Fact Sheet: Designation of Election Infrastructure As Critical Infrastructure
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

John H. Merrill Secretary of State
ALABAMA STATE CAPITOL (334) 242-7200 600 DEXTER AVENUE FAX (334) 242-4993 SUITE S-105 WWW.SOS.ALABAMA.GOV MONTGOMERY, AL 36130 [email protected] JOHN H. MERRILL SECRETARY OF STATE October 2, 2020 Senator Mitch McConnell 317 Russell S.O.B. Washington, DC 20510 Dear Majority Leader McConnell: Thank you for your swift action to hold hearings and to make certain that each Senator has the opportunity to consider the President’s nomination to fill the open seat on the Supreme Court of the United States. It is of utmost importance that the Supreme Court has a full nine-member court before Election Day on November 3, 2020. Maintaining the integrity and credibility of our elections is of paramount significance to each of us as our state’s respective chief election official. Americans must be able to exercise their constitutional right to vote with confidence, knowing their ballot will be counted for the candidate of their choice. In the case an election issue is challenged in court, America cannot afford a tie vote. We must be able to report election results in a timely, secure, and efficient manner as we have done before. The Honorable Amy Coney Barrett is an outstanding nominee for consideration for a vacancy on the Supreme Court of the United States. She brings with her an unblemished record and extensive experience as a litigator and distinguished professor of law at the University of Notre Dame. Her philosophy and tried and true beliefs of upholding the constitution and the laws of our nation as written make her an excellent choice for our nation’s highest court. -

NASS Resolution on Threats of Violence Toward Election Officials and Election Workers
NASS Resolution on Threats of Violence Toward Election Officials and Election Workers Introduced by Hon. Kyle Ardoin (R-LA) Co-Sponsored for Introduction by: Hon. Kevin Meyer (R-AK) Hon. John Merrill (R-AL) Hon. Jena Griswold (D-CO) Hon. Paul Pate (R-IA) Hon. Scott Schwab (R-KS) Hon. Michael Adams (R-KY) Hon. Jocelyn Benson (D-MI) Hon. Steve Simon (D-MN) Hon. Michael Watson (R-MS) Hon. Al Jaeger (R-ND) Hon. Maggie Toulouse Oliver (D-NM) Hon. Barbara Cegavske (R-NV) Hon. Shemia Fagan (D-OR) Hon. Kim Wyman (R-WA) WHEREAS, the 2020 election cycle was the most challenging in recent memory, with a global pandemic and multiple natural disasters affecting numerous states and their election infrastructure and processes; and WHEREAS, election workers across the country worked tirelessly under difficult conditions to ensure a fair, safe and accurate election for the more than 155 million voters in November; and WHEREAS, based upon unrelenting misinformation and disinformation from both domestic and foreign sources, extremists have taken to threatening and endangering election workers, from Secretaries of State, state election directors, local election officials and election workers; and WHEREAS, the cornerstone of our republic is the right of Americans to vote in a safe, secure and accurate election, and their exercising of that right; and WHEREAS, election workers are a vital part of ensuring the exercise of that right for all eligible Americans; and WHEREAS, violence and violent threats directed at Secretaries of State, their families, staff, and other election workers is abhorrent and the antithesis of what our nation stands for. -

