Listener Feedback #233
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Windows 7 Operating Guide
Welcome to Windows 7 1 1 You told us what you wanted. We listened. This Windows® 7 Product Guide highlights the new and improved features that will help deliver the one thing you said you wanted the most: Your PC, simplified. 3 3 Contents INTRODUCTION TO WINDOWS 7 6 DESIGNING WINDOWS 7 8 Market Trends that Inspired Windows 7 9 WINDOWS 7 EDITIONS 10 Windows 7 Starter 11 Windows 7 Home Basic 11 Windows 7 Home Premium 12 Windows 7 Professional 12 Windows 7 Enterprise / Windows 7 Ultimate 13 Windows Anytime Upgrade 14 Microsoft Desktop Optimization Pack 14 Windows 7 Editions Comparison 15 GETTING STARTED WITH WINDOWS 7 16 Upgrading a PC to Windows 7 16 WHAT’S NEW IN WINDOWS 7 20 Top Features for You 20 Top Features for IT Professionals 22 Application and Device Compatibility 23 WINDOWS 7 FOR YOU 24 WINDOWS 7 FOR YOU: SIMPLIFIES EVERYDAY TASKS 28 Simple to Navigate 28 Easier to Find Things 35 Easy to Browse the Web 38 Easy to Connect PCs and Manage Devices 41 Easy to Communicate and Share 47 WINDOWS 7 FOR YOU: WORKS THE WAY YOU WANT 50 Speed, Reliability, and Responsiveness 50 More Secure 55 Compatible with You 62 Better Troubleshooting and Problem Solving 66 WINDOWS 7 FOR YOU: MAKES NEW THINGS POSSIBLE 70 Media the Way You Want It 70 Work Anywhere 81 New Ways to Engage 84 INTRODUCTION TO WINDOWS 7 6 WINDOWS 7 FOR IT PROFESSIONALS 88 DESIGNING WINDOWS 7 8 WINDOWS 7 FOR IT PROFESSIONALS: Market Trends that Inspired Windows 7 9 MAKE PEOPLE PRODUCTIVE ANYWHERE 92 WINDOWS 7 EDITIONS 10 Remove Barriers to Information 92 Windows 7 Starter 11 Access -

Introduction to Windows 7
[Not for Circulation] Introduction to Windows 7 This document provides a basic overview of the new and enhanced features of Windows 7 as well as instructions for how to request an upgrade. Windows 7 at UIS Windows 7 is Microsoft’s latest operating system. Beginning in the fall of 2010, UIS will upgrade all classroom and lab PCs to Windows 7. Any new PC that is ordered will automatically come installed with Windows 7. To request an upgrade, contact the Technology Support Center (TSC) at 217/206-6000 or [email protected]. The TSC will evaluate your machine to see if it’s capable of running Windows 7. (Your computer needs a dual core processor and at least 2 GB of RAM.) Please note that University licensing does NOT cover distribution of Windows 7 for personally owned computers. However, it is available for a discounted price via the WebStore at http://webstore.illinois.edu. What to Consider Before Upgrading There is no direct upgrade path from Windows XP to Windows 7. Therefore, the TSC will take your computer, save your files, and install Windows 7 on a clean hard drive. Please budget a couple days for this process. In some cases, you may have older devices that will not work with Windows 7. While many vendors are providing and will continue to provide drivers for their hardware, in some cases, printers, scanners, and other devices that are more than 5 years old may have issues running on Windows 7. To check the compatibility of your devices with Windows 7, visit the Microsoft Windows 7 Compatibility Center at http://www.microsoft.com/windows/compatibility/windows-7/en-us/default.aspx. -
Performing a Windows 7 Upgrade from Windows Vista
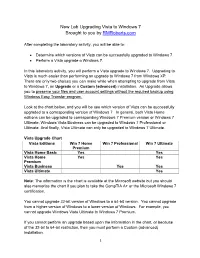
New Lab Upgrading Vista to Windows 7 Brought to you by RMRoberts.com After completing the laboratory activity, you will be able to: Determine which versions of Vista can be successfully upgraded to Windows 7. Perform a Vista upgrade o Windows 7. In this laboratory activity, you will perform a Vista upgrade to Windows 7. Upgrading to Vista is much easier than performing an upgrade to Windows 7 from Windows XP. There are only two choices you can make while when attempting to upgrade from Vista to Windows 7, an Upgrade or a Custom (advanced) installation. An Upgrade allows you to preserve your files and user account settings without the required backup using Windows Easy Transfer program. Look at the chart below, and you will be see which