Improving Content Delivery and Service Discovery in Networks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Fortinet and Vyatta Fortinet and Vyatta
DEPLOYMENT GUIDE Fortinet and Vyatta Fortinet and Vyatta Overview . 3 Deployment Prerequisites . 3 Architecture Overview . 3 Figure 1: Topology.......................................... 3 Partner Configuration....................................... 4 Hardware Installation . 4 Figure 2: Vyatta Dashboard .................................. 4 Figure 3: Vyatta Virtualization ................................ 5 Fortinet Configuration . 5 Figure 4: Vyatta Virtualization Console Access .................. 5 Summary . 6 Access to Vyatta Demo . 6 How To Get Help........................................... 6 2 DEPLOYMENT GUIDE | Fortinet and Vyatta Overview The Brocade 5600 vRouter (formerly Vyatta 5600 vRouter) provides a solution Deployment Prerequisites for network functions virtualization (NFV). It offers easy scalability, a broad set of capabilities, and reliability. The Fortinet and Brocade Vyatta deployment requires the following: In addition, it utilizes Intel Data Plane Development Kit (DPDK) to deliver higher performance, and it can be installed on hypervisors and any x86-based system. 1. Vyatta OS Together, Fortinet and Brocade deliver an industry-leading security and network 2. Supermicro x86-Based Hardware solution. FortiGate virtual firewall products enable customers to deploy branch office 3. FortiGate KVM Firewall services. Customers can deploy virtual CPE (vCPE) combined with industry-leading FortiGate security. The Brocade Vyatta Network OS with Fortinet network security appliances and subscription services provides broad, integrated, -

Planning Guide
Oracle AutoVue 20.2, Client/Server Deployment Planning Guide March 2012 Copyright © 1999, 2012, Oracle and/or its affiliates. All rights reserved. Portions of this software Copyright 1996-2007 Glyph & Cog, LLC. Portions of this software Copyright Unisearch Ltd, Australia. Portions of this software are owned by Siemens PLM © 1986-2012. All rights reserved. This software uses ACIS® software by Spatial Technology Inc. ACIS® Copyright © 1994-2008 Spatial Technology Inc. All rights reserved. Oracle is a registered trademark of Oracle Corporation and/or its affiliates. Other names may be trademarks of their respective owners. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this software or related documentation is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Govern- ment, the following notice is applicable: U.S. GOVERNMENT RIGHTS Programs, software, databases, and related documentation and technical data delivered to U.S. Government customers are "com- mercial computer software" or "commercial technical data" pursuant to the applicable Federal Acquisition Regulation and agency- specific supplemental regulations. -

Dynamic Integration of Mobile JXTA with Cloud Computing for Emergency Rural Public Health Care
Osong Public Health Res Perspect 2013 4(5), 255e264 http://dx.doi.org/10.1016/j.phrp.2013.09.004 pISSN 2210-9099 eISSN 2233-6052 - ORIGINAL ARTICLE - Dynamic Integration of Mobile JXTA with Cloud Computing for Emergency Rural Public Health Care Rajasekaran Rajkumar*, Nallani Chackravatula Sriman Narayana Iyengar School of Computing Science and Engineering, VIT University, Vellore, India. Received: August 21, Abstract 2013 Objectives: The existing processes of health care systems where data collection Revised: August 30, requires a great deal of labor with high-end tasks to retrieve and analyze in- 2013 formation, are usually slow, tedious, and error prone, which restrains their Accepted: September clinical diagnostic and monitoring capabilities. Research is now focused on 3, 2013 integrating cloud services with P2P JXTA to identify systematic dynamic process for emergency health care systems. The proposal is based on the concepts of a KEYWORDS: community cloud for preventative medicine, to help promote a healthy rural ambulance alert alarm, community. We investigate the approaches of patient health monitoring, emergency care, and an ambulance alert alarm (AAA) under mobile cloud-based cloud, telecare or community cloud controller systems. JXTA, Methods: Considering permanent mobile users, an efficient health promotion mHealth, method is proposed. Experiments were conducted to verify the effectiveness of P2P the method. The performance was evaluated from September 2011 to July 2012. A total of 1,856,454 cases were transported and referred to hospital, identified with health problems, and were monitored. We selected all the peer groups and the control server N0 which controls N1,N2, and N3 proxied peer groups. -

