Modern Game Console Exploitation
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Avionics Hardware Issues 2010/11/19 Chih-Hao Sun Avionics Software--Hardware Issue -History
Avionics Hardware Issues 2010/11/19 Chih-hao Sun Avionics Software--Hardware Issue -History -HW Concepts History -FPGA vs ASIC The Gyroscope, the first auto-pilot device, was -Issues on • Avionics Computer introduced a decade after the Wright Brothers -Avionics (1910s) Computer -PowerPC • holds the plane level automatically -Examples -Energy Issue • is connected to computers for missions(B-17 and - Certification B-29 bombers) and Verification • German V-2 rocket(WWII) used the earliest automatic computer control system (automatic gyro control) • contains two free gyroscopes (a horizontal and a vertical) 2 Avionics Software--Hardware Issue -History -HW Concepts History -FPGA vs ASIC Avro Canada CF-105 Arrow fighter (1958) first used -Issues on • Avionics Computer analog computer to improve flyability -Avionics Computer is used to reduce tendency to yaw back and forth -PowerPC • -Examples F-16 (1970s) was the first operational jet fighter to use a -Energy Issue • fully-automatic analog flight control system (FLCS) - Certification and Verification • the rudder pedals and joysticks are connected to “Fly-by-wire” control system, and the system adjusts controls to maintain planes • contains three computers (for redundancy) 3 Avionics Software--Hardware Issue -History -HW Concepts History -FPGA vs ASIC NASA modified Navy F-8 with digital fly-by wire system in -Issues on • Avionics Computer 1972. -Avionics Computer • MD-11(1970s) was the first commercial aircraft to adopt -PowerPC computer-assisted flight control -Examples -Energy Issue The Airbus A320 series, late 1980s, used the first fully-digital - • Certification fly-by-wire controls in a commercial airliner and Verification • incorporates “flight envelope protection” • calculates that flight envelope (and adds a margin of safety) and uses this information to stop pilots from making aircraft outside that flight envelope. -

Computer Game Mods, Modders, Modding, and the Mod Scene
Computer Game Mods, Modders, Modding, and the Mod Scene Walt Scacchi Institute for Software Research and Center for Computer Games and Virtual Worlds University of California, Irvine 92697-3455 USA March 2010 Abstract Computer games have increasingly been the focus of user-led innovations in the form of game mods. This paper examines how different kinds of socio-technical affordances serve to organize the actions of the people who develop and share their game mods. The affordances examined include customization and tailoring mechanisms, software and content copyright licenses, game software infrastructure and development tools, career contingencies and organizational practices of mod teams, and social worlds intersecting the mod scene. Numerous examples will be used to ground this review and highlight how such affordances can organize, facilitate or constrain what can be done. Overall, this study helps to provide a deeper understanding of how a web of associated affordances collectively serve to govern what mods get made, how modding practices emerge and flourish, and how modders and the game industry serve each others' interests, though not always in equivocal terms. Introduction Computer game mods are a leading form of user-led innovation in game design and game play experience. But modded games are not standalone systems, as they require the user to have an originally acquired or authorized copy of the unmodded game. Thus, there are questions of not only who creates what and who owns such modified games, but also whether or how the practice of game modding is controlled or governed by external parties to ultimately exploit the efforts of game modders. -

