Master's Program in Computer Science & Technology
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

)ممتاز( الف گروه Shanghai استان 1. Fudan University 2. Shanghai Jiao
گروه الف )ممتاز( استان Shanghai 1. Fudan University 2. Shanghai Jiao Tong University استان Jiangsu 1. Nanjing University استان Beijing (صرفاً در رشته هوافضا Beihang University (Aerospace Science and Technology .1 2. Peking University 3. Chinese Academy of Agricultural Sciences صرفاً در رشته ژئوساینس )مجموعه علوم زمین شناسی( China University of Geosciences .4 5. Tsinghua University 6. University of Chinese Academy of Sciences استان Guangdong 1. Sun Yat-sen University استان Hangzhou 1. Zhejiang University Anhuiاستان 1. University of Science and Technology of China گروه ب )خوب( استان Beijing 1. Beihang University (former BUAA) 2. Beijing Foreign Studies University 3. Beijing Institute of Technology 4. Beijing Jiao tong University 5. Beijing Language & Culture University 6. Beijing Normal University صرفاً در رشته های علوم ورزشی و تربیت بدنی Beijing Sport University .7 8. Beijing University of Technology صرفاً در رشته های فنی Beijing University of Chemical Technology .9 10. Beijing University of Chinese Medicine 11. Beijing University of Posts and Telecommunications 12. China Agricultural University صرفاً در رشته های علوم سیاسی و حقوق در گرایش های مختلف China University of political Sciences & Law .13 14. China University of Petroleum - Beijing 15. Minzu University of China 16. Renmin (People’s) University of China 17. University of Science and Technology Beijing 18. University of International Business and Economics (UIBE) استان Fujian 1. Xiamen University استان Guangdong 1. Guangdong University of Foreign Studies 2. Guangzhou University 3. Harbin Institute of Technology Shenzhen Graduate School 4. Jinan University صرفاً تا مقطع کارشناسی Shenzhen University .5 6. South China University of Technology استان Heilongjiang 1. Harbin Institute of Technology 2. -

Multiple Passive Sensor Multi-Target Tracking Based On
2017 International Conference on Network and Information Systems for Computers (ICNISC 2017) Shanghai, China 14 – 16 April 2017 IEEE Catalog Number: CFP17B68-POD ISBN: 978-1-5386-1619-2 Copyright © 2017 by the Institute of Electrical and Electronics Engineers, Inc. All Rights Reserved Copyright and Reprint Permissions: Abstracting is permitted with credit to the source. Libraries are permitted to photocopy beyond the limit of U.S. copyright law for private use of patrons those articles in this volume that carry a code at the bottom of the first page, provided the per-copy fee indicated in the code is paid through Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923. For other copying, reprint or republication permission, write to IEEE Copyrights Manager, IEEE Service Center, 445 Hoes Lane, Piscataway, NJ 08854. All rights reserved. *** This is a print representation of what appears in the IEEE Digital Library. Some format issues inherent in the e-media version may also appear in this print version. IEEE Catalog Number: CFP17B68-POD ISBN (Print-On-Demand): 978-1-5386-1619-2 ISBN (Online): 978-1-5386-1618-5 Additional Copies of This Publication Are Available From: Curran Associates, Inc 57 Morehouse Lane Red Hook, NY 12571 USA Phone: (845) 758-0400 Fax: (845) 758-2633 E-mail: [email protected] Web: www.proceedings.com 2017 International Conference on Network and Information Systems for Computers (ICNISC) ICNISC 2017 Table of Contents Preface xii Conference Organization xiii Program Committee xiv Keynotes xv Computer Network -

Factors Affecting Logistics Development in Gulin County And
2019 4th International Conference on Electromechanical Control Technology and Transportation (ICECTT 2019) Guilin, China 26 – 28 April 2019 IEEE Catalog Number: CFP19T75-POD ISBN: 978-1-7281-0043-2 Copyright © 2019 by the Institute of Electrical and Electronics Engineers, Inc. All Rights Reserved Copyright and Reprint Permissions: Abstracting is permitted with credit to the source. Libraries are permitted to photocopy beyond the limit of U.S. copyright law for private use of patrons those articles in this volume that carry a code at the bottom of the first page, provided the per-copy fee indicated in the code is paid through Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923. For other copying, reprint or republication permission, write to IEEE Copyrights Manager, IEEE Service Center, 445 Hoes Lane, Piscataway, NJ 08854. All rights reserved. *** This is a print representation of what appears in the IEEE Digital Library. Some format issues inherent in the e-media version may also appear in this print version. IEEE Catalog Number: CFP19T75-POD ISBN (Print-On-Demand): 978-1-7281-0043-2 ISBN (Online): 978-1-7281-0042-5 Additional Copies of This Publication Are Available From: Curran Associates, Inc 57 Morehouse Lane Red Hook, NY 12571 USA Phone: (845) 758-0400 Fax: (845) 758-2633 E-mail: [email protected] Web: www.proceedings.com 2019 4th International Conference on Electromechanical Control Technology and Transportation (ICECTT) ICECTT 2019 Table of Contents Preface xv Conference Organization xvi International Technical -

