OAKS Online Technical Specifications for System Administrators 2012-2013
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Grapher 12 Quick Start Guide
GrapherTM Registration Information Your Grapher serial number is located on the CD cover or in the email download instructions, depending on how you purchased Grapher. Register your Grapher serial number online at www.GoldenSoftware.com. This information will not be redistributed. Registration entitles you to free technical support, free minor updates, and upgrade pricing on future Grapher releases. The serial number is required when you run Grapher the first time, contact technical support, or purchase Grapher upgrades. For future reference, write your serial number on the line below. _________________________________ GrapherTM Quick Start Guide The Ultimate Technical Graphing Package Golden Software, LLC 809 14th Street, Golden, Colorado 80401-1866, U.S.A. Phone: 303-279-1021 Fax: 303-279-0909 www.GoldenSoftware.com COPYRIGHT NOTICE Copyright Golden Software, LLC 2016 The GrapherTM program is furnished under a license agreement. The Grapher software and quick start guide may be used or copied only in accordance with the terms of the agreement. It is against the law to copy the software or quick start guide on any medium except as specifically allowed in the license agreement. Contents are subject to change without notice. Grapher is a registered trademark of Golden Software, LLC. All other trademarks are the property of their respective owners. March 2016 Quick Start Guide Table of Contents Introduction to Grapher ......................................................................................1 System Requirements ........................................................................................2 -
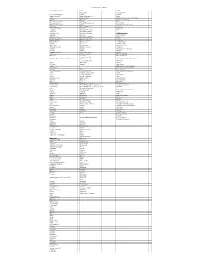
Software List (1-3-2017)
Software List (1-3-2017) Information Commons BU 104 LLCD Adobe Flash Academic online JVC Pro HD Manager Chrome Acrobat Adobe Reader DC Adobe Photoshop CS6 Adobe Itunes Adobe Reader XI Comprehensive Medical Terminology Maple 16 Drive M:\ Glencoe Keyboarding Microsoft Office 2016 Firefox Itunes Microsoft Publisher Irwin/GDP Keyboarding Kurzeil 3000 MS visual studio 2015 Itunes Microsoft Office Suite 2007 Quicktime Kurzweil 3000 v.12 Quick time SPSS for Windows Maple 16 Skills bank real player Microsoft Office 2016 Vista 3-Scanners MS platform installer Windows 7 & 10 Microsoft Visio 2016 Wellington Center sharepoint MS SQL Internet Explorer XPS viewer MS Visual Studio 2015 ITunes Express for desktop Quicken deluxe 2014 McAfee Express for Web VLC Media Player Quicktime MS silverlight Windows 10 " " Media Player Statdisk Scanner Mozilla Firefox Skype 2016 MS silverlight Adobe Reader XI windows dvd maker wolfram cdf player Windows 8 Onedrive Filezilla Microsoft Office Suite 2013 notepad++ Gimp 2 Maple 16 respounds/lockdown opera mobile emulator Statdisk 3D builder VM ware/ vsphere Wolfram CDF Player MS Azure wire shark VLC Media Player cisco packet tracker MACS Software (Information Commons) 3D builder Brunswick Front Desk Computers java development kit Windows 7 System project 2016 Adobe 9 Developer notepad++ Apple Itunes Utilities IBM Iseries access for windows Time Machine Intel Management and Security TextEdit UC 222 Iseries navigator System Preferences Acrobat Reader XI Malware Bytes Anti Malware Stickies Adult Clinical Simulation Mcaffe -

Getting Started a Guide for Your Apple Mobile Learning Lab Contents
Getting Started A guide for your Apple Mobile Learning Lab Contents Introduction 1 Setting Up and Working with Your Mobile Lab 3 Setting Up Your Mobile Lab 3 Daily Setup 6 Sharing the Mobile Lab 9 Creating and Managing User Accounts 9 Installing Software 11 Sharing and Storing Files 14 Apple Remote Desktop: Managing Student Computers from One Computer 15 Using Parental Controls to Provide Extra Security 16 Maintaining Your Mobile Lab 17 Using the Tools That Come with Your Mobile Lab 20 Using iChat AV to Communicate and Collaborate with Video, Audio, and Text 20 Having Instant Access to Information with Widgets 22 Finding Files in a Flash with Spotlight 23 Crunching Numbers with Calculator and Grapher 24 Browsing the Internet with Safari 25 Staying Up to Date with iCal 27 Producing Digital Media Projects with iLife 28 Creating Digital Stories with iMovie 29 Creating Digital Music and Recording Audio with GarageBand 30 Organizing, Editing, and Sharing Digital Photos with iPhoto 32 Building Websites with Photos, Movies, Podcasts, and Text with iWeb 34 Organizing and Playing Music and Audio with iTunes 36 Reaching All Learners with Built-in Accessibility Features 37 Communicating via Email with Mail 38 Supporting Writing with Dictionary and TextEdit 39 Getting Started: A guide for your Apple Mobile Learning Lab II Contents More Tools to Use with Your Mobile Lab 40 Increasing Student Achievement with the Apple Digital Learning Series 40 Using the iPod as a Portable Learning Tool 44 Creating, Presenting, and Publishing Work with iWork 45 Additional Resources 47 Apple Learning Interchange 47 Apple Education 47 Apple Professional Development 48 Apple Support 48 Mobile Lab Teacher Sign-Up Sheet 49 Mobile Lab Student Checkout Sheet 50 Mobile Lab Teacher Checkout Sheet 51 © 2007 Apple Inc. -

