Azure Privileged Identity Management- Adoption Kit
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Introducing Windows Azure for IT Professionals
Introducing Windows ServerIntroducing Release 2012 R2 Preview Introducing Windows Azure For IT Professionals Mitch Tulloch with the Windows Azure Team PUBLISHED BY Microsoft Press A Division of Microsoft Corporation One Microsoft Way Redmond, Washington 98052-6399 Copyright © 2013 Microsoft Corporation All rights reserved. No part of the contents of this book may be reproduced or transmitted in any form or by any means without the written permission of the publisher. Library of Congress Control Number: 2013949894 ISBN: 978-0-7356-8288-7 Microsoft Press books are available through booksellers and distributors worldwide. If you need support related to this book, email Microsoft Press Book Support at [email protected]. Please tell us what you think of this book at http://www.microsoft.com/learning/booksurvey. Microsoft and the trademarks listed at http://www.microsoft.com/about/legal/en/us/IntellectualProperty/ Trademarks/EN-US.aspx are trademarks of the Microsoft group of companies. All other marks are property of their respective owners. The example companies, organizations, products, domain names, email addresses, logos, people, places, and events depicted herein are fictitious. No association with any real company, organization, product, domain name, email address, logo, person, place, or event is intended or should be inferred. This book expresses the author’s views and opinions. The information contained in this book is provided without any express, statutory, or implied warranties. Neither the authors, Microsoft Corporation, nor -

Chris Ford Astronomy Visualizations
Vol. 55, No. 8 – August 2007 September 19, 2007 – General Meeting 7:00 pm Doors Open . 7:30 pm Announcements . 8:00 pm Speaker CHRIS FORD PIXAR ANIMATION STUDIOS’ RENDERMAN BUSINESS DIRECTOR ASTRONOMY VISUALIZATIONS Astronomy and the art of astronomical visualization have always been closely linked. The traditional paintings of artists such as Chesley Bonestell, Don Dixon, or Ron Miller are well known and have educated and inspired millions. Since the early 1980's, traditional techniques of illustration have increasingly been replaced as a medium of education by computer generated imagery. (CG) This process has advanced to the point that is now rare to see traditional paintings in the astronomical media. The additional dimension of animation also broadens the visual possibilities available to communicate the latest data and research. The increasingly photo-realistic quality of the CG medium has largely been driven by the demands of Hollywood computer generated special effects and animation. The same technology used to create alien landscapes in Star Wars or Star Trek can just as easily be used to interpret real scientific data in a manner that both explains and entertains. Today it is now possible to create astronomical simulations from scientific data that are so photo-realistic that in immersive projection environments such as Imax, it is possible to believe you are "really there". Chris Ford is currently the RenderMan Business DIrector at Pixar Animation Studios and over his career has managed some of the most important CG software tools used in photo-realistic CG astronomical visualization including Maya, 3ds max, Dynamation, and RenderMan. -

Group Tour Manual
Group Tour GUIDE 1 5 17 33 36 what's inside 1 WELCOME 13 FUN FACTS – (ESCORT NOTES) 2 WEATHER INFORMATION 17 ATTRACTIONS 3 GROUP TOUR SERVICES 30 SIGHTSEEING 5 TRANSPORTATION INFORMATION 32 TECHNICAL TOURS Airport 35 PARADES Motorcoach Parking – Policies 36 ANNUAL EVENTS Car Rental Metro & Trolley 37 SAMPLE ITINERARIES 7 MAPS Central Corridor Metro Forest Park Downtown welcome St. Louis is a place where history and imagination collide, and the result is a Midwestern destination like no other. In addition to a revitalized downtown, a vibrant, new hospitality district continues to grow in downtown St. Louis. More than $5 billion worth of development has been invested in the region, and more exciting projects are currently underway. The Gateway to the West offers exceptional music, arts and cultural options, as well as such renowned – and free – attractions as the Saint Louis Art Museum, Zoo, Science Center, Missouri History Museum, Citygarden, Grant’s Farm, Laumeier Sculpture Park, and the Anheuser-Busch brewery tours. Plus, St. Louis is easy to get to and even easier to get around in. St. Louis is within approximately 500 miles of one-third of the U.S. population. Each and every new year brings exciting additions to the St. Louis scene – improved attractions, expanded attractions, and new attractions. Must See Attractions There’s so much to see and do in St. Louis, here are a few options to get you started: • Ride to the top of the Gateway Arch, towering 630-feet over the Mississippi River. • Visit an artistic oasis in the heart of downtown. -