Master's Program in Environmental Engineering
Master’s Program in Environmental Engineering Title/degree: Master of Environmental Engineering (M.E) Duration: 2-3 years, full-time Start month: September Language of instruction: English I. Program Description The people who incept master's degree in this field need to master basic theories of environmental engineering (pollution control in water, air and solid waste), strategic thought of sustainable development, environmental management and planning, cleaner production, waste resource recovery, urban ecology etc. and systematical professional knowledge. II. Why study Environmental Engineering at Donghua University? 1. Depart. Environmental Engineering (EE) of Donghua University is one of the earliest environmental disciplines established in China. It started to enroll undergraduate in 1976, and it obtained doctoral discipline of environment engineering in 2000, class-one doctoral discipline of Environmental Science and Engineering in 2005 and established post-doctoral station in 2007, which has a comprehensive system of cultivating bachelor, master, PhD and post doctorate. The subject is in the forefront of the same kind subject of colleges and universities with 211 Project, and is also with distinctive feature of textile. It is the vice president of China dyeing and Printing Industry Association as well as the vice director unit of Environmental Protection Committee of professional technical. The environment technology specialty has been approved the key subject of Shanghai in 2007, the national characteristic specialty in 2011, and have been incorporated in the national first ‘excellent engineers education training plan’ and ‘Comprehensive reform of the Education Ministry’. In 2012 ESE as the class-one discipline was included in the first-class discipline (class B) construction plan in Shanghai. -
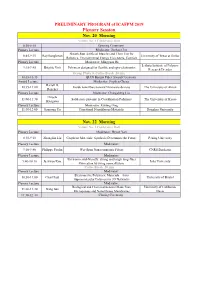
2019ICAFPM-PRELIMINARY PROGRAM-07112019.Xlsx
PRELIMINARY PROGRAM of ICAFPM 2019 Plenary Session Nov. 20 Morning Venue: No. 1 Conference Hall 8:30-8:45 Opening Ceremony Plenary Lecture Moderator: Junhao Chu Sheath-Run Artificial Muscles and Their Use for 8:45-9:15 Ray Baughman University of Texas at Dallas Robotics, Environmental Energy Harvesters, Comfort Plenary Lecture Moderator: Mingyuan He Leibniz Institute of Polymer 9:15-9:45 Brigitte Voit Polymers designed for flexible and opto-electronics Research Dresden Group Photo & Coffee Break 20 min 10:05-10:35 QIAN Baojun Fiber Award Ceremony Award Lecture Moderator: Stephen Cheng Darrell H. 10:35-11:00 Inside nanofibers toward Nanoware devices The University of Akron Reneker Plenary Lecture Moderator: Changsheng Liu Hiroshi 11:00-11:30 Solid-state protonic in Coordination Polymers The University of Kyoto Kitagawa Plenary Lecture Moderator: Kuiling Ding 11:30-12:00 Jianyong Yu Functional Nanofibrous Materials Donghua University Nov. 22 Morning Venue: No. 1 Conference Hall Plenary Lecture Moderator: Deyue Yan 8:30-9:10 Zhongfan Liu Graphene Materials: Synthesis Determines the Future Peking University Plenary Lecture Moderator: 9:10-9:40 Philippe Poulin Wet-Spun Nanocomposite Fibers CNRS Bordeaux Plenary Lecture Moderator: Environmental-friendly, strong and tough long-fiber 9:40-10:10 Jaehwan Kim Inha University fabrication by using nanocellulose Coffee Break 20 min Plenary Lecture Moderator: Electroactive Polymeric Materials – from 10:30-11:00 Charl Faul University of Bristol Supramolecular Polymers to 3D Networks Plenary Lecture Moderator: Biological and Chemical Sensors Made from University of California, 11:00-11:30 Gang Sun Microporous and Nanofibrous Membranes Davis 11:30-12:00 Closing Ceremony PRELIMINARY PROGRAM of ICAFPM 2019 Parallel Session Nov. -