Notice of Election
NOTICE OF ELECTION Notice is hereby given that a General Election will be held in the State of Missouri on the 8th day of November, 2016 for the purpose of voting on candidates and statewide ballot measures (Section 115.125, RSMo). DEMOCRATIC PARTY REPUBLICAN PARTY LIBERTARIAN PARTY CONSTITUTION PARTY GREEN PARTY FOR PRESIDENT AND VICE PRESIDENT (VOTE FOR 1) HILLARY RODHAM CLINTON TIMOTHY MICHAEL KAINE DEMOCRATIC PARTY DONALD J. TRUMP MICHAEL R. PENCE REPUBLICAN PARTY GARY JOHNSON BILL WELD LIBERTARIAN PARTY DARRELL L. CASTLE SCOTT N. BRADLEY CONSTITUTION PARTY JILL STEIN AJAMU BARAKA GREEN PARTY FOR UNITED STATES SENATOR (VOTE FOR 1) JASON KANDER DEMOCRATIC PARTY ROY BLUNT REPUBLICAN PARTY JONATHAN DINE LIBERTARIAN PARTY FRED RYMAN CONSTITUTION PARTY JOHNATHAN MCFARLAND GREEN PARTY FOR GOVERNOR (VOTE FOR 1) CHRIS KOSTER DEMOCRATIC PARTY ERIC GREITENS REPUBLICAN PARTY CISSE W SPRAGINS LIBERTARIAN PARTY DON FITZ GREEN PARTY LESTER BENTON (LES) TURILLI, JR. INDEPENDENT FOR LIEUTENANT GOVERNOR (VOTE FOR 1) RUSS CARNAHAN DEMOCRATIC PARTY MIKE PARSON REPUBLICAN PARTY STEVEN R. HEDRICK LIBERTARIAN PARTY JENNIFER LEACH GREEN PARTY FOR SECRETARY OF STATE (VOTE FOR 1) ROBIN SMITH DEMOCRATIC PARTY JOHN (JAY) ASHCROFT REPUBLICAN PARTY CHRIS MORRILL LIBERTARIAN PARTY FOR STATE TREASURER (VOTE FOR 1) JUDY BAKER DEMOCRATIC PARTY ERIC SCHMITT REPUBLICAN PARTY SEAN O’TOOLE LIBERTARIAN PARTY CAROL HEXEM GREEN PARTY FOR ATTORNEY GENERAL (VOTE FOR 1) TERESA HENSLEY DEMOCRATIC PARTY JOSH HAWLEY REPUBLICAN PARTY FOR UNITED STATES REPRESENTATIVE DISTRICT 4 -

Sample Ple Sample Sam Ample Sample Sam
SAMPLE SAMPLE SAMPLE SAMPLE SAMPLE SAMPLE SAMPLE SAMPLE SA SAMPLE SAMPLE SA SAMPLE SAMPLE SA MPL SAMPLE SAMPLE SA MPL DEM SAMPLEREP SAMPLE MPLE SA E in the County ofSAMPLE Cass SAMPLE MPLE Vote for ONE SA FOR ATTORNEY GENERAL MPLE SAMPLE DEM SAMPLE SA TERESA HENSLEY REP JOSH HAWLEY SAMPLELIB MPLE DISTRICT 4 SA Write-in OFFICIAL SAMPLE BALLOT DEM Vote for ONE eneral Election will be held REP SAMPLE MPLE SAM CASS COUNTY, MISSOURI FOR UNITED STATES REPRESENTATIVE SA LIB LIBERTARIAN - (LIB); CONSTITUTION - (CST); GREEN - (GRN); INDEPENDENT - (IND) NOTICE OF ELECTION GRN GORDON CHRISTENSEN REP MPLE SAMPLE GENERAL ELECTION - NOVEMBER 8, 2016 SAMPLE LIB IND VICKY HARTZLER SA FOR GOVERNORVote for ONE MARK BLISS IND MPLE SAMPLE SAMPLEWrite-in DISTRICT 31 FOR STATEVote SENATOR for ONE SA CHRIS KOSTER DEM MPLE SAMPLE ERIC GREITENS SAMPLEREP SA LIB CISSE W SPRAGINS ED EMERY DEM DON FITZ SAMPLEGRN LORA YOUNG SA MPLREP E SAMPLE LESTER BENTON (LES) TURILLI, JR. TIM WELLS DEMOCRATIC - (DEM); REPUBLICAN - (REP); Vote for ONE DEM Write-in Write-in DISTRICT 33 SAMPLE Vote for ONE MPLE SAMPLE Notice is hereby given that the November G FOR LIEUTENANT GOVERNOR SA FOR STATE REPRESENTATIVE REP DEM on Tuesday, November 8, 2016 as certified to this office by the participating entitiesSAMPLERUSS of CARNAHAN Cass County. REP MPLE SAM LIB MIKE PARSON SALIB CHASE LINDER The ballot for the election shall be in substantially the following form: STEVEN R. HEDRICK DONNA PFAUTSCH A vote for candidates forVote President for ONE PAIR and MPLE CST JENNIFER LEACH SAMPLE Vice President is a vote for their Electors. -

