Z39.50 Implementation Experiences
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Könyvtárüggyel Kapcsolatos Nemzetközi Szabványok
A könyvtárüggyel kapcsolatos nemzetközi szabványok 1. Állomány-nyilvántartás ISO 20775:2009 Information and documentation. Schema for holdings information 2. Bibliográfiai feldolgozás és adatcsere, transzliteráció ISO 10754:1996 Information and documentation. Extension of the Cyrillic alphabet coded character set for non-Slavic languages for bibliographic information interchange ISO 11940:1998 Information and documentation. Transliteration of Thai ISO 11940-2:2007 Information and documentation. Transliteration of Thai characters into Latin characters. Part 2: Simplified transcription of Thai language ISO 15919:2001 Information and documentation. Transliteration of Devanagari and related Indic scripts into Latin characters ISO 15924:2004 Information and documentation. Codes for the representation of names of scripts ISO 21127:2014 Information and documentation. A reference ontology for the interchange of cultural heritage information ISO 233:1984 Documentation. Transliteration of Arabic characters into Latin characters ISO 233-2:1993 Information and documentation. Transliteration of Arabic characters into Latin characters. Part 2: Arabic language. Simplified transliteration ISO 233-3:1999 Information and documentation. Transliteration of Arabic characters into Latin characters. Part 3: Persian language. Simplified transliteration ISO 25577:2013 Information and documentation. MarcXchange ISO 259:1984 Documentation. Transliteration of Hebrew characters into Latin characters ISO 259-2:1994 Information and documentation. Transliteration of Hebrew characters into Latin characters. Part 2. Simplified transliteration ISO 3602:1989 Documentation. Romanization of Japanese (kana script) ISO 5963:1985 Documentation. Methods for examining documents, determining their subjects, and selecting indexing terms ISO 639-2:1998 Codes for the representation of names of languages. Part 2. Alpha-3 code ISO 6630:1986 Documentation. Bibliographic control characters ISO 7098:1991 Information and documentation. -

Online Development in the Nordic Countries
Online development in the Nordic countries A history of online information from the 1960s to the ‘00s and NORDINFO’s role in its development Elisabet Mickos (†), Teodora Oker-Blom, Marie Wallin, Lars Klasén, Aud Lamvik and Ulla Retlev (Eds.) Helsinki 2018 Online development in the Nordic countries A history of online information from the 1960s to the ‘00s and NORDINFO’s role in its development Elisabet Mickos (†), Teodora Oker-Blom, Marie Wallin, Lars Klasén, Aud Lamvik and Ulla Retlev (Eds.) i Online development in the Nordic countries © The editors Published 2018 by the editors Teodora Oker-Blom (Finland), Marie Wallin (Sweden), Lars Klasén (Sweden), Aud Lamvik (Norway) and Ulla Retlev (Denmark) Graphic design by Lars Klasén (Sweden) The publishing process began as a project within NORDINFO - the Nordic Council for Scientific Information. NORDINFO was closed down in 2004 and the editors had to take the responsibility of completing the project by publishing this book. Some of the contributions to this book have previously been published as manuscripts in 2007. See: URI http://hdl.handle.net/1975/1490 ISBN 978-952-94-0548-0 (PDF) URI http://hdl.handle.net/10138/235272 Licencees may copy, distribute, display, and perform only verbatim copies of the work, not derivative works and remixes based on it. The book is published under a Creative Commons Attribution Non-derivative licence (CC BY-ND 4.0). ii Online development in the Nordic countries Contents Foreword, acknowledgements Marie Wallin & Teodora Oker-Blom ...................................... v Acronyms, abbreviations and technical terms ......................................................................... viii 1 INTRODUCTION. ONLINE SERVICES - PAST AND PRESENT IN A NORDIC AND INTERNATIONAL PERSPECTIVE Sauli Laitinen ........................................... -