JAVASCRIPT TRANSPILERI Završni Rad
SVEUČILIŠTE JOSIPA JURJA STROSSMAYERA U OSIJEKU FAKULTET ELEKTROTEHNIKE, RAČUNARSTVA I INFORMACIJSKIH TEHNOLOGIJA Preddiplomski studij JAVASCRIPT TRANSPILERI Završni rad Zvonimir Grubišić Osijek, 2017 Obrazac Z1P - Obrazac za ocjenu završnog rada na preddiplomskom sveučilišnom studiju Osijek, 23.09.2018. Odboru za završne i diplomske ispite Prijedlog ocjene završnog rada Ime i prezime studenta: Zvonimir Grubišić Studij, smjer: Preddiplomski sveučilišni studij Računarstvo Mat. br. studenta, godina upisa: R3637, 29.09.2017. OIB studenta: 50946540896 Mentor: Izv. prof. dr. sc. Irena Galić Sumentor: Hrvoje Leventić Sumentor iz tvrtke: Naslov završnog rada: Javascript transpileri Znanstvena grana rada: Programsko inženjerstvo (zn. polje računarstvo) Predložena ocjena završnog rada: Izvrstan (5) Primjena znanja stečenih na fakultetu: 3 bod/boda Kratko obrazloženje ocjene prema Postignuti rezultati u odnosu na složenost zadatka: 3 bod/boda Kriterijima za ocjenjivanje završnih i Jasnoća pismenog izražavanja: 3 bod/boda diplomskih radova: Razina samostalnosti: 3 razina Datum prijedloga ocjene mentora: 23.09.2018. Datum potvrde ocjene Odbora: 26.09.2018. Potpis: Potpis mentora za predaju konačne verzije rada u Studentsku službu pri završetku studija: Datum: IZJAVA O ORIGINALNOSTI RADA Osijek, 01.10.2018. Ime i prezime studenta: Zvonimir Grubišić Studij: Preddiplomski sveučilišni studij Računarstvo Mat. br. studenta, godina upisa: R3637, 29.09.2017. Ephorus podudaranje [%]: 1% Ovom izjavom izjavljujem da je rad pod nazivom: Javascript transpileri izrađen pod vodstvom mentora Izv. prof. dr. sc. Irena Galić i sumentora Hrvoje Leventić moj vlastiti rad i prema mom najboljem znanju ne sadrži prethodno objavljene ili neobjavljene pisane materijale drugih osoba, osim onih koji su izričito priznati navođenjem literature i drugih izvora informacija. Izjavljujem da je intelektualni sadržaj navedenog rada proizvod mog vlastitog rada, osim u onom dijelu za koji mi je bila potrebna pomoć mentora, sumentora i drugih osoba, a što je izričito navedeno u radu. -

Presentazione Standard Di Powerpoint
ARGOMENTO 1 ARGOMENTO Secrets safe and centralize with Azure KeyVault and Azure App Configuration! «My name is Bonanni, Massimo Bonanni» 2 Azure Key Vault is a service that enables you to store & manage cryptographic keys and secrets in one central secure vault!! The doubts of the Developers and IT Pros!! I don't want the I want customers to own and responsibility or potential manage their keys so that I liability for my customers' can concentrate on doing tenant keys and secrets. what I do best, which is providing the core software features. I want to write an application for Azure that uses keys for signing and I want to make sure that encryption. But I want my organization is in these keys to be external control of the key from my application. lifecycle and can monitor key usage. Azure KeyVault key features Key Management Certificate Store secrets Secrets Management backed by Management Hardware Security Azure Key Vault can also be used as a Key Azure Key Vault lets you Modules Azure Key Vault can be Management solution. easily provision, manage, used to Securely store Azure Key Vault makes it and deploy public and and tightly control access easy to create and private Transport Layer The secrets and keys can to tokens, passwords, control the encryption Security/Secure Sockets be protected either by certificates, API keys, and keys used to encrypt your Layer (TLS/SSL) software or FIPS 140-2 other secrets data. certificates. Level 2 validated HSMs Azure KeyVault actors Vault Custodian Vault Consumer • Can create a key vault and • A vault consumer can gain full access and control perform actions on the over it. -

