Security Analysis of Xbox 360 Vulnerabilities
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Xbox LIVE Arcade Game Development Katie Stone Perez
Xbox LIVE Arcade Game Development Katie Stone Perez Sr. Game Program Manager Microsoft Endless Fun is Just a Download Away! Agenda What is Xbox LIVE Arcade The Growth of Xbox LIVE Arcade What’s New Portfolio Goals Questions What is Xbox LIVE Arcade? Xbox Live Arcade is a destination for users to download, try and buy broad appeal content on Xbox 360 High-visibility placement in every console (Games Blade) Deep Marketplace integration (download, purchase, licensing) Available to both Silver & Gold Xbox Live Subscribers Arcade-specific banner placements drives awareness of new titles Rich around-the-game feature set drives retention & repeat play What is an Xbox LIVE Arcade Game? Full game experience No pieces of games Must stand on its own Smaller in size <150 MB (most games <50 MB) Playable without physical media or other dependencies No instruction manual required Approachable pickup & play Free Trial Version with limited but entertaining gameplay Must up-sell to unlocked “full” version In-game promotional up-sell Plugs into Xbox Live Arcade around-the-game experiences Out-of-game Leaderboards Achievements & Gamerscore Cross-game invites Growth Of Xbox LIVE Arcade 25M games downloaded Instant hit on the Xbox 360, with nearly 70% of all connected consoles already downloading and playing Xbox LIVE Arcade titles. Widespread recognition of XBLA as a “key differentiator” for Xbox 360 Broad recognition of individual titles Over 600K search results for “Cloning Clyde” or “Assault Heroes” Rapid growth of XBLA publisher ecosystem Ultimately means more great games! Top Arcade Titles to Date Street Fighter II' HF Bankshot Billiards 2 Marble Blast Ultra UNO® DOOM® Xbox LIVE Arcade- What’s Next? Size Limit increase to 150 MB Additional Achievements and Gamerscore for PDLC (Paid Downloadable Content) 3 Additional achievements available for a total of 50 additional Gamerscore. -
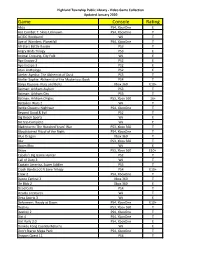
Game Console Rating
Highland Township Public Library - Video Game Collection Updated January 2020 Game Console Rating Abzu PS4, XboxOne E Ace Combat 7: Skies Unknown PS4, XboxOne T AC/DC Rockband Wii T Age of Wonders: Planetfall PS4, XboxOne T All-Stars Battle Royale PS3 T Angry Birds Trilogy PS3 E Animal Crossing, City Folk Wii E Ape Escape 2 PS2 E Ape Escape 3 PS2 E Atari Anthology PS2 E Atelier Ayesha: The Alchemist of Dusk PS3 T Atelier Sophie: Alchemist of the Mysterious Book PS4 T Banjo Kazooie- Nuts and Bolts Xbox 360 E10+ Batman: Arkham Asylum PS3 T Batman: Arkham City PS3 T Batman: Arkham Origins PS3, Xbox 360 16+ Battalion Wars 2 Wii T Battle Chasers: Nightwar PS4, XboxOne T Beyond Good & Evil PS2 T Big Beach Sports Wii E Bit Trip Complete Wii E Bladestorm: The Hundred Years' War PS3, Xbox 360 T Bloodstained Ritual of the Night PS4, XboxOne T Blue Dragon Xbox 360 T Blur PS3, Xbox 360 T Boom Blox Wii E Brave PS3, Xbox 360 E10+ Cabela's Big Game Hunter PS2 T Call of Duty 3 Wii T Captain America, Super Soldier PS3 T Crash Bandicoot N Sane Trilogy PS4 E10+ Crew 2 PS4, XboxOne T Dance Central 3 Xbox 360 T De Blob 2 Xbox 360 E Dead Cells PS4 T Deadly Creatures Wii T Deca Sports 3 Wii E Deformers: Ready at Dawn PS4, XboxOne E10+ Destiny PS3, Xbox 360 T Destiny 2 PS4, XboxOne T Dirt 4 PS4, XboxOne T Dirt Rally 2.0 PS4, XboxOne E Donkey Kong Country Returns Wii E Don't Starve Mega Pack PS4, XboxOne T Dragon Quest 11 PS4 T Highland Township Public Library - Video Game Collection Updated January 2020 Game Console Rating Dragon Quest Builders PS4 E10+ Dragon -

