Binary-Level Lightweight Data Integration to Develop Program Understanding Tools for Embedded Software in C
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Practical C Programming, 3Rd Edition
Practical C Programming, 3rd Edition By Steve Oualline 3rd Edition August 1997 ISBN: 1-56592-306-5 This new edition of "Practical C Programming" teaches users not only the mechanics or programming, but also how to create programs that are easy to read, maintain, and debug. It features more extensive examples and an introduction to graphical development environments. Programs conform to ANSI C. 0 TEAM FLY PRESENTS Table of Contents Preface How This Book is Organized Chapter by Chapter Notes on the Third Edition Font Conventions Obtaining Source Code Comments and Questions Acknowledgments Acknowledgments to the Third Edition I. Basics 1. What Is C? How Programming Works Brief History of C How C Works How to Learn C 2. Basics of Program Writing Programs from Conception to Execution Creating a Real Program Creating a Program Using a Command-Line Compiler Creating a Program Using an Integrated Development Environment Getting Help on UNIX Getting Help in an Integrated Development Environment IDE Cookbooks Programming Exercises 3. Style Common Coding Practices Coding Religion Indentation and Code Format Clarity Simplicity Summary 4. Basic Declarations and Expressions Elements of a Program Basic Program Structure Simple Expressions Variables and Storage 1 TEAM FLY PRESENTS Variable Declarations Integers Assignment Statements printf Function Floating Point Floating Point Versus Integer Divide Characters Answers Programming Exercises 5. Arrays, Qualifiers, and Reading Numbers Arrays Strings Reading Strings Multidimensional Arrays Reading Numbers Initializing Variables Types of Integers Types of Floats Constant Declarations Hexadecimal and Octal Constants Operators for Performing Shortcuts Side Effects ++x or x++ More Side-Effect Problems Answers Programming Exercises 6. -

Emacspeak — the Complete Audio Desktop User Manual
Emacspeak | The Complete Audio Desktop User Manual T. V. Raman Last Updated: 19 November 2016 Copyright c 1994{2016 T. V. Raman. All Rights Reserved. Permission is granted to make and distribute verbatim copies of this manual without charge provided the copyright notice and this permission notice are preserved on all copies. Short Contents Emacspeak :::::::::::::::::::::::::::::::::::::::::::::: 1 1 Copyright ::::::::::::::::::::::::::::::::::::::::::: 2 2 Announcing Emacspeak Manual 2nd Edition As An Open Source Project ::::::::::::::::::::::::::::::::::::::::::::: 3 3 Background :::::::::::::::::::::::::::::::::::::::::: 4 4 Introduction ::::::::::::::::::::::::::::::::::::::::: 6 5 Installation Instructions :::::::::::::::::::::::::::::::: 7 6 Basic Usage. ::::::::::::::::::::::::::::::::::::::::: 9 7 The Emacspeak Audio Desktop. :::::::::::::::::::::::: 19 8 Voice Lock :::::::::::::::::::::::::::::::::::::::::: 22 9 Using Online Help With Emacspeak. :::::::::::::::::::: 24 10 Emacs Packages. ::::::::::::::::::::::::::::::::::::: 26 11 Running Terminal Based Applications. ::::::::::::::::::: 45 12 Emacspeak Commands And Options::::::::::::::::::::: 49 13 Emacspeak Keyboard Commands. :::::::::::::::::::::: 361 14 TTS Servers ::::::::::::::::::::::::::::::::::::::: 362 15 Acknowledgments.::::::::::::::::::::::::::::::::::: 366 16 Concept Index :::::::::::::::::::::::::::::::::::::: 367 17 Key Index ::::::::::::::::::::::::::::::::::::::::: 368 Table of Contents Emacspeak :::::::::::::::::::::::::::::::::::::::::: 1 1 Copyright ::::::::::::::::::::::::::::::::::::::: -