Grapher 11 Quick Start Guide
TakeTake YourYour DataData toto NewNew HeightsHeights www.GoldenSoftware.com Quick Start Guide Golden Software, Inc. GrapherTM Registration Information Your Grapher serial number is located on the CD cover or in the email download instructions, depending on how you purchased Grapher. Register your Grapher serial number online at www.GoldenSoftware.com. Or, complete the Registration Form.PDF, located in the main directory of the installation CD. Return the Registration Form.PDF by mail or fax. This information will not be redistributed. Registration entitles you to free technical support, free minor updates, and upgrade pricing on future Grapher releases. The serial number is required when you run Grapher the first time, contact technical support, or purchase Grapher upgrades. For future reference, write your serial number on the line below. _________________________________ GrapherTM Quick Start Guide 2D and 3D Graphing Software for Scientists, Engineers, and Business Professionals Golden Software, Inc. 809 14th Street, Golden, Colorado 80401-1866, U.S.A. Phone: 303-279-1021 Fax: 303-279-0909 www.GoldenSoftware.com COPYRIGHT NOTICE Copyright Golden Software, Inc. 2014 The GrapherTM program is furnished under a license agreement. The Grapher software and quick start guide may be used or copied only in accordance with the terms of the agreement. It is against the law to copy the software or quick start guide on any medium except as specifically allowed in the license agreement. Contents are subject to change without notice. Grapher is a -

