Conference Reports From
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Love Hörnquist-Åstrand Assar Westerlund Harald Barth
Arla A Free AFS implementation from KTH Edition 0.1, for version 0.34 1999 - 2000 Love H¨ornquist-Astrand˚ Assar Westerlund Harald Barth last updated $Date: 2000/10/01 19:18:41 $ Copyright (c) 1998 - 1999 Kungliga Tekniska H¨ogskolan (Royal Institute of Technology, Stock- holm, Sweden). All rights reserved. Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met: 1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer. 2. Redistributions in binary form must reproduce the above copyright notice, this list of condi- tions and the following disclaimer in the documentation and/or other materials provided with the distribution. 3. All advertising materials mentioning features or use of this software must display the following acknowledgement: This product includes software developed by Kungliga Tekniska H¨ogskolan and its contributors. 4. Neither the name of the Institute nor the names of its contributors may be used to endorse or promote products derived from this software without specific prior written permission. THIS SOFTWARE IS PROVIDED BY THE INSTITUTE AND CONTRIBUTORS \AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PAR- TICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE INSTITUTE OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THE- ORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (IN- CLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. -

Nelda Reyes-Resume Ryanartists
Nelda Reyes SAG/AFTRA Hair: Dark brown Eyes: Brown Height: 5” 3’ TV/FILM “Not one more” Isabel Heather Dominguez dir./Art Institute of Portland Grimm - Episode # 111 “Tarantella” Maid Peter Werner /NBC COMMERCIAL/INDUSTRIAL *Complete list available upon request “OCDC Spanish & English PSA” Nelda Reyes Rex-post “SEIU Orientation and Safety Video” HCA Branch Ave. Productions “Wired MD Patient Educational Videos” Health Expert Krames Video Solutions “American Red Cross EMR” Health Officer Erica Portfolio Productions “Depression Relapse”-ORCAS Carmen Moving Images VOICEOVER AND DUBBING *Complete list available upon request “Kaiser Permanente Diabetes Bilingual Campaign” Patti The Fotonovela Production Company “Abuelo -Ac tive Living” -Multnomah County Health Univision Portland Mom Department. “CISCO Online Support website ” Narrator Intersect Video THEATER *Complete list available upon request CORRIDO CALAVERA Concepcion, INC Rep, Rosario Miracle Theatre Group/Lakin Valdez dir. DANCE FOR A DOLLAR Gloria Miracle Theatre Group/Daniel Jaquez dir. BLOOD WEDDING Criada, Luna, Niña 1 Miracle Theatre Group/Olga Sanchez dir LA CARPA CALAVERA Nina Miracle Theatre Group/Philip Cuomo dir. ACTING AND MOVEMENT TRAINING Acting, Scene Work and Movement Moscow Art Theatre School and IATT, Harvard University M. Lovanov/ Alla Prokoskaya/ Oleg Topolyanskiy /N. Fedorovna Acting: Process, Classical, Experimental styles Devon Allen. Portland State University. MA. In Theatre Arts Script Analysis and Dramaturgy Karin Magaldi. Portland State University. MA. In Theatre Arts Clown Fausto Ramirez (Mexico) and Les Matapestes (France) Alexander, Decroux, Lecoq, Contact Improv. Diplomado de Teatro del Cuerpo (Mexico City) Diploma for Instructors in Kundalini Yoga IKYTA/ Yoga Alliance Empty Hand Combat and basic weaponry Anthony De Longis (USA) Shelley Lipkin Acting for the Camera (USA) Professional Training in Aerial Arts The Circus Project (US A) Pre-professional Classic Dance Program Ballet Nacional de Cuba/Gloria Campobello Co. -