Becker Collegeâ•Žs Agile Mindset Is Enhanced by Microsoft Technol
This site uses cookies for analytics, personalized content and ads. By continuing to browse this site, you agree to this use. Learn more Microsoft 365 Azure All Microsoft Office 365 Dynamics 365 Cart SQL Search Windows 10 Becker College’s Agile Mindset is enhanced by Microsoft Customer Technology BECKER COLLEGE Partner August 10, 2018 Live Tiles Products and Services Azure Machine Learning Office 365 SharePoint Online Industry Higher Education Organization Size Medium (50 - 999 employees) Country United States Share this story © 2017 Microsoft Becker College is a small, distinctive institution in central Massachusetts that is ranked by the Princeton Review as the #4 school in the world for interactive media and game design, and with a #6 ranked Master of Fine Arts in Interactive Media. With more than 600 students enrolled in the program out of the approximately 1,800 students across its 2 campuses (Worcester and Leicester, Mass.), Becker is considered to be one of the largest game design schools in the world. Becker College might sound like just another high- achieving, East Coast college, destined to be successful because it attracts the best of the best students, but in reality, what attracts students to Becker is something much different than what they can expect from other schools—an Agile Mindset and curriculum approach. How the Agile Mindset is integrated into coursework Alan Ritacco, Dean of the School of Design and Technology, says, “I think what draws students to Becker College is that we’re a small school that can impact students in a large way.” Ritacco says there are four key components to the Agile Mindset required for every student at Becker, regardless of school or major. -

Plugged in Wires—And That’S When We Got the Com- Ment
being unconnected for five days of camp- ALUMNI ing. “In Yellowstone we were completely cut o≠, not even a cell-phone signal,” she says. The hotel o≠ered the chance to “to- tally geek out for an hour with all of our Plugged In wires—and that’s when we got the com- ment. Some people may look at how con- nected my family and I are as a negative, Networking with a digital-age provocateur that we don’t interact with ‘real’ people. But technology actually enables me to be more connected, to reach out beyond my daily work, home, and school routines “We gave ourselves an and connect with people I know in unex- hour of quality Wi-Fi pected ways.” time,” says Charlene Li This new wave of technological social- of a recent hotel stop on a family vacation. izing, of having hundreds—or thou- sands—of “friends” (the very definition is shifting), of sharing personal informa- tion more freely, of “being connected” 24/7, tends to push people’s boundaries. And that’s part of Li’s purpose; she is something of a digital-age provocateur in geek’s clothing. Li first made a name for herself as a marketing analyst at Forrester Research Inc., where she covered media and tech- nology; she has followed Google and Yahoo! from their inceptions. She was among the first analysts to push for and get her own company blog (in 2004), through which she dispensed news and analysis of current events, promoted re- ports, answered press questions, and n a recent trip to Yellow- At the campsite, the octopus of elec- communed with current and prospective stone National Park, Char- tronics was left in the car—virtually un- clients—all of which established her pro- lene Li ’88, M.B.A. -
Microsoft from Wikipedia, the Free Encyclopedia Jump To: Navigation, Search
Microsoft From Wikipedia, the free encyclopedia Jump to: navigation, search Coordinates: 47°38′22.55″N 122°7′42.42″W / 47.6395972°N 122.12845°W / 47.6395972; -122.12845 Microsoft Corporation Public (NASDAQ: MSFT) Dow Jones Industrial Average Type Component S&P 500 Component Computer software Consumer electronics Digital distribution Computer hardware Industry Video games IT consulting Online advertising Retail stores Automotive software Albuquerque, New Mexico Founded April 4, 1975 Bill Gates Founder(s) Paul Allen One Microsoft Way Headquarters Redmond, Washington, United States Area served Worldwide Key people Steve Ballmer (CEO) Brian Kevin Turner (COO) Bill Gates (Chairman) Ray Ozzie (CSA) Craig Mundie (CRSO) Products See products listing Services See services listing Revenue $62.484 billion (2010) Operating income $24.098 billion (2010) Profit $18.760 billion (2010) Total assets $86.113 billion (2010) Total equity $46.175 billion (2010) Employees 89,000 (2010) Subsidiaries List of acquisitions Website microsoft.com Microsoft Corporation is an American public multinational corporation headquartered in Redmond, Washington, USA that develops, manufactures, licenses, and supports a wide range of products and services predominantly related to computing through its various product divisions. Established on April 4, 1975 to develop and sell BASIC interpreters for the Altair 8800, Microsoft rose to dominate the home computer operating system (OS) market with MS-DOS in the mid-1980s, followed by the Microsoft Windows line of OSes. Microsoft would also come to dominate the office suite market with Microsoft Office. The company has diversified in recent years into the video game industry with the Xbox and its successor, the Xbox 360 as well as into the consumer electronics market with Zune and the Windows Phone OS. -

