The Rump Kernel: a Tool for Driver Development and a Toolkit for Applications
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Examining the Viability of MINIX 3 As a Consumer Operating
Examining the Viability of MINIX 3 as a Consumer Operating System Joshua C. Loew March 17, 2016 Abstract The developers of the MINIX 3 operating system (OS) believe that a computer should work like a television set. You should be able to purchase one, turn it on, and have it work flawlessly for the next ten years [6]. MINIX 3 is a free and open-source microkernel-based operating system. MINIX 3 is still in development, but it is capable of running on x86 and ARM processor architectures. Such processors can be found in computers such as embedded systems, mobile phones, and laptop computers. As a light and simple operating system, MINIX 3 could take the place of the software that many people use every day. As of now, MINIX 3 is not particularly useful to a non-computer scientist. Most interactions with MINIX 3 are done through a command-line interface or an obsolete window manager. Moreover, its tools require some low-level experience with UNIX-like systems to use. This project will examine the viability of MINIX 3 from a performance standpoint to determine whether or not it is relevant to a non-computer scientist. Furthermore, this project attempts to measure how a microkernel-based operating system performs against a traditional monolithic kernel-based OS. 1 Contents 1 Introduction 5 2 Background and Related Work 6 3 Part I: The Frame Buffer Driver 7 3.1 Outline of Approach . 8 3.2 Hardware and Drivers . 8 3.3 Challenges and Strategy . 9 3.4 Evaluation . 10 4 Progress 10 4.1 Compilation and Installation . -

The Dragonflybsd Operating System
1 The DragonFlyBSD Operating System Jeffrey M. Hsu, Member, FreeBSD and DragonFlyBSD directories with slightly over 8 million lines of code, 2 million Abstract— The DragonFlyBSD operating system is a fork of of which are in the kernel. the highly successful FreeBSD operating system. Its goals are to The project has a number of resources available to the maintain the high quality and performance of the FreeBSD 4 public, including an on-line CVS repository with mirror sites, branch, while exploiting new concepts to further improve accessible through the web as well as the cvsup service, performance and stability. In this paper, we discuss the motivation for a new BSD operating system, new concepts being mailing list forums, and a bug submission system. explored in the BSD context, the software infrastructure put in place to explore these concepts, and their application to the III. MOTIVATION network subsystem in particular. A. Technical Goals Index Terms— Message passing, Multiprocessing, Network The DragonFlyBSD operating system has several long- operating systems, Protocols, System software. range technical goals that it hopes to accomplish within the next few years. The first goal is to add lightweight threads to the BSD kernel. These threads are lightweight in the sense I. INTRODUCTION that, while user processes have an associated thread and a HE DragonFlyBSD operating system is a fork of the process context, kernel processes are pure threads with no T highly successful FreeBSD operating system. Its goals are process context. The threading model makes several to maintain the high quality and performance of the FreeBSD guarantees with respect to scheduling to ensure high 4 branch, while exploring new concepts to further improve performance and simplify reasoning about concurrency. -

Mac OS X Intro for UNIX Users
Mac OS X An Introduction for UNIX Users Leon Towns-von Stauber, Occam's Razor Seattle BSD Users Group, October 2004 http://www.occam.com/osx/ X Contents Opening Remarks.............................3 Where Did Mac OS X Come From?.....5 What is Mac OS X?..........................13 A New Kind of UNIX........................25 A Different Kind of UNIX.................28 Why Use Mac OS X?.........................60 Resources.......................................63 Closing Remarks.............................67 X Opening Remarks 3 This is a technical introduction to Mac OS X, mainly targeted to experienced UNIX users for whom OS X is at least relatively new Some emphasis on comparisons with FreeBSD I'm assuming basic familiarity with operating system design Where I'm coming from: UNIX user and some-time admin since 1990 Full-time UNIX admin since 1995 NeXTstep user and admin since 1991 This presentation covers primarily Mac OS X 10.3.5 (Darwin 7.5) X Legal Notices 4 This presentation Copyright © 2003-2004 Leon Towns-von Stauber. All rights reserved. Trademark notices Apple®, Mac®, Macintosh®, Mac OS®, Aqua®, Finder™, Quartz™, Cocoa®, Carbon®, AppleScript®, Rendezvous™, Panther™, and other terms are trademarks of Apple Computer. See <http:// www.apple.com/legal/appletmlist.html>. NeXT®, NeXTstep®, OpenStep®, and NetInfo® are trademarks of NeXT Software. See <http://www.apple.com/legal/nexttmlist.html>. PowerPC™ is a trademark of International Business Machines. Java™ is a trademark of Sun Microsystems. Other trademarks are the property of their -

