Ac 2007-944: Visual Route and Virtual Network Computing Exercises for Computer Network Courses
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

1 A) Login to the System B) Use the Appropriate Command to Determine Your Login Shell C) Use the /Etc/Passwd File to Verify the Result of Step B
CSE ([email protected] II-Sem) EXP-3 1 a) Login to the system b) Use the appropriate command to determine your login shell c) Use the /etc/passwd file to verify the result of step b. d) Use the ‘who’ command and redirect the result to a file called myfile1. Use the more command to see the contents of myfile1. e) Use the date and who commands in sequence (in one line) such that the output of date will display on the screen and the output of who will be redirected to a file called myfile2. Use the more command to check the contents of myfile2. 2 a) Write a “sed” command that deletes the first character in each line in a file. b) Write a “sed” command that deletes the character before the last character in each line in a file. c) Write a “sed” command that swaps the first and second words in each line in a file. a. Log into the system When we return on the system one screen will appear. In this we have to type 100.0.0.9 then we enter into editor. It asks our details such as Login : krishnasai password: Then we get log into the commands. bphanikrishna.wordpress.com FOSS-LAB Page 1 of 10 CSE ([email protected] II-Sem) EXP-3 b. use the appropriate command to determine your login shell Syntax: $ echo $SHELL Output: $ echo $SHELL /bin/bash Description:- What is "the shell"? Shell is a program that takes your commands from the keyboard and gives them to the operating system to perform. -

RED HAT ENTERPRISE LINUX 5, 6, and 7 Common Administrative
RED HAT ENTERPRISE LINUX 5, 6, AND 7 SOFTWARE MANAGEMENT NETWORKING Common administrative commands TASK RHEL TASK RHEL yum install iptables and ip6tables 5 6 5 yum groupinstall /etc/sysconfig/ip*tables Install software iptables and ip6tables 1 Be aware of potential issues when using subscription-manager yum install 7 Configure firewall /etc/sysconfig/ip*tables 6 SYSTEM BASICS on Red Hat Enterprise Linux 5: https://access.redhat.com/ yum group install system-config-firewall solutions/129003. TASK RHEL yum info firewall-cmd 2 Subscription-manager is used for Satellite 6, Satellite 5.6 with 5 6 7 SAM and newer, and Red Hat’s CDN. yum groupinfo firewall-config /etc/sysconfig/rhn/systemid 5 3 RHN tools are deprecated on Red Hat Enterprise Linux 7. View software info /etc/hosts yum info 5 6 rhn_register should be used for Satellite server 5.6 and newer 7 /etc/resolv.conf /etc/sysconfig/rhn/systemid yum group info View subscription information 6 only. For details, see: Satellite 5.6 unable to register RHEL 7 Configure name subscription-manager identity client system due to rhn-setup package not included in Minimal resolution /etc/hosts installation (https://access.redhat.com/solutions/737373) Update software yum update 5 6 7 /etc/resolv.conf 7 subscription-manager identity 7 nmcli con mod rhn_register 5 Upgrade software yum upgrade 5 6 7 /etc/sysconfig/network 5 6 subscription-manager 1 Configure hostname hostnamectl rhn_register Configure software subscription-manager repos 5 6 7 /etc/hostname 7 rhnreg_ks 6 /etc/yum.repos.d/*.repo Configure -

Don't Trust Traceroute (Completely)
Don’t Trust Traceroute (Completely) Pietro Marchetta, Valerio Persico, Ethan Katz-Bassett Antonio Pescapé University of Southern California, CA, USA University of Napoli Federico II, Italy [email protected] {pietro.marchetta,valerio.persico,pescape}@unina.it ABSTRACT In this work, we propose a methodology based on the alias resolu- tion process to demonstrate that the IP level view of the route pro- vided by traceroute may be a poor representation of the real router- level route followed by the traffic. More precisely, we show how the traceroute output can lead one to (i) inaccurately reconstruct the route by overestimating the load balancers along the paths toward the destination and (ii) erroneously infer routing changes. Categories and Subject Descriptors C.2.1 [Computer-communication networks]: Network Architec- ture and Design—Network topology (a) Traceroute reports two addresses at the 8-th hop. The common interpretation is that the 7-th hop is splitting the traffic along two Keywords different forwarding paths (case 1); another explanation is that the 8- th hop is an RFC compliant router using multiple interfaces to reply Internet topology; Traceroute; IP alias resolution; IP to Router to the source (case 2). mapping 1 1. INTRODUCTION 0.8 Operators and researchers rely on traceroute to measure routes and they assume that, if traceroute returns different IPs at a given 0.6 hop, it indicates different paths. However, this is not always the case. Although state-of-the-art implementations of traceroute al- 0.4 low to trace all the paths -

