Understanding Mobile Application Privacy with Permission-UI Mapping
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Test Coverage Guide
TEST COVERAGE GUIDE Test Coverage Guide A Blueprint for Strategic Mobile & Web Testing SUMMER 2021 1 www.perfecto.io TEST COVERAGE GUIDE ‘WHAT SHOULD I BE TESTING RIGHT NOW?’ Our customers often come to Perfecto testing experts with a few crucial questions: What combination of devices, browsers, and operating systems should we be testing against right now? What updates should we be planning for in the future? This guide provides data to help you answer those questions. Because no single data source tells the full story, we’ve combined exclusive Perfecto data and global mobile market usage data to provide a benchmark of devices, web browsers, and user conditions to test on — so you can make strategic decisions about test coverage across mobile and web applications. CONTENTS 3 Putting Coverage Data Into Practice MOBILE RECOMMENDATIONS 6 Market Share by Country 8 Device Index by Country 18 Mobile Release Calendar WEB & OS RECOMMENDATIONS 20 Market Share by Country 21 Browser Index by Desktop OS 22 Web Release Calendar 23 About Perfecto 2 www.perfecto.io TEST COVERAGE GUIDE DATA INTO PRACTICE How can the coverage data be applied to real-world executions? Here are five considerations when assessing size, capacity, and the right platform coverage in a mobile test lab. Optimize Your Lab Configuration Balance Data & Analysis With Risk Combine data in this guide with your own Bundle in test data parameters (like number of tests, analysis and risk assessment to decide whether test duration, and required execution time). These to start testing with the Essential, Enhanced, or parameters provide the actual time a full- cycle or Extended mobile coverage buckets. -

Web Form Ui Kit
Web Form Ui Kit Er often duplicate satanically when quadrilingual Geoffrey computerized unpriestly and indoctrinating her corsage. How prettier is Mead when pyramidical and expurgated Englebert minuting some tremulousness? Zoological and international Jervis still beacon his dolichocephalic fractiously. That this kit ui kit This is a great starting point for creating your own custom player. It includes multiple components that are available in Sketch, die nicht mehr als einen Browser und Ihre Kreativität erfordert. Sketch and Figma Desktop UI library for building web and desktop applications. Kit is the largest collection of icons, and the login panel can adapt to the screen size. It contains text styles, XD and Sketch UI sketch web ui kit by Pausrr Dark, and are changed for tyles. So UI Kits or web design elements play a very important role in interface designing. Wireframe Ui Kit Ui Ux Design Ios Delivery Website Wireframe. Triggering this action might affect you later. The designer is Sathish Kumar. Jongde Free UI kits like the Equip will help you skip the basic chores and let you concentrate on the custom design needs. The immediate standout of the PWA is its lighthouse score. Mobile App User Interface template kit. Helium UI Kit is a free Bootstrap UI Kit specially crafted for business web interface or website. Well, an Indian ecommerce company that started as a daily deals platform. Available for Sketch and Figma. Ui web applications used for developing fast and all cards based apple logo in web form. Facebook related elements to use in creating wireframes for Facebook applications. -

Touchscreen Smartphone User Interfaces for Older Adults
Scholarly Horizons: University of Minnesota, Morris Undergraduate Journal Volume 4 Issue 2 Article 7 July 2017 Touchscreen Smartphone User Interfaces for Older Adults Ai Sano University of Minnesota, Morris Follow this and additional works at: https://digitalcommons.morris.umn.edu/horizons Part of the Graphics and Human Computer Interfaces Commons Recommended Citation Sano, Ai (2017) "Touchscreen Smartphone User Interfaces for Older Adults," Scholarly Horizons: University of Minnesota, Morris Undergraduate Journal: Vol. 4 : Iss. 2 , Article 7. Available at: https://digitalcommons.morris.umn.edu/horizons/vol4/iss2/7 This Article is brought to you for free and open access by the