Graphs: Structures and Algorithms Vocabulary
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
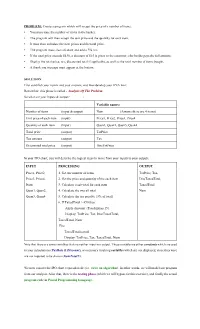
Create a Program Which Will Accept the Price of a Number of Items. • You Must State the Number of Items in the Basket
PROBLEM: Create a program which will accept the price of a number of items. • You must state the number of items in the basket. • The program will then accept the unit price and the quantity for each item. • It must then calculate the item prices and the total price. • The program must also calculate and add a 5% tax. • If the total price exceeds $450, a discount of $15 is given to the customer; else he/she pays the full amount. • Display the total price, tax, discounted total if applicable, as well as the total number of items bought. • A thank you message must appear at the bottom. SOLUTION First establish your inputs and your outputs, and then develop your IPO chart. Remember: this phase is called - Analysis Of The Problem. So what are your inputs & output? : Variable names: Number of items (input & output) Num (Assume there are 4 items) Unit price of each item (input) Price1, Price2, Price3, Price4 Quantity of each item (Input) Quan1, Quan2, Quan3, Quan4 Total price (output) TotPrice Tax amount (output) Tax Discounted total price (output) DiscTotPrice In your IPO chart, you will describe the logical steps to move from your inputs to your outputs. INPUT PROCESSING OUTPUT Price1, Price2, 1. Get the number of items TotPrice, Tax, Price3, Price4, 2. Get the price and quantity of the each item DiscTaxedTotal, Num 3. Calculate a sub-total for each item TaxedTotal Quan1, Quan2, 4. Calculate the overall total Num Quan3, Quan4 5. Calculate the tax payable {5% of total} 6. If TaxedTotal > 450 then Apply discount {Total minus 15} Display: TotPrice, Tax, DiscTaxedTotal, TaxedTotal, Num Else TaxedTotal is paid Display: TotPrice, Tax, TaxedTotal, Num Note that there are some variables that are neither input nor output. -

Packing and Covering Dense Graphs
Packing and Covering Dense Graphs Noga Alon ∗ Yair Caro y Raphael Yuster z Abstract Let d be a positive integer. A graph G is called d-divisible if d divides the degree of each vertex of G. G is called nowhere d-divisible if no degree of a vertex of G is divisible by d. For a graph H, gcd(H) denotes the greatest common divisor of the degrees of the vertices of H. The H-packing number of G is the maximum number of pairwise edge disjoint copies of H in G. The H-covering number of G is the minimum number of copies of H in G whose union covers all edges of G. Our main result is the following: For every fixed graph H with gcd(H) = d, there exist positive constants (H) and N(H) such that if G is a graph with at least N(H) vertices and has minimum degree at least (1 − (H)) G , then the H-packing number of G and the H-covering number of G can be computed j j in polynomial time. Furthermore, if G is either d-divisible or nowhere d-divisible, then there is a closed formula for the H-packing number of G, and the H-covering number of G. Further extensions and solutions to related problems are also given. 1 Introduction All graphs considered here are finite, undirected and simple, unless otherwise noted. For the standard graph-theoretic terminology the reader is referred to [1]. Let H be a graph without isolated vertices. An H-covering of a graph G is a set L = G1;:::;Gs of subgraphs of G, where f g each subgraph is isomorphic to H, and every edge of G appears in at least one member of L. -

Embedding Trees in Dense Graphs
Embedding trees in dense graphs Václav Rozhoň February 14, 2019 joint work with T. Klimo¹ová and D. Piguet Václav Rozhoň Embedding trees in dense graphs February 14, 2019 1 / 11 Alternative definition: substructures in graphs Extremal graph theory Definition (Extremal graph theory, Bollobás 1976) Extremal graph theory, in its strictest sense, is a branch of graph theory developed and loved by Hungarians. Václav Rozhoň Embedding trees in dense graphs February 14, 2019 2 / 11 Extremal graph theory Definition (Extremal graph theory, Bollobás 1976) Extremal graph theory, in its strictest sense, is a branch of graph theory developed and loved by Hungarians. Alternative definition: substructures in graphs Václav Rozhoň Embedding trees in dense graphs February 14, 2019 2 / 11 Density of edges vs. density of triangles (Razborov 2008) (image from the book of Lovász) Extremal graph theory Theorem (Mantel 1907) Graph G has n vertices. If G has more than n2=4 edges then it contains a triangle. Generalisations? Václav Rozhoň Embedding trees in dense graphs February 14, 2019 3 / 11 Extremal graph theory Theorem (Mantel 1907) Graph G has n vertices. If G has more than n2=4 edges then it contains a triangle. Generalisations? Density of edges vs. density of triangles (Razborov 2008) (image from the book of Lovász) Václav Rozhoň Embedding trees in dense graphs February 14, 2019 3 / 11 3=2 The answer for C4 is of order n , lower bound via finite projective planes. What is the answer for trees? Extremal graph theory Theorem (Mantel 1907) Graph G has n vertices. If G has more than n2=4 edges then it contains a triangle. -

