A Software of Visiblitlity Graph with Multiple Reflection and Its Application of Wireless Communication Design
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

3 Polygons in Architectural Design
ARTS IMPACT LESSON PLAN Vis ual Arts and Math Infused Lesson Lesson Three: Polygons in Architectural Design Author: Meredith Essex Grade Level: Fifth Enduring Understanding Polygons are classified according to properties and can be combined in architectural designs. Lesson Description (Use for family communication and displaying student art) Students praCtiCe drawing a variety of geometriC figures using math/arChitectural drawing tools. Students then observe, name, and Classify polygons seen in urban photos and arChitectural plans. Students design a bridge, tower, or building combining three different kinds of triangles and three different kinds of quadrilaterals. Pencil drawings are traced in pen, and arChiteCtural details/ patterns are added. Last, students reflect on and Classify 2-dimensional figures seen in their arChiteCtural designs. Learning Targets and Assessment Criteria Target: Classifies 2-dimensional figures. Criteria: Identifies and desCribes polygon figures, and properties of their sides, and angles seen in art. Target: Combines polygons in an arChiteCtural design. Criteria: Designs a structure made of straight sided shapes that include three kinds of triangles and three kinds of quadrilaterals. Target: Refines design. Criteria: TraCes over drawing in pen, adds arChiteCtural details and patterns. Target: Uses Craftsmanship. Criteria: Uses grid, rulers, and templates in drawing design. Vocabulary Materials Learning Standards Arts Infused: Museum Artworks or Performance: WA Arts State Grade Level Expectations GeometriC shape -

Sweeping the Sphere
Sweeping the Sphere Joao˜ Dinis Margarida Mamede Departamento de F´ısica CITI, Departamento de Informatica´ Faculdade de Ciencias,ˆ Universidade de Lisboa Faculdade de Cienciasˆ e Tecnologia, FCT Campo Grande, Edif´ıcio C8 Universidade Nova de Lisboa 1749-016 Lisboa, Portugal 2829-516 Caparica, Portugal [email protected] [email protected] Abstract—We introduce the first sweep line algorithm for and Hong [5], [6], which is O(n log n) worst case optimal, computing spherical Voronoi diagrams, which proves that where n is the number of sites. An asymptotically slower Fortune’s method can be extended to points on a sphere alternative in the worst case is the randomized incremental surface. This algorithm is similar to Fortune’s plane sweep algorithm, sweeping the sphere with a circular line instead of algorithm of Clarkson and Shor [7], whose expected running a straight one. time is O(n log n). The well-known Quickhull algorithm of Like its planar counterpart, the novel linear-space algorithm Barber et al. [8] can be seen as an efficient variation of the has worst-case optimal running time. Furthermore, it copes previous algorithm. very well with degeneracies and is easy to implement. Experi- A different approach is to adapt the randomized incremen- mental results show that the performance of our algorithm is very similar to that of Fortune’s algorithm, both with synthetic tal algorithm that computes the planar Delaunay triangula- data sets and with real data. tion [9], [10]. The essential operation used in the incremental The usual solutions make use of the connection between step, which checks if a circle defined by three sites contains a convex hulls and spherical Delaunay triangulations. -

Uwaterloo Latex Thesis Template
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by University of Waterloo's Institutional Repository Approximation Algorithms for Geometric Covering Problems for Disks and Squares by Nan Hu A thesis presented to the University of Waterloo in fulfillment of the thesis requirement for the degree of Master of Mathematics in Computer Science Waterloo, Ontario, Canada, 2013 c Nan Hu 2013 I hereby declare that I am the sole author of this thesis. This is a true copy of the thesis, including any required final revisions, as accepted by my examiners. I understand that my thesis may be made electronically available to the public. ii Abstract Geometric covering is a well-studied topic in computational geometry. We study three covering problems: Disjoint Unit-Disk Cover, Depth-(≤ K) Packing and Red-Blue Unit- Square Cover. In the Disjoint Unit-Disk Cover problem, we are given a point set and want to cover the maximum number of points using disjoint unit disks. We prove that the problem is NP-complete and give a polynomial-time approximation scheme (PTAS) for it. In Depth-(≤ K) Packing for Arbitrary-Size Disks/Squares, we are given a set of arbitrary-size disks/squares, and want to find a subset with depth at most K and maxi- mizing the total area. We prove a depth reduction theorem and present a PTAS. In Red-Blue Unit-Square Cover, we are given a red point set, a blue point set and a set of unit squares, and want to find a subset of unit squares to cover all the blue points and the minimum number of red points. -