Cscope Security Update (RHSA-2009-1101)
cscope security update (RHSA-2009-1101) Original Release Date: June 16, 2009 Last Revised: June 16, 2009 Number: ASA-2009-236 Risk Level: None Advisory Version: 1.0 Advisory Status: Final 1. Overview: cscope is a mature, ncurses-based, C source-code tree browsing tool. Multiple buffer overflow flaws were found in cscope. An attacker could create a specially crafted source code file that could cause cscope to crash or, possibly, execute arbitrary code when browsed with cscope. The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the names CVE-2004-2541, CVE-2006-4262, CVE-2009- 0148 and CVE-2009-1577 to these issues. Note: This advisory is specific to RHEL3 and RHEL4. No Avaya system products are vulnerable, as cscope is not installed by default. More information about these vulnerabilities can be found in the security advisory issued by RedHat Linux: · https://rhn.redhat.com/errata/RHSA-2009-1101.html 2. Avaya System Products using RHEL3 or RHEL4 with cscope installed: None 3. Avaya Software-Only Products: Avaya software-only products operate on general-purpose operating systems. Occasionally vulnerabilities may be discovered in the underlying operating system or applications that come with the operating system. These vulnerabilities often do not impact the software-only product directly but may threaten the integrity of the underlying platform. In the case of this advisory Avaya software-only products are not affected by the vulnerability directly but the underlying Linux platform may be. Customers should determine on which Linux operating system the product was installed and then follow that vendor's guidance. -

Linux Kernel and Driver Development Training Slides
Linux Kernel and Driver Development Training Linux Kernel and Driver Development Training © Copyright 2004-2021, Bootlin. Creative Commons BY-SA 3.0 license. Latest update: October 9, 2021. Document updates and sources: https://bootlin.com/doc/training/linux-kernel Corrections, suggestions, contributions and translations are welcome! embedded Linux and kernel engineering Send them to [email protected] - Kernel, drivers and embedded Linux - Development, consulting, training and support - https://bootlin.com 1/470 Rights to copy © Copyright 2004-2021, Bootlin License: Creative Commons Attribution - Share Alike 3.0 https://creativecommons.org/licenses/by-sa/3.0/legalcode You are free: I to copy, distribute, display, and perform the work I to make derivative works I to make commercial use of the work Under the following conditions: I Attribution. You must give the original author credit. I Share Alike. If you alter, transform, or build upon this work, you may distribute the resulting work only under a license identical to this one. I For any reuse or distribution, you must make clear to others the license terms of this work. I Any of these conditions can be waived if you get permission from the copyright holder. Your fair use and other rights are in no way affected by the above. Document sources: https://github.com/bootlin/training-materials/ - Kernel, drivers and embedded Linux - Development, consulting, training and support - https://bootlin.com 2/470 Hyperlinks in the document There are many hyperlinks in the document I Regular hyperlinks: https://kernel.org/ I Kernel documentation links: dev-tools/kasan I Links to kernel source files and directories: drivers/input/ include/linux/fb.h I Links to the declarations, definitions and instances of kernel symbols (functions, types, data, structures): platform_get_irq() GFP_KERNEL struct file_operations - Kernel, drivers and embedded Linux - Development, consulting, training and support - https://bootlin.com 3/470 Company at a glance I Engineering company created in 2004, named ”Free Electrons” until Feb. -

The Journal of AUUG Inc. Volume 25 ¯ Number 3 September 2004
The Journal of AUUG Inc. Volume 25 ¯ Number 3 September 2004 Features: mychart Charting System for Recreational Boats 8 Lions Commentary, part 1 17 Managing Debian 24 SEQUENT: Asynchronous Distributed Data Exchange 51 Framework News: Minutes to AUUG board meeting of 5 May 2004 13 Liberal license for ancient UNIX sources 16 First Australian UNIX Developer’s Symposium: CFP 60 First Digital Pest Symposium 61 Regulars: Editorial 1 President’s Column 3 About AUUGN 4 My Home Network 5 AUUG Corporate Members 23 A Hacker’s Diary 29 Letters to AUUG 58 Chapter Meetings and Contact Details 62 AUUG Membership AppLication Form 63 ISSN 1035-7521 Print post approved by Australia Post - PP2391500002 AUUGN The journal of AUUG Inc. Volume 25, Number 3 September 2004 Editor ial Gr eg Lehey <[email protected]> After last quarter's spectacularly late delivery of For those newcomers who don't recall the “Lions AUUGN, things aregradually getting back to nor- Book”, this is the “Commentary on the Sixth Edi- mal. I had hoped to have this on your desk by tion UNIX Operating System” that John Lions the end of September,but it wasn't to be. Given wr ote for classes at UNSW back in 1977. Suppos- that that was only a couple of weeks after the “Ju- edly they werethe most-photocopied of all UNIX- ly” edition, this doesn’t seem to be such a prob- related documents. Ihad mislaid my photocopy, lem. I'm fully expecting to get the December is- poor as it was (weren't they all?) some time earli- sue out in time to keep you from boredom over er,soIwas delighted to have an easy to read ver- the Christmas break. -