Fractional Arboricity, Strength, and Principal Partitions in Graphs and Matroids
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Elsevier - Publisher Connector Discrete Applied Mathematics 40 (1992) 285-302 285 North-Holland Fractional arboricity, strength, and principal partitions in graphs and matroids Paul A. Catlin Wayne State University, Detroit, MI 48202. USA Jerrold W. Grossman Oakland University, Rochester, MI 48309, USA Arthur M. Hobbs* Texas A & M University, College Station, TX 77843, USA Hong-Jian Lai** West Virginia University, Morgantown, WV 26506, USA Received 15 February 1989 Revised 15 November 1989 Abstract Catlin, P.A., J.W. Grossman, A.M. Hobbs and H.-J. Lai, Fractional arboricity, strength, and principal partitions in graphs and matroids, Discrete Applied Mathematics 40 (1992) 285-302. In a 1983 paper, D. Gusfield introduced a function which is called (following W.H. Cunningham, 1985) the strength of a graph or matroid. In terms of a graph G with edge set E(G) and at least one link, this is the function v(G) = mmFr9c) IFl/(w(G F) - w(G)), where the minimum is taken over all subsets F of E(G) such that w(G F), the number of components of G - F, is at least w(G) + 1. In a 1986 paper, C. Payan introduced thefractional arboricity of a graph or matroid. In terms of a graph G with edge set E(G) and at least one link this function is y(G) = maxHrC lE(H)I/(l V(H)1 -w(H)), where H runs over Correspondence to: Professor A.M. Hobbs, Department of Mathematics, Texas A & M University, College Station, TX 77843, USA. -

Limits of Graph Sequences
Snapshots of modern mathematics № 10/2019 from Oberwolfach Limits of graph sequences Tereza Klimošová Graphs are simple mathematical structures used to model a wide variety of real-life objects. With the rise of computers, the size of the graphs used for these models has grown enormously. The need to ef- ficiently represent and study properties of extremely large graphs led to the development of the theory of graph limits. 1 Graphs A graph is one of the simplest mathematical structures. It consists of a set of vertices (which we depict as points) and edges between the pairs of vertices (depicted as line segments); several examples are shown in Figure 1. Many real-life settings can be modeled using graphs: for example, social and computer networks, road and other transport network maps, and the structure of molecules (see Figure 2a and 2b). These models are widely used in computer science, for instance for route planning algorithms or by Google’s PageRank algorithm, which generates search results. What these models all have in common is the representation of a set of several objects (the vertices) and relations or connections between pairs of those objects (the edges). In recent years, with the increasing use of computers in all areas of life, it has become necessary to handle large volumes of data. To represent such data (for example, connections between internet servers) in turn requires graphs with very many vertices and an even larger number of edges. In such situations, traditional algorithms for processing graphs are often impractical, or even impossible, because the computations take too much time and/or computational 1 Figure 1: Examples of graphs. -

Constructing Algorithms and Pseudocoding This Document Was Originally Developed by Professor John P
Constructing Algorithms and Pseudocoding This document was originally developed by Professor John P. Russo Purpose: # Describe the method for constructing algorithms. # Describe an informal language for writing PSEUDOCODE. # Provide you with sample algorithms. Constructing Algorithms 1) Understand the problem A common mistake is to start writing an algorithm before the problem to be solved is fully understood. Among other things, understanding the problem involves knowing the answers to the following questions. a) What is the input list, i.e. what information will be required by the algorithm? b) What is the desired output or result? c) What are the initial conditions? 2) Devise a Plan The first step in devising a plan is to solve the problem yourself. Arm yourself with paper and pencil and try to determine precisely what steps are used when you solve the problem "by hand". Force yourself to perform the task slowly and methodically -- think about <<what>> you are doing. Do not use your own memory -- introduce variables when you need to remember information used by the algorithm. Using the information gleaned from solving the problem by hand, devise an explicit step-by-step method of solving the problem. These steps can be written down in an informal outline form -- it is not necessary at this point to use pseudo-code. 3) Refine the Plan and Translate into Pseudo-Code The plan devised in step 2) needs to be translated into pseudo-code. This refinement may be trivial or it may take several "passes". 4) Test the Design Using appropriate test data, test the algorithm by going through it step by step. -