OS X Mountain Lion Includes Ebook & Learn Os X Mountain Lion— Video Access the Quick and Easy Way!
Final spine = 1.2656” VISUAL QUICKSTA RT GUIDEIn full color VISUAL QUICKSTART GUIDE VISUAL QUICKSTART GUIDE OS X Mountain Lion X Mountain OS INCLUDES eBOOK & Learn OS X Mountain Lion— VIDEO ACCESS the quick and easy way! • Three ways to learn! Now you can curl up with the book, learn on the mobile device of your choice, or watch an expert guide you through the core features of Mountain Lion. This book includes an eBook version and the OS X Mountain Lion: Video QuickStart for the same price! OS X Mountain Lion • Concise steps and explanations let you get up and running in no time. • Essential reference guide keeps you coming back again and again. • Whether you’re new to OS X or you’ve been using it for years, this book has something for you—from Mountain Lion’s great new productivity tools such as Reminders and Notes and Notification Center to full iCloud integration—and much, much more! VISUAL • Visit the companion website at www.mariasguides.com for additional resources. QUICK Maria Langer is a freelance writer who has been writing about Mac OS since 1990. She is the author of more than 75 books and hundreds of articles about using computers. When Maria is not writing, she’s offering S T tours, day trips, and multiday excursions by helicopter for Flying M Air, A LLC. Her blog, An Eclectic Mind, can be found at www.marialanger.com. RT GUIDE Peachpit Press COVERS: OS X 10.8 US $29.99 CAN $30.99 UK £21.99 www.peachpit.com CATEGORY: Operating Systems / OS X ISBN-13: 978-0-321-85788-0 ISBN-10: 0-321-85788-7 BOOK LEVEL: Beginning / Intermediate LAN MARIA LANGER 52999 AUTHOR PHOTO: Jeff Kida G COVER IMAGE: © Geoffrey Kuchera / shutterstock.com ER 9 780321 857880 THREE WAYS To learn—prINT, eBOOK & VIDEO! VISUAL QUICKSTART GUIDE OS X Mountain Lion MARIA LANGER Peachpit Press Visual QuickStart Guide OS X Mountain Lion Maria Langer Peachpit Press www.peachpit.com To report errors, please send a note to [email protected]. -
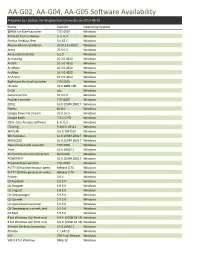
AA-G02, AA-G04, AA-G05 Software Availability
AA-G02, AA-G04, AA-G05 Software Availability Prepared by LabStats for Binghamton University on 2019-08-26 Name Version Operating System @RISK for Excel Launcher 7.05.0001 Windows ActiveQt Test Container 3, 2, 0, 0 Windows Alertus Desktop Alert 5.0.43.1 Windows Alteryx 64-bit Installation 2019.1.6.58192 Windows Amos 25.0.0.0 Windows Anaconda3 Installer 5.2.0 Windows ArcCatalog 10.3.0.4322 Windows ArcGIS 10.3.0.4322 Windows ArcGlobe 10.3.0.4322 Windows ArcMap 10.3.0.4322 Windows ArcScene 10.3.0.4322 Windows BigPicture for Excel Launcher 7.05.0001 Windows chrome 76.0.3809.100 Windows Cn3D n/a Windows DataViewerCLI 25.0.0.0 Windows Evolver Launcher 7.05.0001 Windows EXCEL 16.0.10349.20017 Windows Firefox 60.8.0 Windows Google Drive File Stream 33.0.16.0 Windows Google Earth 7.3.2.5776 Windows IDEA: Data Analysis Software 6, 0, 0, 0 Windows ITConfig 9.400.0.18312 Windows MATLAB 9.6.0.1047502 Windows MS Publisher 16.0.10349.20017 Windows MSACCESS 16.0.10349.20017 Windows NeuralTools Excel Launcher 7.05.0001 Windows Paint 10.0.18362.1 Windows Perl Command Line Interpreter Build 626 Windows POWERPNT 16.0.10349.20017 Windows PrecisionTree Launcher 7.05.0001 Windows PuTTY SSH authentication agent Release 0.70 Windows PuTTY SSH key generation utility Release 0.70 Windows Python 3.6.5 Windows Qt Assistant 5.9.5.0 Windows Qt Designer 5.9.5.0 Windows Qt Linguist 5.9.5.0 Windows Qt Qmlcachegen 5.9.5.0 Windows Qt Qscxmlc 5.9.5.0 Windows Qt Qtattributionsscanner 5.9.5.0 Windows Qt Qwebengine_convert_dict 5.9.5.0 Windows Qt Repc 5.9.5.0 Windows R for Windows -

Mac OS X Desktop.Pdf
Apple Training Series Mac OS X Support Essentials v10.6 Kevin M. White Apple Training Series: Mac OS X Support Essentials v10.6 Kevin M. White Copyright © 2010 by Apple Inc. Published by Peachpit Press. For information on Peachpit Press books, contact: Peachpit Press 1249 Eighth Street Berkeley, CA 94710 510/524-2178 510/524-2221 (fax) www.peachpit.com To report errors, please send a note to [email protected]. Peachpit Press is a division of Pearson Education. Apple Training Series Editor: Rebecca Freed Production Editors: Danielle Foster, Becky Winter Copyeditor: Peggy Nauts Tech Editor: Gordon Davisson Apple Editor: Shane Ross Proofreader: Suzie Nasol Compositor: Danielle Foster Indexer: Valerie Perry Cover design: Mimi Heft Cover illustrator: Kent Oberheu Notice of Rights All rights reserved. No part of this book may be reproduced or transmitted in any form by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior written permission of the publisher. For infor- mation on getting permission for reprints and excerpts, contact [email protected]. Notice of Liability The information in this book is distributed on an “As Is” basis without warranty. While every precaution has been taken in the preparation of the book, neither the author nor Peachpit shall have any liability to any person or entity with respect to any loss or damage caused or alleged to be caused directly or indirectly by the instructions contained in this book or by the computer software and hardware products described in it. Trademarks Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. -

Instructions For
! ! ! ! Instructions for Use! ! ! ! ! ! ! ! ! ! ! !!!!!!!!!!!!Grapher! !!!!!!!!!!!Versions 1.1 2.0 2.1! !!!!!!!!!!!!!! 2.2 2.3 2.5 ! !!!!!!!!!!!(and old Curvus Pro X 1.3.2)! ! ! ! ! ! ! (including a list of bugs and their workarounds)! ! ! “ When everything else fails, read the instructions “! ! !!!!!!!!!!April 16th 2014 edition" #1 ! Contents! ! ! page! ! Overview of Grapher! !! Summary!..........................................................................................................................4! !! Intuitive user interface!.......................................................................................................4! !! Inspectors!.........................................................................................................................5! !! Intuitive syntax!..................................................................................................................5! !! Animations!........................................................................................................................6! !! 3D view!.............................................................................................................................7! !! Export your creations!........................................................................................................7! !!! Contextual menus!.............................................................................................................7! ! Initiation! !! Lesson 1 : Creating a document!.......................................................................................8! -