A Brief History of Unix
A Brief History of Unix Tom Ryder [email protected] https://sanctum.geek.nz/ I Love Unix ∴ I Love Linux ● When I started using Linux, I was impressed because of the ethics behind it. ● I loved the idea that an operating system could be both free to customise, and free of charge. – Being a cash-strapped student helped a lot, too. ● As my experience grew, I came to appreciate the design behind it. ● And the design is UNIX. ● Linux isn’t a perfect Unix, but it has all the really important bits. What do we actually mean? ● We’re referring to the Unix family of operating systems. – Unix from Bell Labs (Research Unix) – GNU/Linux – Berkeley Software Distribution (BSD) Unix – Mac OS X – Minix (Intel loves it) – ...and many more Warning signs: 1/2 If your operating system shows many of the following symptoms, it may be a Unix: – Multi-user, multi-tasking – Hierarchical filesystem, with a single root – Devices represented as files – Streams of text everywhere as a user interface – “Formatless” files ● Data is just data: streams of bytes saved in sequence ● There isn’t a “text file” attribute, for example Warning signs: 2/2 – Bourne-style shell with a “pipe”: ● $ program1 | program2 – “Shebangs” specifying file interpreters: ● #!/bin/sh – C programming language baked in everywhere – Classic programs: sh(1), awk(1), grep(1), sed(1) – Users with beards, long hair, glasses, and very strong opinions... Nobody saw it coming! “The number of Unix installations has grown to 10, with more expected.” — Ken Thompson and Dennis Ritchie (1972) ● Unix in some flavour is in servers, desktops, embedded software (including Intel’s management engine), mobile phones, network equipment, single-board computers.. -
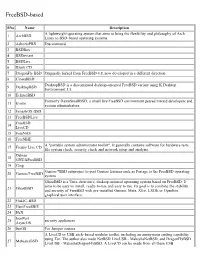
List of BSD Operating Systems
FreeBSD-based SNo Name Description A lightweight operating system that aims to bring the flexibility and philosophy of Arch 1 ArchBSD Linux to BSD-based operating systems. 2 AskoziaPBX Discontinued 3 BSDBox 4 BSDeviant 5 BSDLive 6 Bzerk CD 7 DragonFly BSD Originally forked from FreeBSD 4.8, now developed in a different direction 8 ClosedBSD DesktopBSD is a discontinued desktop-oriented FreeBSD variant using K Desktop 9 DesktopBSD Environment 3.5. 10 EclipseBSD Formerly DamnSmallBSD; a small live FreeBSD environment geared toward developers and 11 Evoke system administrators. 12 FenestrOS BSD 13 FreeBSDLive FreeBSD 14 LiveCD 15 FreeNAS 16 FreeSBIE A "portable system administrator toolkit". It generally contains software for hardware tests, 17 Frenzy Live CD file system check, security check and network setup and analysis. Debian 18 GNU/kFreeBSD 19 Ging Gentoo/*BSD subproject to port Gentoo features such as Portage to the FreeBSD operating 20 Gentoo/FreeBSD system GhostBSD is a Unix-derivative, desktop-oriented operating system based on FreeBSD. It aims to be easy to install, ready-to-use and easy to use. Its goal is to combine the stability 21 GhostBSD and security of FreeBSD with pre-installed Gnome, Mate, Xfce, LXDE or Openbox graphical user interface. 22 GuLIC-BSD 23 HamFreeSBIE 24 HeX IronPort 25 security appliances AsyncOS 26 JunOS For Juniper routers A LiveCD or USB stick-based modular toolkit, including an anonymous surfing capability using Tor. The author also made NetBSD LiveUSB - MaheshaNetBSD, and DragonFlyBSD 27 MaheshaBSD LiveUSB - MaheshaDragonFlyBSD. A LiveCD can be made from all these USB distributions by running the /makeiso script in the root directory. -