Pynchon's Sound of Music
Pynchon’s Sound of Music Christian Hänggi Pynchon’s Sound of Music DIAPHANES PUBLISHED WITH SUPPORT BY THE SWISS NATIONAL SCIENCE FOUNDATION 1ST EDITION ISBN 978-3-0358-0233-7 10.4472/9783035802337 DIESES WERK IST LIZENZIERT UNTER EINER CREATIVE COMMONS NAMENSNENNUNG 3.0 SCHWEIZ LIZENZ. LAYOUT AND PREPRESS: 2EDIT, ZURICH WWW.DIAPHANES.NET Contents Preface 7 Introduction 9 1 The Job of Sorting It All Out 17 A Brief Biography in Music 17 An Inventory of Pynchon’s Musical Techniques and Strategies 26 Pynchon on Record, Vol. 4 51 2 Lessons in Organology 53 The Harmonica 56 The Kazoo 79 The Saxophone 93 3 The Sounds of Societies to Come 121 The Age of Representation 127 The Age of Repetition 149 The Age of Composition 165 4 Analyzing the Pynchon Playlist 183 Conclusion 227 Appendix 231 Index of Musical Instruments 233 The Pynchon Playlist 239 Bibliography 289 Index of Musicians 309 Acknowledgments 315 Preface When I first read Gravity’s Rainbow, back in the days before I started to study literature more systematically, I noticed the nov- el’s many references to saxophones. Having played the instru- ment for, then, almost two decades, I thought that a novelist would not, could not, feature specialty instruments such as the C-melody sax if he did not play the horn himself. Once the saxophone had caught my attention, I noticed all sorts of uncommon references that seemed to confirm my hunch that Thomas Pynchon himself played the instrument: McClintic Sphere’s 4½ reed, the contra- bass sax of Against the Day, Gravity’s Rainbow’s Charlie Parker passage. -

Using the Andrew File System on *BSD [email protected], Bsdcan, 2006 Why Another Network Filesystem
Using the Andrew File System on *BSD [email protected], BSDCan, 2006 why another network filesystem 1-slide history of Andrew File System user view admin view OpenAFS Arla AFS on OpenBSD, FreeBSD and NetBSD Filesharing on the Internet use FTP or link to HTTP file interface through WebDAV use insecure protocol over vpn History of AFS 1984: developed at Carnegie Mellon 1989: TransArc Corperation 1994: over to IBM 1997: Arla, aimed at Linux and BSD 2000: IBM releases source 2000: foundation of OpenAFS User view <1> global filesystem rooted at /afs /afs/cern.ch/... /afs/cmu.edu/... /afs/gorlaeus.net/users/h/hugo/... User view <2> authentication through Kerberos #>kinit <username> obtain krbtgt/<realm>@<realm> #>afslog obtain afs@<realm> #>cd /afs/<cell>/users/<username> User view <3> ACL (dir based) & Quota usage runs on Windows, OS X, Linux, Solaris ... and *BSD Admin view <1> <cell> <partition> <server> <volume> <volume> <server> <partition> Admin view <2> /afs/gorlaeus.net/users/h/hugo/presos/afs_slides.graffle gorlaeus.net /vicepa fwncafs1 users hugo h bram <server> /vicepb Admin view <2a> /afs/gorlaeus.net/users/h/hugo/presos/afs_slides.graffle gorlaeus.net /vicepa fwncafs1 users hugo /vicepa fwncafs2 h bram Admin view <3> servers require KeyFile ~= keytab procedure differs for Heimdal: ktutil copy MIT: asetkey add Admin view <4> entry in CellServDB >gorlaeus.net #my cell name 10.0.0.1 <dbserver host name> required on servers required on clients without DynRoot Admin view <5> File locking no databases on AFS (requires byte range locking) -

(“Spider-Man”) Cr
PRIVILEGED ATTORNEY-CLIENT COMMUNICATION EXECUTIVE SUMMARY SECOND AMENDED AND RESTATED LICENSE AGREEMENT (“SPIDER-MAN”) CREATIVE ISSUES This memo summarizes certain terms of the Second Amended and Restated License Agreement (“Spider-Man”) between SPE and Marvel, effective September 15, 2011 (the “Agreement”). 1. CHARACTERS AND OTHER CREATIVE ELEMENTS: a. Exclusive to SPE: . The “Spider-Man” character, “Peter Parker” and essentially all existing and future alternate versions, iterations, and alter egos of the “Spider- Man” character. All fictional characters, places structures, businesses, groups, or other entities or elements (collectively, “Creative Elements”) that are listed on the attached Schedule 6. All existing (as of 9/15/11) characters and other Creative Elements that are “Primarily Associated With” Spider-Man but were “Inadvertently Omitted” from Schedule 6. The Agreement contains detailed definitions of these terms, but they basically conform to common-sense meanings. If SPE and Marvel cannot agree as to whether a character or other creative element is Primarily Associated With Spider-Man and/or were Inadvertently Omitted, the matter will be determined by expedited arbitration. All newly created (after 9/15/11) characters and other Creative Elements that first appear in a work that is titled or branded with “Spider-Man” or in which “Spider-Man” is the main protagonist (but not including any team- up work featuring both Spider-Man and another major Marvel character that isn’t part of the Spider-Man Property). The origin story, secret identities, alter egos, powers, costumes, equipment, and other elements of, or associated with, Spider-Man and the other Creative Elements covered above. The story lines of individual Marvel comic books and other works in which Spider-Man or other characters granted to SPE appear, subject to Marvel confirming ownership. -