3,000 Xbox 360S on Pre-Sale at Ebay 21 November 2005
3,000 Xbox 360s on pre-sale at eBay 21 November 2005 eBay said Monday almost 3,000 Xbox 360 games are available for pre-sale, ahead of the official sale of the product at midnight Tuesday. The much-anticipated Microsoft game console will be going on sale when the clock strikes midnight nationwide, but the online auction house said about 9,000 Xbox 360s have been pre-sold for the past two weeks. eBay said that the average price sold was $550. Many have been bundled with game cartridges, the company said. Microsoft said Monday over 4,500 retailers nationwide will be opening at midnight Tuesday to sell the Xbox 360 game console. "The debut of Xbox 360 marks one of the biggest consumer launches in Microsoft's history," Robbie Bach, president of the entertainment division, said in a news release. The company said that Best Buy is its retail partner for the Xbox 360 launch events, and its stores will open at 9 a.m. on Nov. 22. In addition, Microsoft said more than 3,500 gamers from around the world descended on an Xbox 360 oasis in California's Mojave Desert Monday night to celebrate the arrival of the console at an exclusive launch party called Xbox 360: Zero Hour. The system launches Dec. 2 in Europe and Dec. 10 in Japan. Copyright 2005 by United Press International APA citation: 3,000 Xbox 360s on pre-sale at eBay (2005, November 21) retrieved 23 September 2021 from https://phys.org/news/2005-11-xbox-360s-pre-sale-ebay.html This document is subject to copyright. -
Kinect Manual
1 English 19 Français 37 Español 59 Português English WARNING Before using this product, read this manual, the Xbox 360® console 2 Xbox 360 Kinect Sensor instructions, and the manuals of any other accessories or games for 3 Adequate Space for Playing important safety and health information. Keep all manuals for future 4 Choose a Location for Your reference. For replacement manuals, Sensor visit www.xbox.com/support (see “If You Need More Help”). 5 Set Up Your Sensor The limited warranty covering this product appears in this manual, 9 Clean Your Sensor which is also available online at www.xbox.com/support. 10 Troubleshooting WARNING 11 If You Need More Help Before allowing children to use the Kinect sensor: 12 Limited Warranty • Determine how each child is able to use the sensor (playing games, 14 Software License chatting or video messaging with english other players online) and whether 16 Regulations they should be supervised during these activities. 18 Copyright • If you allow children to use the sensor without supervision, be sure to explain all relevant safety and health information and instructions. Make sure children using the Kinect sensor play safely. Make sure children using the Kinect sensor play safely and within their limits, and make sure they understand proper use of the system. This symbol identifies safety and health messages in this manual and Xbox 360 accessories manuals. 1 XBOX 360 KINECT SENSOR Xbox 360 Kinect Sensor Thanks for choosing the Xbox 360® Kinect™ Sensor. The Kinect sensor offers a revolutionary new way to play: you’re the controller. -