NSWI 0138: Advanced Unix Programming
NSWI 0138: Advanced Unix programming (c) 2011-2016 Vladim´ırKotal (c) 2009-2010 Jan Pechanec, Vladim´ırKotal SISAL MFF UK, Malostransk´en´am.25, 118 00 Praha 1 Charles University Czech Republic Vladim´ırKotal [email protected] March 10, 2016 1 Vladim´ırKotal NSWI 0138 (Advanced Unix programming) Contents 1 Overview 5 1.1 What is this lecture about? . .5 1.2 The lecture will cover... .5 1.3 A few notes on source code files . .6 2 Testing 6 2.1 Why?...........................................6 2.2 When ? . .6 2.3 Types of testing . .7 3 Debugging 8 3.1 Debuging in general . .8 3.2 Observing . .9 3.3 Helper tools . .9 3.3.1 ctags . .9 3.3.2 cscope . 10 3.3.3 OpenGrok . 11 3.3.4 Other tools . 11 3.4 Debugging data . 11 3.4.1 stabs . 11 3.4.2 DWARF . 12 3.4.3 CTF (Compact C Type Format) . 12 3.5 Resource leaks . 13 3.6 libumem . 13 3.6.1 How does libumem work . 14 3.6.2 Using libumem+mdb to find memory leaks . 14 3.6.3 How does ::findleaks work . 16 3.7 watchmalloc . 17 3.8 Call tracing . 18 3.9 Using /proc . 19 3.10 Debugging dynamic libraries . 20 3.11 Debuggers . 20 3.12 Symbol search and interposition . 20 3.13 dtrace . 21 4 Terminals 21 4.1 Terminal I/O Overview . 21 4.2 Terminal I/O Overview (cont.) . 22 4.3 Physical (Hardware) Terminal . 24 4.4 stty(1) command . 24 4.5 TTY Driver Connected To a Phy Terminal . -