CS 6290 Chapter 1
Spring 2011 Prof. Hyesoon Kim Xbox 360 System Architecture, „Anderews, Baker • 3 CPU cores – 4-way SIMD vector units – 8-way 1MB L2 cache (3.2 GHz) – 2 way SMT • 48 unified shaders • 3D graphics units • 512-Mbyte DRAM main memory • FSB (Front-side bus): 5.4 Gbps/pin/s (16 pins) • 10.8 Gbyte/s read and write • Xbox 360: Big endian • Windows: Little endian http://msdn.microsoft.com/en-us/library/cc308005(VS.85).aspx • L2 cache : – Greedy allocation algorithm – Different workloads have different working set sizes • 2-way 32 Kbyte L1 I-cache • 4-way 32 Kbyte L1 data cache • Write through, no write allocation • Cache block size :128B (high spatial locality) • 2-way SMT, • 2 insts/cycle, • In-order issue • Separate vector/scalar issue queue (VIQ) Vector Vector Execution Unit Instructions Scalar Scalar Execution Unit • First game console by Microsoft, released in 2001, $299 Glorified PC – 733 Mhz x86 Intel CPU, 64MB DRAM, NVIDIA GPU (graphics) – Ran modified version of Windows OS – ~25 million sold • XBox 360 – Second generation, released in 2005, $299-$399 – All-new custom hardware – 3.2 Ghz PowerPC IBM processor (custom design for XBox 360) – ATI graphics chip (custom design for XBox 360) – 34+ million sold (as of 2009) • Design principles of XBox 360 [Andrews & Baker] - Value for 5-7 years -!ig performance increase over last generation - Support anti-aliased high-definition video (720*1280*4 @ 30+ fps) - extremely high pixel fill rate (goal: 100+ million pixels/s) - Flexible to suit dynamic range of games - balance hardware, homogenous resources - Programmability (easy to program) Slide is from http://www.cis.upenn.edu/~cis501/lectures/12_xbox.pdf • Code name of Xbox 360‟s core • Shared cell (playstation processor) ‟s design philosophy. -

Smart Home Automation with Linux Smart
CYAN YELLOW MAGENTA BLACK PANTONE 123 C BOOKS FOR PROFESSIONALS BY PROFESSIONALS® THE EXPERT’S VOICE® IN LINUX Companion eBook Available Smart Home Automation with Linux Smart Dear Reader, With this book you will turn your house into a smart and automated home. You will learn how to put together all the hardware and software needed for Automation Home home automation, to control appliances such as your teakettle, CCTV, light switches, and TV. You’ll be taught about the devices you can build, adapt, or Steven Goodwin, Author of hack yourself from existing technology to accomplish these goals. Cross-Platform Game In Smart Home Automation with Linux, you’ll discover the scope and possi- Programming bilities involved in creating a practical digital lifestyle. In the realm of media and Game Developer’s Open media control, for instance, you’ll learn how you can read TV schedules digitally Source Handbook and use them to program video remotely through e-mail, SMS, or a web page. You’ll also learn the techniques for streaming music and video from one machine to another, how to give your home its own Twitter and e-mail accounts for sending automatic status reports, and the ability to remotely control the home Smart Home lights or heating system. Also, Smart Home Automation with Linux describes how you can use speech synthesis and voice recognition systems as a means to converse with your household devices in new, futuristic, ways. Additionally, I’ll also show you how to implement computer-controlled alarm clocks that can speak your daily calendar, news reports, train delays, and local with weather forecasts. -
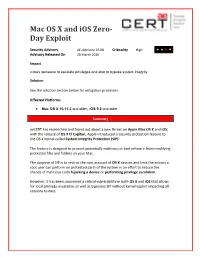
Mac OS X and Ios Zero- Day Exploit
Mac OS X and iOS Zero- Day Exploit Security Advisory AE-Advisory 16-08 Criticality High Advisory Released On 28 March 2016 Impact Allows someone to escalate privileges and also to bypass system integrity Solution See the solution section below for mitigation processes. Affected Platforms Mac OS X 10.11.3 and older, iOS 9.2 and older Summary aeCERT has researched and found out about a new threat on Apple Mac OS X and iOS; with the release of OS X El Capitan, Apple introduced a security protection feature to the OS X kernel called System Integrity Protection (SIP). The feature is designed to prevent potentially malicious or bad software from modifying protected files and folders on your Mac. The purpose of SIP is to restrict the root account of OS X devices and limit the actions a root user can perform on protected parts of the system in an effort to reduce the chance of malicious code hijacking a device or performing privilege escalation. However, it has been uncovered a critical vulnerability in both OS X and iOS that allows for local privilege escalation as well as bypasses SIP without karnel exploit impacting all versions to date. Threat Details The zero day vulnerability is a Non-Memory Corruption bug that allows hackers to execute arbitrary code on any targeted machine, perform remote code execution (RCE) or sandbox escapes. The attacker then escalates the malware's privileges to bypass System Integrity Protection SIP, alter system files, and then stay on the infected system. By default, System Integrity Protection or SIP protects these folders: /System. -