Deploying a CMS to Azure – What You Need to Know!
Deploying a CMS To Azure: What you need to know! Bryan Soltis Kentico Technical Evangelist Deploying Your CMS To Azure Agenda • Hosting • Storage • Supporting Configurations • Integrations • Traffic Management • Scaling / Performance • Tips • Learn More Deploying Your CMS To Azure Hosting • Web • Cloud Services (PaaS) • Virtual Machines (IaaS) • Web Apps • Mobile Services • Hybrid solutions • Database • Azure Database • Sizes / Price • VM Image • Firewalls • Backups Deploying Your CMS To Azure Hosting Deploying Your CMS To Azure Storage • Configuration • Location • Geo-replication • REST Services • CDN • TTL • Security • Shared Access Signatures (SAS) • Media • Table Storage • Tools • Azure Storage Explorer • CloudBerry Deploying Your CMS To Azure Supporting Configurations • Session • InProc vs SQL Server vs Hosted • REDIS Cache • SMTP • SendGrid • Search • Azure Search • Authentication • Web Apps • Active Directory Deploying Your CMS To Azure Integrations • CRMs • ERPs • Virtual Networks • Web Apps • Mobile Services • REST service • Machine Learning • TFS / GitHub Deploying Your CMS To Azure Traffic Management • Routing options • Failover • Performance • Round Robin • Load Balancing • Swap VIP • Database replication Deploying Your CMS To Azure Scaling & Performance • CPU Utilization • Scheduled • Licensing • Limits • Endpoint Monitoring Deploying Your CMS To Azure Random Tips • Start with Web Apps, then find a reason • Consider using Table Storage for non- not to use them relational data • Use Azure Configuration files for cloud • Be -
Recommended Resources Microsoft Platform Platform Resources Github Channel 9 Microsoft Graph Microsoft Graph Microsoft Graph St
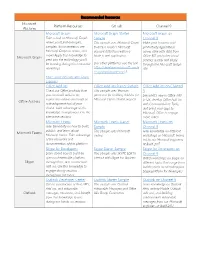
Recommended Resources Microsoft Platform Resources GitHub Channel 9 Platform Microsoft Graph Microsoft Graph Starter Microsoft Graph on Take a look at Microsoft Graph Sample Channel 9 where you’ll find examples, This sample uses Microsoft Graph Make your business and samples, documentation, see to access a user’s Microsoft productivity applications Microsoft Graph in action, and account data from within a comes alive with data from more! Apply this knowledge to Microsoft Graph Node.js web application. Office 365 and other cloud peek into the technology you’ll services quickly and easily be learning during the interactive [For other platforms; use this link: through the Microsoft Graph workshops https://developer.microsoft.com/e API. n-us/graph/quick-start ] Make some API calls with Graph Explorer! Office Add-ins Office Add-ins Starter Sample Office Add-ins on Channel Check out Office products that This sample uses Yeoman 9 you can build add-ins on, generator for building Add-ins for See what’s new in Office add- explore the add-in and build on Microsoft Office related projects Office Add-ins in UX, develop Office Add-ins a development tool of your with Command-Line Tools, choice. Take advantage of this and bring your apps to knowledge to implement it to the Microsoft Office to engage interactive sessions more users! Microsoft Teams Microsoft Teams Starter Microsoft Teams on Gain familiarity on how to build, Sample Channel 9 publish, and learn about Microsoft Teams This sample uses Microsoft Gain knowledge on different Microsoft teams. Take advantage Teams workshops on Microsoft Teams of the resources and led by our Microsoft engineers documentation of this platform at Build 2017 Skype for Developers Skype Starter Sample Skype for Developers on Learn about how to build an This sample uses SKYPE SDK to Channel 9 open and extensible platform interact with Skype For Business Watch workshops on Skype on Skype through bots, web control and different topics that range from add-ins. -