El Llegat Dels Germans Grimm En El Segle Xxi: Del Paper a La Pantalla Emili Samper Prunera Universitat Rovira I Virgili [email protected]
El llegat dels germans Grimm en el segle xxi: del paper a la pantalla Emili Samper Prunera Universitat Rovira i Virgili [email protected] Resum Les rondalles que els germans Grimm van recollir als Kinder- und Hausmärchen han traspassat la frontera del paper amb nombroses adaptacions literàries, cinema- togràfiques o televisives. La pel·lícula The brothers Grimm (2005), de Terry Gilli- am, i la primera temporada de la sèrie Grimm (2011-2012), de la cadena NBC, són dos mostres recents d’obres audiovisuals que han agafat les rondalles dels Grimm com a base per elaborar la seva ficció. En aquest article s’analitza el tractament de les rondalles que apareixen en totes dues obres (tenint en compte un precedent de 1962, The wonderful world of the Brothers Grimm), així com el rol que adopten els mateixos germans Grimm, que passen de creadors a convertir-se ells mateixos en personatges de ficció. Es recorre, d’aquesta manera, el camí invers al que han realitzat els responsables d’aquestes adaptacions: de la pantalla (gran o petita) es torna al paper, mostrant quines són les rondalles dels Grimm que s’han adaptat i de quina manera s’ha dut a terme aquesta adaptació. Paraules clau Grimm, Kinder- und Hausmärchen, The brothers Grimm, Terry Gilliam, rondalla Summary The tales that the Grimm brothers collected in their Kinder- und Hausmärchen have gone beyond the confines of paper with numerous literary, cinematographic and TV adaptations. The film The Brothers Grimm (2005), by Terry Gilliam, and the first season of the series Grimm (2011–2012), produced by the NBC network, are two recent examples of audiovisual productions that have taken the Grimm brothers’ tales as a base on which to create their fiction. -

