Security Advisory MTIS10-235
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Windows Live Movie Maker: Create, Edit, and View Movies
Windows Live Movie Maker: Create, Edit, and View Movies By Andy Rathbone from Windows 7 For Dummies To create, edit, and view digital movies in Windows 7, you must download Windows Live Movie Maker. Windows Live Movie Maker — a stripped-down version of the movie-editing program that came with XP and Vista — works best for creating short videos. Download Movie Maker from Microsoft's Live Essentials Web page. You also need Windows Live Photo Gallery to import the movies from your camcorder. To make a movie, you follow three basic steps: 1. Import. For some reason, Windows Live Movie Maker can't import your video from your video camera. You must import it through Windows Live Photo Gallery, instead. 2. Edit. This step combines your video clips, music, and pictures into a structured movie. Edit each clip down to its best moments and add transitions between the clips — the way one clip fades into the next. Toss in a soundtrack, as well. 3. Publish. When you finish editing, Movie Maker combines your batch of clips or photos into a complete movie, ready to be played back on your computer or saved to a DVD. Creating movies requires a lot of free hard drive space. A 15-minute movie can consume 2.5GB. If Movie Maker complains about space, you have two choices: Create smaller videos or upgrade your computer with a second hard drive. Step 1: Import video, pictures, and music If you've already imported footage from a digital camcorder, jump ahead to Step 4 in the steps in this section and begin there. -
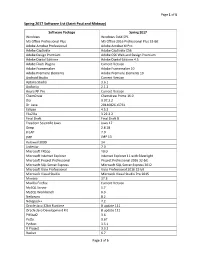
Spring 2017 Software List (Saint Paul and Midway)
Page 1 of 5 Spring 2017 Software List (Saint Paul and Midway) Software Package Spring 2017 Windows Windows 7x64 SP1 MS Office Professional Plus MS Office 2016 Professional Plus 32-Bit Adobe Acrobat Professional Adobe Acrobat XI Pro Adobe Captivate Adobe Captivate CS6 Adobe Design Premium Adobe CS6 Web and Design Premium Adobe Digital Editions Adobe Digital Editions 4.5 Adobe Flash Plugins Current Version Adobe Framemaker Adobe Framemaker 10 Adobe Premiere Elements Adobe Premiere Elements 10 Android Studio Current Version Aptana Studio 3.6.1 Audacity 2.1.2 Axure RP Pro Current Version ChemDraw Chemdraw Prime 16.0 Dia 0.97.2.2 Dr. Java 20140826-r5761 Eclipse 4.5.2 FileZilla 3.22.2.2 Final Draft Final Draft 8 Freedom Scientific Jaws Jaws 17 Gimp 2.8.18 JFLAP 7.0 JMP JMP 13 Kurzweil 3000 14 Lodestar 7.0 Microsoft FXCop 10.0 Microsoft Internet Explorer Internet Explorer 11 with Silverlight Microsoft Project Professional Project Professional 2016 32-bit Microsoft SQL Server Express Microsoft SQL Server Express 2012 Microsoft Visio Professional Visio Professional 2016 32-bit Microsoft Visual Studio Microsoft Visual Studio Pro 2015 Minitab 17.3 Mozilla Firefox Current Version MySQL Server 5.7 MySQL Workbench 6.3 Netbeans 8.2 Notepad++ 7.2 Oracle Java 32bit Runtime 8 update 111 Oracle Java Development Kit 8 update 111 PHStat2 3.6 Putty 0.67 Python 3.5.1 R Project 3.3.2 Racket 6.7 Page 1 of 5 Page 2 of 5 Software Package Spring 2017 Raptor Current Version SAP Client SAP Client 7.4.9 SAP Lumira 1.31.1 SAP Crystal Reports Current Version SPSS SPSS -