Kinect for Xbox 360
MEDIA ALERT “Kinect” for Xbox 360 sets the future in motion — no controller required Microsoft reveals new ways to play that are fun and easy for everyone Sydney, Australia – June 15th – Get ready to Kinect to fun entertainment for everyone. Microsoft Corp. today capped off a two-day world premiere in Los Angeles, complete with celebrities, stunning physical dexterity and news from a galaxy far, far away, to reveal experiences that will transform living rooms in North America, beginning November 4th and will roll out to Australia and the rest of the world thereafter. Opening with a magical Cirque du Soleil performance on Sunday night attended by Hollywood’s freshest faces, Microsoft gave the transformation of home entertainment a name: Kinect for Xbox 360. Then, kicking off the Electronic Entertainment Expo (E3), Xbox 360 today invited the world to dance, hurdle, soar and make furry friends for life — all through the magic of Kinect — no controller required. “With ‘Kinectimals*’ and ‘Kinect Sports*’, ‘Your Shape™: Fitness Evolved*’ and ‘Dance Central™*’, your living room will become a zoo, a stadium, a fitness room or a dance club. You will be in the centre of your entertainment, using the best controller ever made — you,” said Kudo Tsunoda, creative director for Microsoft Game Studios. Microsoft and LucasArts also announced that they will bring Star Wars® to Kinect in 2011. And, sprinkling a little fairy dust on Xbox 360, Disney will bring its magic as well. “Xbox LIVE is about making it simple to find the entertainment you want, with the friends you care about, wherever you are. -

Kinect™ Sports** Caution: Gaming Experience May Soccer, Bowling, Boxing, Beach Volleyball, Change Online Table Tennis, and Track and Field
General KEY GESTURES Your body is the controller! When you’re not using voice control to glide through Kinect Sports: Season Two’s selection GAME MODES screens, make use of these two key navigational gestures. Select a Sport lets you single out a specific sport to play, either alone or HOLD TO SELECT SWIPE with friends (in the same room or over Xbox LIVE). Separate activities To make a selection, stretch To move through multiple based on the sports can also be found here. your arm out and direct pages of a selection screen the on-screen pointer with (when arrows appear to the Quick Play gets you straight into your hand, hovering over a right or left), swipe your arm the competitive sporting action. labelled area of the screen across your body. Split into two teams and nominate until it fills up. players for head-to-head battles while the game tracks your victories. Take on computer GAME MENUS opponents if you’re playing alone. To bring up the Pause menu, hold your left arm out diagonally at around 45° from your body until the Kinect Warranty For Your Copy of Xbox Game Software (“Game”) Acquired in Australia or Guide icon appears. Be sure to face the sensor straight New Zealand on with your legs together and your right arm at your IF YOU ACQUIRED YOUR GAME IN AUSTRALIA OR NEW ZEALAND, THE FOLLOWING side. From this menu you can quit, restart, or access WARRANTY APPLIES TO YOU IN ADDITION the Kinect Tuner if you experience any problems with TO ANY STATUTORY WARRANTIES: Consumer Rights the sensor (or press on an Xbox 360 controller if You may have the benefi t of certain rights or remedies against Microsoft Corpor necessary). -

Volume 1: Setup Volume 1: Installation Volumen 1
Register your Xbox 360 console online today. It only takes a few minutes to join the Xbox community and gain access to exclusive information, rewards and offers. Go to www.xbox.com/registermyxbox Inscrivez votre Console Xbox 360 en ligne dès aujourd'hui Quelques minutes suffisent pour vous joindre à la communauté Xbox et accéder à des informa- tions, récompenses et offres exclusives. Visitez la page www.xbox.com/registermyxbox Registra tu Consola Xbox 360 en línea hoy mismo En sólo unos minutos, únete a la comunidad Xbox y obtén acceso a información exclusiva, premios y ofertas. Visita www.xbox.com/registermyxbox VOLUME 1: SETUP VOLUME 1: INSTALLATION Printed in China VOLUMEN 1: CONFIGURACIÓN 0805 Part Number X11-42612-01 Xbox 360 English 2 Your Xbox 360 Video Game and WARNING Entertainment System Failure to properly set up, use, and care for the Xbox 360 video game system can 3 Select a Location for the increase the risk of serious injury or death, Xbox 360 Console or damage to the Xbox 360 video game 1 English system. Read this manual and the manuals 4 Set Up Your Xbox 360 Video of any peripherals for important safety and Game System health information. Keep all manuals for future reference. For replacement manuals, 6 Connect the Console to Power 25 Français go to www.xbox.com/support or call the Xbox Customer Support number provided on the back cover. 8 The Xbox 360 Wireless Controller Before allowing children to use the Xbox 8 Prepare the Wireless Controller 49 Español 360 video game system: for Use 1 Determine how each child can use the 10 Family Settings Xbox 360 console (playing games, connecting to Xbox Live, replacing 11 Using the Disc Drive batteries, making electrical, AV cable, and network connections) and whether 12 Important Health Warnings About english they should be supervised during these Playing Video Games activities. -

