SSL/TLS Vulnerabilities 02/25/2021
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Know Before You Go
Know Before You Go NORWAY A Guide to Keep You Safe Abroad provided by: Pathways to Safety International Updated May 2019 KNOW BEFORE YOU GO: NORWAY 2 Let’s be perfectly clear, the number one way to prevent sexual assault is to not rape. While the responsibility of ending sexual gender based violence is on the perpetrators, this guide will offer general safety tips, country-specific information, and resources to help prevent and prepare travelers for the possibility of sexual assault abroad. GENERAL SAFETY TIPS: 1. Use the buddy system and travel with friends. 7 out of 10 2. Be aware of social and cultural norms. For example, looking at someone in rapes are the eyes when you speak to them is perfectly normal in the U.S., but in committed another country that could signify you’re interested in the person. by someone known to the 3. Recognize controlling behavior when entering a relationship. Most rape 1 survivors recall feeling “uncomfortable” about some of their partner’s behaviors victim such as degrading jokes/language or refusal to accept “no” as an answer, whether in a sexual context or otherwise.2 4. Avoid secluded places where you could be more vulnerable. Meet new people in public spaces and let a trusted friend know where you’ll be beforehand. Always have a backup plan in mind. 5. Trust your gut. Many victims have a “bad feeling” right before an assault takes place. It’s okay to leave a situation that is making you feel uncomfortable. Stay alert and aware in new social settings and places. -

Alcatel-Lucent Security Advisory Sa0xx
Alcatel-Lucent Security Advisory No. SA0053 Ed. 04 Information about Poodle vulnerability Summary POODLE stands for Padding Oracle On Downgraded Legacy Encryption. The POODLE has been reported in October 14th 2014 allowing a man-in-the-middle attacker to decrypt ciphertext via a padding oracle side-channel attack. The severity is not considered as the same for Heartbleed and/or bash shellshock vulnerabilities. The official risk is currently rated Medium. The classification levels are: Very High, High, Medium, and Low. The SSLv3 protocol is only impacted while TLSv1.0 and TLSv1.2 are not. This vulnerability is identified CVE- 2014-3566. Alcatel-Lucent Enterprise voice products using protocol SSLv3 are concerned by this security alert. Openssl versions concerned by the vulnerability: OpenSSL 1.0.1 through 1.0.1i (inclusive) OpenSSL 1.0.0 through 1.0.0n (inclusive) OpenSSL 0.9.8 through 0.9.8zb (inclusive) The Alcatel-Lucent Enterprise Security Team is currently investigating implications of this security flaw and working on a corrective measure, for OpenTouch 2.1.1 planned in Q4 2015, to prevent using SSLv3 that must be considered as vulnerable. This note is for informational purpose about the padding-oracle attack identified as “POODLE”. References CVE-2014-3566 http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3566 Advisory severity CVSS Base score : 4.3 (MEDIUM) - AV:N/AC:M/Au:N/C:P/I:N/A:N https://www.openssl.org/news/secadv_20141015.txt https://www.openssl.org/~bodo/ssl-poodle.pdf Description of the vulnerabilities Information about Poodle vulnerability (CVE-2014-3566). -

SMTP Protocol
CS 280 Lecture 4: Application Layer, Email, DNS, P2P John Magee 21 September 2016 Most slides adapted from Kurose and Ross, Computer Networking 7/e Source material copyright 1996-2016 1 J.F Kurose and K.W. Ross Chapter 2: outline Last Class: 2.1 principles of network Next Class: applications 2.6 video streaming and 2.2 Web and HTTP content distribution networks Today: 2.7 socket programming with UDP and TCP 2.3 electronic mail • SMTP, POP3, IMAP 2.4 DNS 2.5 P2P applications Application Layer 2-2 outgoing Electronic mail message queue user mailbox Three major components: user agent . user agents . mail servers mail user server . simple mail transfer agent protocol: SMTP SMTP mail user server agent User Agent SMTP . a.k.a. “mail reader” SMTP user agent . composing, editing, reading mail server mail messages user . e.g., Outlook, Thunderbird, agent iPhone mail client user . outgoing, incoming agent messages stored on server Application Layer 2-3 Electronic mail: mail servers mail servers: user agent . mailbox contains incoming messages for user mail user server . message queue of outgoing agent (to be sent) mail messages SMTP mail user . SMTP protocol between server agent mail servers to send email SMTP messages SMTP user agent • client: sending mail mail server server • “server”: receiving mail user server agent user agent Application Layer 2-4 Electronic Mail: SMTP [RFC 2821] . uses TCP to reliably transfer email message from client to server, port 25 . direct transfer: sending server to receiving server . three phases of transfer • handshaking (greeting) • transfer of messages • closure . command/response interaction (like HTTP) • commands: ASCII text • response: status code and phrase . -