Program Windows Movie Maker (2012)
PaSA – CA – SZŠ INF/API: video editor Windows Movie Maker PaSA – CA – SZŠ INF/API: video editor Windows Movie Maker Program Windows Movie Maker (2012) Prehľad (čo je program Movie Maker) (ak chcete porozprávať svoj príbeh a vytvoriť zo svojich fotografií a videí ukážkový film už po pár kliknutiach, vaše Či už uprednostňujete Hollywood alebo nezávislú scénu, v programe Movie Maker ste režisérom vy. vlastné filmové štúdio získate jediným stiahnutím: http://go.microsoft.com/fwlink/p/?LinkID=255475 ) Import a úprava prezentácií a videí Zdroj: http://windows.microsoft.com/sk-sk/windows-live/movie-maker#t1=overview http://windows.microsoft.com/sk-sk/windows/music-video-photo-download Fotografie a videozáznamy z počítača alebo kamery môžete rýchlo pridať do programu Movie Maker . Tam potom http://sk.wikipedia.org/wiki/Windows_Movie_Maker , ... môžete doladiť svoj film podľa vlastných predstáv. Jednotlivé sekvencie môžete presúvať, zrýchľovať alebo spomaľovať – je len na vás, ako sa rozhodnete. Obsah: *) Úprava zvukovej stopy a pridanie motívu Charakteristika programu Niektoré systémové požiadavky Obohaťte svoj film o zvukovú stopu a motív . Program Movie Maker automaticky pridá prechody a efekty , aby film *) Prehľad ( čo je program Movie Maker) pôsobil elegantným a profesionálnym dojmom. Import fotografií a videí Zdieľanie filmu online (okrem toho naďalej môžete vaše video vypáliť na CD alebo DVD pre vaše domáce kino Úprava filmov alebo importovať do flashu) Úprava zvuku Výber motívu Po dokončení môžete svoj film zdieľať na Facebooku, YouTube alebo v iných sociálnych sieťach a lokalitách na Zdieľanie na webe zdieľanie videa. Pošlite prepojenie na svoj film v e-maile členom rodiny a priateľom, aby si ho mohli pozrieť . -
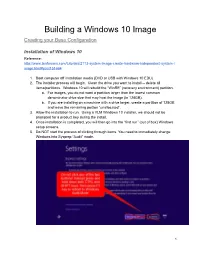
Building a Windows 10 Image Creating Your Base Configuration
Building a Windows 10 Image Creating your Base Configuration Installation of Windows 10 Reference: http://www.tenforums.com/tutorials/2113-system-image-create-hardware-independent-system-i mage.html#post151664 1. Boot computer off installation media (DVD or USB with Windows 10 EDU) 2. The installer process will begin. Clean the drive you want to install -- delete all items/partitions. Windows 10 will rebuild the “WinRE” (recovery environment) partition. a. For images, you do not want a partition larger than the lowest common denominator drive size that may host the image (ie 128GB). b. If you are installing on a machine with a drive larger, create a partition of 128GB and leave the remaining portion “unallocated”. 3. Allow the installation to run. Using a VLM Windows 10 installer, we should not be prompted for a product key during the install. 4. Once installation is completed, you will then go into the “first run” (out of box) Windows setup screens. 5. Do NOT start the process of clicking through items. You need to immediately change Windows into Sysprep “Audit” mode. 1 6. Windows reboots, and enters Audit Mode using the built-in “Administrator” account. When the desktop loads, you will notice the Sysprep box open in the middle of your screen. Close it for now by pressing the Cancel button. a. NOTE on AUDIT MODE: Throughout image construction process, remain in AUDIT Mode. When reboots are required, system will boot back up and auto-login to Administrator account. Sysprep box will be presented. Simply hit CANCEL option each time. Creation of “Base” Image In this stage, you will start setup and customization of your “template” profile. -
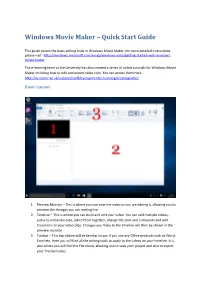
Windows Movie Maker – Quick Start Guide
Windows Movie Maker – Quick Start Guide This guide covers the basic editing tools in Windows Movie Maker, for more detailed instructions please visit - http://windows.microsoft.com/en-gb/windows-vista/getting-started-with-windows- movie-maker The e-learning team at the University has also created a series of online tutorials for Windows Movie Maker including how to edit and export video clips. You can access them here - http://as.exeter.ac.uk/support/staffdevelopment/e-learning/creatingvideo/ Basic Layout 1. Preview Monitor – This is where you can view the video as you are editing it, allowing you to preview the changes you are making live. 2. Timeline – This is where you can build and edit your video. You can add multiple videos, pictures and audio clips, splice them together, change the start and end points and add transitions to your video clips. Changes you make to the timeline will then be shown in the preview monitor. 3. Toolbar – This top ribbon will be familiar to you if you use any Office products such as Word, Excel etc. Here you will find all the editing tools to apply to the videos on your timeline. It is also where you will find the File menu, allowing you to save your project and also to export your finished video. Importing Video To get started you need to import a video that you have filmed. Click Home > Add videos and photos This will open up a new window, allowing you to browse your computer for video files. Choose a video and then select Open. -