Solving Quarto with JXTA and JNGI
Solving Quarto with JXTA and JNGI Matthew Shepherd University of Texas at Austin Abstract. This paper presents an implementation of a grid-based autonomous quarto player. The implementation uses the JNGI framework which itself is written on top of JXTA. 1 Introduction Quarto is a game reminiscent of tic-tac-toe. It is played with sixteen unique pieces on a four-by-four square board. Each piece is large or small, black or white, solid or hollow and square or round. The game begins with an empty board and all sixteen pieces available. Two players take successive turns with the first player choosing an available piece. That piece is given to the second player who places it on an empty spot on the board. The roles reverse and the process repeats. A player wins by placing the final piece in a row, column or diagonal where all four pieces have at least one attribute in common. For example, the winner might place a piece that completes a row of four black pieces or a column of four round pieces. My goal was to write an implementation of the game and an autonomous program for a human player to compete against. The program performs an exhaustive search of possible moves in order to find the most appropriate one. If the program were to perform the search on the first move of the game, the sixteen available pieces and sixteen empty squares would combine to produce a (16!)^2 search space. Eliminating the moves that take place after a game has already been won reduces that number, but a single processor would still not be sufficient to perform such a task in a reasonable amount of time. -

Extensions of JADE and JXTA for Implementing a Distributed System
EXTENSIONS OF JADE AND JXTA FOR IMPLEMENTING A DISTRIBUTED SYSTEM Edward Kuan-Hua Chen A THESIS SUBMITTED IN PARTIAL FULFILLMENT OF THE REQUIREMENTS FOR THE DEGREE OF MASTER OF APPLIED SCIENCE School of Engineering Science O Edward Kuan-Hua Chen 2005 SIMON FRASER UNIVERSITY Spring 2005 All rights reserved. This work may not be reproduced in whole or in part, by photocopy or other means, without the permission of the author. APPROVAL Edward Kuan-Hua Chen Master of Applied Science Extensions of JADE and JXTA for Implementing a Distributed System EXAMINING COMMITTEE Chair: John Jones Professor, School of Engineering Science William A. Gruver Academic Supervisor Professor, School of Engineering Science Dorian Sabaz Technical Supervisor Chief Technology Officer Intelligent Robotics Corporation Shaohong Wu External Examiner National Research Council Date Approved: April 8, 2004 SIMON FRASER UNIVERSITY PARTIAL COPYRIGHT LICENCE The author, whose copyright is declared on the title page of this work, has granted to Simon Fraser University the right to lend this thesis, project or extended essay to users of the Simon Fraser University Library, and to make partial or single copies only for such users or in response to a request from the library of any other university, or other educational institution, on its own behalf or for one of its users. The author has further granted permission to Simon Fraser University to keep or make a digital copy for use in its circulating collection. The author has further agreed that permission for multiple copying of this work for scholarly purposes may be granted by either the author or the Dean of Graduate Studies. -

Brocade Vyatta Network OS Data Sheet
DATA SHEET Brocade Vyatta Network OS HIGHLIGHTS A Network Operating System for the Way Forward • Offers a proven, modern network The Brocade® Vyatta® Network OS lays the foundation for a flexible, easy- operating system that accelerates the adoption of next-generation to-use, and high-performance network services architecture capable of architectures meeting current and future network demands. The operating system was • Creates an open, programmable built from the ground up to deliver robust network functionality that can environment to enhance be deployed virtually or as an appliance, and in concert with solutions differentiation, service quality, and from a large ecosystem of vendors, to address various Software-Defined competitiveness Networking (SDN) and Network Functions Virtualization (NFV) use cases. • Supports a broad ecosystem for With the Brocade Vyatta Network OS, organizations can bridge the gap optimal customization and service between traditional and new architectures, as well as leverage existing monetization investments and maximize operational efficiencies. Moreover, they can • Simplifies and automates network compose and deploy unique, new services that will drive differentiation functions to improve time to service, increase operational efficiency, and and strengthen competitiveness. reduce costs • Delivers breakthrough performance flexibility, performance, and operational and scale to meet the needs of any A Proven, Modern Operating efficiency, helping organizations create deployment System The Brocade Vyatta Network OS new service offerings and value. Since • Provides flexible deployment options separates the control and data planes in 2012, the benefits of this operating to support a wide variety of use cases software to fit seamlessly within modern system have been proven by the Brocade SDN and NFV environments. -

