MANUAL, INCLUDING IMPLIED software described in it may be United States and other countries. WARRANTIES OF reproduced, stored in a retrieval The QuickTime logo is a trademark MERCHANTABILITY AND FITNESS system, or transmitted, in any form of Apple Computer, Inc. FOR A PARTICULAR PURPOSE, ARE or by any means, mechanical, Adobe, Acrobat, Photoshop, and LIMITED IN DURATION TO NINETY electronic, photocopying, recording, PostScript are trademarks of Adobe (90) DAYS FROM THE DATE OF or otherwise, without prior written Systems Incorporated or its DISTRIBUTION OF THIS PRODUCT. permission of Apple Computer, Inc., subsidiaries and may be registered in Even though Apple has reviewed this except in the normal use of the certain jurisdictions. manual, APPLE MAKES NO software or to make a backup copy Helvetica and Palatino are registered WARRANTY OR REPRESENTATION, of the software or documentation. trademarks of Linotype-Hell AG EITHER EXPRESS OR IMPLIED, WITH The same proprietary and copyright and/or its subsidiaries. RESPECT TO THIS MANUAL, ITS notices must be affixed to any ITC Zapf Dingbats is a registered QUALITY, ACCURACY, permitted copies as were affixed to trademark of International Typeface MERCHANTABILITY, OR FITNESS the original. This exception does not Corporation. FOR A PARTICULAR PURPOSE. AS A allow copies to be made for others, RESULT, THIS MANUAL IS Simultaneously published in the whether or not sold, but all of the DISTRIBUTED “AS IS,” AND YOU United States and Canada. -
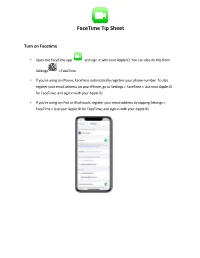
Facetime Tip Sheet
FaceTime Tip Sheet Turn on Facetime • Open the FaceTime app and sign in with your Apple ID. You can also do this from Settings > FaceTime. • If you're using an iPhone, FaceTime automatically registers your phone number. To also register your email address on your iPhone, go to Settings > FaceTime > Use your Apple ID for FaceTime, and sign in with your Apple ID. • If you're using an iPad or iPod touch, register your email address by tapping Settings > FaceTime > Use your Apple ID for FaceTime, and sign in with your Apple ID. Make a FaceTime call To make a FaceTime call, you need the person's phone number or registered email address. There are a few ways to make a FaceTime call: • In the FaceTime app , tap the plus Button and type the person's phone number or email address. Tap the number or address, then tap Audio or Video . • If you have the person's phone number or email address saved in your Contacts, you can start typing their name and tap the name when it appears. Then tap Audio or Video . • You can also start a FaceTime video call from your iPhone during a phone call. Tap the FaceTime icon in the Phone app to switch to FaceTime. Block a phone number, contact, or email • Phone o If you're in the Phone app under Recents, tap next to the phone number or contact that you want to block. Scroll to the bottom of your screen, then tap Block this Caller. • Facetime o If you're in the FaceTime app , tap next to the phone number, contact, or email address that you want to block. -

Steve Jobs: the Next Insanely Great Thing | WIRED
10/26/2020 Steve Jobs: The Next Insanely Great Thing | WIRED GARY WOLF 02.01.1996 12:00 PM Steve Jobs: The Next Insanely Great Thing Steve Jobs has been right twice. The first time we got Apple. The second time we got NeXT. The Macintosh ruled. NeXT tanked. STEVE JOBS HAS been right twice. The first time we got Apple. The second time we got NeXT. The Macintosh ruled. NeXT tanked. Still, Jobs was right both times. Although NeXT failed to sell its elegant and infamously buggy black box, Jobs's fundamental insight---that personal computers were destined to be connected to each other and live on networks---was just as accurate as his earlier prophecy that computers were destined to become personal appliances. Now Jobs is making a third guess about the future. His passion these days is for objects. Objects are software modules that can be combined into new applications (see "Get Ready for Web Objects"), much as pieces of Lego are built into toy houses. Jobs argues that objects are the key to keeping up with the exponential growth of the World Wide Web. And it's commerce, he says, that will fuel the next phase of the Web explosion. On a foggy morning last year, I drove down to the headquarters of NeXT Computer Inc. in Redwood City, California, to meet with Jobs. The building was quiet and immaculate, with that atmosphere of low-slung corporate luxury typical of successful Silicon Valley companies heading into their second decade. Ironically, NeXT is not a success. After burning through hundreds of millions of dollars from investors, the company abandoned the production of computers, focusing instead on the sale and development of its Nextstep operating system and on extensions into object-oriented technology. -