Video Editing with Microsoft Movie Maker Contents
Video Editing with Microsoft Movie Maker Contents Introduction ..................................................................................................................... 2 Creating a new project ..................................................................................................... 2 Importing footage ............................................................................................................ 3 Import from DV tape ..................................................................................................... 3 Question ................................................................................................................... 4 Getting started ................................................................................................................. 4 Editor view ....................................................................................................................... 5 Editing a clip ..................................................................................................................... 6 Splitting clips .................................................................................................................... 6 Splitting a clip ............................................................................................................... 7 Question ................................................................................................................... 7 Trimming clips ................................................................................................................. -

Copyrighted Material
Index Note to the Reader: Page numbers in bold indicate the principle discussion of a topic or the defi- nition of a term. Page numbers in italic indicate illustrations. overview of, 251–252 A policy templates, 256–259 access control user exclusions, 253–254 applications, 209–210 Add Counters dialog box, 497 SMTP server access settings, 169–171 Add Features Wizard, 17–18 WSS end users, 292–294 Add Node Wizard, 423 access logs, 193–195 Add Roles Wizard, 319 formats, 195 ADFS (Active Directory overview of, 193–194 Federation Services) per-site and per-server, 194 configuring Web SSO, 300–304 rollover criteria, 194 Web SSO, 296 ACLs (Access control Lists) Admin logs, 469 creating, 248–249 admin switch, mstc.exe, 123–124 enabling ACL authorization, 247 Administrative Events custom view, activation. See WPA (Windows 472–473 Product Activation) administrative notices, WSS e-mail Active Directory Certificate Services settings, 273 (AD CS), 202 administrators Active Directory Federation event logs and, 472 Services (ADFS) WDS and, 366 configuring Web SSO, 300–304 advanced delivery options, SMTP Web SSO, 296 messages, 174–175 Active Directory Rights Management advanced streaming options, streaming Service. See AD RMS (Active media, 240 Directory Rights Management agent properties, SNMP, 501–502 Service) alerts, WSS outgoing e-mail settings, 273 AD (Active Directory), WDS server as alternate access mapping, WSS, 287–289 member of AD domain, 366 American National Standards Institute AD Client Certificate Authentication (ANSI), 195 client certificate -

Create Basic Home Videos
WINDOWS® GUIDE Create Basic Home Videos IN THIS GUIDE Connect a Camera Page 2 Import Video Page 5 Create a Video Page 13 Share a Video with Others Page 27 What You’ll Need n Windows® Movie Maker—included on Windows Vista® Ultimate and Home Premium editions n Windows Live™ Photo Gallery—available as a free download n A Windows Live ID—free to sign up n A digital video camera n A FireWire or USB 2.0 cable that fits the camera n A DVD burner (if you plan to publish your movies to DVD) n A computer running Windows Vista Windows Guides is a library of easy-to-use guides that show you how to get more from your Windows experience. Share these guides with your friends and family. © 2008 Microsoft. All rights reserved. WINDOWS GUIDE Create Basic Home Videos Connect a Camera Nothing captures special occasions and memorable moments quite like digital video. It’s hard to imagine that we ever managed without it. Family vacations, graduation, birthday parties, and weddings— all preserved and ready when you want to take a stroll down memory lane. Now there’s an easy way to store, edit and publish your movies, so that the people you care about can share in the memories too. TYPES OF CAMERA coNNECTIONS There are two ways to connect a digital video camera to your PC, and once you know which method works best with your camera, importing video is a snap. n A FireWire cable is the most popular method because it can transfer very large files both quickly and efficiently. -

Windows Movie Maker 2011
Windows Movie Maker 2011 User Guide Download, install and create video presentations using Windows Movie Maker 2011, part of the Microsoft Live Essentials package. Windows Movie Maker 2011 User Guide Before you Begin: Users of this Windows Movie Maker 2011 instruction manual are expected to have a basic understanding of the following software and hardware: z Microsoft Office Word z Word processing z Graphic image editing (resizing, cropping and saving to alternate formats) z Internet download procedures z File upload from external devices, including digital cameras, digital video cameras, digital voice recorders and smart phones. z The proper operation of digital media hardware, including digital cameras, digital video cameras, digital voice recorders and smart phones. ©2011 Andy Weingartner Table of Contents Chapter 1: Getting Started .....................................................5 Download and install Movie Maker ...........................................................5 System Requirements ...........................................................................5 Download and install Windows Live Essentials ...................................5 File Organization ......................................................................................10 File organization guidelines ................................................................10 Create and save your Movie Maker 2011 project file ..............................11 Chapter 2: Script & Narration .............................................13 Script Preparation ....................................................................................13 -