RFC 8766: Discovery Proxy for Multicast DNS-Based Service
Stream: Internet Engineering Task Force (IETF) RFC: 8766 Category: Standards Track Published: June 2020 ISSN: 2070-1721 Author: S. Cheshire Apple Inc. RFC 8766 Discovery Proxy for Multicast DNS-Based Service Discovery Abstract This document specifies a network proxy that uses Multicast DNS to automatically populate the wide-area unicast Domain Name System namespace with records describing devices and services found on the local link. Status of This Memo This is an Internet Standards Track document. This document is a product of the Internet Engineering Task Force (IETF). It represents the consensus of the IETF community. It has received public review and has been approved for publication by the Internet Engineering Steering Group (IESG). Further information on Internet Standards is available in Section 2 of RFC 7841. Information about the current status of this document, any errata, and how to provide feedback on it may be obtained at https://www.rfc-editor.org/info/rfc8766. Copyright Notice Copyright (c) 2020 IETF Trust and the persons identified as the document authors. All rights reserved. This document is subject to BCP 78 and the IETF Trust's Legal Provisions Relating to IETF Documents (https://trustee.ietf.org/license-info) in effect on the date of publication of this document. Please review these documents carefully, as they describe your rights and restrictions with respect to this document. Code Components extracted from this document must include Simplified BSD License text as described in Section 4.e of the Trust Legal Provisions and are provided without warranty as described in the Simplified BSD License. Cheshire Standards Track Page 1 RFC 8766 Multicast Service Discovery Proxy June 2020 Table of Contents 1. -

Peer-To-Peer Virtualized Services
International Journal on Advances in Internet Technology, vol 4 no 3 & 4, year 2011, http://www.iariajournals.org/internet_technology/ 89 Peer-to-Peer Virtualized Services David Bailey and Kevin Vella University of Malta Msida, Malta Email: [email protected], [email protected] Abstract—This paper describes the design and operation advance a rethink of general purpose operating system of a peer-to-peer framework for providing, locating and architecture. consuming distributed services that are encapsulated within The performance hit commonly associated with virtual- virtual machines. We believe that the decentralized nature of peer-to-peer networks acting in tandem with techniques such ization has been partly addressed on commodity computers as live virtual machine migration and replication facilitate by recent modifications to the x86 architecture [3], with both scalable and on-demand provision of services. Furthermore, AMD and Intel announcing specifications for integrating the use of virtual machines eases the deployment of a wide IOMMUs (Input/Output Memory Management Units) with range of legacy systems that may subsequently be exposed upcoming architectures. While this largely resolves the issue through the framework. To illustrate the feasibility of running distributed services within virtual machines, several computa- of computational slow-down and simplifies hypervisor de- tional benchmarks are executed on a compute cluster running sign, virtualized I/O performance will remain mostly below our framework, and their performance characteristics are par until I/O devices are capable of holding direct and evaluated. While I/O-intensive benchmarks suffer a penalty concurrent conversations with several virtual machines on due to virtualization-related limitations in the prevailing I/O the same host. -

Internet Telephony Digital August Issue 2006
Where Can You Turn for a Total Solution? As a total solutions provider, NEC understands the complexities today’s converged networks can present to your business. With our proven experience, we know what it takes to help you avoid traveling in the wrong direction. NEC delivers the most choices of IP communications platforms to meet the unique needs of your business. Add to that a strong portfolio of applications and services, and before you know it, your business is traveling in the direction of improved customer experience, enhanced employee productivity, increased revenue generation and maximum return on investment. Why go in different directions when you can focus on a Total Solution? Turn to NEC! www.necunified.com/tmc © 2006 NEC Corporation NEC and the NEC logo are registered trademarks of NEC Corporation. By Greg Galitzine Group Publisher and Editor-In-Chief, Rich Tehrani ([email protected]) EDITORIAL Location, Location, Editorial Director, Greg Galitzine ([email protected]) Associate Editor, Erik Linask ([email protected]) Location TMC LABS Executive Technology Editor/CTO/VP, Tom Keating ([email protected]) Let’s take a trip back to the late 1990s, right ART about the time when every thing connected to Senior Art Director, Lisa D. Morris Art Director, Alan Urkawich telecom was seemingly awash in money, and EXECUTIVE OFFICERS there was WAP, and with WAP there was the Nadji Tehrani, Chairman and CEO Rich Tehrani, President early promise of location-based services. Dave Rodriguez, VP of Publications and Conferences Who remembers this WAP enabled application? You’re walking down the street and, as Kevin J. -