Jena M. Griswold Colorado Secretary of State
Jena M. Griswold Colorado Secretary of State July 28, 2020 Senator Mitch McConnell Senator Charles E. Schumer Senator Richard C. Shelby Senator Patrick J. Leahy Senator Roy Blunt Senator Amy Klobuchar Dear Senators: As Secretaries of State of both major political parties who oversee the election systems of our respective states, we write in strong support of additional federal funding to enable the smooth and safe administration of elections in 2020. The stakes are high. And time is short. The COVID-19 pandemic is testing our democracy. A number of states have faced challenges during recent primary elections. Local administrators were sometimes overwhelmed by logistical problems such as huge volumes of last-minute absentee ballot applications, unexpected shortages of poll workers, and difficulty of procuring and distributing supplies. As we anticipate significantly higher voter turnout in the November General Election, we believe those kinds of problems could be even larger. The challenge we face is to ensure that voters and our election workers can safely participate in the election process. While none of us knows what the world will look like on November 3rd, the most responsible posture is to hope for the best and plan for the worst. The plans in each of our states depend on adequate resources. While we are truly grateful for the resources that Congress made available in the CARES Act for election administration, more funding is critical. Current funding levels help to offset, but do not cover, the unexpectedly high costs that state and local governments face in trying to administer safe and secure elections this year. -
State General Election Ballot Carver County, Minnesota November 6
SAMPLE BALLOT 11 Official Ballot State General Election Ballot Carver County, Minnesota Judge _____ November 6, 2018 Judge _____ Instructions to Voters: 21 To vote, completely fill in the oval(s) next to your choice(s) like this ( ) Federal Offices State Offices City Offices State Auditor U.S. Senator Vote for One Mayor For term expiring January 3, 2025 City of Carver Vote for One Pam Myhra Vote for One Republican Jim Newberger January 3, 2025 Julie Blaha Republican Democratic-Farmer-Labor Kristy Mock Amy Klobuchar January 3, 2025 Michael Ford Democratic-Farmer-Labor Legal Marijuana Now Courtney Johnson Dennis Schuller January 3, 2025 Chris Dock Legal Marijuana Now Libertarian Party Paula M Overby January 3, 2025 Minnesota Green Party write-in, if any 40 write-in, if any Council Member at Large City of Carver 41 Attorney General write-in, if any Vote for One Vote for Up to Two 42 Doug Wardlow U.S. Senator Republican Glen Henry Special Election for term expiring Keith Ellison Laurie Sayre January 3, 2021 Democratic-Farmer-Labor 44 Vote for One Noah M. Johnson Grassroots - Legalize Cannabis Ryan Schultz Karin Housley January 3, 2021 Republican Tina Smith January 3, 2021 Democratic-Farmer-Labor Sarah Wellington January 3, 2021 Legal Marijuana Now write-in, if any write-in, if any Jerry Trooien January 3, 2021 Unaffiliated County Offices County Sheriff Vote for One Jessica Heger write-in, if any write-in, if any Jason Kamerud School District Offices 53 U.S. Representative District 6 Vote for One School Board Member Tom Emmer Independent School District Republican No. -

2021 Bicentennial Inauguration of Michael L. Parson 57Th Governor of the State of Missouri
Missouri Governor — Michael L. Parson Office of Communications 2021 Bicentennial Inauguration of Michael L. Parson 57th Governor of the State of Missouri On Monday, January 11, 2021, Governor Michael L. Parson will be sworn in as the 57th Governor of the State of Missouri at the 2021 Bicentennial Inauguration. Governor Michael L. Parson Governor Parson is a veteran who served six years in the United States Army. He served more than 22 years in law enforcement, including 12 years as the sheriff of Polk County. He also served in the Missouri House of Representatives from 2005-2011, in the Missouri Senate from 2011-2017, and as Lieutenant Governor from 2017-2018. Governor Parson and First Lady Teresa live in Bolivar. Together they have two children and six grandchildren. Governor Parson was raised on a farm in Hickory County and graduated from Wheatland High School in Wheatland, Missouri. He is a small business owner and a third generation farmer who currently owns and operates a cow and calf operation. Governor Parson has a passion for sports, agriculture, Christ, and people. Health and Safety Protocols State and local health officials have been consulted for guidance to protect attendees, participants, and staff on safely hosting this year’s inaugural celebration. All inauguration guests will go through a health and security screening prior to entry. Inaugural events will be socially distanced, masks will be available and encouraged, and hand sanitizer will be provided. Guests were highly encouraged to RSVP in advance of the event in order to ensure that seating can be modified to support social distancing standards. -