Boisvert-Storey-Sony Case Brief
Storey C204 Summer 2014 Case Study BE MOVED SITUATION Sony Corporation is a 68-year old multinational based in Tokyo. In 2012, the tech giant employed 173,000 people, with corporate headquarters in Japan, Europe, and America. In May 2014, the company was down to 146,300, cutting 26,700 as part of CEO Kaz Hirai’s “One Sony” plan. Recently, the firm eVen sold former office buildings in Tokyo for $156 million (Inagaki). This followed a similar $1.2 billion sale in 2013. After seVeral years of losses, Sony’s situation appears critical. In the last fiscal year, the company lost $1.25 billion. EVen the gaming diVision, where the Playstation console family (PS2, PS3, PS4) is projected to sell 17 million units this year, lost $78 million (Quarterly Results). There are many causes: Sony’s jettisoning of its PC brand Vaio, the poor performance and planned spinoff of Sony’s teleVision diVision, PS4 launch and marketing costs, the struggling PSVita, R&D costs for Sony’s Project Morpheus, and the fluctuation of exchange rate markets. For the current year, Sony is projecting a $489 million loss. How sustainable is Sony’s current business model? Will the success of the PS4 lead to renewed profitability for the games diVision and the company as a whole? Perhaps opportunities in new markets can spark a turn-around. The company’s core businesses are electronic entertainment (Sony Computer Entertainment, Sony Music Entertainment, and Sony Pictures Entertainment) and hardware (Sony Mobile Communications and Sony Electronics). Though it also dabbles in financial serVices, publishing, and medical imaging, electronics represents roughly two-thirds of the corporation’s reVenue (Sony Annual Report 2011, 2013). -
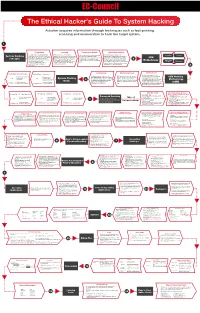
Download the Ethical Hacker's Guide to System Hacking
The Ethical Hacker's Guide To System Hacking Attacker acquires information through techniques such as foot printing, scanning and enumeration to hack the target system. 1 Footprinting Scanning Enumeration Module Vulnerability Analysis It is the process of accumulating data Vulnerability Assessment is an This is a procedure for identifying This is a method of intrusive probing, Footprinting Scanning System Hacking regarding a specific network environment. active hosts, open ports, and unnecessary through which attackers gather examination of the ability of a system or In this phase, the attacker creates a profile services enabled on ports. Attackers use information such as network user lists, application, including current security CEH concepts of the target organization, obtaining different types of scanning, such as port routing tables, security flaws, and procedures, and controls to with stand 2 information such as its IP address range, scanning network scanning, and simple network protocol data (SNMP) assault. Attackers perform this analysis Methodology Vulnerability namespace and employees. Enumeration vulnerability, scanning of target networks data. to identify security loopholes, in the target Analysis Footprinting eases the process of or systems which help in identifying organization’s network, communication system hacking by revealing its possible vulnerabilities. infrastructure, and end systems. vulnerabilities 3 Clearing Logs Maintaining Access Gaining Access Hacking Stage Escalating Privileges Hacking Stage Gaining Access It involves gaining access to To maintain future system access, After gaining access to the target low-privileged user accounts by To acquire the rights of To bypass access CEH Hacking attackers attempt to avoid recognition system, attackers work to maintain cracking passwords through Goal another user or Goal controls to gain System Hacking by legitimate system users. -