Donovan Hall Room 1229
Donovan Hall Room 1229 Software Title Version Display Calibrator 4.10.0 Dock 1.8 DRWV_18_2 4.6.0.391 DVD Player 5.8 Dwell Control 1 eaptlstrust 13 Embed - EmojiFunctionRowIM 1 EPFaxAutoSetupTool 1.71 EPSON Scanner 5.7.24 epsonfax 1.71 EscrowSecurityAlert 1 ESHR_1_1_1 4.6.0.391 Expansion Slot Utility 1.5.2 Export Flash Animation - Extract - FaceTime 4 Family 1 Fax Receive Monitor 1.71 FAX Utility 1.73 Feedback Assistant 4.5 FileMerge 2.11 FileZilla 3.35.2 Final Cut Pro 10.4.3 Finder 10.13.5 FindMyMacMessenger 4.1 Firefox 61.0.2 Flash Player 26.0.0.137 Flash Player Debugger 26.0.0.137 FLPR_18_0_2 4.6.0.391 Folder Actions Setup 1.2 FolderActionsDispatcher 1 FollowUpUI 1 Font Book 8 FontRegistryUIAgent 81 Games 1 Donovan Hall Room 1229 Software Title Version GarageBand 10.3.1 Gmsh 4.0.0 Google Chrome 68.0.3440.106 Grab 1.1 Grapher 2.6 HelpViewer 6 HindiIM 1 iBooks 1.15 iCloud 1 iCloud Drive 1 iCloudUserNotificationsd 1 identityservicesd 10 IDSN_13_1 4.6.0.391 IDSRemoteURLConnectionAgent 10 ILST_22_1 4.6.0.391 Image Capture 7 Image Events 1.1.6 ImageCaptureService 6.7 imagent 10 IMAutomaticHistoryDeletionAgent 10 imavagent 10 iMovie 10.1.9 imtransferagent 10 InkServer 10.9 Install 4.3.0.256 Install Command Line Developer Tools 1 Install in Progress 3 Install macOS Mojave 14.1.0 Installer 6.2.0 Installer Progress 1 Instruments 9.4.1 iTunes 12.8 JapaneseIM 1 Jar Launcher 15.0.1 Java Web Start 15.0.1 Jing 2.8.1 Donovan Hall Room 1229 Software Title Version Jumpcut 0.63 KBRG_8_1 4.6.0.391 KeyboardSetupAssistant 10.7 KeyboardViewer 3.2 Keychain -

The ISI Grapher Manual
ISI Technical Manual ISI/TM-88-197 February1988 University of Southern California Gabriel Robins % % .. ... .. The ISI Grapher Manual INFORMATION SCIENCES 213/822-1511 INSTITUTEJ f-"-676466Admiralty Way/Marina del R ey/California292-t5 90292-6695 Unclassified SECURITY CLASSIFicATION OF T'HIS PAC.F THTPPARý SECURITY CLASSIFICATION OF REPORT DOCUMENTATION PAGE !a REPORT SECURITY CLASSIFICATION lb. RESTRICTIVE MARKINGS Unclassified 2a. SECURITY CLASSIFICATION AUTHORITY 3. DISTRIBUTION/ AVAILABILITY OF REPORT This document is approved for public release, 2b. DECLASSIFICATION / DOWNGRADING SCHEDULE distribution is unlimited. 4 PERFORMING ORGANIZATION REPORT NUMBERtS) S. MONITORING ORGANIZATION REPORT NUMBER(S) ISI/TM-88-197 6a. NAME OF PERFORMING ORGANIZATION USC/Information Sciences Institute 6c. ADDRESS (City, State, and ZIP Code) 4676 Admiralty Way Marina del Rey, CA 90292 Ba. NAME OF FUNDING/SPONSORING 8b. OFFICE SYMBOL 9. PROCUREMENT INSTRUMENT IDENTIFICATION NUMBER ORGANIZATION (If applicable) MDA903-81-C-0335 DARPA I Bc. ADDRESS (City, State, and ZIP Code) 10. SOURCE OF FUNDING NUMBERS DARPA PROGRAM PROJECT TASK WORK UNIT 1400 Wilson Blvd. ELEMENT NO. NO. NO. ACCESSION NO. Arlington, VA 22209 I I I 11. TITLE (Include Security Classification) The ISI Grapher Manual [Unclassified] 12. PERSONAL AUTHOR(S) Robins, Gabriel 13a. TYPE OF REPORT 13b. TIME COVERED 14. DATE OF REPORT (Year, Month, Day) 1S. PAGE COUNT 106 Research Report FROM TO 1988, February _ _6 16 SUPPLEMENTARY NOTATION 17. COSATI CODES 18. 5UBJECT TERMS (Continue on reverse if necessary and identify by block number) FIELD GROUP SUB-GROUP artificial Intelligence tools, graph algorithms, graphs, intelligent systems, 09 02 _ SI Grapher, layout algorithms, user interfaces 19 ABSTRACT (Continue on reverse if necessary and identify by block number) This document describes the implementation and usage of the ISI Grapher, a portable software package that allows graphs to be displayed pictorially. -