The 3Ourn L of AUUG Inc. Volume 25 ¯ Number 4 December 2004
The 3ourn l of AUUG Inc. Volume 25 ¯ Number 4 December 2004 Features: A Convert to the Fold 7 Lions Commentary, part 1 16 News: Minutes of AUUG Annual General Meeting, 1 September 2004 54 AUUG 2005 annual conference: CFP 58 First Australian UNIX Developer’s Symposium: CFP 59 First Digital Pest Symposium 60 Regulars: Editorial 1 President’s Column 3 My Home Network 4 This Issue’s CD 29 The Future of AUUG CDs 30 A Hacker’s Diary 31 AUUG Corporate Members 56 Letters to AUUG 56 About AUUGN 61 Chapter Meetings and Contact Details 62 AUUG Membership Application Form 63 ISSN 1035-7521 Print post approved by Australia Post - PP2391500002 AUUGN The journal of AUUG Inc. Volume 25, Number 3 September 2004 Editor ial Frank Crawford <[email protected]> Well, after many, many years of involvement with mittee, preparing each edition. Curr ently, this AUUGN, I’ve finally been roped into writing the consists of Greg Lehey and myself, but we are editorial. In fact, AUUGN has a very long and keen to expand this by a few more, in an effort to distinguished history, providing important infor- spr ead the load. And as with previous changes, mation to generations of Unix users. During that we have a “new” approach to finding contribu- time, therehave been a range of editors all of tions. AUUG has a huge body of work, from whom have guided it through ups and downs. both the Annual Conference and regional meet- Certainly you will know many of the recent ones, ings that should be seen morewidely, especially such as David Purdue (current AUUG President), by those who weren't able to attend these events. -
Some Results Recall: FAT Properties FAT Assessment – Issues
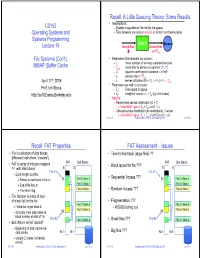
Recall: A Little Queuing Theory: Some Results • Assumptions: CS162 – System in equilibrium; No limit to the queue Operating Systems and – Time between successive arrivals is random and memoryless Systems Programming Queue Server Lecture 19 Arrival Rate Service Rate μ=1/Tser File Systems (Con’t), • Parameters that describe our system: MMAP, Buffer Cache – : mean number of arriving customers/second –Tser: mean time to service a customer (“m1”) –C: squared coefficient of variance = 2/m12 –μ: service rate = 1/Tser th April 11 , 2019 –u: server utilization (0u1): u = /μ = Tser • Parameters we wish to compute: Prof. Ion Stoica –Tq: Time spent in queue http://cs162.eecs.Berkeley.edu –Lq: Length of queue = Tq (by Little’s law) • Results: –Memoryless service distribution (C = 1): » Called M/M/1 queue: Tq = Tser x u/(1 – u) –General service distribution (no restrictions), 1 server: » Called M/G/1 queue: Tq = Tser x ½(1+C) x u/(1 – u)) 4/11/19 Kubiatowicz CS162 © UCB Spring 2019 Lec 19.2 Recall: FAT Properties FAT Assessment – Issues • File is collection of disk blocks • Time to find block (large files) ?? (Microsoft calls them “clusters”) FAT Disk Blocks FAT Disk Blocks • FAT is array of integers mapped • Block layout for file ??? 1-1 with disk blocks 0: 0: 0: 0: File #1 File #1 – Each integer is either: • Sequential Access ??? » Pointer to next block in file; or 31: File 31, Block 0 31: File 31, Block 0 » End of file flag; or File 31, Block 1 File 31, Block 1 » Free block flag File 63, Block 1 • Random Access ??? File 63, Block 1 • File Number -

Open Source Licenses Applicable to Hitachi's Products Earlier Versions
Open Source Licenses Applicable to Hitachi’s Products EARLIER VERSIONS Several products are listed below together with certain open source licenses applicable to the particular product. The open source software licenses are included at the end of this document. If the open source package has been modified, an asterisk (*) appears next to the name of the package. Note that the source code for packages licensed under the GNU General Public License or similar type of license that requires the licensor to make the source code publicly available (“GPL Software”) may be available for download as indicated below. If the source code for GPL Software is not included in the software or available for download, please send requests for source code for GPL Software to the contact person listed for the applicable product. The materials below are provided “AS IS,” without warranty of any kind, including, but not limited to, the implied warranties of merchantability, fitness for a particular purpose, and non-infringement. Access to this material grants you no right or license, express or implied, statutorily or otherwise, under any patent, trade secret, copyright, or any other intellectual property right of Hitachi Vantara Corporation (“Hitachi”). Hitachi reserves the right to change any material in this document, and any information and products on which this material is based, at any time, without notice. Hitachi shall have no responsibility or liability to any person or entity with respect to any damages, losses, or costs arising from the materials -