Copy Protection Wars: Analyzing Retro and Modern Schemes Disk
Copy Protection Wars: Analyzing Retro and Modern Schemes Copy Protection Wars: Analyzing Retro and Modern Schemes Nate Lawson Cryptography Research, Inc. Hackers & Threats II (1450) February 6 th , 2007 Which copy protection era are you? Disk drive…? 2006 1996 1986 Copyright © 2006-2007 Cryptography Research, Inc. 1 Copy Protection Wars: Analyzing Retro and Modern Schemes Which copy protection era are you? Modchip…? 2006 1996 1986 (Xbox360) (Sony PS1) (Commodore 1541 floppy) Which copy protection era are you? ANSI…? 2006 1996 1986 Copyright © 2006-2007 Cryptography Research, Inc. 2 Copy Protection Wars: Analyzing Retro and Modern Schemes Which copy protection era are you? Monitor…? 2006 1996 1986 Who am I? • Co-designer of the Blu-ray disc content protection layer (Cryptography Research) • Designer of ISS RealSecure network intrusion detection system • FreeBSD committer since 2002 — Author/maintainer of power management and ACPI kernel code, SCSI and USB • Contributor to C64 Preservation Project — Software for imaging original floppies and replicating copy protection schemes bit-for-bit Copyright © 2006-2007 Cryptography Research, Inc. 3 Copy Protection Wars: Analyzing Retro and Modern Schemes Why does the past matter? • Approaches are still the same as for C64 — Killer tracks = LaserLock CD/DVD protection — Track-to-track alignment = Xbox1/360 sector skew checks — Custom GCR encoding = ECC tricks, weak sectors • Many modern hackers linked to C64 scene — commodore4eva: Xbox360 drive firmware hacks — Michael Steil: Xbox1 MIST PCI hack = ? Legal support for retro-hacking • Excluded from DMCA anti-circumvention clause — Library of Congress ruling (every 3 years) • Copyright protection still applies so you must have original media • Seek legal advice before circumventing any protection — I’m not your lawyer! Exemptions: 2. -

Architecture of Hyper-Threading on Intel Xenon Processor
International Journal of Advanced Research in Electronics and Communication Engineering (IJARECE) Volume 4, Issue 4, April 2015 Architecture of Hyper-Threading on Intel Xenon Processor L.Jyothsna, IV/IV B.Tech, Dept. of Electronics and Computer Dr. K. Kiran kumar, Professor, Dept. of Electronics and Computer Abstract— Over the years, the computer architects were processor architecture. This performance is increased based on continuously devising new hard ware technologies to the number of instructions. That is when we increase the improve the system performance and to compete with the number of instructions the clock frequencies increased and advancements in software. Simultaneous Multithreading executed each second. Due to far more instructions in a super Technology (SMT) was one of the techniques where pipelining, micro architecture which manages the events that multiple threads can be simultaneously executed by a wrap the pipelining such as cache misses and interrupts. single processor without doing a context switch. Hyper- Threading, the Intel’s way of providing Simultaneous A. Hyper threading Technology Architecture: Multithreading Technology, adds a virtual thread along the side of a physical thread to increase the processing Normally a CPU can execute one instruction at a time by power of a processor. This paper combines the concepts of maintaining a single instruction pointer . And the processor can architecture of hyper-threading and its implementation on execute multiple threads by switching between the threads. In Intel’s xenon processor. The experimentation is done on Simultaneous Multithreading Technology (SMT), a single processor could simultaneously execute multiple threads Intel’s enterprise product line with wide variety of without context switching [7]. -