ANSI/NISO Z39.50-2003 Information Retrieval Application Service Definition and Protocol Specification
ANSI/NISO Z39.50-2003 ISSN: 1041-5653 (revision of Z39.50-1995) Information Retrieval (Z39.50): Application Service Definition and Protocol Specification Abstract: This standard defines a client/server based service and protocol for Information Retrieval. It specifies procedures and formats for a client to search a database provided by a server, retrieve database records, and perform related information retrieval functions. The protocol addresses communication between information retrieval applications at the client and server; it does not address interaction between the client and the end-user. An American National Standard Developed by the National Information Standards Organization Approved November 27, 2002 by the American National Standards Institute Published by the National Information Standards Organization Bethesda, Maryland NISO Press, Bethesda, Maryland, U.S.A. ©NISO Published by NISO Press 4733 Bethesda Avenue, Suite 300 Bethesda, MD 20814 www.niso.org Copyright ©2003 by the National Information Standards Organization All rights reserved under International and Pan-American Copyright Conventions. No part of this book may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopy, recording, or any information storage or retrieval system, without prior permission in writing from the publisher. All inquiries should be addressed to NISO Press, 4733 Bethesda Avenue, Suite 300, Bethesda, MD 20814. Printed in the United States of America ISSN: 1041-5653 National Information Standard Series ISBN: 1-880124-55-6 ¥ This paper meets the requirements of ANSI/NISO Z39.48-1992 Permanence of Paper. Library of Congress Cataloging-in-Publication Data National Information Standards Organization (U.S.) Information retrieval (Z39.50) : application service definition and protocol specification : an American national standard / developed by the National Information Standards Organization. -

Renardus D1.1
Citation for published version: Day, M, Ardö, A, Dovey, MJ, Hamilton, M, Heikkinen, R, Powell, A & Olsen, AN 2000, Evaluation report of existing broker models in related projects. Renardus Project. Publication date: 2000 Document Version Early version, also known as pre-print Link to publication University of Bath Alternative formats If you require this document in an alternative format, please contact: [email protected] General rights Copyright and moral rights for the publications made accessible in the public portal are retained by the authors and/or other copyright owners and it is a condition of accessing publications that users recognise and abide by the legal requirements associated with these rights. Take down policy If you believe that this document breaches copyright please contact us providing details, and we will remove access to the work immediately and investigate your claim. Download date: 05. Oct. 2021 Deliverable: D1.1 Evaluation report of existing broker models Issue: 1.0 Date of issue: 27 April 2000 RENARDUS: PROJECT DELIVERABLE Project Number: IST-1999-10562 Project Title: Reynard - Academic Subject Gateway Service Europe Deliverable Type: Public Deliverable Number: D1.1 Contractual Date of Delivery: 31 March 2000 Actual Date of Delivery: 27 April 2000 Title of Deliverable: Evaluation report of existing broker models in related projects Workpackage contributing to the Deliverable: WP1 Nature of the Deliverable: Report URL: http://www.renardus.org/deliverables/ Authors: Michael Day, Anders Ardö, Matthew J. Dovey, Martin Hamilton, Risto Heikkinen, Andy Powell and Arthur N. Olsen. Contact Details: Michael Day, UKOLN: the UK Office for Library and Information Networking, University of Bath, Bath BA2 7AY, UK. -

A Könyvtárüggyel Kapcsolatos Nemzetközi Szabványok
A könyvtárüggyel kapcsolatos nemzetközi szabványok 1. Állomány-nyilvántartás ISO 20775:2009 Information and documentation. Schema for holdings information 2. Bibliográfiai feldolgozás és adatcsere, transzliteráció ISO 10754:1996 Information and documentation. Extension of the Cyrillic alphabet coded character set for non-Slavic languages for bibliographic information interchange ISO 11940:1998 Information and documentation. Transliteration of Thai ISO 11940-2:2007 Information and documentation. Transliteration of Thai characters into Latin characters. Part 2: Simplified transcription of Thai language ISO 15919:2001 Information and documentation. Transliteration of Devanagari and related Indic scripts into Latin characters ISO 15924:2004 Information and documentation. Codes for the representation of names of scripts ISO 21127:2014 Information and documentation. A reference ontology for the interchange of cultural heritage information ISO 233:1984 Documentation. Transliteration of Arabic characters into Latin characters ISO 233-2:1993 Information and documentation. Transliteration of Arabic characters into Latin characters. Part 2: Arabic language. Simplified transliteration ISO 233-3:1999 Information and documentation. Transliteration of Arabic characters into Latin characters. Part 3: Persian language. Simplified transliteration ISO 25577:2013 Information and documentation. MarcXchange ISO 259:1984 Documentation. Transliteration of Hebrew characters into Latin characters ISO 259-2:1994 Information and documentation. Transliteration of Hebrew characters into Latin characters. Part 2. Simplified transliteration ISO 3602:1989 Documentation. Romanization of Japanese (kana script) ISO 5963:1985 Documentation. Methods for examining documents, determining their subjects, and selecting indexing terms ISO 639-2:1998 Codes for the representation of names of languages. Part 2. Alpha-3 code ISO 6630:1986 Documentation. Bibliographic control characters ISO 7098:1991 Information and documentation. -