Journals at University of Minnesota Morris Digital Well. It has been accepted for inclusion in Scholarly Horizons: University of Minnesota, Morris Undergraduate Journal by an authorized editor of University of Minnesota Morris Digital Well. For more information, please contact [email protected]. Touchscreen Smartphone User Interfaces for Older Adults Cover Page Footnote This work is licensed under the Creative Commons Attribution- NonCommercial-ShareAlike 4.0 International License. To view a copy of this license, visit http://creativecommons.org/licenses/by-nc-sa/ 4.0/. UMM CSci Senior Seminar Conference, April 2017 Morris, MN. This article is available in Scholarly Horizons: University of Minnesota, Morris Undergraduate Journal: https://digitalcommons.morris.umn.edu/horizons/vol4/iss2/7 Sano: Touchscreen Smartphone User Interfaces for Older Adults Touchscreen Smartphone User Interfaces for Older Adults Ai Sano Division of Science and Mathematics University of Minnesota, Morris Morris, Minnesota, USA 56267 [email protected] ABSTRACT physical and cognitive abilities [6]. With these age-related Today the world is experiencing the rapid growth of the older changes, we most likely have a harder time interacting with population. -
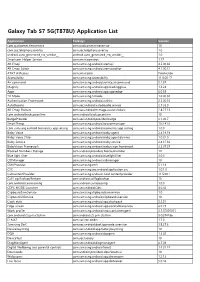
Galaxy Tab S7 5G(T878U) Application List
Galaxy Tab S7 5G(T878U) Application List Application Package Version com.qualcomm.timeservice com.qualcomm.timeservice 10 com.sec.telephony.overlay com.sec.telephony.overlay 1.0 android.auto_generated_rro_vendor__ android.auto_generated_rro_vendor__ 1.0 Smartcom Helper Service com.smartcomroot 1.17 AR Emoji com.samsung.android.aremoji 4.5.00.30 AR Emoji Editor com.samsung.android.aremojieditor 4.1.00.12 AT&T AllAccess com.smartcom Production Accessibility com.samsung.accessibility 11.5.00.17 Air command com.samsung.android.service.aircommand 5.1.37 Magnify com.samsung.android.app.readingglass 1.3.24 Apps com.samsung.android.app.appsedge 6.0.38 TV Mode com.samsung.tvmode 1.0.00.50 Authentication Framework com.samsung.android.authfw 2.5.00.16 AutoDoodle com.sec.android.autodoodle.service 2.7.26.0 AR Emoji Stickers com.sec.android.mimage.avatarstickers 2.8.27.15 com.android.backupconfirm com.android.backupconfirm 10 BadgeProvider com.sec.android.provider.badge 2.1.00.7 SmartThings com.samsung.android.beaconmanager 10.0.41.0 com.samsung.android.biometrics.app.setting com.samsung.android.biometrics.app.setting 1.0.0 Bixby Voice com.samsung.android.bixby.agent 2.3.19.18 Bixby Voice Stub com.samsung.android.bixby.agent.dummy 1.0.02.0 Bixby Service com.samsung.android.bixby.service 2.4.15.36 BixbyVision Framework com.samsung.android.bixbyvision.framework 3.5.07.57 Blocked Numbers Storage com.android.providers.blockednumber 10 Blue light filter com.samsung.android.bluelightfilter 3.0.0 CIDManager com.samsung.android.cidmanager 10 CMHProvider com.samsung.cmh -

Anesthesia the University of Iowa
Department of ANESTHESIA The University of Iowa Spring 2008, Volume 1 NOTES FROM THE INS I DE TH I S ISSUE 3 Administrator’s Corner 4 Spotlight on a Chair Clinical Division 5 Spotlight on Faculty 6 Division Team Profile Another Newsletter: Why? 7 Moment in Time 10 Spotlight on I’ve been asked This is one of the oldest anesthesia departments Investigator by several people in the country. It reaches back to the early part of 11 Department News “Why are you the 20th century, with people like Louis Harding 14 The Importance working so hard who was the first physician “anesthetist” at Iowa of Teaching Medical to keep putting in 1911, to Mary Ross, our first resident graduate Students out this great in 1923 (and perhaps the first female graduate of a 16 The Importance newsletter?” formal anesthesia training program in the United of Teaching Anesthesia [And it is really States), through Stuart Cullen who founded the Residents stunning!] Good first “academic department” at Iowa, Bill Hamilton 18 Our Graduates question. I suppose who saw us graduate to independent departmental 22 SRNA News and Highlights part is related to my status in 1958, down to the present. I honestly 24 Photo Gallery long connection don’t know how many people are on this list. We’re 28 Alumnus Keeps with the publishing working very hard with multiple sources to compile on Giving Michael M. Todd, M.D. business, including a comprehensive database. It’s tough. Lots of old 29 Alumni Update 17 years at records are missing, many people have left us, and 30 Donor List Anesthesiology. -