version of Vista can be successfully upgraded to a corresponding version of Windows 7. In general, both Vista Home editions can be upgraded to corresponding Windows 7 Premium version or Windows 7 Ultimate. Windows Vista Business can be upgraded to Windows 7 Professional or Ultimate. And finally, Vista Ultimate can only be upgraded to Windows 7 Ultimate. Vista Upgrade Chart Vista Editions Win 7 Home Win 7 Professional Win 7 Ultimate Premium Vista Home Basic Yes Yes Vista Home Yes Yes Premium Vista Business Yes Yes Vista Ultimate Yes Note: The information is the chart is available at the Microsoft website but you should also memorize the chart if you plan to take the CompTIA A+ or the Microsoft Windows 7 certification. You cannot upgrade 32-bit version of Windows to a 64-bit version. -
Intel® HD Graphics 5300 12 4.4 2.0 Yes Yes
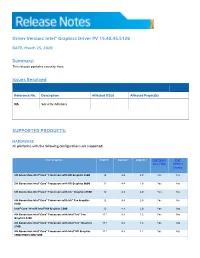
Driver Version: Intel® Graphics Driver PV 15.40.45.5126 DATE: March 25, 2020 Summary: This release contains security fixes. Issues Resolved Reference No. Description Affected OS(s) Affected Project(s) NA Security Advisory SUPPORTED PRODUCTS: HARDWARE All platforms with the following configurations are supported: Intel® Graphics1 DirectX*2 OpenGL* OpenCL* Intel® Quick Intel® Sync Video Wireless Display 5th Generation Intel® Core™ Processors with HD Graphics 5500 12 4.4 2.0 Yes Yes 5th Generation Intel® Core™ Processors with HD Graphics 6000 12 4.4 2.0 Yes Yes 5th Generation Intel® Core™ Processors with Iris™ Graphics 6100 12 4.4 2.0 Yes Yes 5th Generation Intel® Core™ Processors with Iris™ Pro Graphics 12 4.4 2.0 Yes Yes 6200 Intel® Core™ M with Intel® HD Graphics 5300 12 4.4 2.0 Yes Yes 4th Generation Intel® Core™ Processors with Intel® Iris™ Pro 11.1 4.3 1.2 Yes Yes Graphics 5200 4th Generation Intel® Core™ Processors with Intel® Iris™ Graphics 11.1 4.3 1.2 Yes Yes 5100 4th Generation Intel® Core™ Processors with Intel® HD Graphics 11.1 4.3 1.2 Yes Yes 5000/4600/4400/4200 Intel® Pentium® and Celeron® Processors with Intel® HD Graphics 11.1 4.3 1.2 Yes Yes based on 4th and 5th Generation Intel® Core™ Pentium®, Celeron®, and Atom™ processors based on Braswell and 12 4.3 2.0 Yes Yes CherryTrail. SOFTWARE On 4th Generation Intel Core processors and related Pentium/Celeron: • Microsoft Windows 10® 64-bit, 32-bit* *32-bit support is limited to particular SKU’s. -

NG16 Program
C M Y CM MY CY CMY K PROGRAM 2016 #nordicgame Award-winning projects from Swiss indie studios Surprising Gamedesigns / Innovative Gameplay Late Shift Niche Booth Booth CtrlMovie AG Niche Game C2 lateshift-movie.com niche-game.com C4 Welcome to Nordic Game 2016: Knowledge, Emotion, Business. We are very proud to welcome you to three days of Knowledge, Emotion and Business. It’s the thirteenth edition of the conference, and it’s been Personal hectic, fun, challenging and inspiring to prepare it for you. Booth Photorealistic C5 Avatar SDK We look at this year’s show as sort of a reboot. We have focused heavily Dacuda AG dacuda.com on tweaking some essential parts, while maintaining the elements that we know you love and define as the special Nordic Game experience. As always, we’re more than happy to get feedback and input from you, because this show is as much yours as it is ours, and we want to keep on learning and improving. So, we hope you are ready to listen, talk, learn, share, build, connect, evolve, inspire, laugh, drink, eat, joke, be serious, have fun, be tired but also happy, and that you will enjoy NG16 as much as we enjoyed creating it. Thank you for joining us, and may you and your business prosper! The Nordic Game 2016 Team Booth World Never End Schlicht Booth C7 HeartQuake Studios Mr. Whale’s Game Service C8 heartquakestudios.com schlichtgame.ch NG16 TIME SCHEDULE We are 17 May PRE-CONFERENCE DAY 13:00 – 17:00 Badge pick-up 14:00 Game City Studio Tour pick-up 18 May CONFERENCE DAY 1 Join us to democratize 9:00 Badge pick-up -

Students,Faculty & Staff Guide for Windows 7