The Essential Guide to Telecommunications, Sixth Edition
PRAISE FOR THE ESSENTIAL GUIDE TO TELECOMMUNICATIONS, SIXTH EDITION “Dodd’s The Essential Guide to Telecommunications provides the history and context that make a fundamental underpinning of modern business more accessible to technologists and businesspeople alike. This new edition of her primer is an essential reference in the continuously evolving communica- tions landscape.” —Tom Hopcroft, President and CEO, Mass Technology Leadership Council “Annabel Dodd’s book is a clear guide and big-picture view of technologies and industries. It is an up-to-date guide for anyone who wants to be familiar with important innovations and key technologies. This is truly an industry bible for mobile, Internet, and networking services.” —Hiawatha Bray, Technology Reporter, The Boston Globe “Ms. Dodd’s aptly titled The Essential Guide to Telecommunications has been my bible for all things telecom since my days as an AT&T transmission network engineer nearly twenty years ago. Exhaus- tively and meticulously researched, concisely written for lay folks and techs/engineers alike, this book aids me in my current role as an IT Support Technician II when discussing new technology with our telecommunications department. Thank you to Ms. Dodd for keeping us all current!” —Todd Garbarini, IT Support Technician II Commvault Systems, Inc. “The Essential Guide to Telecommunications is probably one of the most useful and well-written books on our telecom bookshelf. Annabel Z. Dodd does a great job of capturing a snapshot of the current telecom industry. Even those with little or no technical training should be able to understand the text. This is the perfect book for salespeople who want to learn more about the products and services they are selling, or for those who just want to keep up to date on the latest in telecom technology.” —William Van Hefner, President, Vantek Communications, Inc. -

Network Disaggregation at the Edge with the Open SD-Edge Platform
Network Disaggregation at the Edge With the Open SD-Edge Platform November 11, 2020 Sponsored By: Information Classification: General Today’s Speakers Jennifer Clark, Robert Bays Principal Analyst – Assistant VP Heavy Reading ATT - Vyatta Srikanth Krishnamohan Elad Blatt Director of Product Marketing CSO IP Infusion Silicom Information Classification: General ©Page 2020 3 Omdia NFV in a Production Environment: Leading Use Cases Commercial NFV deployment expectation Information Classification: General Enterprises are Shifting to Managed Services Enterprises are shifting from DIY vCPE to managed services, supporting the same VFNs but with improved security, performance, reliability and cost Information Classification: General Edge deployment barriers • Today, operators are faced with three top challenges to deploying edge: – High costs – Unclear business case – Technical issues Information Classification: General Edge Investment: Everything is a Priority Information Classification: General Network Disaggregation at the Edge With the Open SD-Edge Platform Q&A Information Classification: General DANOS Vyatta Edition 2020-11-11.1 © 2020 AT&T Inc. What is DANOS Vyatta Edition? Gen 2 architecture >700 Subscription Multiple CSPs Vyatta sets vRouter Founded released customers Standardize on Vyatta speed record Domain 2.0 partner Acquires Vyatta Initial release Apr 2005 Oct 2007 Sep 2011 Jan 2013 Jun 2014 Dec 2014 July 2017 Nov 2019 First release 1M Downloads Gen 3 architecture Broadcom Tomahawk Gen 4 architecture EA Oct 2005 Jan 2011 Acquires -
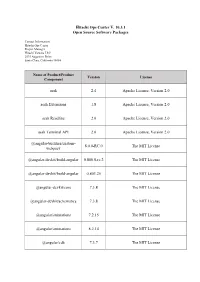
Open Source Software Packages
Hitachi Ops Center V. 10.3.1 Open Source Software Packages Contact Information: Hitachi Ops Center Project Manager Hitachi Vantara LLC 2535 Augustine Drive Santa Clara, California 95054 Name of Product/Product Version License Component aesh 2.4 Apache License, Version 2.0 aesh Extensions 1.8 Apache License, Version 2.0 aesh Readline 2.0 Apache License, Version 2.0 aesh Terminal API 2.0 Apache License, Version 2.0 @angular-builders/custom- 8.0.0-RC.0 The MIT License webpack @angular-devkit/build-angular 0.800.0-rc.2 The MIT License @angular-devkit/build-angular 0.803.25 The MIT License @angular-devkit/core 7.3.8 The MIT License @angular-devkit/schematics 7.3.8 The MIT License @angular/animations 7.2.15 The MIT License @angular/animations 8.2.14 The MIT License @angular/cdk 7.3.7 The MIT License Name of Product/Product Version License Component @angular/cli 8.0.0 The MIT License @angular/cli 8.3.25 The MIT License @angular/common 7.2.15 The MIT License @angular/common 8.2.14 The MIT License @angular/compiler 7.2.15 The MIT License @angular/compiler 8.2.14 The MIT License @angular/compiler-cli 8.2.14 The MIT License @angular/core 7.2.15 The MIT License @angular/forms 7.2.13 The MIT License @angular/forms 7.2.15 The MIT License @angular/forms 8.2.14 The MIT License @angular/forms 8.2.7 The MIT License @angular/language-service 8.2.14 The MIT License @angular/platform-browser 7.2.15 The MIT License @angular/platform-browser 8.2.14 The MIT License Name of Product/Product Version License Component @angular/platform-browser- 7.2.15 The MIT License