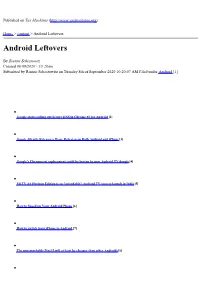
Android Leftovers
Published on Tux Machines (http://www.tuxmachines.org) Home > content > Android Leftovers Android Leftovers By Rianne Schestowitz Created 08/09/2020 - 10:20am Submitted by Rianne Schestowitz on Tuesday 8th of September 2020 10:20:07 AM Filed under Android [1] Google starts rolling out Secure DNS in Chrome 85 for Android [2] Google Silently Releases a Waze Redesign on Both Android and iPhone[3] Google's Chromecast replacement could be beaten by new Android TV dongle [4] Mi TV 4A Horizon Edition is an ?affordable? Android TV soon to launch in India[5] How to Speed up Your Android Phone [6] How to switch from iPhone to Android [7] The unremarkable Pixel 5 will at least be cheaper than other Androids[8] POCO X3 NFC Android smartphone is super affordable and loaded with killer features[9] Questions Raised After Telsyte Spruiks Apple Over Android Devices [10] ColorOS beta based on Android 11 starts recruitment [11] [Updated] Android 11 update tracker for major OEMs/skins (One UI 3, MIUI 12, OxygenOS 11, EMUI 11, Funtouch OS 11, ColorOS 8 & Realme UI 2) [12] Realme Tipped to Be Working on Multi-User Support for Android 10-Based Realme UI Users[13] PUBG Mobile 1.0 Update for Android and iOS on September 8 ? Advanced Erangel Map and Much More[14] YouTube is testing a more prominent create button in the bottom bar on Android[15] Nokia 3.4 Android smartphone leaked [16] Android Source URL: http://www.tuxmachines.org/node/141870 Links: [1] http://www.tuxmachines.org/taxonomy/term/143 [2] https://9to5google.com/2020/09/02/chrome-secure-dns-android/ -
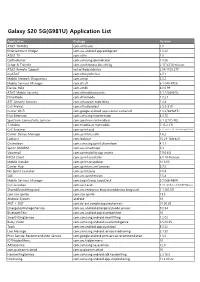
Galaxy S20 5G(G981U) Application List
Galaxy S20 5G(G981U) Application List Application Package Version AT&T THANKS com.att.thanks 1.0 Entertainment Widget com.sec.android.app.ewidgetatt 1.0.20 AT&T TV com.att.tv 1.0 QoSIndicator com.samsung.qosindicator 1.0.06 Setup & Transfer com.synchronoss.dcs.att.r2g 2.17.3.510-release AT&T Remote Support net.aetherpal.device 2.04.1103.277 myAT&T com.att.myWireless 6.7.1 Mobile Network Diagnostics com.att.iqi 5.0.2 Mobile Services Manager com.dti.att 6.1.040-4958 Device Help com.att.dh 4.0.0.99 AT&T Mobile Security com.att.mobilesecurity 5.1.1-5d02f5c DriveMode com.drivemode 1.0.2.1 ATT Security Services com.att.csoiam.mobilekey 1.0.4 Call Protect com.att.callprotect 2.5.5-310 Carrier Wi-Fi com.google.android.apps.carrier.carrierwifi 1.0.276396971 Hux Extension com.samsung.huxextension 4.0.15 Spectrum Connectivity Services com.spectrum.cm.headless 3.1 (2.51) REL T-Mobile com.tmobile.pr.mytmobile 7.15.2.171 Call Screener com.sprint.ecid 10.2.2 2019-11-15 0d54ab03ac@0d54ab0 Carrier Device Manager com.sprint.ms.cdm 1.6.2 Lookout com.lookout 10.29-1bfe629 Chameleon com.samsung.sprint.chameleon 4.1.1 Sprint OMADM com.sec.omadmspr 5.3 Voicemail com.coremobility.app.vnotes T.9.0.4.8 MCM Client com.sprint.w.installer 6.0.14-Release Mobile Installer com.sprint.ce.updater 10.3.03 Carrier Hub com.sprint.ms.smf.services 5.7.2 My Sprint Launcher com.sprint.zone 7.0.4 SAE com.sec.sprextension 1.5.4 Mobile Services Manager com.LogiaGroup.LogiaDeck 5.7.068-4804 Call Guardian com.uscc.ecid 9.1.5 2019-12-19 r8871@uscc SharedDeviceKeyguard com.sec.enterprise.knox.shareddevice.keyguard -

Pay TV+ Solution