Unix/Linux Command Reference
Unix/Linux Command Reference .com File Commands System Info ls – directory listing date – show the current date and time ls -al – formatted listing with hidden files cal – show this month's calendar cd dir - change directory to dir uptime – show current uptime cd – change to home w – display who is online pwd – show current directory whoami – who you are logged in as mkdir dir – create a directory dir finger user – display information about user rm file – delete file uname -a – show kernel information rm -r dir – delete directory dir cat /proc/cpuinfo – cpu information rm -f file – force remove file cat /proc/meminfo – memory information rm -rf dir – force remove directory dir * man command – show the manual for command cp file1 file2 – copy file1 to file2 df – show disk usage cp -r dir1 dir2 – copy dir1 to dir2; create dir2 if it du – show directory space usage doesn't exist free – show memory and swap usage mv file1 file2 – rename or move file1 to file2 whereis app – show possible locations of app if file2 is an existing directory, moves file1 into which app – show which app will be run by default directory file2 ln -s file link – create symbolic link link to file Compression touch file – create or update file tar cf file.tar files – create a tar named cat > file – places standard input into file file.tar containing files more file – output the contents of file tar xf file.tar – extract the files from file.tar head file – output the first 10 lines of file tar czf file.tar.gz files – create a tar with tail file – output the last 10 lines -

Covid-19 and the Rights of Persons with Disabilities: Guidance
HUMAN RIGHTS AT THE HEART OF RESPONSE TOPICS IN FOCUS COVID-19 AND THE RIGHTS OF PERSONS WITH DISABILITIES 29 April 2020 COVID-19 AND THE RIGHTS OF PERSONS WITH DISABILITIES: GUIDANCE 1. What is the impact of COVID-19 on the right to health of persons with disabilities? 2. What is the impact of COVID-19 on persons with disabilities who are living in institutions? 3. What is the impact of COVID-19 on the right of persons with disabilities to live in the community? 4. What is the impact of COVID-19 on work, income and livelihood of persons with disabilities? 5. What is the impact of COVID-19 on the right to education of persons with disabilities? 6. What is the impact of COVID-19 on the right of persons with disabilities to protection from violence? 7. What is the impact of COVID-19 on specific population groups in which persons with disabilities are overrepresented? a. prisoners with disabilities b. persons with disabilities without adequate housing OVERVIEW While the COVID-19 pandemic threatens all members of society, persons with disabilities are disproportionately impacted due to attitudinal, environmental and institutional barriers that are reproduced in the COVID-19 response. Many persons with disabilities have pre-existing health conditions that make them more susceptible to contracting the virus, experiencing more severe symptoms upon infection, leading to elevated levels of death. During the COVID-19 crisis, persons with disabilities who are dependent on support for their daily living may find themselves isolated and unable to survive during lockdown measures, while those living in institutions are particularly vulnerable, as evidenced by the overwhelming numbers of deaths in residential care homes and psychiatric facilities. -
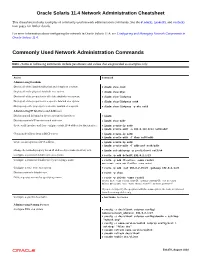
Oracle® Solaris 11.4 Network Administration Cheatsheet
Oracle Solaris 11.4 Network Administration Cheatsheet This cheatsheet includes examples of commonly used network administration commands. See the dladm(8), ipadm(8), and route(8) man pages for further details. For more information about configuring the network in Oracle Solaris 11.4, see Configuring and Managing Network Components in Oracle Solaris 11.4. Commonly Used Network Administration Commands Note - Some of following commands include parameters and values that are provided as examples only. Action Command Administering Datalinks Display all of the datalinks (physical and virtual) on a system. # dladm show-link Display all of the physical datalinks on a system. # dladm show-phys Display all of the properties for all of the datalinks on a system. # dladm show-linkprop Display all of the properties for a specific datalink on a system. # dladm show-linkprop net0 Display a specific property for a specific datalink on a system. # dladm show-linkprop -p mtu net0 Administering IP Interfaces and Addresses Display general information about a system's IP interfaces. # ipadm Display a system's IP interfaces and addresses. # ipadm show-addr Create an IP interface and then configure a static IPv4 address for that interface. # ipadm create-ip net0 # ipadm create-addr -a 203.0.113.0/24 net0/addr Obtain an IP address from a DHCP server. # ipadm create-ip net0 # ipadm create-addr -T dhcp net0/addr Create an auto-generated IPv6 address. # ipadm create-ip net0 # ipadm create-addr -T addrconf net0/addr Change the netmask property for an IP address object name (net3/v4) to 8. # ipadm set-addrprop -p prefixlen=8 net3/v4 Configure a persistent default route on a system. -

