ANKER Wireless Chargers Instructions
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Nokia Lumia 928: Safety
Nokia Lumia 928: Safety Safety Read these simple guidelines. Not following them may be dangerous or illegal. For further information, read the complete user guide. Switch off in Restricted Areas Batteries, Chargers, and other Switch the device off when mobile phone use is Accessories not allowed or when it may cause interference or Use only batteries, chargers, and other accessories danger, for example, in aircraft, in hospitals or near approved for use with this device. Do not connect medical equipment, fuel, chemicals, or blasting incompatible products. areas. Obey all instructions in restricted areas. Road Safety Comes First Keep your Device dry Obey all local laws. Always keep your hands free to Your device is not water-resistant. Keep it dry. operate the vehicle while driving. Your first consid- eration while driving should be road safety. Interference Glass Parts All wireless devices may be susceptible to interfer- The device screen is made of glass. This glass can ence, which could affect performance. break if the device is dropped on a hard surface or receives a substantial impact. If the glass breaks, do not touch the glass parts of the device or attempt to remove the broken glass from the device. Stop using the device until the glass is replaced by quali- fied service personnel. Qualified Service Protect your Hearing Only qualified personnel may install or repair this To prevent possible hearing damage, do not listen product. at high volume levels for long periods. Exercise cau- tion when holding your device near your ear while the speakerphone is in use. Chapter 2 1 Contents Safety ........................................................1 Use the touch screen ....................................................... -

7.5W Fast-Charging Mode and 5W Standard Mode
Before you start: For Anker 7.5W Wireless Chargers This document will help you identify problems and get the most out of your experience with our wireless chargers. It is important to note that although wireless chargers are a transformatively convenient way to charge, they are not yet capable of the charging speeds provided by traditional wired chargers. Attachments (Must-Read!) If you're experiencing interrupted or slow charging, check the following: The back of your phone should not have any metal, pop sockets, or credit cards. Put the phone in the center of the charging surface (this lets the charging coil in your phone line up with the one inside the wireless charger). The wireless charging coil on Sony phones is located slightly below center. Phone cases should be no thicker than 5 mm for effective charging. Choose the correct adapter for your wireless charger: Quick Charge or Power Delivery adapter for Fast Charge Modes. 5V/2A adapter for Standard Charge Mode. Not compatible with 5V/1A adapters. Phone Brands & Power Input For Anker 7.5W Wireless Chargers Apple iPhone X iPhone XS iPhone XS Max iPhone 8 / 8 Plus iPhone XR Two charging modes: 7.5W fast-charging mode and 5W standard mode. For the best results, use a Quick Charge wall charger, desktop charger, car charger, power strip (output power of 9V/2A or 12V/1.5A). For standard 5W charging mode, use with wall chargers, desktop chargers, car chargers, and power strips with an output of 5V/2A or above.Not compatible with the iPhone stock charger (5V/1A). -

The Technology That Brings Together All Things Mobile
NFC – The Technology That Brings Together All Things Mobile Philippe Benitez Wednesday, June 4th, 2014 NFC enables fast, secure, mobile contactless services… Card Emulation Mode Reader Mode P2P Mode … for both payment and non-payment services Hospitality – Hotel room keys Mass Transit – passes and limited use tickets Education – Student badge Airlines – Frequent flyer card and boarding passes Enterprise & Government– Employee badge Automotive – car sharing / car rental / fleet management Residential - Access Payment – secure mobile payments Events – Access to stadiums and large venues Loyalty and rewards – enhanced consumer experience 3 h h 1996 2001 2003 2005 2007 2014 2014 2007 2005 2003 2001 1996 previous experiences experiences previous We are benefiting from from benefiting are We Barriers to adoption are disappearing ! NFC Handsets have become mainstream ! Terminalization is being driven by ecosystem upgrades ! TSM Provisioning infrastructure has been deployed Barriers to adoption are disappearing ! NFC Handsets have become mainstream ! Terminalization is being driven by ecosystem upgrades ! TSM Provisioning infrastructure has been deployed 256 handset models now in market worldwide Gionee Elife E7 LG G Pro 2 Nokia Lumia 1020 Samsung Galaxy Note Sony Xperia P Acer E320 Liquid Express Google Nexus 10 LG G2 Nokia Lumia 1520 Samsung Galaxy Note 3 Sony Xperia S Acer Liquid Glow Google Nexus 5 LG Mach Nokia Lumia 2520 Samsung Galaxy Note II Sony Xperia Sola Adlink IMX-2000 Google Nexus 7 (2013) LG Optimus 3D Max Nokia Lumia 610 NFC Samsung -