The Relationship Between the Facial Expression of People in University Campus and Host- City Variables
Supplementary: The relationship between the facial expression of people in university campus and Host- city variables Hongxu Wei 1, Richard J. Hauer 2 and Xuquan Zhai 3,* 1 Northeast Institute of Geography and Agroecology, Chinese Academy of Sciences, Changchun 130102, China; [email protected] 2 College of Natural Resources, University of Wisconsin–Stevens Point, 800 Reserve St., Stevens Point, WI 54481, United States; [email protected] 3 China Center for Public Sector Economy Research, Jilin University, Room 3007, Kuang, Yaming Building, 2699 Qianjin Road, Chaoyang District, Changchun 130012, China, Changchun 130012, China; * Correspondence: [email protected]; Tel.: +86-431-8516-8829 Figure S1. The panel of FireFACETM-V1.0 to recognize photos with typically happy, sad, and neutral facial expressions. The model is Ryōko Hirosue from Japan. Photos are downloaded from following websites: Happy: https://images.app.goo.gl/Kh5FgWEMMSPUa3sD9 Sad: https://images.app.goo.gl/GazwjvTh8a6qiyBa9 Neutral: https://images.app.goo.gl/Hn2gtLonVpoLd5o27 Figure S2. The copyright of the FireFACETM-V1.0 software that is authorized in mainland China. Table S1. The list of key universities in the 211-Project of mainland China with Province and City names. Rank Province City University name 1 Anhui University 2 Anhui Hefei Hefei University of Technology 3 University of Science and Technology of China 4 Beijing Foreign Studies University 5 Beijing Forestry University 6 Beijing Institute of Technology 7 Beijing Jiaotong University 8 Beijing Normal University -

Initiative Disciplines Development List 01 Natural and Physical Sciences (100)
“Double First-Class” initiative disciplines development list (Sorted by discipline) Note: The list was published by the Ministry of Education of the People’s Republic of China on 21 September 2017. This list sorted by discipline has been prepared by the Education and Research Section, Australian Embassy, Beijing based on the Australian Standard Classification of Education (ASCED) 2001, Australian Bureau of Statistics. Initial translation credit to Science, Technology and Education Section, Embassy of Switzerland in China. 01 Natural and Physical Sciences (100) Astronomy (2) Nanjing University University of Science and Technology of China Atmosphere Science (3) Nanjing University Nanjing University of Information Science & Technology Lanzhou University Biology (16) Peking University Tsinghua University China Agricultural University Peking Union Medical College Inner Mongolia University Fudan University Shanghai Jiao Tong University Nanjing University Zhejiang University University of Science and Technology of China Xiamen University Huazhong Agricultural University Henan University Sun Yat-sen University Wuhan University Southwest University Chemistry (25) Peking University Tsinghua University Nankai University Tianjin University Dalian University of Technology Jilin University Northeast Normal University Fudan University Shanghai Jiao Tong University East China University of Science and Technology Nanjing University Zhejiang University Xiamen University University of Science and Technology of China Fuzhou University Shandong University -

Chinese University Disciplines Assessment Outcome (A+) (Round 4)
Chinese University Disciplines assessment outcome (A+) (Round 4) Note: The Chinese University Disciplines Assessment (round 4) outcome was published by the China Academic Degrees and Graduate Education Development Centre on 28 December 2017. This translated document prepared by the Education and Research Section, Australian Embassy, Beijing lists universities that have been rated A+ for the following disciplines and subjects.1 Table of Contents 1 Humanities and Social Sciences .................................................................................. 1 2 Sciences ...................................................................................................................... 2 3 Engineering and Technology ...................................................................................... 3 4 Agriculture .................................................................................................................. 5 5 Medical Science .......................................................................................................... 6 6 Management .............................................................................................................. 7 7 Arts .............................................................................................................................. 7 1 Humanities and Social Sciences Philosophy Peking University Fudan University Theoretical Economics Renmin University of China Fudan University Applied Economics Peking University Renmin University of China Central University -
Second Announcement of the Conference
The Fourth International Conference on Recent Advances in Applied Dynamical Systems (Second Announcement) Zhejiang Normal University Jinhua, Zhejiang, China June 17{20, 2010 Financial support: Zhejiang Normal University, National Natural Science Foundation of China, National Science Foundation of United States (pending) Topics: Advances in all aspects of dynamical systems research, including differential/difference equations, bifurcation theory and chaos and applications to biology, economics, engineering, chemistry, fluid dynamics, neural networks, physics and other nonlinear sciences. Format: More than 80 invited speakers from China, USA, Canada, Japan and other coun- tries will give 40 minute talks on dynamical systems and applications. A limited number of slots in the 20 minute contributed talk session or the poster session are available for junior mathematicians who wish to present their results. Registration: If you plan to participate this conference, please send us an e-mail by May 1, 2010 to the organizing committee via email [email protected] and containing your name, affiliation, postal address, e-mail address, travel schedule and additional information and comments. Deadline: The deadline for registration is May 1, 2010. Titles and abstracts of all the invited talks/contributed talks/poster must be received by May 1, 2010. Abstracts should be typed in LaTeX or plain text document, containing your name, institute affiliation, postal address, e-mail address, title and abstract, not to exceed 200 words and sent by email to [email protected]. -