ACT PC Users Group
ACT PC Users Group Derek Moir Samesh Singh Solutions Specialist – Senior Consultant Infrastructure Windows Vista Key scenarios Easier More Secure Find and use Improve security and information legislative compliance Better Connected Lower Cost Enable your mobile Optimize desktop workforce infrastructure End IT Users Pros Find And Use Information Easier Find and use information Streamlined user experience » Advanced productivity and stability with Windows Aero (Authentic, Energetic, Reflective and Open) » Information visualization with Live Icons End Easy to search & organize your data Users » Fast, integrated desktop search » Smart tools to organize information Easy to navigate & search data online » Improved browsing with Tabs and Quick Tabs » Real-time data delivery with RSS feeds discovery Reliability » Self-healing and assisted problem resolution » Trustworthy Computing initiative Layout and visualization » Windows Explorer's task pane has been removed, integrating the relevant task options into the toolbar. » A Favourites pane on the left contains commonly accessed folders and pre-populated Search Folders. » Seven different views are available to view files and folders, » List, Details, Small icons, Medium icons, Large icons, Extra large icons or Tiles. » Windows Explorer visualization of files on a computer. » Details pane, which displays metadata and information relating to the currently selected file or folder. a graphical thumbnail of the file (known as live icon). » The preview panel allows you to see thumbnails of all sorts of files and view the contents of documents, similar to the way you can preview email messages in Outlook, without opening the files. » Icons in Windows Vista are visually more realistic than illustrative. "Windows Classic" visual style. "Windows Vista Basic" visual style. -

Computer Sci & Info Technology (Cst)
COMPUTER SCI & INFO TECHNOLOGY (CST) 1 CST 220 - SYSTEMS ENGINEERING II COMPUTER SCI & INFO This course surveys personal computer operating systems (Windows 7,8) and provides an introduction to networking technology. Topics TECHNOLOGY (CST) include file system design and management installation and upgrade of operating systems, input/output devices, and networking devices and CST 100 - ESSENTIAL COMPUTER SKILLS topologies. The course employs a computer troubleshooting approach in Basic hardware and software components of a PC; several of the most the instructional methodology. popular PC software applications including word processing, electronic Credits: 3 spreadsheets, databases, Power Point, Internet Browsers, and Windows. Prerequisites: CST 240 A computer use course. CST 232 - LAN Credits: 3 This course will provide a theoretical and practical guidance to Local Area CST 101 - BEYOND PC ESSENTIALS Networking using Windows 2016 Server software. The student will focus This course covers several interesting topics for students: Essential on installing, configuring, managing and troubleshooting the Windows Computer Concepts; Internet/Browsers; Windows; MS-Office; the 2016 environment. Network hardware requirements will be discussed. Web design; EBay; Windows Movie Maker; Photo Gallery; Simple Included are client server software installation, active directory set- Programming; and Publisher. In addition there is a field trip and up, network security, client account creation, and installation of print discussion of Emerging Technologies. services. The student will learn to monitor and optimize the system for Credits: 3 best performance. All concepts are introduced in both lecture and hands- CST 110 - QUANT PROB SOLV on laboratory exercises. Students will use Excel as a tool to solve problems which include critical Credits: 3 thinking and problem-solving skills that are necessary for decision- CST 236 - PYTHON SCRIPT PROGRAMMING making in everyday life. -

I Get No Image Or a Black Image with Webcam Station. What Should I Do?
I get no image or a black image with Webcam Station. What should I do? If you get no image or a black image when launching the “Webcam Station” software, please verify the following: 1- Make sure that the cap protecting your webcam’s lens is removed. 2- In Webcam Station, go to Preferences / Capture configuration and then select the Webcam Deluxe or Webcam Classic as the capture device, then click OK . 3- Make sure that no other program such as MSN, Skype or similar software is using your webcam. If this is the case, close the software using your webcam and then re- launch Webcam Station. 4- If this does not correct the problem, verify that your webcam is properly installed. To do so, please consult the FAQ “How can I make sure that my webcam’s drivers are properly installed on my computer? ”. 5- If the problem persists, verify that the latest version of DirectX is installed on your computer (Version 9.0c or later): To do so, click the Windows Start button, then click Run and enter the command “dxdiag.exe ”. Make a note of the DirectX version listed under System Information . If your version is not up to date, you can install the version of DirectX9.0c included on your CD-ROM. To do so, click the Windows Start button, then click Run and enter the command “D:\Redist\DirectX9\dxsetup.exe ”, “D” corresponding to the letter of your CD-ROM drive. Follow the on-screen instructions. 6- If the different steps detailed above have still not resolved your problem, reinstall Webcam Station from the installation CD-ROM.