All SABS Standards Page 1
All SABS Standards January 2020 SANS Number Edition Title SANS 1-2:2013 2 Standard for standards Part 2: Recognition of Standards Development Organizations (SDOs) in South Africa SATS 2:2012 1 The development of normative documents other than South African National Standards SANS 2:2013 7.01 Lead-acid starter batteries (SABS 2) SANS 4:2008 3.03 Locks, latches, and associated furniture for doors (SABS 4) (Domestic Type) SANS 11:2007 1.02 Unplasticized poly(vinyl chloride) (PVC-U) (SABS 11) components for external rainwater systems SANS 13:2008 2.03 Wax polish, solvent-based, for floors and furniture (SABS 13) SANS 14:1994/ISO 49:1994, IDT, Ed. 2 1 Malleable cast iron fittings threaded to ISO 7-1 (SABS ISO 49) SANS 15:2008 2.03 Wax emulsion polish for floors and furniture (SABS 15) SANS 16:2007/ISO/IEC 10116:2006, IDT, Ed. 3 2 Information technology - Security techniques - Modes of operation for an n-bit block cipher SANS 17:2014 1.01 Glass and plastics in furniture SANS 18-1:2003/ISO/IEC 10118-1:2000, IDT, Ed. 2 1 Information technology - Security techniques - Hash- functions Part 1: General SANS 18-2:2011/ISO/IEC 10118-2:2010, IDT, Ed. 3 2 Information technology - Security techniques - Hash- functions Part 2: Hash-functions using an n-bit block cipher SANS 18-3:2007/ISO/IEC 10118-3:2004, IDT, Ed. 3 2 Information technology - Security techniques - Hash- functions Part 3: Dedicated hash-functions SANS 18-4:2003/ISO/IEC 10118-4:1998, IDT, Ed. 1 1 Information technology - Security techniques - Hash- functions Part 4: Hash-functions using modular arithmetic SANS 19:2018 2 The inspection, testing and examination of mobile cranes SANS 20:2008 2.01 Primary zinc (SABS 20) SANS 21-1:2009/EN 115-1:2008, IDT, Ed. -