Northern Junket, Index
CTT3 I —•\ I •—I I I N D E I I X Digitized by the Internet Archive in 2011 with funding from Boston Library Consortium Member Libraries http://www.archive.org/details/northernjunketinOOpage I ND O NORTHERN JUNKI VOLUME 1. - NUMBER 1. THROUGH VOLUME 14.- NUMBER 9 APRIL 1949. THROUGH JULY 1984. RALPH PAGE - EDITOR AND PUBLISHER. INDEX Compiled and Published by Roger Knox INDEX TO NORTHERN JUNKET COPYRIGHT 1985 by Roger C. Knox Roger C. Knox 702 North Tioga Street Ithaca, NY 14850 TO THE MEMORY OF RALPH PAGE THIS WORK IS RESPECTFULLY AND AFFECTIONATELY DEDICATED "He was a very special human being." (Dave Fuller) "It was a sad day for the dance world when he passed on. He left thousands of friends, and probably hundreds of his-taught Contra-callers who will perpetuate his memory for some time to come." (Beverly B. Wilder Jr.) "All who knew him have suffered a great loss." (Lannie McQuaide) "About very few can it be truly said that 'He was a legend in his own time,' but Ralph certainly was and is such a legend. The world of dance is a richer place because he was here." (Ed Butenhof) ACKNOWLEDGEMENTS There is a danger when one starts naming those who helped in a task that someone may have been left off the "Honor Roll." To avoid that problem 1 wish to thank everyone who gave me any encouragement, advice, orders for the Index, or anything else one can imagine. I wish specifically to thank several people who played an important role in this endeavor and I will risk the wrath of someone I may have missed but who will nevertheless live in my heart forever. -

Using the Andrew File System with BSD
Using the Andrew File System with BSD H. Meiland May 4, 2006 Abstract Since the beginning of networks, one of the basic idea’s has been sharing of files; even though with the Internet as advanced as today, simple platform independent file sharing is not common. Why is the closest thing we use WebDAV, a ’neat trick over http’, instead of a real protocol? In this paper the Andrew File System will be described which has been (and is) the file sharing core of many universities and companies world- wide. Also the reason for it’s relative unawareness in the community will be answered, and it’s actual features and performance in comparison with alternative network filesystems. Finally some information will be given on how to use it with our favorite OS: BSD. 1 History • 1984 Carnegie Mellon University, first release • 1989 TransArc Corporation formed by part of original team members • 1994 TransArc purchased by IBM • 1997 Start of Arla development at stacken.kth.se • 2000 IBM releases AFS in opensource (IBM License) • 2000 http://www.OpenAFS.org • 2006 good support for lot’s of platforms, many new features etc. 1 2 Overview 2.1 User point of view 2.1.1 Global namespace While discussing global filesystem, it is easy to dive into a organization, and explain wonderfull features like having replicas of often accessed data in branch-offices, and moving home-directories to local fileservers when mov- ing employees between departments. An essential feature of AFS is often overlooked: a common root as accesspoint of all AFS stored data. -

Introduction to Free Software-SELF
Introduction to Free Software Jordi Mas Hernández (coordinador) David Megías Jiménez (coordinador) Jesús M. González Barahona Joaquín Seoane Pascual Gregorio Robles XP07/M2101/02708 © FUOC • XP07/M2101/02708 Introduction to Free Software Jordi Mas Hernández David Megías Jiménez Jesús M. González Barahona Founding member of Softcatalà and Computer Science Engineer by the Professor in the Department of Tele- of the telematic network RedBBS. Universitat Autònoma de Barcelona matic Systems and Computation of He has worked as a consultant in (UAB, Spain). Master in Advanced the Rey Juan Carlos University (Ma- companies like Menta, Telépolis, Vo- Process Automatisation Techniques drid, Spain), where he coordinates dafone, Lotus, eresMas, Amena and by the UAB. PhD. in Computer Sci- the research group LibreSoft. His Terra España. ence by the UAB. Associate Profes- professional areas of interest include sor in the Computer Science, Multi- the study of free software develop- media and Telecommunication De- ment and the transfer of knowledge partment of the Universitat Oberta in this field to the industrial sector. de Catalunya (UOC, Spain) and Di- rector of the Master Programme in Free Software at the UOC. Joaquín Seoane Pascual Gregorio Robles PhD. Enigeer of Telecommunicati- Assistant professor in the Rey Juan ons in the Politechnical University Carlos University (Madrid, Spain), of Madrid (Spain). He has worked where he acquired his PhD. de- in the private sector and has al- gree in February 2006. Besides his so taught in the Computer Scien- teaching tasks, he researches free ce Faculty of that same university. software development from the Nowadays he is professor in the De- point of view of software enginee- partment of Telematic Systems En- ring, with special focus in quantitati- gineering, and has taught courses ve issues.