The $ K $-Strong Induced Arboricity of a Graph
The k-strong induced arboricity of a graph Maria Axenovich, Daniel Gon¸calves, Jonathan Rollin, Torsten Ueckerdt June 1, 2017 Abstract The induced arboricity of a graph G is the smallest number of induced forests covering the edges of G. This is a well-defined parameter bounded from above by the number of edges of G when each forest in a cover consists of exactly one edge. Not all edges of a graph necessarily belong to induced forests with larger components. For k > 1, we call an edge k-valid if it is contained in an induced tree on k edges. The k-strong induced arboricity of G, denoted by fk(G), is the smallest number of induced forests with components of sizes at least k that cover all k-valid edges in G. This parameter is highly non-monotone. However, we prove that for any proper minor-closed graph class C, and more gener- ally for any class of bounded expansion, and any k > 1, the maximum value of fk(G) for G 2 C is bounded from above by a constant depending only on C and k. This implies that the adjacent closed vertex-distinguishing number of graphs from a class of bounded expansion is bounded by a constant depending only on the class. We further t+1 d prove that f2(G) 6 3 3 for any graph G of tree-width t and that fk(G) 6 (2k) for any graph of tree-depth d. In addition, we prove that f2(G) 6 310 when G is planar. -

Sparse Exchangeable Graphs and Their Limits Via Graphon Processes
Journal of Machine Learning Research 18 (2018) 1{71 Submitted 8/16; Revised 6/17; Published 5/18 Sparse Exchangeable Graphs and Their Limits via Graphon Processes Christian Borgs [email protected] Microsoft Research One Memorial Drive Cambridge, MA 02142, USA Jennifer T. Chayes [email protected] Microsoft Research One Memorial Drive Cambridge, MA 02142, USA Henry Cohn [email protected] Microsoft Research One Memorial Drive Cambridge, MA 02142, USA Nina Holden [email protected] Department of Mathematics Massachusetts Institute of Technology Cambridge, MA 02139, USA Editor: Edoardo M. Airoldi Abstract In a recent paper, Caron and Fox suggest a probabilistic model for sparse graphs which are exchangeable when associating each vertex with a time parameter in R+. Here we show that by generalizing the classical definition of graphons as functions over probability spaces to functions over σ-finite measure spaces, we can model a large family of exchangeable graphs, including the Caron-Fox graphs and the traditional exchangeable dense graphs as special cases. Explicitly, modelling the underlying space of features by a σ-finite measure space (S; S; µ) and the connection probabilities by an integrable function W : S × S ! [0; 1], we construct a random family (Gt)t≥0 of growing graphs such that the vertices of Gt are given by a Poisson point process on S with intensity tµ, with two points x; y of the point process connected with probability W (x; y). We call such a random family a graphon process. We prove that a graphon process has convergent subgraph frequencies (with possibly infinite limits) and that, in the natural extension of the cut metric to our setting, the sequence converges to the generating graphon. -

Introduction to Computer Science CSCI 109
Introduction to Computer Science CSCI 109 China – Tianhe-2 Readings Andrew Goodney Fall 2019 St. Amant, Ch. 5 Lecture 7: Compilers and Programming 10/14, 2019 Reminders u Quiz 3 today – at the end u Midterm 10/28 u HW #2 due tomorrow u HW #3 not out until next week 1 Where are we? 2 Side Note u Two things funny/note worthy about this cartoon u #1 is COBOL (we’ll talk about that later) u #2 is ?? 3 “Y2k Bug” u Y2K bug?? u In the 1970’s-1980’s how to store a date? u Use MM/DD/YY v More efficient – every byte counts (especially then) u What is/was the issue? u What was the assumption here? v “No way my COBOL program will still be in use 25+ years from now” u Wrong! 4 Agenda u What is a program u Brief History of High-Level Languages u Very Brief Introduction to Compilers u ”Robot Example” u Quiz 6 What is a Program? u A set of instructions expressed in a language the computer can understand (and therefore execute) u Algorithm: abstract (usually expressed ‘loosely’ e.g., in english or a kind of programming pidgin) u Program: concrete (expressed in a computer language with precise syntax) v Why does it need to be precise? 8 Programming in Machine Language is Hard u CPU performs fetch-decode-execute cycle millions of time a second u Each time, one instruction is fetched, decoded and executed u Each instruction is very simple (e.g., move item from memory to register, add contents of two registers, etc.) u To write a sophisticated program as a sequence of these simple instructions is very difficult (impossible) for humans 9 Machine Language Example -