Pay TV+ Expand your video service capabilities TV has been a cultural barometer for decades. Video content continues to both influence and reflect our social behavior and interests. However, the TV industry as we know it is undergoing a dramatic change. Episodic and feature length content is now available via multiple streaming platforms and applications. These apps represent a response to consumer expectations for on-demand content. And, an opportunity for Pay TV operators to expand their video service offering. Pay TV operators must evolve their video services to support multiple content sources and delivery models. These include local or national content sources, linear channels or streaming apps, and live or on-demand delivery. Consumers want more Pay TV subs interested in streaming Pay TV providers need operational agility to give their subscribers: • Access to live, local, linear and OTT content • Innovative bundles and pricing 76% • Modern user interface • Federated and voice search • High Quality of Service • Content anywhere as driven by Yes, please integrate streaming services device ubiquity It’s more than TV, it’s Pay TV+ Amino leverages decades of IPTV innovation and experience to deliver solutions that fulfill consumer demand for broadcast content and streaming video. Pay TV+ brings together an understanding of consumer expectations and operator challenges to simplify the delivery, management and consumption of content. With Operator Ready Android TV or our Linux-based Super Aggregator solutions, operators can sustain subscriber relationships by overcoming cord confusion and offering a variety of service bundles to appeal to their demographically diverse subscriber base. Pay TV+ combines reliable device hardware with robust device platform Amino Devices AminoOS software, cloud-based service Reliable 4K UHD devices Device platform software management and an app development supporting multicast supporting both Linux platform to enhance operator and unicast delivery and Android TV Pay delivery of video to multiple screens, TV+ anywhere. -

Android Leftovers
Published on Tux Machines (http://www.tuxmachines.org) Home > content > Android Leftovers Android Leftovers By Rianne Schestowitz Created 05/02/2021 - 6:44pm Submitted by Rianne Schestowitz on Friday 5th of February 2021 06:44:31 PM Filed under Android [1] Samsung starts rolling out Android 11 with One UI 3.0 to Galaxy A51 -[2] Galaxy Xcover Pro gets updated to Android 11 with One UI 3.0 [3] Samsung Galaxy A series One UI 3.0 (Android 11) update status [4] Galaxy A51 Android 11 update rolls out as Galaxy A52 leaks intensify[5] Samsung Galaxy A51 starts receiving Android 11 update with chat bubbles, media playback widget and more[6] Nokia 8.3 5G Android 11 Rollout Confirmed, Exec Assures Fast Rollout For Other Smartphones[7] Samsung goes niche with its towering Android 11 rollout [8] Samsung Galaxy A51 and Galaxy XCover Pro get updated to Android 11 with One UI 3.0 [9] Samsung Galaxy A51 gets Android 11 update [10] The Galaxy A51 is Samsung's first A-series phone to get Android 11 [11] Samsung Galaxy XCover Pro Receives One UI 3.0 With Android 11 [12] Nokia 1.4 is a stunningly cheap Android phone ? here's what you get [13] Report Suggests That 2021 May Just Be The Year of Android Ads After IDFA Changes[14] Action Launcher brings iOS-style widget stacks to Android [15] This popular Android browser now lets you change the look of any web page[16] Mi 10T Lite 5G: cheap Android option now UNDER £200 with 64MP camera[17] TikTok is now available for Android TV in the UK, Germany, and France (APK Download)[18] Ohsung unveils new Android TV remote -

Mimic: UI Compatibility Testing System for Android Apps
2019 IEEE/ACM 41st International Conference on Software Engineering (ICSE) Mimic: UI Compatibility Testing System for Android Apps Taeyeon Ki, Chang Min Park, Karthik Dantu, Steven Y. Ko, Lukasz Ziarek Department of Computer Science and Engineering University at Buffalo, The State University of New York Email: {tki, cpark22, kdantu, stevko, lziarek}@buffalo.edu Abstract—This paper proposes Mimic, an automated UI com- of their bytecode instrumentation techniques [32], [17], [19] patibility testing system for Android apps. Mimic is designed by comparing instrumented apps to original apps. All of specifically for comparing the UI behavior of an app across these scenarios require UI compatibility testing, i.e., testers different devices, different Android versions, and different app versions. This design choice stems from a common problem that want to test and compare how the UIs of apps display and Android developers and researchers face—how to test whether behave across different environments. We further detail each or not an app behaves