2014 BT Compatibility List 20141030
Item Brand Name Model 1 Acer Acer beTouch E210 2 Acer acer E400 3 Acer acer P400 4 Acer DX650 5 Acer E200 6 Acer Liquid E 7 Acer Liquid Mini (E310) 8 Acer M900 9 Acer S110 10 Acer Smart handheld 11 Acer Smart handheld 12 Acer Smart handheld E100 13 Acer Smart handheld E101 14 Adec & Partner AG AG vegas 15 Alcatel Alcatel OneTouch Fierce 2 16 Alcatel MISS SIXTY MSX10 17 Alcatel OT-800/ OT-800A 18 Alcatel OT-802/ OT-802A 19 Alcatel OT-806/ OT-806A/ OT-806D/ OT-807/ OT-807A/ OT-807D 20 Alcatel OT-808/ OT-808A 21 Alcatel OT-880/ OT-880A 22 Alcatel OT-980/ OT-980A 23 Altek Altek A14 24 Amazon Amazon Fire Phone 25 Amgoo Telecom Co LTD AM83 26 Apple Apple iPhone 4S 27 Apple Apple iPhone 5 28 Apple Apple iPhone 6 29 Apple Apple iPhone 6 Plus 30 Apple iPhone 2G 31 Apple iPhone 3G 32 Apple iPhone 3Gs 33 Apple iPhone 4 34 Apple iPhone 5C 35 Apple iPHone 5S 36 Aramasmobile.com ZX021 37 Ascom Sweden AB 3749 38 Asustek 1000846 39 Asustek A10 40 Asustek G60 41 Asustek Galaxy3_L and Galaxy3_S 42 Asustek Garmin-ASUS M10E 43 Asustek P320 44 Asustek P565c 45 BlackBerry BlackBerry Passport 46 BlackBerry BlackBerry Q10 47 Broadcom Corporation BTL-A 48 Casio Hitachi C721 49 Cellnet 7 Inc. DG-805 Cellon Communications 50 C2052, Technology(Shenzhen) Co., Ltd. Cellon Communications 51 C2053, Technology(Shenzhen) Co., Ltd. Cellon Communications 52 C3031 Technology(Shenzhen) Co., Ltd. Cellon Communications 53 C5030, Technology(Shenzhen) Co., Ltd. -

Detective 11.0 October 2018
OXYGEN FORENSIC® DETECTIVE 11.0 OCTOBER 2018 USE NEW WHATSAPP EXTRACTION METHOD AQCUIRE IOT DEVICES WhatsApp is without doubt the most popular messenger Digital assistants are already a part of everyday life and in the world with over 1.5 billion users globally. Thus, have been successfully used to solve several crimes. extracting complete WhatsApp content from all possible Oxygen Forensic® Detective v.11 brings support for the sources is essential for any investigation. two most popular digital assistants – Amazon Alexa and Google Home. Commonly used methods of WhatsApp data acquisition involve extracting data from mobile devices and their You can access Amazon Alexa cloud using a username cloud backups. Oxygen Forensic® Detective v.11 and password or token. A token can be found on the introduces an industry-first alternative method of device’s associated computer with Oxygen Forensic® WhatsApp data extraction. KeyScout and used in Cloud Extractor. The software acquires a complete evidence set from Amazon Alexa, In the new software version, you can access complete including account and device details, contacts, messages, WhatsApp data by scanning a QR code from a mobile calendars, notifications, lists, activities, skills, etc. app or using the WhatsApp token from a PC. This token can be extracted by our KeyScout utility from the Google Home data can be extracted via Google WhatsApp desktop app or from desktop Web browsers. username/password or a master token found in mobile devices. Extracted Google Home data includes account Once data is extracted, you will be able to download and device details, voice commands, and information WhatsApp communications from the subject’s account about users.Google Home data can also be acquired from any time later when an investigation requires by using a the Google Home mobile app on Apple iOS and Android specially generated WhatsApp QR token available in the devices. -