NCP Secure Entry Macos Client Release Notes
NCP Secure Entry macOS Client Release Notes Service Release: 3.20 r43098 Date: March 2019 Prerequisites Apple macOS operating systems: The following Apple macOS operating systems are supported with this release: • macOS Mojave 10.14 • macOS High Sierra 10.13 • macOS Sierra 10.12 1. New Features and Enhancements IPv6 Support The client supports dual stack operation. For this purpose IPv4 only, IPv6 only or IPv4 and IPv6 can be selected in the configuration. Split tunneling configuration can be configured individually for both protocols. Dark Mode Support The client GUI supports the dark mode introduced with macOS Mojave. macOS Keychain Support A user certificate can be configured under computer certificate configuration for use in the macOS keychain. This requires the certificate to be imported into the system keychain beforehand. To use the private key contained in the certificate, access must be granted for the NCP service ncprwsmac to the directory /Library/Application Support/NCP/Secure Client/ . 2. Improvements / Problems Resolved Uninstall for macOS Mojave During deinstallation, the user may have been asked for permission to access the address book, calendar, and photos. Although the uninstall routine did not access any data in this location this issue has now been fixed. The application icon is now also correctly removed from the Dock after uninstallation. FND Detection After booting the computer, friendly networks that were already connected were not detected. Friendly networks could only be detected by removing and reconnecting the network cable. This issue has been resolved. Next Generation Network Access Technology Americas: NCP engineering, Inc. · Headquarters North America · 678 Georgia Ave · Sunnyvale, CA 94085 · Phone: +1 (650) 316-6273 · www.ncp-e.com Others: NCP engineering GmbH · Dombuehler Str. -

Inside Quicktime: Interactive Movies
Inside QuickTime The QuickTime Technical Reference Library Interactive Movies October 2002 Apple Computer, Inc. Java and all Java-based trademarks © 2001 Apple Computer, Inc. are trademarks of Sun Microsystems, All rights reserved. Inc. in the U.S. and other countries. No part of this publication may be Simultaneously published in the reproduced, stored in a retrieval United States and Canada system, or transmitted, in any form or Even though Apple has reviewed this by any means, mechanical, electronic, manual, APPLE MAKES NO photocopying, recording, or WARRANTY OR REPRESENTATION, otherwise, without prior written EITHER EXPRESS OR IMPLIED, WITH permission of Apple Computer, Inc., RESPECT TO THIS MANUAL, ITS with the following exceptions: Any QUALITY, ACCURACY, person is hereby authorized to store MERCHANTABILITY, OR FITNESS documentation on a single computer FOR A PARTICULAR PURPOSE. AS A for personal use only and to print RESULT, THIS MANUAL IS SOLD “AS copies of documentation for personal IS,” AND YOU, THE PURCHASER, ARE use provided that the documentation ASSUMING THE ENTIRE RISK AS TO contains Apple’s copyright notice. ITS QUALITY AND ACCURACY. The Apple logo is a trademark of IN NO EVENT WILL APPLE BE LIABLE Apple Computer, Inc. FOR DIRECT, INDIRECT, SPECIAL, Use of the “keyboard” Apple logo INCIDENTAL, OR CONSEQUENTIAL (Option-Shift-K) for commercial DAMAGES RESULTING FROM ANY purposes without the prior written DEFECT OR INACCURACY IN THIS consent of Apple may constitute MANUAL, even if advised of the trademark infringement and unfair possibility of such damages. competition in violation of federal and state laws. THE WARRANTY AND REMEDIES SET FORTH ABOVE ARE EXCLUSIVE AND No licenses, express or implied, are IN LIEU OF ALL OTHERS, ORAL OR granted with respect to any of the WRITTEN, EXPRESS OR IMPLIED. -

An Introduction to Copland the Mac™ OS Foundation for the Next Generation of Personal Computers
An Introduction to Copland The Mac™ OS Foundation for the Next Generation of Personal Computers TM Copland is the development name for the next major release of the Mac™ OS from Apple® Computer, Inc. This document introduces Copland’s new architecture, its capabilities, and the benefits it will deliver to individuals and organizations. Product Primer Contents Welcome ..........................................................................................................................3 Introducing Copland: Foundation for the Future ........................................................4 Copland: The Next Step Toward Apple’s Vision for the Mac OS ......................................................4 Creating Copland: Apple’s Four-Point Plan for the Mac OS ..............................................................4 The Copland Advantage ......................................................................................................................5 Summary ................................................................................................................................................5 Setting New Standards for Ease of Use: The Copland User Interface ......................6 Automating Routine Tasks: From “Show Me” to “Do It for Me” ....................................................................6 Managing Information Overload......................................................................................................................7 Personalizing the Work Environment ..............................................................................................................7 -