RA FSP MQTT/TLS Azure Cloud Connectivity Solution Application
Application Note Renesas RA FSP™ Platform RA FSP MQTT/TLS Azure Cloud Connectivity Solution Introduction This application note describes IoT Cloud connectivity solutions in general and introduces you briefly to the IoT Cloud provider Microsoft Azure. It covers the RA FSP MQTT/TLS module along with the Azure IoT SDK for embedded C. This application project is built with the integrated “Azure IoT SDK for Embedded C” package which allows small embedded (IoT) devices like Renesas RA family of MCUs RA6M3/4/5 to communicate with Azure services. The application example uses Azure IoT DPS (Device Provisioning Service ) to provision, register the IoT device, and send and receive data to and from the development kit. This application note enables you to effectively use the RA FSP modules in your own design with the Azure IoT SDK. Upon completion of this guide, you will be able to add the FSP modules to your own design, configure it correctly with Azure IoT SDK for the target application, and write code using the included application example code as a reference and efficient starting point. References to more detailed API descriptions, and sample code that demonstrates advanced usage of FSP modules are available in the RA FSP Software Package (FSP) User’s Manual (see Next Steps section) and serve as valuable resources in creating more complex designs. Explaining the underlying operation of Azure IoT SDK for Embedded C is beyond the scope of this document. Users are recommended to refer to the documentation from Microsoft for education on topics related to Azure IoT SDK section https://docs.microsoft.com/en-us/azure/iot-hub/iot-hub- devguide-sdks In this release, the EK-RA6M5 kit is used for the application project. -

Reflection in the .NET Framework
Mastering C# and .NET Framework Deep dive into C# and .NET architecture to build efficient, powerful applications Marino Posadas BIRMINGHAM - MUMBAI Mastering C# and .NET Framework Copyright © 2016 Packt Publishing All rights reserved. No part of this book may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, without the prior written permission of the publisher, except in the case of brief quotations embedded in critical articles or reviews. Every effort has been made in the preparation of this book to ensure the accuracy of the information presented. However, the information contained in this book is sold without warranty, either express or implied. Neither the author, nor Packt Publishing, and its dealers and distributors will be held liable for any damages caused or alleged to be caused directly or indirectly by this book. Packt Publishing has endeavored to provide trademark information about all of the companies and products mentioned in this book by the appropriate use of capitals. However, Packt Publishing cannot guarantee the accuracy of this information. First published: December 2016 Production reference: 1091216 Published by Packt Publishing Ltd. Livery Place 35 Livery Street Birmingham B3 2PB, UK. ISBN 978-1-78588-437-5 www.packtpub.com Credits Author Project Coordinator Marino Posadas Izzat Contractor Reviewers Proofreader Fabio Claudio Ferracchiati Safis Editing Commissioning Editor Indexer Edward Gordon Rekha Nair Acquisition Editor Graphics Denim Pinto Disha Haria Content Development Editor Production Coordinator Priyanka Mehta Aparna Bhagat Technical Editor Cover Work Dhiraj Chandanshive Aparna Bhagat Copy Editor Stuti Srivastava About the Author Marino Posadas is an independent senior trainer, writer, and consultant in Microsoft Technologies and Web Standards.