Curio 16 Documentation
Curio 16 Documentation Copyright © 2021 Zengobi, Inc. Table of contents Table of contents Introducing Curio 15 Curio Editions 15 Availability 16 Curio From the Zengobi Website 16 Curio From the Mac App Store 19 Getting Help 20 Curiota 21 Projects 22 Project Gallery 23 Using the Project Gallery 23 Working with the Open Project Gallery 24 The New Project Gallery 25 Projects Toolbar Button 26 Project Templates 26 Inspector 27 Calendar Sync STANDARD PRO 27 PDF Mirror STANDARD PRO 29 Additional Details 30 Reference Types PRO 32 Custom Variables PRO 33 Advanced Project Options PRO 35 The Organizer 37 Sections STANDARD PRO 40 Folders 41 Trash 41 Archive 43 Filter 43 Navigation Controls 44 Inspector 45 Tags 45 Labels 47 Notes 47 Info 48 The Idea Space 50 Working with Idea Spaces 50 Idea Space Styles 50 Idea Space Templates STANDARD PRO 51 - 2/270 - Copyright © 2021 Zengobi, Inc. Table of contents Zooming 52 Gestures 53 Inserting Space 53 Inspector 54 Background 54 Transitions PRO 55 Dimensions 55 Figures 57 Terminology 57 Insert Popover 57 Basic Shapes 58 Styled Shape or Stencil 58 List / Mind Map / Table / Index Card / Album / Pinboard 58 Audio Recording 59 Video Recording 59 YouTube / Vimeo Video 59 Instant Document 60 Equation STANDARD PRO 60 Web View 60 Google Doc 60 Date and Time 60 Variable 61 List/Mind Map/Table From File 61 File 62 Insert Menu 62 Insert Other Content 62 From the Finder 62 From Curiota 63 From the Web 63 From Mail 63 From Contacts 64 From Calendar 64 From a LinkBack Application 64 From an Equation/Formula Editor 64 From OneNote 65 From TaskPaper STANDARD PRO 66 From OmniOutliner STANDARD PRO 66 Insert from Library 67 Meta Import STANDARD PRO 68 Spread PDF STANDARD PRO 71 Instant Document Templates 72 - 3/270 - Copyright © 2021 Zengobi, Inc. -

Full User's Guide
Golden Software, Inc. 2D & 3D Graphing for Scientists, Engineers & Business Professionals Full User's Guide www.GoldenSoftware.com Golden Software, Inc. GrapherTM Registration Information Your Grapher serial number is located on the CD cover or in the email download instructions, depending on how you purchased Grapher. Register your Grapher serial number online at www.GoldenSoftware.com. Or, complete the Registration Form.PDF, located in the main directory of the installation CD. Return the Registration Form.PDF by mail or fax. This information will not be redistributed. Registration entitles you to free technical support, free minor updates, and upgrade pricing on future Grapher releases. The serial number is required when you run Grapher the first time, contact technical support, or purchase Grapher upgrades. For future reference, write your serial number on the line below. _________________________________ GrapherTM User’s Guide 2D & 3D Graphing Software for Scientists, Engineers & Business Professionals Golden Software, Inc. 809 14th Street, Golden, Colorado 80401-1866, U.S.A. Phone: 303-279-1021 Fax: 303-279-0909 www.GoldenSoftware.com COPYRIGHT NOTICE Copyright Golden Software, Inc. 2011 The GrapherTM User’s Guide is furnished under a single user license agreement. Only a single user may use a single user’s guide. With the purchase of the Grapher User’s Guide, the user is entitled to download the user’s guide content to one (1) electronic medium and print one (1) hardcopy. No part of this document or the related files may be reproduced or transmitted in any form, by any means (electronic, photocopying, recording, or otherwise) thereafter. Contents are subject to change without notice.