Statement from Directtrust Regarding the EFAIL Vulnerability
Statement from DirectTrust regarding the EFAIL Vulnerability Summary EFAIL is a set of attacks used to exploit vulnerabilities in email clients that decrypt and display PGP and S/MIME encrypted messages by coercing them into sending the decrypted text of the emails to an attacker. Properly implemented, Direct is NOT vulnerable. However, we recommend that if you are exchanging with anyone outside of the DirectTrust Network, you will want to understand at a reasonable depth how their implementation protects against EFAIL. How does EFAIL work? EFAIL consists of two different attack scenarios that create “backchannels” to send the decrypted text to an attacker. Both require an attacker to first obtain the encrypted message. 1. The attacker “wraps” the encrypted body with carefully crafted markup that can result in an email client decrypting the message and sending the decrypted body to the attacker. 2. The attacker manipulates the encrypted body of the message using well known S/MIME weaknesses that produce a message that can send the decrypted body to the attacker once rendered in the email client. Although the attacks are different, the end result is the same: a vulnerable email client sends the decrypted text to the attacker. How is this relevant to Direct? Direct uses S/MIME to encrypt messages, so in theory every Direct message could be vulnerable to this attack. However, Direct, when implemented correctly, is NOT vulnerable. The vulnerability is only applicable if decryption and rendering of the message are done in certain email clients like Thunderbird, iOS, Apple Mail, and some versions of Outlook. -

Cipher Support on a Citrix MPX/SDX (N3) Appliance
Cipher support on a Citrix MPX/SDX (N3) appliance The following table lists the support for different ciphers on SSL entities, such as virtual server, frontend, backend, and internal services. On an SDX appliance, if an SSL chip is assigned to a VPX instance, the cipher support of an MPX appliance applies. Otherwise, the normal cipher support of a VPX instance applies. From release 10.5 build 56.22, NetScaler MPX appliances support full hardware optimization for all ciphers. In earlier releases, part of ECDHE/DHE cipher optimization was done in software. Use the 'show hardware' command to identify whether your appliance has N3 chips. > sh hardware Platform: NSMPX-22000 16*CPU+24*IX+12*E1K+2*E1K+4*CVM N3 2200100 Manufactured on: 8/19/2013 CPU: 2900MHZ Host Id: 1006665862 Serial no: ENUK6298FT Encoded serial no: ENUK6298FT Done How to read the table Unless a build number is specified, a cipher suite is supported for all builds in a release. Example • 10.5, 11.0, 11.1, 12.0, 12.1, 13.0: All builds of 10.5, 11.0, 11.1, 12.0, 12.1, 13.0, releases. • 11.1, 12.0, 12.1, 13.0: All builds of 11.1, 12.0, 12.1, 13.0 releases. • 10.5-53.x and later, 11.0, 11.1, 12.0, 12.1, 13.0: Build 53.x and later in release 10.5. All builds of 11.0, 11.1, 12.0, 12.1, 13.0 releases. • NA: not applicable. Ciphersuite Name Hex Wireshark Ciphersuite Name Builds Builds Code Supported Supported (frontend) (backend) TLS1-AES-256-CBC-SHA 0x0035 TLS_RSA_WITH_AES_256_CB 10.5, 11.0, 10.5, 11.0, C_SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1-AES-128-CBC-SHA 0x002f -