GPU Rasterization for Real-Time Spatial Aggregation Over Arbitrary Polygons
GPU Rasterization for Real-Time Spatial Aggregation over Arbitrary Polygons Eleni Tzirita Zacharatou∗‡, Harish Doraiswamy∗†, Anastasia Ailamakiz, Claudio´ T. Silvay, Juliana Freirey z Ecole´ Polytechnique Fed´ erale´ de Lausanne y New York University feleni.tziritazacharatou, anastasia.ailamakig@epfl.ch fharishd, csilva, [email protected] ABSTRACT Not surprisingly, the problem of providing efficient support for Visual exploration of spatial data relies heavily on spatial aggre- visualization tools and interactive queries over large data has at- gation queries that slice and summarize the data over different re- tracted substantial attention recently, predominantly for relational gions. These queries comprise computationally-intensive point-in- data [1, 6, 27, 30, 31, 33, 35, 56, 66]. While methods have also been polygon tests that associate data points to polygonal regions, chal- proposed for speeding up selection queries over spatio-temporal lenging the responsiveness of visualization tools. This challenge is data [17, 70], these do not support interactive rates for aggregate compounded by the sheer amounts of data, requiring a large num- queries, that slice and summarize the data in different ways, as re- ber of such tests to be performed. Traditional pre-aggregation ap- quired by visual analytics systems [4, 20, 44, 51, 58, 67]. proaches are unsuitable in this setting since they fix the query con- Motivating Application: Visual Exploration of Urban Data Sets. straints and support only rectangular regions. On the other hand, In an effort to enable urban planners and architects to make data- query constraints are defined interactively in visual analytics sys- driven decisions, we developed Urbane, a visualization framework tems, and polygons can be of arbitrary shapes. -

Visibility Graphs and Cell Decompositions
Visibility Graphs and Cell Decompositions CIS 390 Kostas Daniilidis With material from Chapter 5 - Roadmaps Principles of Robot Motion: Theory, Algorithms, and Implementation by Howie ChosetÂet al. The MIT Press © 2005 For polygonal obstacles in 2D • Assume robot is a point • Any shortest path from start to goal among a set of disjoint polygonal obstacles is a polygonal path whose inner vertices are convex vertices of the obstacles (imagine a tight rope from start to end) Visibility graph • Vertices: all vertices of the polygonal obstacles plus the start and the goal • Edges: all line segments between vertices that do not intersect obstacles • It is not a planar graph: edges are crossing (not at vertices) Visibility graph construction • Brute force O(n^3) algorithm visits – all n vertices – applies a rotational plane sweep that connects with all other n vertices – and determines whether each segment intersects any of the O(n) edges • We can do better by sorting the vertices. Sweep Line Algorithm • Input: A set of vertices {νi} (whose edges do not intersect) and a vertex ν • Output: A subset of vertices from {νi} that are within line of sight of ν • 1: For each vertex vi, calculate αi, the angle from the horizontal axis to the line segment • ννi. • 2: Create the vertex list E , containing the αi 's sorted in increasing order. • 3: Create the active list S, containing the sorted list of edges that intersect the horizontal • half-line emanating from ν. • 4: for all αi do • 5: if νi is visible to ν then • 6: Add the edge (ν, νi )to the visibility graph. -

A Visibility-Based Approach to Computing Non-Deterministic
Article The International Journal of Robotics Research 1–16 A visibility-based approach to computing Ó The Author(s) 2021 Article reuse guidelines: non-deterministic bouncing strategies sagepub.com/journals-permissions DOI: 10.1177/0278364921992788 journals.sagepub.com/home/ijr Alexandra Q Nilles1 , Yingying Ren1, Israel Becerra2,3 and Steven M LaValle1,4 Abstract Inspired by motion patterns of some commercially available mobile robots, we investigate the power of robots that move forward in straight lines until colliding with an environment boundary, at which point they can rotate in place and move forward again; we visualize this as the robot ‘‘bouncing’’ off boundaries. We define bounce rules governing how the robot should reorient after reaching a boundary, such as reorienting relative to its heading prior to collision, or relative to the normal of the boundary. We then generate plans as sequences of rules, using the bounce visibility graph generated from a polygonal environment definition, while assuming we have unavoidable non-determinism in our actuation. Our planner can be queried to determine the feasibility of tasks such as reaching goal sets and patrolling (repeatedly visiting a sequence of goals). If the task is found feasible, the planner provides a sequence of non-deterministic interaction rules, which also provide information on how precisely the robot must execute the plan to succeed. We also show how to com- pute stable cyclic trajectories and use these to limit uncertainty in the robot’s position. Keywords Underactuated robots, dynamics, motion control, motion planning 1. Introduction approach is powerful and well-suited to dynamic environ- ments, but also resource-intensive in terms of energy, Mobile robots have rolled smoothly into our everyday computation, and storage space. -