Pipenightdreams Osgcal-Doc Mumudvb Mpg123-Alsa Tbb
pipenightdreams osgcal-doc mumudvb mpg123-alsa tbb-examples libgammu4-dbg gcc-4.1-doc snort-rules-default davical cutmp3 libevolution5.0-cil aspell-am python-gobject-doc openoffice.org-l10n-mn libc6-xen xserver-xorg trophy-data t38modem pioneers-console libnb-platform10-java libgtkglext1-ruby libboost-wave1.39-dev drgenius bfbtester libchromexvmcpro1 isdnutils-xtools ubuntuone-client openoffice.org2-math openoffice.org-l10n-lt lsb-cxx-ia32 kdeartwork-emoticons-kde4 wmpuzzle trafshow python-plplot lx-gdb link-monitor-applet libscm-dev liblog-agent-logger-perl libccrtp-doc libclass-throwable-perl kde-i18n-csb jack-jconv hamradio-menus coinor-libvol-doc msx-emulator bitbake nabi language-pack-gnome-zh libpaperg popularity-contest xracer-tools xfont-nexus opendrim-lmp-baseserver libvorbisfile-ruby liblinebreak-doc libgfcui-2.0-0c2a-dbg libblacs-mpi-dev dict-freedict-spa-eng blender-ogrexml aspell-da x11-apps openoffice.org-l10n-lv openoffice.org-l10n-nl pnmtopng libodbcinstq1 libhsqldb-java-doc libmono-addins-gui0.2-cil sg3-utils linux-backports-modules-alsa-2.6.31-19-generic yorick-yeti-gsl python-pymssql plasma-widget-cpuload mcpp gpsim-lcd cl-csv libhtml-clean-perl asterisk-dbg apt-dater-dbg libgnome-mag1-dev language-pack-gnome-yo python-crypto svn-autoreleasedeb sugar-terminal-activity mii-diag maria-doc libplexus-component-api-java-doc libhugs-hgl-bundled libchipcard-libgwenhywfar47-plugins libghc6-random-dev freefem3d ezmlm cakephp-scripts aspell-ar ara-byte not+sparc openoffice.org-l10n-nn linux-backports-modules-karmic-generic-pae -
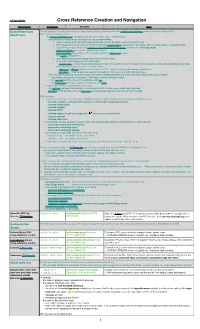
⅀ Xref Local PDF
⬉ Topic Index Cross Reference Creation and Navigation Description Keystroke Function Note Cross References Emacs provides several cross reference tools. Some tools are unified under the unified xref interface some others are independent. with Emacs PEL support several of them: • The unified xref interface is available since Emacs version 25.1. This includes: • The xref unified interface can be used with various back-ends: 1. major-mode specific load/interpretation backend (such as what is used for Emacs Lisp) 2. Tags-based tools using external TAGS file with the etags syntax supported by the etags utility and other etags-compatible tools: • etags (Emacs tags utility) ; see how to create TAGS files with etags, used by the xref-etag-mode. • Universal Ctags (successor of Exuberant Ctags) • GNU GLOBAL gtags utility with Universal Ctags and Pygments plugin. • The gxref xref back-end 3. other specialized parsers based tools that do not use tags: • Programming language agnostic packages: • dumb-jump, a fast grep/ag/ripgrep-based engine to navigate in over 40 programming languages without tags/database index files. • Specialized packages for specific major modes: • rtag-xref, a RTags backend specialized for C/C++ code. It uses a client/server application. • info-xref an internal package used to navigate into info document external references. • The xref unified interface can also be used with various front-end selectors when several entries are found for a search: • The default xref selector that uses a *xref* buffer to show all search result • The ivy-xref interface to select candidates with ivy • The helm-xref interface to select candidates with helm. -

Using Cscope in Vim
How to incorporate Cscope functionality into VIM. It also supports the use of the cursor to select source code symbols in VIM where you can type custom keystrokes to invoke powerful Cscope functionality. Not only that, it will allow you to invoke Cscope symbols from within any directory in your source code tree. That is because the Cscope database will be built from source- code file path-names referenced from your root directory instead of the standard present directory if you built the Cscope file without the necessary trickery. OS/ program requirements Cscope must be installed on your system. If you don’t have it, then install it be typing in the Terminal ‘yum install cscope’ if running Fedora or ‘sudo apt-get cscope’ if you are running Ubuntu. Note: You must have at least VIM 6.x for this to work correctly. Setting it up You must have cscope_maps.vim. This file should be located in ~/.vim/plugin. If this directory does not exist, then create it. Step 1) Add the .vim plugin directory to your $PATH. Add these lines to the end of your ~/.bash_profile or ~/.bashrc file. PATH=$PATH:$HOME/.vim/plugin EDITOR="vim" Step 2) Add the following code to the bottom of your ~/.bashrc file. This is the function and alias which builds the cscope database. This one is setup to find .c and .h files. Change for the file extensions that are in your source code. function build_cscope_db_func() { local PROJDIR=$PWD cd / find $PROJDIR –name ‘*.c’ –o –name ‘*.h’ > $PROJDIR/cscope.files cd $PROJDIR cscope –Rbkq } alias csbuild=‘build_cscope_db_func’ Step 3) Launch another bash session by typing ‘bash’ at the command prompt. -