Secure Shell- Its Significance in Networking (Ssh)
International Journal of Application or Innovation in Engineering & Management (IJAIEM) Web Site: www.ijaiem.org Email: [email protected] Volume 4, Issue 3, March 2015 ISSN 2319 - 4847 SECURE SHELL- ITS SIGNIFICANCE IN NETWORKING (SSH) ANOOSHA GARIMELLA , D.RAKESH KUMAR 1. B. TECH, COMPUTER SCIENCE AND ENGINEERING Student, 3rd year-2nd Semester GITAM UNIVERSITY Visakhapatnam, Andhra Pradesh India 2.Assistant Professor Computer Science and Engineering GITAM UNIVERSITY Visakhapatnam, Andhra Pradesh India ABSTRACT This paper is focused on the evolution of SSH, the need for SSH, working of SSH, its major components and features of SSH. As the number of users over the Internet is increasing, there is a greater threat of your data being vulnerable. Secure Shell (SSH) Protocol provides a secure method for remote login and other secure network services over an insecure network. The SSH protocol has been designed to support many features along with proper security. This architecture with the help of its inbuilt layers which are independent of each other provides user authentication, integrity, and confidentiality, connection- oriented end to end delivery, multiplexes encrypted tunnel into several logical channels, provides datagram delivery across multiple networks and may optionally provide compression. Here, we have also described in detail what every layer of the architecture does along with the connection establishment. Some of the threats which Ssh can encounter, applications, advantages and disadvantages have also been mentioned in this document. Keywords: SSH, Cryptography, Port Forwarding, Secure SSH Tunnel, Key Exchange, IP spoofing, Connection- Hijacking. 1. INTRODUCTION SSH Secure Shell was first created in 1995 by Tatu Ylonen with the release of version 1.0 of SSH Secure Shell and the Internet Draft “The SSH Secure Shell Remote Login Protocol”. -

Internet Security Threat Report VOLUME 21, APRIL 2016 TABLE of CONTENTS 2016 Internet Security Threat Report 2
Internet Security Threat Report VOLUME 21, APRIL 2016 TABLE OF CONTENTS 2016 Internet Security Threat Report 2 CONTENTS 4 Introduction 21 Tech Support Scams Go Nuclear, 39 Infographic: A New Zero-Day Vulnerability Spreading Ransomware Discovered Every Week in 2015 5 Executive Summary 22 Malvertising 39 Infographic: A New Zero-Day Vulnerability Discovered Every Week in 2015 8 BIG NUMBERS 23 Cybersecurity Challenges For Website Owners 40 Spear Phishing 10 MOBILE DEVICES & THE 23 Put Your Money Where Your Mouse Is 43 Active Attack Groups in 2015 INTERNET OF THINGS 23 Websites Are Still Vulnerable to Attacks 44 Infographic: Attackers Target Both Large and Small Businesses 10 Smartphones Leading to Malware and Data Breaches and Mobile Devices 23 Moving to Stronger Authentication 45 Profiting from High-Level Corporate Attacks and the Butterfly Effect 10 One Phone Per Person 24 Accelerating to Always-On Encryption 45 Cybersecurity, Cybersabotage, and Coping 11 Cross-Over Threats 24 Reinforced Reassurance with Black Swan Events 11 Android Attacks Become More Stealthy 25 Websites Need to Become Harder to 46 Cybersabotage and 12 How Malicious Video Messages Could Attack the Threat of “Hybrid Warfare” Lead to Stagefright and Stagefright 2.0 25 SSL/TLS and The 46 Small Business and the Dirty Linen Attack Industry’s Response 13 Android Users under Fire with Phishing 47 Industrial Control Systems and Ransomware 25 The Evolution of Encryption Vulnerable to Attacks 13 Apple iOS Users Now More at Risk than 25 Strength in Numbers 47 Obscurity is No Defense -
![[Hal-00744922, V1] Improving Content Availability in the I2P Anonymous](https://docslib.b-cdn.net/cover/4228/hal-00744922-v1-improving-content-availability-in-the-i2p-anonymous-324228.webp)
[Hal-00744922, V1] Improving Content Availability in the I2P Anonymous
Improving Content Availability in the I2P Anonymous File-Sharing Environment Juan Pablo Timpanaro, Isabelle Chrisment*, Olivier Festor INRIA Nancy-Grand Est, France *LORIA - ESIAL, Universit´ede Lorraine Email: fjuanpablo.timpanaro, [email protected] Email: [email protected] Abstract. Anonymous communication has gained more and more inter- est from Internet users as privacy and anonymity problems have emerged. Dedicated anonymous networks such as Freenet and I2P allow anony- mous file-sharing among users. However, one major problem with anony- mous file-sharing networks is that the available content is highly reduced, mostly with outdated files, and non-anonymous networks, such as the BitTorrent network, are still the major source of content: we show that in a 30-days period, 21648 new torrents were introduced in the BitTor- rent community, whilst only 236 were introduced in the anonymous I2P network, for four different categories of content. Therefore, how can a user of these anonymous networks access this varied and non-anonymous content without compromising its anonymity? In this paper, we improve content availability in an anonymous environment by proposing the first internetwork model allowing anonymous users to access and share content in large public communities while remaining anonymous. We show that our approach can efficiently interconnect I2P users and public BitTorrent swarms without affecting their anonymity nor their performance. Our model is fully implemented and freely usable. 1 Introduction Peer-to-peer file-sharing has always been one of the major sources of the Internet hal-00744922, version 1 - 24 Oct 2012 traffic, since its early beginnings in 2000. It has been moving from semi-central approaches (eDonkey2000, for example), to semi-decentralized approaches (Kazaa, for instance) to fully decentralized file-sharing architectures (like the KAD net- work). -