Novice Programmer = (Sourcecode) (Pseudocode) Algorithm
Journal of Computer Science Original Research Paper Novice Programmer = (Sourcecode) (Pseudocode) Algorithm 1Budi Yulianto, 2Harjanto Prabowo, 3Raymond Kosala and 4Manik Hapsara 1Computer Science Department, School of Computer Science, Bina Nusantara University, Jakarta, Indonesia 11480 2Management Department, BINUS Business School Undergraduate Program, Bina Nusantara University, Jakarta, Indonesia 11480 3Computer Science Department, Faculty of Computing and Media, Bina Nusantara University, Jakarta, Indonesia 11480 4Computer Science Department, BINUS Graduate Program - Doctor of Computer Science, Bina Nusantara University, Jakarta, Indonesia 11480 Article history Abstract: Difficulties in learning programming often hinder new students Received: 7-11-2017 as novice programmers. One of the difficulties is to transform algorithm in Revised: 14-01-2018 mind into syntactical solution (sourcecode). This study proposes an Accepted: 9-04-2018 application to help students in transform their algorithm (logic) into sourcecode. The proposed application can be used to write down students’ Corresponding Author: Budi Yulianto algorithm (logic) as block of pseudocode and then transform it into selected Computer Science Department, programming language sourcecode. Students can learn and modify the School of Computer Science, sourcecode and then try to execute it (learning by doing). Proposed Bina Nusantara University, application can improve 17% score and 14% passing rate of novice Jakarta, Indonesia 11480 programmers (new students) in learning programming. Email: [email protected] Keywords: Algorithm, Pseudocode, Novice Programmer, Programming Language Introduction students in some universities that are new to programming and have not mastered it. In addition, Programming language is a language used by some universities (especially in rural areas or with programmers to write commands (syntax and semantics) limited budget) do not have tools that can help their new that can be understood by a computer to create a students in learning programming (Yulianto et al ., 2016b). -

4. Elementary Graph Algorithms in External Memory∗
4. Elementary Graph Algorithms in External Memory∗ Irit Katriel and Ulrich Meyer∗∗ 4.1 Introduction Solving real-world optimization problems frequently boils down to process- ing graphs. The graphs themselves are used to represent and structure rela- tionships of the problem’s components. In this chapter we review external- memory (EM) graph algorithms for a few representative problems: Shortest path problems are among the most fundamental and also the most commonly encountered graph problems, both in themselves and as sub- problems in more complex settings [21]. Besides obvious applications like preparing travel time and distance charts [337], shortest path computations are frequently needed in telecommunications and transportation industries [677], where messages or vehicles must be sent between two geographical lo- cations as quickly or as cheaply as possible. Other examples are complex traffic flow simulations and planning tools [337], which rely on solving a large number of individual shortest path problems. One of the most commonly encountered subtypes is the Single-Source Shortest-Path (SSSP) version: let G =(V,E) be a graph with |V | nodes and |E| edges, let s be a distinguished vertex of the graph, and c be a function assigning a non-negative real weight to each edge of G. The objective of the SSSP is to compute, for each vertex v reachable from s, the weight dist(v) of a minimum-weight (“shortest”) path from s to v; the weight of a path is the sum of the weights of its edges. Breadth-First Search (BFS) [554] can be seen as the unweighted version of SSSP; it decomposes a graph into levels where level i comprises all nodes that can be reached from the source via i edges. -

Sparse Graphs
EuroComb 2005 DMTCS proc. AE, 2005, 181–186 Pebble Game Algorithms and (k, l)-Sparse Graphs Audrey Lee1†and Ileana Streinu2‡ 1Department of Computer Science, University of Massachusetts at Amherst, Amherst, MA, USA. [email protected] 2Computer Science Department, Smith College, Northampton, MA, USA. [email protected] A multi-graph G on n vertices is (k, l)-sparse if every subset of n0 ≤ n vertices spans at most kn0 − l edges, 0 ≤ l < 2k. G is tight if, in addition, it has exactly kn − l edges. We characterize (k, l)-sparse graphs via a family of simple, elegant and efficient algorithms called the (k, l)-pebble games. As applications, we use the pebble games for computing components (maximal tight subgraphs) in sparse graphs, to obtain inductive (Henneberg) constructions, and, when l = k, edge-disjoint tree decompositions. Keywords: sparse graph, pebble game, rigidity, arboricity, graph orientation with bounded degree 1 Introduction A graph§ G = (V, E) with n = |V | vertices and m = |E| edges is (k, l)-sparse if every subset of n0 ≤ n vertices spans at most kn0 − l edges. If, furthermore, m = kn − l, G will be called tight. A graph is a (k, a)-arborescence if it can be decomposed into k edge-disjoint spanning trees after the addition of any a edges. Here, k, l and a are positive integers satisfying a simple relationship, which is 0 ≤ l < 2k for sparseness or 0 ≤ a < k for arboricity. Sparseness and arboricity are closely related, and have important applications in Rigidity Theory. Clas- sical results of Nash-Williams [10] and Tutte [16] identify the class of graphs decomposable into k edge- disjoint spanning trees with the tight (k, k)-sparse graphs.