WORLDSPECIAL REPORT the Tech Behind Bitcoin Has Been Released
THE INSATIABLE DO YOU NEED THE BLOCK-CHAINING THE MONEY MINES BITCOIN BEAST A BLOCKCHAIN? OF WALL STREET OF MONGOLIA Cryptocurrency’s Find out in seconds A new platform for How watts coming energy crisis with our handy guide trading in the trillions become bitcoins P. 36 P. 38 P. 40 P. 46 FOR THE TECHNOLOGY INSIDER | 10.17 BLOCK- CHAIN WORLD SPECIAL REPORT The tech behind Bitcoin has been released into the wild. Here’s how it’s going to change the landscape P. 24 SUPERMICRO® BigTwin® The IT Industry’s Highest Performing Twin Multi-Node System 2U Multi-Node System Supporting • A Full Range of Processors Up to the highest performing 205 watt CPUs • Maximum Memory 3TB 24 DIMMs per node • All-Flash NVMe 24 All Flash NVMe or Hybrid NVMe/SAS3 drives • Double the I/O Capacity Three PCI-E 3.0 x16 options per node • Supports Intel® Xeon® Scalable Processors Intel Inside®. Powerful Productivity Outside. Learn more at supermicro.com/GPU © Super Micro Computer, Inc. Specifications subject to change without notice. Intel, the Intel logo, Xeon, and Xeon Inside are trademarks or registered trademarks of Intel Corporation in the U.S. and/or other countries. 10.17 Special Report: BLOCKCHAIN WORLD The Blossoming 26 Blockchains: How They 45 Blockchain Lingo Work and Why They’ll Change Your cheat sheet for all things blockchain. of Blockchain the World 24 Enthusiasts The technology behind Bitcoin could touch every 46 Photo Essay: are sure that transaction you ever make. By Morgen E. Peck The Bitcoin Mines of China This Bitcoin operation in Inner Mongolia uses blockchain 36 Feeding the sophisticated semiconductors to turn cheap, dirty technology is Blockchain Beast energy into digital cash. -

Android Exploits Commanding Higher Price Than Ever Before
Memo 10/09/2019 - TLP:WHITE Android exploits commanding higher price than ever before Reference: Memo [190910-1] – Version: 1.0 Keywords: Android, iOS, exploit, vulnerability Sources: Zerodium, Google, Wired Key Points The price of android exploits exceeds the price of iOS exploits for the first time This is possibly because Android security is improving over iOS The release of Android 10 is also a likely cause for the price hike Summary Zerodium1, a cyber security exploit broker dealing in zero-day vulnerabilities, has published its most recent price list. It indicates that the price of an Android full-chain exploit with persistence can fetch the developer up to 2,500,000 dollars. The going rate for a similar exploit for Apple’s iOS has gone down by 500,000 dollars and is now worth 2,000,000. This is the first confirmed time when Android exploits are valued more than iOS. Zerodium payouts for mobile devices Up to $2,500,000 Android zero click full compromise chain with persistence. Up to $2,000,000 iOS zero click full compromise chain with persistence. Up to $1,500,000 WhatsApp zero click remote code execution with iMessage remote code execution with local local privilege escalation on iOS or Android. privilege escalation. Up to $1,000,000 WhatsApp remote code execution with local privilege SMS/MMS remote code execution with local escalation on iOS or Android. privilege escalation on iOS or Android. Comments Zero-click exploits do not require interaction from the user. This is very difficult to achieve and thus commands the highest prices. -

Consumer Vs. Gamer Rights at Play
Consumer vs. gamer Rights at play February 2011 The Norwegian Consumer Council (NCC) is an independent, government-funded interest group working for a consumer-friendly society. The digital market is one of the NCC’s top priorities for the coming years. The Consumer Council is a supporter of games, gamer culture and gaming innovations. Thus, it is long overdue to ask the question: Is there a need for consumer rights for gamers? NCC’s digital charter consists of eight mandatory consumer rights for digital products legally available to consumers. The charter is the foundation of the Consumer Council’s work on digital services.1 This document highlights challenges related to core games and the platforms they are played on. As this is meant to serve as a starting point for our work on games, we do not go in depth with regards to casual games or games/apps for handheld devices such as phones or tablets. 1 http://forbrukerportalen.no/Artikler/2007/consumers_digital_rights 2 Introduction The market for pc- and console games has Connectivity has allowed game publishers to grown substantially the last years. In fact, the repair glitches, patch flaws and add content market has continuously grown over the last after the game is taken off the shelves. In many three or four decades. From being a quirky way cases this is a clear benefit for the gamer. But for scientists to put their room filling super- at the same time it opens up possibilities to computers to use, games are now household, target consumer groups for advertising, tap or even handheld, entertainment.