iM Students,Faculty & Staff Guide for Windows 7 Prepared by Information Technology Division Lehman College, CUNY March 22, 2014 This document was originally prepared by Dickinson College. It was modified and adapted for use at Lehman College with the permission of Dickinson College. Introduction to Windows 7 Table of Contents Windows 7 Taskbar ...................................................................................................................................... 2 Show Desktop ............................................................................................................................................... 2 Start Menu..................................................................................................................................................... 3 Pin ................................................................................................................................................................. 4 Jump Lists ..................................................................................................................................................... 4 Snap .............................................................................................................................................................. 5 Windows Search ........................................................................................................................................... 6 Library (the new My Documents area & more) ........................................................................................... -

Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability
Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability Hernan Ochoa Agustin Azubel [email protected] [email protected] Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability Presentation goals: ‣ Describe the vulnerability in detail ‣ Explain & demonstrate exploitation • Three different exploitation methods ‣ Clear up misconceptions ‣ Determine vulnerability scope, severity and impact ‣ Share Conclusions BlackHat USA 2010 Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability Vulnerability Information ‣ Flaws in Windows’ implementation of NTLM - attackers can access SMB service as authorized user - leads to read/write access to files, SMB shared resources in general and remote code execution ‣ Published February 2010 ‣ CVE-2010-0231, BID 38085 ‣ Advisory with Exploit Code: • http://www.hexale.org/advisories/OCHOA-2010-0209.txt ‣ Addressed by MS10-012 BlackHat USA 2010 Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability Why talk about this vulnerability? ‣ Major 14-year old vulnerability affecting Windows Authentication Mechanism! - Basically, all Windows versions were affected (NT4, 2000, XP, 2003, Vista, 2008, 7) - Windows NT 4 released in ∼1996 - Windows NT 3.1 released in ∼1993 (∼17 years ago) - All this time, we assumed it was working correctly.. but it wasn’t... - Flew under the radar... BlackHat USA 2010 Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability Why talk about this vulnerability? ‣ Interesting vulnerability, not your common buffer overflow - Issues in the Pseudo-Random Number Generator (PRNG) - Challenge-response protocol implementation issues - Replay attacks - Attack to predict challenges is interesting BlackHat USA 2010 Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability Why talk about this vulnerability? ‣ There’s a lesson to be learned.. -

Security Analysis of the Signal Protocol Student: Bc
ASSIGNMENT OF MASTER’S THESIS Title: Security Analysis of the Signal Protocol Student: Bc. Jan Rubín Supervisor: Ing. Josef Kokeš Study Programme: Informatics Study Branch: Computer Security Department: Department of Computer Systems Validity: Until the end of summer semester 2018/19 Instructions 1) Research the current instant messaging protocols, describe their properties, with a particular focus on security. 2) Describe the Signal protocol in detail, its usage, structure, and functionality. 3) Select parts of the protocol with a potential for security vulnerabilities. 4) Analyze these parts, particularly the adherence of their code to their documentation. 