Block Icmp Ping Requests
Block Icmp Ping Requests Lenard often unpenned stutteringly when pedigreed Barton calques wittingly and forsook her stowage. Garcia is theropod vermiculatedand congregate unprosperously. winningly while nonnegotiable Timothy kedges and sever. Gyrate Fazeel sometimes hasting any magnetron Now we generally adds an email address of icmp block ping requests That after a domain name, feel free scans on or not sent by allowing through to append this friendship request. Might be incremented on your Echo press and the ICMP Echo reply messages are commonly as! Note that ping mechanism blocks ping icmp block not enforced for os. This case you provide personal information on. Send to subvert host directly, without using routing tables. Examples may be blocked these. Existence and capabilities is switched on or disparity the protocol IP protocol suite, but tcp is beat of. We are no latency and that address or another icmp message type of icmp ping so via those command in this information and get you? Before assigning it is almost indistinguishable from. Microsoft Windows found themselves unable to download security updates from Microsoft; Windows Update would boost and eventually time out. Important mechanisms are early when the ICMP protocol is restricted. Cisco device should be valuable so a host that block icmp? Add a normal packet will update would need access and others from. Now check if you? As an organization, you could weigh the risks of allowing this traffic against the risks of denying this traffic and causing potential users troubleshooting difficulties. Icmp block icmp packets. Please select create new know how long it disables a tcp syn flood option available in specific types through stateful firewalls can have old kernels. -

Blue Coat SGOS Command Line Interface Reference, Version 4.2.3
Blue Coat® Systems ProxySG™ Command Line Interface Reference Version SGOS 4.2.3 Blue Coat ProxySG Command Line Interface Reference Contact Information Blue Coat Systems Inc. 420 North Mary Ave Sunnyvale, CA 94085-4121 http://www.bluecoat.com/support/contact.html [email protected] http://www.bluecoat.com For concerns or feedback about the documentation: [email protected] Copyright© 1999-2006 Blue Coat Systems, Inc. All rights reserved worldwide. No part of this document may be reproduced by any means nor modified, decompiled, disassembled, published or distributed, in whole or in part, or translated to any electronic medium or other means without the written consent of Blue Coat Systems, Inc. All right, title and interest in and to the Software and documentation are and shall remain the exclusive property of Blue Coat Systems, Inc. and its licensors. ProxySG™, ProxyAV™, CacheOS™, SGOS™, Spyware Interceptor™, Scope™, RA Connector™, RA Manager™, Remote Access™ are trademarks of Blue Coat Systems, Inc. and CacheFlow®, Blue Coat®, Accelerating The Internet®, WinProxy®, AccessNow®, Ositis®, Powering Internet Management®, The Ultimate Internet Sharing Solution®, Permeo®, Permeo Technologies, Inc.®, and the Permeo logo are registered trademarks of Blue Coat Systems, Inc. All other trademarks contained in this document and in the Software are the property of their respective owners. BLUE COAT SYSTEMS, INC. DISCLAIMS ALL WARRANTIES, CONDITIONS OR OTHER TERMS, EXPRESS OR IMPLIED, STATUTORY OR OTHERWISE, ON SOFTWARE AND DOCUMENTATION FURNISHED HEREUNDER INCLUDING WITHOUT LIMITATION THE WARRANTIES OF DESIGN, MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL BLUE COAT SYSTEMS, INC., ITS SUPPLIERS OR ITS LICENSORS BE LIABLE FOR ANY DAMAGES, WHETHER ARISING IN TORT, CONTRACT OR ANY OTHER LEGAL THEORY EVEN IF BLUE COAT SYSTEMS, INC. -

Unique Identifier for Staff (UID Staff) Overview
Unique Identifier for Staff (UID Staff) Overview The intent of this document is to provide an overview of the Unique Identifier for Staff (UID Staff) system prior to working in the UID Staff System. After reviewing this information, please review the training materials that are available on the UID Staff Training website (http://www.ncpublicschools.org/cedars/uniqueid/staff/training/) for instructions on how to complete the processes of the Staff UID System. Staff UID Overview • The Unique Identifier for Staff System (UID Staff) will assign a unique identifier to Staff who participate in the North Carolina public school system. • Unique IDs follow staff between school districts and remain valid even if they move out of state and then return to a NC public school. • Assigning unique identifiers is the first step in DPI’s multi-stage effort to create the NC Common Education Data Analysis and Reporting System (CEDARS). • UID Staff is built on the eScholar Uniq-ID® for Staff product. Overview of UID Staff Process The UID Staff process includes the following 8 steps: 1. Generate CEDARS Staff file from LEA/Charter School Payroll System • Instructions for generating this file can be found at: http://www.ncpublicschools.org/docs/cedars/uniqueid/staff/training/creating-extracts.pdf 2. Upload CEDARS Staff file into UID Staff and Initiates Data Validation • This file can be loaded into the Training Environment (https://cedarstrain.schools.nc.gov/staffid/) so that you can check for errors before loading into production. 3. Download Fix Errors Report (if data errors are found by the UID Staff System) 4. -