Recent Security Enhancements in Netbsd
Recent Security Enhancements in NetBSD Elad Efrat < [email protected] > September 2006 Abstract Over the years, NetBSD obtained the position of the BSD focusing on portability. While it is true that NetBSD offers an easily portable operating system, care is also given to other areas, such as security. This paper presents the NetBSD philosophy of security, design decisions, and currently offered security features. Finally, some of the current and future research will be revealed. 1. Introduction Running on almost twenty different architectures, and easily portable to others, NetBSD gained its reputation as the most portable operating system on the planet. While that may indicate high quality code, the ever demanding networked world cares about more than just that. Over the past year, NetBSD evolved quite a bit in various areas; this paper, however, will focus on the aspect relating to security. This paper was written and structured to present a full overview of the recent security enhancements in NetBSD in an easily readable and balanced form that will satisfy new, intermediate, and experienced users. References were sprinkled across the text to provide more information to those who want the gory details, while preserving the continuity. Section 2 will present the bigger picture of security in NetBSD: how NetBSD perceives security, the design decisions of NetBSD software in general and the security infrastructure and features more specifically. Section 3 will present a detailed overview of the recent enhancements in the security infrastructure and features of NetBSD including, where relevant, details about the design, implementation, and possible future development. Section 4 will present current security-related research and development in NetBSD, and section 5 will discuss how the described enhancements work together to provide a more secure platform. -

Mengenal Sistim Operasi *BSD
Mengenal Sistim Operasi *BSD Ada banyak sekali tulisan-tulisan yang membahas tentang BSD, baik tulisan mengenai sejarah, system administrasi, sampai penggunaan BSD kepada end-user sebagai desktop. Tulisan ini memperkenalkan BSD sebagai alternatif lain dari Linux untuk memenuhi kebutuhan akan UNIX-like operating system di Indonesia. Dalam tulisan ini pula, dibahas mengenai beberapa hal yang membedakan antara Linux dan BSD, namun tidak memutuskan mana yang paling baik, karena untuk menentukan mana operating system yang paling baik digunakan adalah Anda sendiri. Daftar Isi 1. Sejarah 2. Distribusi Varian BSD 3. Model Pengembangan 4. Integrasi System 5. Software-software di BSD 6. System Administrasi 7. File System 8. Lain-lain 9. Kesimpulan Sejarah Hampir semua orang telah mendengar Linux saat ini. Namun apa itu BSD? BSD adalah singkatan dari Berkeley Software Distribution. BSD pertama kali dibangun dan dikembangkan oleh Computer System Research Group (CSRG) di University of California at Berkeley (UCB), BSD pertama kali keluar pada akhir 1977 sebagai paket tambahan dan patch dari AT&T UNIX version 6, yang mana waktu itu beroperasi pada mesin PDP-11 minicomputer. BSD pada akhirnya banyak memberikan kontribusi berharga pada pengembangan UNIX secara umum. Ada banyak fitur yang pertama kali diperkenalkan oleh BSD dan beberapa diadopsi dari AT&T dan vendor-vendor lainnya. BSD dibuat, dikembangkan, dan digunakan secara BEBAS sebagai perlawanan terhadap lisensi UNIX yang dimiliki oleh AT&T dan oleh karena itu BSD mempunyai lisensi tersendiri yang memungkinkan setiap orang bebas melakukan pengembangan, dan menggunakan source code BSD. Pada tahun 1993, 4.4BSD dirilis sebagai sebuah Operating System yang utuh. Untuk sejarah lengkap BSD di CSRG, mulai sejarah dari jaman kuda, motivasi orang-orang yang pertama kali mengerjakannya, sampai perseteruan lisensi dan hak cipta dengan AT&T, saya mereferensikan Anda untuk membaca tulisan yang dibuat oleh Kirk McKusick, “Twenty Years of Berkeley Unix“. -