Game Console Failure Rates: Wii 9 Times More Reliable Than Xbox 360, 4 Times More Than PS3
Game Console Failure Rates: Wii 9 times more reliable than Xbox 360, 4 times more than PS3 Synopsis: SquareTrade analyzed failure rates for over 16,000 new game consoles covered by SquareTrade Care Plans and found that the Wii experienced one-fourth of the common failures that the other systems have. Highlights of the study include: - Looking at the first 2 years of ownership, 2.7% of Wii owners reported a system failure to SquareTrade, compared with 10.0% of PlayStation 3 owners, and 23.7% for Xbox 360 owners. - Excluding “Red Ring of Death” failures, which are covered by Microsoft’s 3-year warranty, 11.7% of Xbox 360 owners reported a failure. - While the RROD problem continued to be the major issue for Xbox 360s purchased through 2008, early indications point to the problem abating in 2009. - The most common types of problems seen with the PS3 and Xbox 360 were disc read errors and output issues. The Wii had more power and remote control issues than the other 2 systems. Citations and quotations of this paper’s contents require proper attribution to the source at http://www.squaretrade.com/pages/xbox360-ps3-wii-reliability-08-2009/. Commercial use of this paper’s contents are prohibited without prior written consent from SquareTrade, Inc. For media inquiries, write or call Shelley Risk at [email protected] or 415-905-4037. Prepared by: Austin Sands & Vince Tseng SquareTrade, Inc. www.squaretrade.com Aug. 28, 2009 © SquareTrade, Inc. | All Rights Reserved. | www.squaretrade.com 1 Introduction: Comparing the Wii, Xbox 360 and PS3 SquareTrade first examined and reported on failure rate data for the Microsoft Xbox 360 back in February 2008. -

Read the Case Study
CASE STUDY CASE STUDY: A GAME DESIGNED FOR A BROAD CONSUMER BASE, DEVELOPED IN A FRACTION OF THE TIME How Microsoft Game Studios combined “wild creativity” with discipline, structure and science to develop “Kinect Adventures” OBJECTIVE: Develop a pack-in game that would be enjoyed by a broad cross-section of consum- ers to demonstrate the wide appeal of the Kinect for Xbox 360 system—and do it in an extremely compressed timeframe. What if you could expand a product’s appeal beyond its narrow but very devoted fan base? It’s a question many companies ask themselves, particularly as innovation be- comes key to business growth, competitiveness and success. It’s a question Micro- soft Game Studios asked as well. Microsoft’s Xbox 360 video game platform was a hit with the typical gamer. By de- veloping Kinect for Xbox 360, the company aimed to take that success to a broader consumer market. The groundbreaking Kinect sensor, which launched in November- of 2010, allows users to interact with and control the Xbox 360 using ordinary hand gestures and spoken commands. No game controller or hardcore gamer dexterity required. But Microsoft realized that Kinect would also have to ship a game that equally appealed to a broad consumer audience to fully showcase the product’s reach. What would it take to create an innovative title to deliver on Kinect’s promise? Shannon Loftis, head of Good Science Studio within Microsoft Game Studios, led the team responsible for developing “Kinect Adventures,” the game that would ship with every Kinect sensor sold. -