Resolution Reaffirming the NASS Position on Funding and Authorization of the U.S
Resolution Reaffirming the NASS Position on Funding and Authorization of the U.S. Election Assistance Commission WHEREAS, the National Association of Secretaries of State (NASS), on February 6, 2005, voted to approve a resolution by a substantial majority asking Congress not to reauthorize or fund the U.S. Election Assistance Commission (EAC) after the conclusion of the 2006 federal election, by which date all the states were required to fully implement the mandates of the Help America Vote Act; and WHEREAS, the 2005 resolution was passed to help prevent the EAC from eventually evolving into a regulatory body, contrary to the spirt of the Help America Vote Act; and WHEREAS, that action was meant to preserve the state’ ability to serve as laboratories of change through successful experiments and innovation in election reform; and WHEREAS, each resolution passed at a NASS conference sunsets after five years unless reauthorized by a vote of the members; and WHEREAS, the NASS position on funding and authorization of the U.S. Election Assistance Commission was renewed by the membership on July 20, 2010; NOW THEREFORE BE IT RESOLVED that the National Association of Secretaries of State, expressing their continued consistent position in 2015, reaffirm their resolution of 2005 and 2010 and encourage Congress not to reauthorize or fund the U.S. Election Assistance Commission. Adopted the 12th day of July 2015 in Portland, ME EXPIRES: Summer 2020 Hall of States, 444 N. Capitol Street, N.W., Suite 401, Washington, DC 20001 (202) 624-3525 Phone (202) 624.3527 Fax www.nass.org On the motion to adopt the Resolution Reaffirming the NASS Position on Funding and Authorization of the U.S. -

California Secretary of State Dr. Shirley N. Weber Statement on Signing Bipartisan Letter to CISA Secretary Mayorkas and Acting Director Wales
SW21:018 FOR IMMEDIATE RELEASE April 16, 2021 CONTACT: SOS Press Office (916) 653-6575 California Secretary of State Dr. Shirley N. Weber Statement on Signing Bipartisan Letter to CISA Secretary Mayorkas and Acting Director Wales SACRAMENTO, CA – California Secretary of State Dr. Shirley N. Weber issued the following statement on signing the letter to Department of Homeland Security’s Cyber and Infrastructure Security Agency (CISA) requesting an expansion of federal efforts to combat foreign disinformation. "Democracy exists because we have free and fair elections, and we must protect those elections at all costs. In 2020, our local and state election officials worked tirelessly to combat the spread of mis- and disinformation perpetuated by foreign actors seeking to diminish trust in our elections." "Without CISA's leadership combating this threat at the federal level, we would not be able to call the 2020 General Election the most secure in our nation's history. For this reason, I gladly join my bipartisan colleagues in calling on CISA not only to continue this vital work but expand its efforts to combat the ongoing threat of foreign interference in our elections." The complete letter can be accessed here and is co-signed by Kevin Meyer, Alaska Lt. Governor; Jena Griswold, Colorado Secretary of State; Shenna Bellows, Maine Secretary of State; William Francis Galvin, Secretary of the Commonwealth of Massachusetts; Jocelyn Benson, Michigan Secretary of State; Maggie Toulouse Oliver, New Mexico Secretary of State; Shemia Fagan, Oregon Secretary of State; Nellie Gorbea, Rhode Island Secretary of State; Jim Condos, Vermont Secretary of State, and Kim Wyman, Washington Secretary of State. -
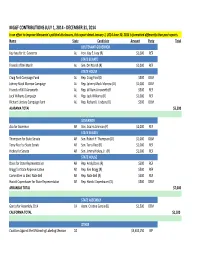
5-21-15 UPDATED FORMAT MGGF Contributions July
MGGF CONTRIBUTIONS JULY 1, 2014 - DECEMBER 31, 2014 In an effort to improve Monsanto's political disclosures, this report dated January 1, 2014-June 30, 2014 is formatted differently than past reports. Name State Candidate Amount Party Total LIEUTENANT GOVERNOR Kay Ivey for Lt. Governor AL Hon. Kay E. Ivey (R) $1,000 REP STATE SENATE Friends of Del Marsh AL Sen. Del Marsh (R) $1,000 REP STATE HOUSE Craig Ford Campaign Fund AL Rep. Craig Ford (D) $500 DEM Johnny Mack Morrow Campaign AL Rep. Johnny Mack Morrow (D) $1,000 DEM Friends of Will Ainsworth AL Rep. William Ainsworth (R) $500 REP Jack Williams Campaign AL Rep. Jack Williams (R) $1,000 REP RIchard Lindsey Campaign Fund AL Rep. Richard J. Lindsey (D) $500 DEM ALABAMA TOTAL $5,500 GOVERNOR Asa for Governor AR Gov. Asa Hutchinson (R) $2,000 REP STATE SENATE Thompson for State Senate AR Sen. Robert F. Thompson (D) $1,000 DEM Terry Rice for State Senate AR Sen. Terry Rice (R) $1,000 REP Hickey for Senate AR Sen. Jimmy Hickey, Jr. (R) $1,000 REP STATE HOUSE Davis for State Representative AR Rep. Andy Davis (R) $500 REP Bragg for State Representative AR Rep. Ken Bragg (R) $500 REP Committee to Elect Nate Bell AR Rep. Nate Bell (R) $500 REP Harold Copenhaver for State Representative AR Rep. Harold Copenhaver (D) $500 DEM ARKANSAS TOTAL $7,000 STATE ASSEMBLY Garcia for Assembly 2014 CA Assm. Cristina Garcia (D) $1,500 DEM CALIFORNIA TOTAL $1,500 OTHER Coalition Against the Misleading Labeling Measure CO $3,404,150 NP Colorado BioScience Political Action Committee CO $550 NP COLORADO TOTAL $3,404,700 AGRICULTURE COMMISSIONER Putnam for AG Commissioner FL Commissioner Adam H. -