<Document Title>
TLS Specification for Storage Systems Version 1.0.1 ABSTRACT: This document specifies the requirements and guidance for use of the Transport Layer Security (TLS) protocol in conjunction with data storage technologies. The requirements are intended to facilitate secure interoperability of storage clients and servers as well as non-storage technologies that may have similar interoperability needs. This document was developed with the expectation that future versions of SMI-S and CDMI could leverage these requirements to ensure consistency between these standards as well as to more rapidly adjust the security functionality in these standards. This document has been released and approved by the SNIA. The SNIA believes that the ideas, methodologies and technologies described in this document accurately represent the SNIA goals and are appropriate for widespread distribution. Suggestion for revision should be directed to http://www.snia.org/feedback/. SNIA Technical Position November 20, 2014 USAGE The SNIA hereby grants permission for individuals to use this document for personal use only, and for corporations and other business entities to use this document for internal use only (including internal copying, distribution, and display) provided that: 1. Any text, diagram, chart, table or definition reproduced shall be reproduced in its entirety with no alteration, and, 2. Any document, printed or electronic, in which material from this document (or any portion hereof) is reproduced shall acknowledge the SNIA copyright on that material, and shall credit the SNIA for granting permission for its reuse. Other than as explicitly provided above, you may not make any commercial use of this document, sell any or this entire document, or distribute this document to third parties. -