UNIX History Page 1 Tuesday, December 10, 2002 7:02 PM
UNIX History Page 1 Tuesday, December 10, 2002 7:02 PM CHAPTER 1 UNIX Evolution and Standardization This chapter introduces UNIX from a historical perspective, showing how the various UNIX versions have evolved over the years since the very first implementation in 1969 to the present day. The chapter also traces the history of the different attempts at standardization that have produced widely adopted standards such as POSIX and the Single UNIX Specification. The material presented here is not intended to document all of the UNIX variants, but rather describes the early UNIX implementations along with those companies and bodies that have had a major impact on the direction and evolution of UNIX. A Brief Walk through Time There are numerous events in the computer industry that have occurred since UNIX started life as a small project in Bell Labs in 1969. UNIX history has been largely influenced by Bell Labs’ Research Editions of UNIX, AT&T’s System V UNIX, Berkeley’s Software Distribution (BSD), and Sun Microsystems’ SunOS and Solaris operating systems. The following list shows the major events that have happened throughout the history of UNIX. Later sections describe some of these events in more detail. 1 UNIX History Page 2 Tuesday, December 10, 2002 7:02 PM 2 UNIX Filesystems—Evolution, Design, and Implementation 1969. Development on UNIX starts in AT&T’s Bell Labs. 1971. 1st Edition UNIX is released. 1973. 4th Edition UNIX is released. This is the first version of UNIX that had the kernel written in C. 1974. Ken Thompson and Dennis Ritchie publish their classic paper, “The UNIX Timesharing System” [RITC74]. -

Assessing Unikernel Security April 2, 2019 – Version 1.0
NCC Group Whitepaper Assessing Unikernel Security April 2, 2019 – Version 1.0 Prepared by Spencer Michaels Jeff Dileo Abstract Unikernels are small, specialized, single-address-space machine images constructed by treating component applications and drivers like libraries and compiling them, along with a kernel and a thin OS layer, into a single binary blob. Proponents of unikernels claim that their smaller codebase and lack of excess services make them more efficient and secure than full-OS virtual machines and containers. We surveyed two major unikernels, Rumprun and IncludeOS, and found that this was decidedly not the case: unikernels, which in many ways resemble embedded systems, appear to have a similarly minimal level of security. Features like ASLR, W^X, stack canaries, heap integrity checks and more are either completely absent or seriously flawed. If an application running on such a system contains a memory corruption vulnerability, it is often possible for attackers to gain code execution, even in cases where the applica- tion’s source and binary are unknown. Furthermore, because the application and the kernel run together as a single process, an attacker who compromises a unikernel can immediately exploit functionality that would require privilege escalation on a regular OS, e.g. arbitrary packet I/O. We demonstrate such attacks on both Rumprun and IncludeOS unikernels, and recommend measures to mitigate them. Table of Contents 1 Introduction to Unikernels . 4 2 Threat Model Considerations . 5 2.1 Unikernel Capabilities ................................................................ 5 2.2 Unikernels Versus Containers .......................................................... 5 3 Hypothesis . 6 4 Testing Methodology . 7 4.1 ASLR ................................................................................ 7 4.2 Page Protections .................................................................... -

Efficient Cache Attacks on AES, and Countermeasures
J. Cryptol. (2010) 23: 37–71 DOI: 10.1007/s00145-009-9049-y Efficient Cache Attacks on AES, and Countermeasures Eran Tromer Computer Science and Artificial Intelligence Laboratory, Massachusetts Institute of Technology, 32 Vassar Street, G682, Cambridge, MA 02139, USA [email protected] and Department of Computer Science and Applied Mathematics, Weizmann Institute of Science, Rehovot 76100, Israel Dag Arne Osvik Laboratory for Cryptologic Algorithms, Station 14, École Polytechnique Fédérale de Lausanne, 1015 Lausanne, Switzerland dagarne.osvik@epfl.ch Adi Shamir Department of Computer Science and Applied Mathematics, Weizmann Institute of Science, Rehovot 76100, Israel [email protected] Communicated by Lars R. Knudsen Received 20 July 2007 and revised 25 June 2009 Online publication 23 July 2009 Abstract. We describe several software side-channel attacks based on inter-process leakage through the state of the CPU’s memory cache. This leakage reveals memory access patterns, which can be used for cryptanalysis of cryptographic primitives that employ data-dependent table lookups. The attacks allow an unprivileged process to attack other processes running in parallel on the same processor, despite partitioning methods such as memory protection, sandboxing, and virtualization. Some of our meth- ods require only the ability to trigger services that perform encryption or MAC using the unknown key, such as encrypted disk partitions or secure network links. Moreover, we demonstrate an extremely strong type of attack, which requires knowledge of nei- ther the specific plaintexts nor ciphertexts and works by merely monitoring the effect of the cryptographic process on the cache. We discuss in detail several attacks on AES and experimentally demonstrate their applicability to real systems, such as OpenSSL and Linux’s dm-crypt encrypted partitions (in the latter case, the full key was recov- ered after just 800 writes to the partition, taking 65 milliseconds). -