Chair"S Message
GreetingsGreetings fromfrom GeneralGeneral ConferenceConference ChairsChairs 20092009 IEEEIEEE InternationalInternational ConferenceConference onon IntelligentIntelligent ComputingComputing andand IntelligentIntelligent SystemsSystems ((ICISICIS 2009)2009) NovemberNovember 2020--22,22, 20092009 Shanghai,Shanghai, ChinaChina http://www.icis09.http://www.icis09.cncn// WelcomeWelcome WelcomeWelcome toto 20092009 IEEEIEEE InternationalInternational ConferenceConference onon IntelligentIntelligent ComputingComputing andand IntelligentIntelligent SystemsSystems (ICIS09)(ICIS09) WelcomeWelcome toto Shanghai,Shanghai, China!China! WelcomeWelcome WeWe hopehope thatthat youyou willwill enjoyenjoy thethe ICISICIS 20092009 technicaltechnical programprogram andand thethe irresistibleirresistible attractionattraction offeredoffered byby thethe amazingamazing citycity ofof ShanghaiShanghai ICISICIS 20092009 OrganizerOrganizer andand SponsorsSponsors Organizers:Organizers: •• ShanghaiShanghai JiaotongJiaotong UniversityUniversity •• XiamenXiamen UniversityUniversity Sponsor:Sponsor: •• IEEEIEEE BeijingBeijing SectionSection CoCo--sponsors:sponsors: •• IEEEIEEE ShanghaiShanghai Section,Section, ChinaChina •• CityCity UniversityUniversity ofof HongHong KongKong •• IwateIwate PrefecturePrefecture UniversityUniversity ICISICIS 20092009 CommitteesCommittees General Conference Co-Chairs: – Changle Zhou, Xiamen University, China – Xiaotie Deng, City University of Hong Kong, China – Kenzoh Itoh, Iwate Prefectural University, Japan Technical Program Committee -

Collaboration of UNC-System Universities with China in Education and Beyond Bailian Li Vice Provost for International Affairs North Carolina State University Outline
Collaboration of UNC-System Universities with China in Education and Beyond Bailian Li Vice Provost for International Affairs North Carolina State University Outline • Overview of North Carolina University partnerships with China – Chinese Language Programs – Community Outreach – Business Relationships • Some highlighted China Programs • Q&A Chinese Language Programs • ASU- program since 1998 with Soochow University • FSU- program since 2006 with Inner Mongolia University • UNCW- program since 2007 with Fudan University • NCSU- Chinese language minor and non credit classes through CI • UNC-CH- major and minor in Chinese • UNC-A- working on a grant with the Asian Studies Development Program in Hawaii which will create minor in Chinese Language and Culture Community Outreach • Two Confucius Institutes in North Carolina – 2007- North Carolina State University, partnership with Nanjing Normal University – 2009- Pfeiffer University, partnership with Shanxi University • WCU- Summer 2010, bringing 30 Chinese students to area to be paired with American students for a summer camp • UNC-CH- Partnership for Social Science Research on HIV/AIDS in China • UNCW- exploring collaboration with Wilmington sister city in Dandong, near Korean Border Business Relationships • WSSU- Business and International Education Grant , to increase business exposure to China through Faculty Development Programs, internships and community awareness • NCA&T – summer “Business in China” course • ASU- partnership with Insigma Hengtian Software Company in Hangzhou and China.org.cn -

Scope and Topics: Program Committee Chairs
ICAIS 2021 Workshop Proposal Title: Internet of Things, Crowdsourcing and Mobile Computing. Abstract: The Internet of Things (IoT) is a dynamic global information network consisting of internet-connected objects, such as RFIDs, sensors, actuators, as well as other instruments and smart appliances that are becoming an integral component of the future internet. It is moving towards pervasiveness and increasing end-user interactions. Beyond the technical improvement in the IoT technology, there is also a need to better interact with the end-users in order to ensure a high level of acceptance and to leverage on their active use of the IoT. The workshop will explore the potential of new approaches and technologies to research and develop better interactions between end-users and IoT, including crowdsourcing approaches. Scope and Topics: Potential topics include but are not limited to: Internet of Things and Its Applications Wireless Sensor Network Crowdsourcing and crowd-sensing technologies Mobile Computing Data Security in the IoT IoT Privacy and personal data protection Attacks and Countermeasures on IoT Systems Trust Model, Data Aggregation and Information Sharing Secure Hardware and Software for IoT Application Security for IoT… Program Committee Chairs: Guiling Wang, New Jersey Institute of Technology, USA [email protected] https://web.njit.edu/~gwang/ Guiling Wang is currently a professor of the Yingwu College of Computing Sciences and the MT School of Management at NJIT. She joined NJIT in July 2006 as an Assistant Professor. She was promoted to Associate Professor with tenure in June 2011 and to full professor in June 2016. She received her Ph.D.