Isqv27no1.Pdf
INFORMATION STANDARDS QUARTERLY SPRING 2015 | VOL 27 | ISSUE 1 | ISSN 1041-0031 TOPIC YEAR IN REVIEW AND STATE OF THE STANDARDS NISO 2014 YEAR IN REVIEW TC46 2014 YEAR IN REVIEW THE FUTURE OF LIBRARY RESOURCE DISCOVERY STATE OF THE STANDARDS NEW for 2015: NISO Training Thursdays A technical webinar for those wanting more in-depth knowledge. Free with registration to the related Virtual Conference or register separately. UPCOMING 2015 EDUCATIONAL EVENTS APRIL JUNE OCTOBER 8 Experimenting with BIBFRAME: 10 Taking Your Website Wherever 1 Using Alerting Systems to Reports from Early Adopters You Go: Delivering Great User Ensure OA Policy Compliance (Webinar) Experience to Multiple Devices (Training Thursday) 29 Expanding the Assessment (Webinar) 14 Cloud and Web Services for Toolbox: Blending the Old 17 The Eternal To-Do List: Making Libraries (Webinar) and New Assessment Practices E-books Work in Libraries 28 Interacting with Content: (Virtual Conference) (Virtual Conference) Improving the User Experience 26 NISO/BISG The Changing (Virtual Conference) MAY Standards Landscape (In-person Forum) 7 Implementing SUSHI/ NOVEMBER COUNTER at Your Institution JULY 18 Text Mining: Digging Deep for (Training Thursday) Knowledge (Webinar) 13 Software Preservation and Use: No events in July I Saved the Files But Can I Run DECEMBER Them? (Webinar) AUGUST 2 The Semantic Web: What’s New 20 Not Business as Usual: 12 MOOCs and Libraries: and Cool (Virtual Conference) Special Cases in RDA Serials A Brewing Collaboration NISO December Two-Part Webinar: Cataloging (NISO/NASIG (Webinar) Joint Webinar) Emerging Resource Types SEPTEMBER 9 Part 1: Emerging Resource Types NISO September Two-Part Webinar: 16 Part 2: Emerging The Practicality of Managing “E” NISO Open Teleconferences Resource Types 9 Part 1: Licensing Join us each month for NISO’s Open 16 Part 2: Staffing Teleconferences—an ongoing series of calls held on the second Monday 23 Scholarly Communication of each month as a way to keep Models: Evolution the community informed of NISO’s or Revolution? activities. -
2021-07-07 Report Date : Cost Centre(S)
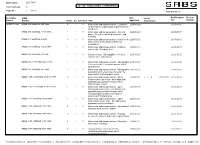
Report Date : 2021-09-17 Cost Centre(s) : % LIST OF PUBLISHED STANDARDS Page No : 1 Of 5 Total Count: 67 Committee SANS Date Latest Reaffirmation Review/ Number Number Int Ed Ed Sansified Title Approved Amendment due Revision SABS/TC 046 SANS 438:2005/ISO 999:1996 2 1 Y Information and documentation - Guidelines 2005-10-28 2015-08-27 for the content, organization and presentation of indexes SANS 480:2006/ISO 11108:1996 1 1 Y Information and documentation - Archival 2006-03-24 2025-07-17 paper - Requirements for permanence and durability SANS 531:2007/ISO 4:1997 3 1 Y Information and documentation - Rules for the 2007-05-25 2017-03-16 abbreviation of title words and titles of publications SANS 618:2009/ISO 10324:1997 1 1 Y Information and documentation - Holdings 2009-03-13 2014-03-13 statements - Summary level SANS 690:2007/ISO 690:1987 2 1 Y Documentation - Bibliographic references - 2007-05-25 2012-05-25 Content, form and structure SANS 690-2:2007/ISO 690-2:1997 1 1 Y Information and documentation - Bibliographic 2007-05-25 2012-05-25 references Part 2: Electronic documents or parts thereof SANS 832:2007/ISO 832:1994 2 1 Y Information and documentation - Bibliographic 2007-05-25 2018-01-25 description and references - Rules for the abbreviation of bibliographic terms SANS 1105-1:2010/ISO 10161-1:1997 2 1 Y Information and documentation - Open 2010-10-01 2 I A 2010-10-01 2015-10-01 Systems Interconnection - Interlibrary loan application protocol specification Part 1: Protocol specification SANS 1105-2:2011/ISO 10161-2:1997 1 1 Y Information -

Standards for Enabling Trade— Mapping and Gap Analysis Study
Standards for Enabling Trade— Mapping and Gap Analysis Study An IA-CEPA Early Outcomes Initiative November 2017 Standards For Enabling Trade—Mapping and Gap Analysis Study 2 An IA-CEPA Early Outcomes Initiative – November 2017 Contents ListofFigures..............................................................................................................3 Abbreviations...............................................................................................................4 Terms..........................................................................................................................6 Acknowledgements......................................................................................................8 ExplanatoryNotes........................................................................................................8 Foreword.....................................................................................................................9 Recommendations.....................................................................................................10 ExecutiveSummary....................................................................................................11 Introduction................................................................................................................13 ProjectPurpose.........................................................................................................13 Objectives..................................................................................................................13 -

NISO Circulation Interchange Part 1: Protocol (NCIP)
ANSI/NISO Z39.83-1-2008 ISSN: 1041-5653 NISO Circulation Interchange Part 1: Protocol (NCIP) Abstract: This Standard defines a protocol that is limited to the exchange of messages between and among computer-based applications to enable them to perform the functions necessary to lend and borrow items, to provide controlled access to electronic resources, and to facilitate co-operative management of these functions. An American National Standard Developed by the National Information Standards Organization Approved November 11, 2008 by the American National Standards Institute Published by: NISO, Baltimore, Maryland, U.S.A. About NISO Standards NISO standards are developed by Working Groups of the National Information Standards Organization. The development process is a strenuous one that includes a rigorous peer review of proposed standards open to each NISO Voting Member and any other interested party. Final approval of the standard involves verification by the American National Standards Institute that its requirements for due process, consensus, and other approval criteria have been met by NISO. Once verified and approved, NISO Standards also become American National Standards. This standard may be revised or withdrawn at any time. For current information on the status of this standard contact the NISO office or visit the NISO website at: http://www.niso.org Published by NISO One North Charles Street Suite 1905 Baltimore, MD 21201 www.niso.org Copyright © 2008 by the National Information Standards Organization All rights reserved under International and Pan-American Copyright Conventions. For noncommercial purposes only, this publication may be reproduced or transmitted in any form or by any means without prior permission in writing from the publisher, provided it is reproduced accurately, the source of the material is identified, and the NISO copyright status is acknowledged. -