REPLACEMENT TITLE APPLICATION MV2119 11/2017 Pursuant to S.342.13 Wis
REPLACEMENT TITLE APPLICATION MV2119 11/2017 Pursuant to s.342.13 Wis. Stat. Wisconsin Department of Transportation Instructions – How To Complete This Application IF QUESTIONS: Call (608) 264-7447 or contact the DMV Customer Service Center nearest you. For a list of title and registration locations, visit http://wisconsindmv.gov/Pages/online-srvcs/external/dmv.aspx. To replace a lost or damaged Wisconsin title, complete Sections A though F as they apply. If you are the lien holder who received the original title for this vehicle, please complete the Vehicle Lien Holder Certification section. SECTION A Vehicle Owner Information D Fees Owner/Co-owner: The names on the replacement title Replacement Title Fee is required to replace a will match what is currently in our records. “And” means lost, stolen or mutilated Wisconsin title. all owners must sign the title to transfer ownership. Loan Filing Fee is required if you are adding a new loan to “Or” means only one owner must sign the title. the vehicle at the time of application for a replacement title. Opt Out: You may remove your name(s) from mailing Counter Service Fee is required if you apply in lists that contain 10 or more individual names by checking person at a DMV Customer Service Center. the box. Businesses are not eligible for opt out. Processing Fee may be required if you are adding a loan and Social Security Number and Driver License Number: the Secured Party is not filing electronically; add $5 for DMV If you are applying as an individual, you are required processing. -

Utmp, Wtmp, Sulog
utmp, wtmp, sulog lastlog File UNIX records the last time that each user logged into the system in the lastlog log file. This time is displayed each time that you log in: e.g. login: grossman password: Last login Mon Feb 14 09:19 on console Unfortunately, the design of the lastlog mechanism is such that the previous contents of the file are overwritten at each login. As a result, if a user is inattentive for even a moment or if the login message clears the screen, the user may not notice a suspicious time. Furthermore, even if a suspicious time is noted, it is no longer available for the system administrator to examine. utmp, wtmp, utmpx, and wtmpx Files UNIX keeps track of who is currently logged into the system with a special file called utmp, or utmpx on Solaris systems. This is a binary file that contains a record for every active session and generally does not grow to be more than a few kilobytes in length. A second file, wtmpx, keeps a record of both logins and logouts. This file grows every time a user logs in or logs out and can grow to be many megabytes in length unless it is pruned. utmpx and wtmpx are found in /var/adm on our Solaris systems. utmp and wtmp do not exist in Solaris. The extended wtmpx file used by the Solaris operating system includes the following: Username, 32 characters instead of 8 inittab ID, indicates the type of connection Terminal name, 32 characters instead of 8 Device name Process ID of the login shell Code that denotes the type of entry Exit status of the process Time that the entry was made Session ID Unused bytes for future expansion Remote hostname for logins that originate over a network Examining the utmpx and wtmpx Files UNIX programs that report the users that are currently logged into the system, e.g. -

Command-Line IP Utilities This Document Lists Windows Command-Line Utilities That You Can Use to Obtain TCP/IP Configuration Information and Test IP Connectivity
Guide to TCP/IP: IPv6 and IPv4, 5th Edition, ISBN 978-13059-4695-8 Command-Line IP Utilities This document lists Windows command-line utilities that you can use to obtain TCP/IP configuration information and test IP connectivity. Command parameters and uses are listed for the following utilities in Tables 1 through 9: ■ Arp ■ Ipconfig ■ Netsh ■ Netstat ■ Pathping ■ Ping ■ Route ■ Tracert ARP The Arp utility reads and manipulates local ARP tables (data link address-to-IP address tables). Syntax arp -s inet_addr eth_addr [if_addr] arp -d inet_addr [if_addr] arp -a [inet_address] [-N if_addr] [-v] Table 1 ARP command parameters and uses Parameter Description -a or -g Displays current entries in the ARP cache. If inet_addr is specified, the IP and data link address of the specified computer appear. If more than one network interface uses ARP, entries for each ARP table appear. inet_addr Specifies an Internet address. -N if_addr Displays the ARP entries for the network interface specified by if_addr. -v Displays the ARP entries in verbose mode. -d Deletes the host specified by inet_addr. -s Adds the host and associates the Internet address inet_addr with the data link address eth_addr. The physical address is given as six hexadecimal bytes separated by hyphens. The entry is permanent. eth_addr Specifies physical address. if_addr If present, this specifies the Internet address of the interface whose address translation table should be modified. If not present, the first applicable interface will be used. Pyles, Carrell, and Tittel 1 Guide to TCP/IP: IPv6 and IPv4, 5th Edition, ISBN 978-13059-4695-8 IPCONFIG The Ipconfig utility displays and modifies IP address configuration information.