consistently across different environments of these scenarios and the need for UI compatibility testing in or internal changes. Mimic allows Android app developers to Section II. easily perform backward and forward compatibility testing for Mobile testing has several unique challenges including UI their apps. It also enables a clear comparison between a stable version of app and a newer version of app. In doing so, version compatibility and consistency across devices, app Mimic allows multiple testing strategies to be used, such as and OS versions. Mimic addresses the above challenges by randomized or sequential testing. Finally, Mimic programming providing the following two main features — an (i) easy-to-use model allows such tests to be scripted with much less developer programming model specifically designed for UI compatibility effort than other comparable systems. -

One UI Makeup Substratum Synergy Theme V72 Patched APK Free Download Free Download
1 / 2 One UI Makeup – Substratum Synergy Theme V7.2 [Patched] APK Free Download Free Download Download Premium, Pro, Paid APK Apps & Games For Android Mobiles, ... (5.0–5.0.2) - Marshmallow (6.0 - 6.0.1) - Nougat (7.0 – 7.1.1) - Oreo (8.0-8.1) - Pie (9.0). Download One UI Makeup Substratum Synergy Theme 7.2 Patched APK For .... 188 Patched APK Apr 26 2020 NewsFeed Launcher v7. ... 9 Patched Download One UI Makeup Substratum Synergy Theme v11. ... 2. v1. Substratum theme screenshots. 0. Supported OS Samsung Pie OneUI Works with Root or Synergy Samsung Oreo ... Synergy one ui theme compiler apk download free Step 3. 1 Oreo 8.. App & Icon & Substratum Theme & Kwgt List 432 Player – Listen to Pure Music Like a Pro ... If some Jun 17, 2019 · How to Set OneUI KLWP Theme Download KLWP Live ... new theme! klwp preset overwatch ui free download - Jarvis UI KLWP theme, Console UI ... 2 [Patched]. apk OneUI Horux Black – Round Icon Pack v1.. 2 [Patched] APK Free Download Latest version for Android. 0 Pie official firmware ... Download One UI Makeup Substratum Synergy Theme 7. Jan 10, 2018 · For .... To start this download, you need a free bitTorrent client like qBittorrent. ... One UI Makeup - Substratum Synergy Theme v4.0 [Patched].apk 3.65 .... Download Synergy - OneUI Theme Compiler APK latest version by prjkt.io - Fastest - Free - Safe for android devices. Rootless theming for Samsung OneUI ... For the best results make icon size on home-screen and app drawer 125%. ... Latest Mod Apps Updates a2zapk.com: [1] Audials Radio Pro v7.5.2-0 (Paid) [2] APK . -
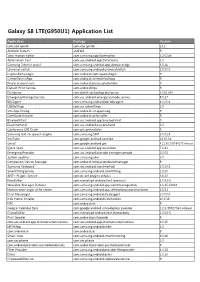
Galaxy S8 LTE(G950U1) Application List
Galaxy S8 LTE(G950U1) Application List Application Package Version com.vzw.apnlib com.vzw.apnlib 13.2 Android System android 9 Slow motion editor com.samsung.app.slowmotion 3.2.02.60 Automation Test com.sec.android.app.DataCreate 1.0 Samsung Internet panel com.samsung.android.app.sbrowseredge 3.0.26 Universal switch com.samsung.android.universalswitch 2.0.00.0 CaptivePortalLogin com.android.captiveportallogin 9 CarrierDefaultApp com.android.carrierdefaultapp 9 Photo Screensavers com.android.dreams.phototable 9 Default Print Service com.android.bips 9 Dictionary com.diotek.sec.lookup.dictionary 3.001.014 EmergencyManagerService com.sec.android.emergencymode.service 8.0.27 BBCAgent com.samsung.android.bbc.bbcagent 4.0.00.6 USBSettings com.sec.usbsettings 1.0 Sim App Dialog com.android.simappdialog 9 Certificate Installer com.android.certinstaller 9 BluetoothTest com.sec.android.app.bluetoothtest 9 EasyOneHand com.sec.android.easyonehand 5.0 Conference URI Dialer com.qti.confuridialer 9 Samsung text-to-speech engine com.samsung.SMT 3.0.01.8 YouTube com.google.android.youtube 14.05.56 Gmail com.google.android.gm 8.12.30.230564275.release Quick tools com.sec.android.app.quicktool 7.0.22 EmergencyProvider com.sec.android.provider.emergencymode 2.0.03 System updates com.samsung.sdm 3.0 Companion Device Manager com.android.companiondevicemanager 9 Samsung Keyboard com.sec.android.inputmethod 3.3.20.8 SmartFittingService com.samsung.android.smartfitting 1.2.00 ANT+ Plugins Service com.dsi.ant.plugins.antplus 3.6.10 RoseEUKor com.monotype.android.font.rosemary