MINIX3: a Reliable and Secure Operating System
MINIX3: A Reliable and Secure Operating System Andrew S. Tanenbaum and a team of students and programmers who actually did all the work Vrije Universiteit Amsterdam, The Netherlands 1 GOAL OF OUR WORK: BUILD A RELIABLE OS Tanenbaum’s definition of a reliable OS: “An operating system is said to be reliable when a typical user has never experienced even a single failure in his or her lifetime and does not know anybody who has ever experienced a failure.” In engineering terms, this is probably mean time to failure > 50 years I don’t think we are there yet 2 THE TELEVISION MODEL 1. You buy the television 2. You plug it in 3. It works perfectly for the next 10 years 3 THE COMPUTER MODEL (WINDOWS EDITION) 1. You buy the computer 2. You plug it in 3. You install service packs 1 through 9f 4. You install 18 new emergency security patches 5. You find and install 7 new device drivers 6. You install antivirus software 7. You install antispyware software 8. You install antihacker software (firewall) 9. You install antispam software 10. You reboot the computer 4 THE COMPUTER MODEL (2) 11. It doesn’t work 12. You call the helpdesk 13. You wait on hold for 30 minutes 14. They tell you to reinstall Windows 5 TYPICAL USER REACTION The New York Times recently reported that 25% of computer users have gotten so angry at their computer that they physically hit it. 6 IS RELIABILITY SO IMPORTANT? • Annoying • Lost work • But also think about – Industrial control systems in factories – Power grids – Hospital operating rooms – Banking and e-commerce servers – Emergency phone centers – Control software in cars, airplanes, etc. -

<[email protected]> Asiabsdcon 2012 Tokyo University of Science, Tokyo, Japan 22
<unnamed>: mpd304-L1-lt: mpd294-lso: mpd294-eso: mpd294-cso: mpd304-eso: mpd304-cso: ngctl306: ksocket [11]: tee [d]: socket [3]: socket [5]: socket [4]: socket [c]: socket [b]: socket [13]: <unnamed>: mpd304-lso: inet/dgram/udp left2right l2tp [f]: socket [a]: <unnamed>: lower ctrl l0 socket [e]: ctrl Introduction to NETGRAPH on FreeBSD Systems Dr. Adrian Steinmann <[email protected]> AsiaBSDCon 2012 Tokyo University of Science, Tokyo, Japan 22 – 25 March, 2012 Tutorial Materials Extended Abstract Tutorial Slides ʻAll About Netgraphʼ man 8 ngctl man 8 nghook man 4 netgraph About Myself Ph.D. in Mathematical Physics (long time ago) Webgroup Consulting AG (now) IT Consulting: Open Source, Security, Perl FreeBSD since version 1.0 (1993) NetBSD since version 3.0 (2005) Traveling, Sculpting, Go Tutorial Outline (1) Netgraph in a historical context (2) Getting to know netgraph (3) Working with netgraph (4) Details of frequently used netgraph node types (5) Examples using netgraph nodes as building blocks (6) Investigate some more sophisticated examples (7) Guidelines for implementing custom node types What is Netgraph Netgraph is in-kernel ‘network plumbing’ Drawn as a graph, a communication protocol can be seen as data packets flowing (bidirectionally) along the edges (lines) between nodes where the packets are processed. In FreeBSD since version 3.0 (2000) Created on FreeBSD 2.2 (1996) by Archie Cobbs <[email protected]> and Julian Elischer <[email protected]> for the Whistle InterJet at Whistle Communications, Inc. Ancient History Dennis Ritchie