On Visibility Problems in the Plane – Solving Minimum Vertex Guard Problems by Successive Approximations ?
On Visibility Problems in the Plane – Solving Minimum Vertex Guard Problems by Successive Approximations ? Ana Paula Tomas´ 1, Antonio´ Leslie Bajuelos2 and Fabio´ Marques3 1 DCC-FC & LIACC, University of Porto, Portugal [email protected] 2 Dept. of Mathematics & CEOC - Center for Research in Optimization and Control, University of Aveiro, Portugal [email protected] 3 School of Technology and Management, University of Aveiro, Portugal [email protected] Abstract. We address the problem of stationing guards in vertices of a simple polygon in such a way that the whole polygon is guarded and the number of guards is minimum. It is known that this is an NP-hard Art Gallery Problem with relevant practical applications. In this paper we present an approximation method that solves the problem by successive approximations, which we intro- duced in [21]. We report on some results of its experimental evaluation and des- cribe two algorithms for characterizing visibility from a point, that we designed for its implementation. 1 Introduction The classical Art Gallery problem for a polygon P is to find a minimum set of points G in P such that every point of P is visible from some point of G. We address MINIMUM VERTEX GUARD in which the set of guards G is a subset of the vertices of P and each guard has 2π range unlimited visibility. This is an NP-hard combinatorial problem both for arbitrary and orthogonal polygons [13, 17]. Orthogonal (i.e. rectilinear) polygons are interesting for they may be seen as abstractions of art galleries, for instance. -

Efficient Computation of Visibility Polygons
EuroCG 2014, Ein-Gedi, Israel, March 3{5, 2014 Efficient Computation of Visibility Polygons Francisc Bungiu∗ Michael Hemmery John Hershbergerz Kan Huangx Alexander Kr¨ollery Abstract a subroutine in algorithms for other problems, most prominently in the context of the Art Gallery Prob- Determining visibility in planar polygons and ar- lem [16]. In experimental work on this problem [15] rangements is an important subroutine for many al- we have identified visibility computations as having a gorithms in computational geometry. In this paper, substantial impact on overall computation times, even we report on new implementations, and correspond- though it is a low-order polynomial-time subroutine in ing experimental evaluations, for two established and an algorithm solving an NP-hard problem. Therefore one novel algorithm for computing visibility polygons. it is of enormous interest to have efficient implemen- These algorithms will be released to the public shortly, tations of visibility polygon algorithms available. as a new package for the Computational Geometry CGAL, the Computational Geometry Algorithms Algorithms Library (CGAL). Library [5], contains a large number of algorithms and data structures, but unfortunately not for the 1 Introduction computation of visibility polygons. We present im- plementations for three algorithms, which form the Visibility is a basic concept in computational geome- basis for an upcoming new CGAL package for visi- try. For a polygon P R2, we say that a point p P bility. Two of these are efficient implementations for ⊂ 2 is visible from q P if the line segment pq P . The standard O(n)- and O(n log n)-time algorithms from 2 ⊆ points that are visible from q form the visibility re- the literature. -

Representing Whole Slide Cancer Image Features with Hilbert Curves Authors
Representing Whole Slide Cancer Image Features with Hilbert Curves Authors: Erich Bremer, Jonas Almeida, and Joel Saltz Erich Bremer (corresponding author) [email protected] Stony Brook University Biomedical Informatics Jonas Almeida [email protected] National Cancer Institute Division of Cancer Epidemiology & Genetics Joel Saltz [email protected] Stony Brook University Biomedical Informatics Abstract Regions of Interest (ROI) contain morphological features in pathology whole slide images (WSI) are [1] delimited with polygons . These polygons are often represented in either a textual notation (with the array of edges) or in a binary mask form. Textual notations have an advantage of human readability and portability, whereas, binary mask representations are more useful as the input and output of feature-extraction pipelines that employ deep learning methodologies. For any given whole slide image, more than a million cellular features can be segmented generating a corresponding number of polygons. The corpus of these segmentations for all processed whole slide images creates various challenges for filtering specific areas of data for use in interactive real-time and multi-scale displays and analysis. Simple range queries of image locations do not scale and, instead, spatial indexing schemes are required. In this paper we propose using Hilbert Curves simultaneously for spatial indexing and as a polygonal ROI [2] representation. This is achieved by using a series of Hilbert Curves creating an efficient and inherently spatially-indexed machine-usable form. The distinctive property of Hilbert curves that enables both mask and polygon delimitation of ROIs is that the elements of the vector extracted ro describe morphological features maintain their relative positions for different scales of the same image. -
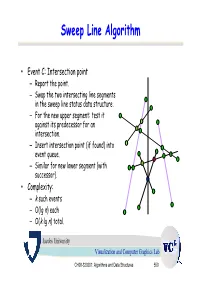
Sweep Line Algorithm
Sweep Line Algorithm • Event C: Intersection point – Report the point. – Swap the two intersecting line segments in the sweep line status data structure. – For the new upper segment: test it against its predecessor for an intersection. – Insert intersection point (if found) into event queue. – Similar for new lower segment (with successor). • Complexity: – k such events – O(lg n) each – O(k lg n) total. Jacobs University Visualization and Computer Graphics Lab CH08-320201: Algorithms and Data Structures 550 Example a3 b4 Sweep Line status: s3 e1 s4 s0, s1, s2, s3 Event Queue: a2 a4 b3 a4, b1, b2, b0, b3, b4 s2 b1 b0 s1 b2 s0 a1 a0 Jacobs University Visualization and Computer Graphics Lab CH08-320201: Algorithms and Data Structures 551 Example a3 b4 Actions: s3 Insert s4 to SLS e1 s4 Test s4-s3 and s4-s2. a2 a4 b3 Add e1 to EQ s2 b1 Sweep Line status: b0 s1 b2 s0, s1, s2, s4, s3 s0 a1 a0 Event Queue: b1, e1, b2, b0, b3, b4 Jacobs University Visualization and Computer Graphics Lab CH08-320201: Algorithms and Data Structures 552 Example a3 b4 Actions: s3 e1 s4 Delete s1 from SLS Test s0-s2. a2 a4 b3 Add e2 to EQ s2 Sweep Line status: e2 b0 b1 s1 b2 s0, s2, s4, s3 s0 a1 a0 Event Queue: e1, e2, b2, b0, b3, b4 Jacobs University Visualization and Computer Graphics Lab CH08-320201: Algorithms and Data Structures 553 Example a3 b4 Actions: s3 e1 s4 Swap s3 and s4 in SLS Test s3-s2. -