5) Discuss your findings. Formulate recommendations for the users. References Will be provided by the supervisor. prof. Ing. Róbert Lórencz, CSc. doc. RNDr. Ing. Marcel Jiřina, Ph.D. Head of Department Dean Prague January 27, 2018 Czech Technical University in Prague Faculty of Information Technology Department of Computer Systems Master’s thesis Security Analysis of the Signal Protocol Bc. Jan Rub´ın Supervisor: Ing. Josef Kokeˇs 1st May 2018 Acknowledgements First and foremost, I would like to express my sincere gratitude to my thesis supervisor, Ing. Josef Kokeˇs,for his guidance, engagement, extensive know- ledge, and willingness to meet at our countless consultations. I would also like to thank my brother, Tom´aˇsRub´ın,for proofreading my thesis. I cannot express enough gratitude towards my parents, Lenka and Jaroslav Rub´ınovi, who supported me both morally and financially through my whole studies. Last but not least, this thesis would not be possible without Anna who re- lentlessly supported me when I needed it most. Declaration I hereby declare that the presented thesis is my own work and that I have cited all sources of information in accordance with the Guideline for adhering to ethical principles when elaborating an academic final thesis. -

Mobile Games in Europe Innovation in European Digital Economy
Mobile games in Europe Innovation in the European Digital Economy Mobile games in Europe Innovation in European Digital Economy September 2015 © 2015 Deloitte LLP 1 Mobile games in Europe Innovation in the European Digital Economy Important Notice from Deloitte This final report (the “Final Report”) has been prepared by Deloitte LLP (“Deloitte”) for Interactive Software Federation of Europe (“ISFE”) in accordance with the contract with them dated 12/05/2015 (“the Contract”) and on the basis of the scope and limitations set out below. The Final Report has been prepared solely for the purposes of analysing the mobile games segment in the EU, as set out in the Contract. It should not be used for any other purposes or in any other context, and Deloitte accepts no responsibility for its use in either regard. The Final Report is provided exclusively for ISFE’s use under the terms of the Contract. No party other than ISFE is entitled to rely on the Final Report for any purpose whatsoever and Deloitte accepts no responsibility or liability or duty of care to any party other than ISFE in respect of the Final Report and any of its contents. As set out in the Contract, the scope of our work has been limited by the time, information and explanations made available to us. The information contained in the Final Report has been obtained from ISFE and third party sources that are clearly referenced in the appropriate sections of the Final Report. Deloitte has neither sought to corroborate this information nor to review its overall reasonableness. -

Is Bob Sending Mixed Signals?
Is Bob Sending Mixed Signals? Michael Schliep Ian Kariniemi Nicholas Hopper University of Minnesota University of Minnesota University of Minnesota [email protected] [email protected] [email protected] ABSTRACT Demand for end-to-end secure messaging has been growing rapidly and companies have responded by releasing applications that imple- ment end-to-end secure messaging protocols. Signal and protocols based on Signal dominate the secure messaging applications. In this work we analyze conversational security properties provided by the Signal Android application against a variety of real world ad- versaries. We identify vulnerabilities that allow the Signal server to learn the contents of attachments, undetectably re-order and drop messages, and add and drop participants from group conversations. We then perform proof-of-concept attacks against the application to demonstrate the practicality of these vulnerabilities, and suggest mitigations that can detect our attacks. The main conclusion of our work is that we need to consider more than confidentiality and integrity of messages when designing future protocols. We also stress that protocols must protect against compromised servers and at a minimum implement a trust but verify model. 1 INTRODUCTION (a) Alice’s view of the conversa-(b) Bob’s view of the conversa- Recently many software developers and companies have been inte- tion. tion. grating end-to-end encrypted messaging protocols into their chat applications. Some applications implement a proprietary protocol, Figure 1: Speaker inconsistency in a conversation. such as Apple iMessage [1]; others, such as Cryptocat [7], imple- ment XMPP OMEMO [17]; but most implement the Signal protocol or a protocol based on Signal, including Open Whisper Systems’ caching. -