Patents and Open Standards
Patents and Open Standards By Priscilla Caplan A white paper prepared for the National Information Standards Organization. Originally published in Information Standards Quarterly, vol. 14, no. 4, October 2003. Published by the National Information Standards Organization Bethesda, Maryland Patents and Open Standards Published by NISO Press Copyright © 2003 by the National Information Standards Organization. All rights reserved under International and Pan-American Copyright Conventions. For noncommercial purposes only, this publication may be reproduced or transmitted in any form or by any means without prior permission in writing from the publisher. All inquiries regarding commercial reproduction or distribution should be addressed to: NISO Press 4733 Bethesda Avenue, Suite 300 Bethesda, MD 208114 Telephone: 301-654-2512 Email: [email protected] About NISO White Papers NISO White Papers are contributed or solicited papers that address an issue that has implications for standards development. White Papers can be viewed as a pre- standardization activity. A NISO White Paper might define or explore some of the questions that come into play in the development of consensus standards. Or, a NISO White Paper might identify areas that are opportunities for standards development and suggest possible approaches. All White Papers are posted on the NISO website (www.niso.org). Suggestions for topics to be addressed in the White Paper series or unsolicited manuscripts should be sent to [email protected]. NISO White Papers now available: • The Exchange of Serials Subscription Information by Ed Jones • Issues in Crosswalking Content Metadata Standards by Margaret St. Pierre and William P. LaPlant, Jr. • The Myth of Free Standards: Giving Away the Farm by Andrew N. -

Prestito Ill Per Sbn
AKROS INFORMATICA S.R.L. PRESTITO ILL PER SBN Specifiche Funzionali per la realizzazione di un sistema di Prestito Interbibliotecario per il Servizio Bibliotecario Nazionale. SVILUPPO PER: Istituto Centrale per il Catalogo Unico PPrrreeessstttiiitttooo IIILLLL PPeeerrr SSBBNN –– SSppeeeccciiifffiiiccchheee FFuunnzziiiooonnaallliii Akros Informatica s.r.l. Via S.Cavina, 7 47100 Ravenna. © 1999, Akros Informatica s.r.l. REVISIONE: 4 del 31 marzo 2000 REDATTO DA VERIFICA E APPROVAZIONE VERIFICA E APPROVAZIONE RESPONSABILE PROGETTO RESPONSABILE PROGETTO FORNITORE COMMITTENTE Daniela Saccomandi Danila Silvagni Claudia Parmeggiani MOTIVO REVISIONE: Aggiornamento Architettura ed analisi compreso le specifiche dell’ambiente di prova. Versione Corrente La versione corrente di questo documento è reperibile, nei seguenti formati, presso il sito aziendale interno: MS-Word '97: http://javasrv.akros.it/PrestitoILL/Analisi/Prestito ILL – Specifichev4.doc Acrobat v3.0: http://javasrv.akros.it/PrestitoILL/Analisi/Prestito ILL – Specifichev4.pdf Versioni Precedenti Le versioni precedenti verranno mantenuti in formato Adobe Acrobat (per sola lettura ): Acrobat v3.0: http://javasrv.akros.it/PrestitoILL/Analisi/Prestito ILL – Specifichev3.pdf Acrobat v3.0: http://javasrv.akros.it/PrestitoILL/Analisi/Prestito ILL – Specifichev2.pdf Acrobat v3.0: http://javasrv.akros.it/PrestitoILL/Analisi/Prestito ILL – Specifichev1.pdf Akros Informatica s.r.l. i Revisione 3 del 10 giugno 1999 PPrrreeessstttiiitttooo IIILLLL PPeeerrr SSBBNN –– SSppeeeccciiifffiiiccchheee FFuunnzziiiooonnaallliii