Parallel Range, Segment and Rectangle Queries with Augmented Maps
Parallel Range, Segment and Rectangle Queries with Augmented Maps Yihan Sun Guy E. Blelloch Carnegie Mellon University Carnegie Mellon University [email protected] [email protected] Abstract The range, segment and rectangle query problems are fundamental problems in computational geometry, and have extensive applications in many domains. Despite the significant theoretical work on these problems, efficient implementations can be complicated. We know of very few practical implementations of the algorithms in parallel, and most implementations do not have tight theoretical bounds. In this paper, we focus on simple and efficient parallel algorithms and implementations for range, segment and rectangle queries, which have tight worst-case bound in theory and good parallel performance in practice. We propose to use a simple framework (the augmented map) to model the problem. Based on the augmented map interface, we develop both multi-level tree structures and sweepline algorithms supporting range, segment and rectangle queries in two dimensions. For the sweepline algorithms, we also propose a parallel paradigm and show corresponding cost bounds. All of our data structures are work-efficient to build in theory (O(n log n) sequential work) and achieve a low parallel depth (polylogarithmic for the multi-level tree structures, and O(n) for sweepline algorithms). The query time is almost linear to the output size. We have implemented all the data structures described in the paper using a parallel augmented map library. Based on the library each data structure only requires about 100 lines of C++ code. We test their performance on large data sets (up to 108 elements) and a machine with 72-cores (144 hyperthreads). -

Parallel Geometric Algorithms. Fenglien Lee Louisiana State University and Agricultural & Mechanical College
Louisiana State University LSU Digital Commons LSU Historical Dissertations and Theses Graduate School 1992 Parallel Geometric Algorithms. Fenglien Lee Louisiana State University and Agricultural & Mechanical College Follow this and additional works at: https://digitalcommons.lsu.edu/gradschool_disstheses Recommended Citation Lee, Fenglien, "Parallel Geometric Algorithms." (1992). LSU Historical Dissertations and Theses. 5391. https://digitalcommons.lsu.edu/gradschool_disstheses/5391 This Dissertation is brought to you for free and open access by the Graduate School at LSU Digital Commons. It has been accepted for inclusion in LSU Historical Dissertations and Theses by an authorized administrator of LSU Digital Commons. For more information, please contact [email protected]. INFORMATION TO USERS This manuscript has been reproduced from the microfilm master. UMI films the text directly from the original or copy submitted. Thus, some thesis and dissertation copies are in typewriter face, while others may be from any type of computer printer. The quality of this reproduction is dependent upon the quality of the copy submitted. Broken or indistinct print, colored or poor quality illustrations and photographs, print bleedthrough, substandard margins, and improper alignment can adversely affect reproduction. In the unlikely event that the author did not send UMI a complete manuscript and there are missing pages, these will be noted. Also, if unauthorized copyright material had to be removed, a note will indicate the deletion. Oversize materials (e.g., maps, drawings, charts) are reproduced by sectioning the original, beginning at the upper left-hand corner and continuing from left to right in equal sections with small overlaps. Each original is also photographed in one exposure and is included in reduced form at the back of the book.