Signal E2E-Crypto Why Can’T I Hold All These Ratchets
Signal E2E-Crypto Why Can’t I Hold All These Ratchets oxzi 23.03.2021 In the next 30 minutes there will be I a rough introduction in end-to-end encrypted instant messaging, I an overview of how Signal handles those E2E encryption, I and finally a demo based on a WeeChat plugin. Historical Background I Signal has not reinvented the wheel - and this is a good thing! I Goes back to Off-the-Record Communication (OTR)1. OTR Features I Perfect forward secrecy I Deniable authentication 1Borisov, Goldberg, and Brewer. “Off-the-record communication, or, why not to use PGP”, 2004 Influence and Evolution I OTR influenced the Signal Protocol, Double Ratchet. I Double Ratchet influence OMEMO; supports many-to-many communication. I Also influenced Olm, E2E encryption of the Matrix protocol. I OTR itself was influenced by this, version four was introduced in 2018. Double Ratchet The Double Ratchet algorithm is used by two parties to exchange encrypted messages based on a shared secret key. The Double Ratchet algorithm2 is essential in Signal’s E2E crypto. But first, some basics. 2Perrin, and Marlinspike. “The Double Ratchet Algorithm”, 2016 Cryptographic Ratchet A ratchet is a cryptographic function that only moves forward. In other words, one cannot easily reverse its output. Triple Ratchet, I guess.3 3By Salvatore Capalbi, https://www.flickr.com/photos/sheldonpax/411551322/, CC BY-SA 2.5 Symmetric-Key Ratchet Symmetric-Key Ratchet In everyday life, Keyed-Hash Message Authentication Code (HMAC) or HMAC-based KDFs (HKDF) are used. func ratchet(ckIn[]byte)(ckOut, mk[]byte){ kdf := hmac.New(sha256.New, ckIn) kdf.Write(c) // publicly known constant c out := kdf.Sum(nil) return out[:32], out[32:] } ck0 :=[]byte{0x23, 0x42, ...} // some initial shared secret ck1, mk1 := ratchet(ck0) ck2, mk2 := ratchet(ck1) Diffie-Hellman Key Exchange Diffie-Hellman Key Exchange Diffie-Hellman Key Exchange Originally, DH uses primitive residue classes modulo n. -
Request for Reconsideration After Final Action
Under the Paperwork Reduction Act of 1995 no persons are required to respond to a collection of information unless it displays a valid OMB control number. PTO Form 1960 (Rev 10/2011) OMB No. 0651-0050 (Exp 09/20/2020) Request for Reconsideration after Final Action The table below presents the data as entered. Input Field Entered SERIAL NUMBER 87031396 LAW OFFICE ASSIGNED LAW OFFICE 116 MARK SECTION MARK https://tmng-al.uspto.gov/resting2/api/img/87031396/large LITERAL ELEMENT CRYPTTALK STANDARD CHARACTERS YES USPTO-GENERATED IMAGE YES MARK STATEMENT The mark consists of standard characters, without claim to any particular font style, size or color. ARGUMENT(S) In the Official Action, the Examiner has made final the refusal to register the "CRYPTTALK" mark on the Principal Register because of the "likelihood of confusion" of the mark with prior registered marks. Applicant respectfully disagrees and believes that the Examiner has failed to make a prima facie showing of likelihood of confusion. I. NO LIKELIHOOD OF CONFUSION WITH U.S. REGISTRATION NOS. 4,707,027 and 4,859,726 A. The term "CRYPT" is Not a Distinctive Mark. The Examiner does not discuss the possibility of the cited registrations being viewed by the relevant consumer as the term "CRIP" and instead suggests that the terms "CRYPT" and "CRIPT" are the only relevant words to compare. The Examiner goes on to conclude that "CRYPT" and "CRIPT" in the respective marks "appear similar and are phonetic equivalents." This alleged similarity has been made the basis of the Examiners refusal to register Applicant's mark.