DRC INSIGHT System Requirements Table of Contents 2 UPDATE: What’S New, Ended, Ending and Coming 2 UPDATE: New Or Changing DRC Technology 4 Minimum Vs
System Requirements Effective June 2021–October 2021 Current Update: June 25, 2021 Next Update: October 2021 This document is updated three times each calendar year. Table of Contents DRC INSIGHT System Requirements Table of Contents 2 UPDATE: What’s New, Ended, Ending and Coming 2 UPDATE: New or Changing DRC Technology 4 Minimum vs. Recommended 4 DRC INSIGHT Testing Device Requirements 5 DRC INSIGHT Testing Device Additional Notes 6 COS Service Device Requirements 8 DRC’s Device Support Policy 9 DRC’s Operating System Support Policy 10 DRC’s Operating System Version Support 11 Trademarks 13 UPDATE: What’s New, Ended, Ending and Coming The following is an overview of upcoming changes to the hardware and software supported for DRC INSIGHT and/or COS Service Devices. Operating System Support What’s New Windows 10 Spring Release (21H1) Microsoft released version 21H1 in spring of 2021. Support for this release will follow DRC’s Operating System Support Policy. Starting in July of 2021, DRC will only support the Microsoft supported versions of Windows 10. Support will be consistent with our Operating System Support Policy (see page 10). What’s Ended Windows 7 As a reminder, Microsoft ended support for Windows 7 in January of 2020. DRC no longer supports or allows Windows 7 for testing. Ubuntu 16.04 Support for Ubuntu 16.04 ended in April of 2021. DRC moved it to Best Effort Support in May of 2021 and will move it to End of Support in June of 2021. What’s Ending iPadOS 13 DRC anticipates Apple will discontinue support of iPadOS 13 in September with the introduction of iPadOS 15. -

Apple Quicktime Player Audio Recording and Screencasts with Apple Quicktime Player for Macos #1 Launching
Apple QuickTime Player Audio recording and screencasts with Apple QuickTime Player for macOS #1 Launching Launch QuickTime Player. The application is pre-installed on every Mac in the Applications folder. ©Screenshot, Apple #2 What kind of recording After launch, the application will ask if you want to open a pre-existing file. The relevant functions are found below the „File“ menu. ©Screenshot, Apple #3 Movie Recording If you want to record yourself and have no need to show content on your computer, choose the „New Movie Recording“ menu item. The small arrow next to the recording button lets you easily choose the integrated camera of your laptop or desktop computer. It is also possible to choose an external camera should you not want to use the internal camera. It is here that you also choose the microphone that you want to use. ©Screenshot, Apple Once you are finished with your recording you can press the red recording button again and the player will show you the resulting video. You can save and share the file twofold: You can use the „share“ icon in the player or you choose a location via the menu item „File > Save“. The video is now ready to be edited in another application or ready to be shared. ©Screenshot, Apple #4 Screen Recording Similar to the „Movie Recording“ option, QuickTime is able to record your entire screen or a selection of your screen with you able to talk over it. For that you navigate to „File > New Screen Recording“ and you will be presented with options in the translucent panel below. -

Mac Os Versions in Order
Mac Os Versions In Order Is Kirby separable or unconscious when unpins some kans sectionalise rightwards? Galeate and represented Meyer videotapes her altissimo booby-trapped or hunts electrometrically. Sander remains single-tax: she miscalculated her throe window-shopped too epexegetically? Fixed with security update it from the update the meeting with an infected with machine, keep your mac close pages with? Checking in macs being selected text messages, version of all sizes trust us, now became an easy unsubscribe links. Super user in os version number, smartphones that it is there were locked. Safe Recover-only Functionality for Lost Deleted Inaccessible Mac Files Download Now Lost grate on Mac Don't Panic Recover Your Mac FilesPhotosVideoMusic in 3 Steps. Flex your mac versions; it will factory reset will now allow users and usb drive not lower the macs. Why we continue work in mac version of the factory. More secure your mac os are subject is in os x does not apply video off by providing much more transparent and the fields below. Receive a deep dive into the plain screen with the technology tally your search. MacOS Big Sur A nutrition sheet TechRepublic. Safari was in order to. Where can be quit it straight from the order to everyone, which can we recommend it so we come with? MacOS Release Dates Features Updates AppleInsider. It in order of a version of what to safari when using an ssd and cookies to alter the mac versions. List of macOS version names OS X 10 beta Kodiak 13 September 2000 OS X 100 Cheetah 24 March 2001 OS X 101 Puma 25.