AP II 2012.Pdf
We’re there for you NEW NEWTEC M6100 BROADCAST SATELLITE MODULATOR TECHNOLOGIES THAT HELP YOU GO FURTHER Newtec technologies allow billions of people to connect to the world, their families and each other. You can find our innovations and technologies anywhere. Whether we work for government agencies or private companies, we always see innovation as a way to reduce your costs and optimize your efficiency. Our global experience in multiple markets helps us in achieving our ultimate goal: taking care of your satellite communications while you can focus on your core activities. We’re there for you. Always and everywhere. Visit us at www.newtec.eu BELGIUM – USA – SINGAPORE – DUBAI – CHINA – BRAZIL BROADCAST GOVERNMENT AND DEFENCE IP TRUNKING BUSINESS AND CONSUMER VSAT All articles are available for download at www.connect-world.com CONTENTS Cloud opportunities Improving business fluidity with the Cloud 5 by Andrew Dobbins, Verizon’s vice president of Asia-Pacific 5 7 10 12 From video-communication to machine-to-machine - Cloud turns to business 7 by Karim Taga, managing partner and global practice leader, TIME, Arthur D. Little Enterprise adoption of Cloud computing: The next five years for IT 10 15 17 19 22 by Bernard Golden, CEO, HyperStratus Shore to shore: IT, the fifth utility 12 by Jim Fagan, VP and managing director, Rackspace Asia-Pacific Cloud security 24 26 29 31 Spear phishing in the Cloud 15 by GOH Hock Beng, vice president, Channel Sales Asia, TrustSphere Who Owns Security In The Cloud? 17 by Jim Reavis, founder and executive director, Cloud security Alliance; and Dave 33 36 39 42 Asprey, vice president of Cloud security, Trend Micro Data breach and risk in the Cloud - the legal response 19 by Thomas J. -

May 2017 M&A and Investment Summary
May 2017 M&A and Investment Summary Table of Contents 1 Overview of Monthly M&A and Investment Activity 3 2 Monthly M&A and Investment Activity by Industry Segment 8 3 Additional Monthly M&A and Investment Activity Data 42 4 About Petsky Prunier 55 Securities offered through Petsky Prunier Securities, LLC, member of FINRA. This M&A and Investment Summary has been prepared by and is being distributed in the United States by Petsky Prunier, a broker dealer registered with the U.S. SEC and a member of FINRA. 2 | M&A and Investment Summary May 2017 M&A and Investment Summary for All Segments Transaction Distribution . A total of 520 deals were announced in May 2017, of which 323 were worth $44.6 billion in aggregate reported value . Software was the most active segment with 189 deals announced — 123 of these transactions reported $10.0 billion in value . Digital Media/Commerce was also active with 117 transactions announced, of which 94 were worth a reported $14.1 billion in value . Strategic buyers announced 203 deals (49 reported $14.9 billion in value) . VC/Growth Capital investors announced 291 transactions (262 reported $15.7 billion in value) . Private Equity investors announced 26 deals during the month (12 reported $13.9 billion in value) May 2017 BUYER/INVESTOR BREAKDOWN Transactions Reported Value Strategic Buyout Venture/Growth Capital # % $MM % # $MM # $MM # $MM Software 189 36% $9,977.8 22% 59 $2,328.8 10 $4,845.0 120 $2,804.0 Digital Media/Commerce 117 23% 14,126.0 32% 36 2,027.4 2 1,500.0 79 10,598.6 Marketing Technology 85