Combat Top Security Vulnerabilities: HPE Tippingpoint Intrusion
Business white paper Combat top security vulnerabilities HPE TippingPoint intrusion prevention system Business white paper Page 2 The year 2014 marked a new pinnacle for hackers. Vulnerabilities were uncovered in some of the most widely deployed software in the world—some of it in systems actually intended to make you more secure. HPE TippingPoint next-generation intrusion prevention system (IPS) and next-generation firewall (NGFW) customers rely on us to keep their networks safe. And when it comes to cyber threats, every second matters. So how did HPE TippingPoint do? This brief highlights the top security vulnerabilities of 2014—the ones that sent corporate security executives scrambling to protect their businesses. And it describes how HPE TippingPoint responded to keep our customers safe. Heartbleed—HPE TippingPoint intrusion prevention system stops blood flow early Any vulnerability is concerning, but when a vulnerability is discovered in software designed to assure security, it leaves businesses exposed and vulnerable. That was the case with the Heartbleed vulnerability disclosed by the OpenSSL project on April 7, 2014. They found the vulnerability in versions of OpenSSL—the open-source cryptographic library widely used to encrypt Internet traffic. Heartbleed grew from a coding error that allowed remote attackers to read information from process memory by sending heartbeat packets that trigger a buffer over-read. As a demonstration of the vulnerability, the OpenSSL Project created a sample exploit that successfully stole private cryptography keys, user names and passwords, instant messages, emails, and business-critical documents and communications. We responded within hours to protect TippingPoint customers. On April 8, we released a custom filter package to defend against the vulnerability. -
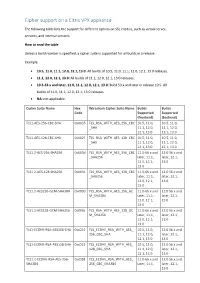
Cipher Support on a Citrix ADC VPX Appliance
Cipher support on a Citrix VPX appliance The following table lists the support for different ciphers on SSL entities, such as virtual server, services, and internal services. How to read the table Unless a build number is specified, a cipher suite is supported for all builds in a release. Example • 10.5, 11.0, 11.1, 12.0, 12.1, 13.0: All builds of 10.5, 11.0, 11.1, 12.0, 12.1, 13.0 releases. • 11.1, 12.0, 12.1, 13.0: All builds of 11.1, 12.0, 12.1, 13.0 releases. • 10.5-53.x and later, 11.0, 11.1, 12.0, 12.1, 13.0: Build 53.x and later in release 10.5. All builds of 11.0, 11.1, 12.0, 12.1, 13.0 releases. • NA: not applicable. Cipher Suite Name Hex Wireshark Cipher Suite Name Builds Builds Code Supported Supported (frontend) (backend) TLS1-AES-256-CBC-SHA 0x0035 TLS_RSA_WITH_AES_256_CBC 10.5, 11.0, 10.5, 11.0, _SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1-AES-128-CBC-SHA 0x002f TLS_RSA_WITH_AES_128_CBC 10.5, 11.0, 10.5, 11.0, _SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1.2-AES-256-SHA256 0x003d TLS_RSA_WITH_AES_256_CBC 11.0-66.x and 12.0 56.x and _SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES-128-SHA256 0x003c TLS_RSA_WITH_AES_128_CBC 11.0-66.x and 12.0 56.x and _SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES256-GCM-SHA384 0x009d TLS_RSA_WITH_AES_256_GC 11.0-66.x and 12.0 56.x and M_SHA384 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES128-GCM-SHA256 0x009c TLS_RSA_WITH_AES_128_GC 11.0-66.x and 12.0 56.x and M_SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1-ECDHE-RSA-AES256-SHA -

Tracking Users Across the Web Via TLS Session Resumption
Tracking Users across the Web via TLS Session Resumption Erik Sy Christian Burkert University of Hamburg University of Hamburg Hannes Federrath Mathias Fischer University of Hamburg University of Hamburg ABSTRACT modes, and browser extensions to restrict tracking practices such as User tracking on the Internet can come in various forms, e.g., via HTTP cookies. Browser fingerprinting got more difficult, as trackers cookies or by fingerprinting web browsers. A technique that got can hardly distinguish the fingerprints of mobile browsers. They are less attention so far is user tracking based on TLS and specifically often not as unique as their counterparts on desktop systems [4, 12]. based on the TLS session resumption mechanism. To the best of Tracking based on IP addresses is restricted because of NAT that our knowledge, we are the first that investigate the applicability of causes users to share public IP addresses and it cannot track devices TLS session resumption for user tracking. For that, we evaluated across different networks. As a result, trackers have an increased the configuration of 48 popular browsers and one million of the interest in additional methods for regaining the visibility on the most popular websites. Moreover, we present a so-called prolon- browsing habits of users. The result is a race of arms between gation attack, which allows extending the tracking period beyond trackers as well as privacy-aware users and browser vendors. the lifetime of the session resumption mechanism. To show that One novel tracking technique could be based on TLS session re- under the observed browser configurations tracking via TLS session sumption, which allows abbreviating TLS handshakes by leveraging resumptions is feasible, we also looked into DNS data to understand key material exchanged in an earlier TLS session.