Microsoft Studios
Live time ■ Microsoft Studio’s global live conference at E3 in Los Angeles is a key opportunity for it to reach its global gaming audience – looking for the latest on games for its Xbox, Xbox 360, Xbox One, Games for Windows, Steam, Windows Store and Windows Phone platforms – and it wanted to reach this audience with all the news ■ Redmond, Washington company needed a production partner that would ensure seamless video and Ethernet transmission to support critical live feeds from the conference to its global audience Always there ■ The Switch connected Microsoft Studios onto its global network by connecting diverse 10 Gbps fiber optic cables between Microsoft Studios’ headquarters in Redmond and The Switch’s local PoP ■ Transmission services allowed Microsoft to send and receive video programming from the conference in a variety of video formats, including 4K, 3G, HD, ASI, J2K as well as selectable bandwidths of Ethernet and DIA ■ Through the use of The Switch’s fiber trailers, ensured permanent connectivity for both on-site and off-site locations Always on Microsoft Studios ■ Result was ES 2019 conference syndicated to the broadcast media at the highest quality available The Switch hits global gaming audience for Xbox ■ Capability to deliver coverage of event to a pool of broadcasters ready to and other MS platforms by hooking them into E3 “pull” the feed (via The Switch network) or encode for non-linear distribution conference news to OTT or social media ■ Through The Switch, Microsoft Studios delivered faultless coverage to developers and the Microsoft community across the world, announcing a staggering 50 games – including 18 Xbox exclusives and 15 world premieres theswitch.tv. -

EXPLORE YOUR XBOX 360® Setup & Warranty
EXPLORE YOUR XBOX 360® SETUP & WARRANTY REGISTER your Xbox 360® ONLINE TODAY It only takes a few minutes to join the Xbox® community and gain access to exclusive information, rewards, and offers. Go to www.xbox.com/registermyxbox. ENGLISH WARNING Failure to properly set up, use, and care for the Xbox 360 1) YOUR XBOX 360 VIDEO GAME AND video game and entertainment system can increase the risk of serious injury or death, or damage to the Xbox 360 video ENTERTAINMENT SYSTEM game and entertainment system. Read this manual and the manuals of any accessories for important safety and health information. Keep all manuals for future reference. For 2) POSITION YOUR XBOX replacement manuals, go to www.xbox.com/support. 3) CONNECT TO YOUR TV Before allowing children to use the Xbox 360 video game and entertainment system: 1 Determine how each child can use the Xbox 360 console 3) CONNECT TO POWER (playing games, connecting to Xbox LIVE, replacing batteries, making electrical, AV cable, and network SET UP YOUR CONTROLLER connections) and whether they should be supervised 4) during these activities. 2 If you allow children to use the Xbox 360 console without 6) SET UP YOUR HEADSET supervision, be sure to explain all relevant safety and health information and instructions. PLAY DISCS The Xbox 360 console will not play copied or “pirated” 6) games or other unauthorized media. Attempting to defeat the Xbox 360 anti-piracy protection system may cause your 7) CHOOSE YOUR FAMILY’S eXPERIENCE Xbox 360 console to stop working permanently. It will also void your Limited Warranty, and may make your Xbox 360 console ineligible for authorized repair, even for a fee. -

Microsoft Xbox 1. Turn on Your Xbox Console with No Game Disc in The
Microsoft XBox 1. Turn on your Xbox console with no game disc in the disc tray. 2. From the Xbox Dashboard, choose Xbox Live. These steps assume you cannot connect to Xbox Live until you finish configuring your Xbox console to use your PC's MAC address. Therefore, you should receive the following message: "Could not connect to Xbox Live. Do you want to troubleshoot your network connection?". 3. From the Connect Status screen, select Settings. 4. The 12-digit number at the bottom-right corner of the Network Settings screens is the MAC address of your Xbox console. Do not change your Xbox console MAC address, just write it down so that you can use it later. Microsoft Xbox 360 1. Go to the System area of the Xbox Dashboard and select Network Settings. 2. Select Edit Settings. 3. Under Basic Settings, check to make sure the IP Settings is on Automatic. 4. Now go to Additional Settings, select Advanced Settings. 5. At the bottom of this screen you'll see a heading called Wired MAC Address. Sony PS2 1. Load the Start-up CD in your PS2. 2. Make sure you have the network cable disconnected. 3. Walk through the Start-Up CD until it starts testing your connection. Since we disconnected the network cable the test will fail. 4. You can now press the select button which will display the MAC. 5. The 12-digit number is the MAC address of your PS2, write it down so that you can use it later. Sony PS 3 1.