Spack a flexible Package Manager for HPC
Spack A flexible package manager for HPC Overview & Introduc0on to Basic Spack Concepts Todd Gamblin Center for Applied Scien0fic Compu0ng LLNL-PRES-806064 This work was performed under the auspices of the U.S. Department of Energy by Lawrence Livermore National Laboratory github.com/LLNL/spack under contract DE-AC52-07NA27344. Lawrence Livermore National Security, LLC Spack is a flexible package manager for HPC § How to install Spack: $ git clone https://github.com/scalability-llnl/spack.git § How to install a package: $ cd spack/bin $ ./spack install hdf5 § HDF5 and its dependencies are installed Get Spack! within the Spack directory. hp://github.com/LLNL/spack § No addi0onal setup required! 2 LLNL-PRES-806064 github.com/LLNL/spack What is the proDucon environment for HPC? § Someone’s home directory? § LLNL? LANL? Sandia? ANL? LBL? TACC? — Environments at large-scale sites are very different. § Which MPI implementaon? § Which compiler? § Which dependencies? § Which versions of dependencies? — Many applicaons require specific dependency versions. Real answer: there isn’t a single production environment or a standard way to build. 3 LLNL-PRES-806064 github.com/LLNL/spack HPC soware is becoming increasingly complex § Not much standardizaon in HPC — every machine/applicaon has a different so[ware stack § Sites share unique hardware among teams with very different requirements — Users want to experiment with many exo0c architectures, compilers, MPI versions — All of this is necessary to get the best performance § Example environment for some LLNL codes: 48 third party packages x 3 MPI versions x 3-ish Platforms mvapich mvapich2 OpenMPI Linux BlueGene Cray Up to 7 compilers Oh, and 2-3 versions of x Intel GCC XLC Clang x each package = ~7,500 combinations PGI Cray Pathscale We want an easy way to quickly sample the space, to build configurations on demand! 4 LLNL-PRES-806064 github.com/LLNL/spack Most exisEng tools Do not support combinatorial versioning § Tradi0onal binary package managers — RPM, yum, APT, yast, etc. -

C User's Guide
C User’s Guide SunSoft, Inc. A Sun Microsystems, Inc. Business 2550 Garcia Avenue Mountain View, CA 94043 USA 415 960-1300 fax 415 969-9131 Part No.: 802-5777-10 Revision A, December 1996 Copyright 1996 Sun Microsystems, Inc., 2550 Garcia Avenue, Mountain View, California 94043-1100 U.S.A. All rights reserved. This product or document is protected by copyright and distributed under licenses restricting its use, copying, distribution, and decompilation. No part of this product or document may be reproduced in any form by any means without prior written authorization of Sun and its licensors, if any. Portions of this product may be derived from the UNIX® system, licensed from Novell, Inc., and from the Berkeley 4.3 BSD system, licensed from the University of California. UNIX is a registered trademark in the United States and other countries and is exclusively licensed by X/Open Company Ltd. Third-party software, including font technology in this product, is protected by copyright and licensed from Sun’s suppliers. RESTRICTED RIGHTS: Use, duplication, or disclosure by the U.S. Government is subject to restrictions of FAR 52.227- 14(g)(2)(6/87) and FAR 52.227-19(6/87), or DFAR 252.227-7015(b)(6/95) and DFAR 227.7202-3(a). Sun, Sun Microsystems, the Sun logo, SunSoft, Solaris, OpenWindows, and Sun WorkShop are trademarks or registered trademarks of Sun Microsystems, Inc. in the United States and other countries. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. in the United States and other countries. -

The Vim Tutorial and Reference the Vim Tutorial and Reference by Steve Oualline
The Vim Tutorial and Reference The Vim Tutorial and Reference By Steve Oualline vim-1.0.odt (28. Sep. 2007) The Vim Book Page 1 The Vim Tutorial and Reference Table of Contents Introduction..............................................................................................26 Chapter 1:Basic Editing............................................................................28 Chapter 2:Editing a Little Faster..............................................................42 Chapter 3:Searching.................................................................................59 Chapter 4:Text Blocks and Multiple Files.................................................69 Chapter 5:Windows and Tabs....................................................................83 Chapter 6:Basic Visual Mode....................................................................99 Chapter 7:Commands for Programmers.................................................111 Chapter 8:Basic Abbreviations, Keyboard Mapping, and Initialization Files.........................................................................................................148 Chapter 9:Basic Command-Mode Commands.........................................159 Chapter 10:Basic GUI Usage...................................................................168 Chapter 11:Dealing with Text Files.........................................................175 Chapter 12:Automatic Completion.........................................................192 Chapter 13:Autocommands.....................................................................202