QI Wireless Compatible Device List Apple Asus Blackberry CASIO
QI Wireless Compatible Device List Apple • iPhone 8 • iPhone 8 Plus • iPhone X • iPhone Xs • iPhone Xs Max • iPhone Xr Asus • Asus PadFone S BlackBerry • BlackBerry Passport • BlackBerry PRIV • BlackBerry Z30 CASIO • CASIO G'z One Commando Caterpillar • Cat S50 • Cat S50C DeWalt • Dewalt MD501 • Dewalt MIL810G Energy Sistem • Energy Phone Pro Qi Fujitsu • Fujitsu Arrows F-09D • Fujitsu Arrows Kiss F-03D • Fujitsu Arrows Kiss F-03E • Fujitsu Arrows X F-10D Google • Google Nexus 4 • Google Nexus 5 • Google Nexus 6 • Google Pixel 3 • Google Pixel 3 XL HP • HP Elite X3 HTC • HTC Droid DNA • HTC Windows Phone 8X Huawei • Huawei Mate20 Pro • Huawei Mate RS Porsche Design • Huawei P30 Pro Kyocera • Kyocera Brigadier • Kyocera DuraForce • Kyocera Hydro Elite • Kyocera Torque G02 • Kyocera Torque KC-S701 • Kyocera Urbano L01 • Kyocera Urbano L03 LG • LG G2 • LG G3 • LG G6 ¹ • LG G6 Plus ¹ • LG G7 • LG G7 ThinQ • LG Lucid 2 • LG Lucid 3 • LG Optimus F5 • LG Optimus G Pro • LG Optimus It L-05E • LG Spectrum 2 • LG Vu 2 • LG Vu 3 • LG V30 • LG V30 Plus • LG V40 ThinQ M.T.T. • M.T.T. Master 4G Meizu • Meizu Zero Microsoft • Microsoft Lumia 950 • Microsoft Lumia 950 Dual Sim • Microsoft Lumia 950 XL • Microsoft Lumia 950 XL Dual Sim Mlais • Mlais MX69W Motorola • Motorola Droid Maxx • Motorola Droid Mini • Motorola Droid Turbo • Motorola Droid Turbo 2 • Motorola Moto Maxx • Motorola Moto X Force mPhone • mPhone 8 NEC • NEC Medias PP N-01D • NEC Medias X N-04E Noa • Noa F10 Pro Nokia • Nokia Lumia 1520 • Nokia Lumia 735 • Nokia Lumia 830 • Nokia Lumia -

HR Kompatibilitätsübersicht
HR-imotion Kompatibilität/Compatibility 2018 / 11 Gerätetyp Telefon 22410001 23010201 22110001 23010001 23010101 22010401 22010501 22010301 22010201 22110101 22010701 22011101 22010101 22210101 22210001 23510101 23010501 23010601 23010701 23510320 22610001 23510420 Smartphone Acer Liquid Zest Plus Smartphone AEG Voxtel M250 Smartphone Alcatel 1X Smartphone Alcatel 3 Smartphone Alcatel 3C Smartphone Alcatel 3V Smartphone Alcatel 3X Smartphone Alcatel 5 Smartphone Alcatel 5v Smartphone Alcatel 7 Smartphone Alcatel A3 Smartphone Alcatel A3 XL Smartphone Alcatel A5 LED Smartphone Alcatel Idol 4S Smartphone Alcatel U5 Smartphone Allview P8 Pro Smartphone Allview Soul X5 Pro Smartphone Allview V3 Viper Smartphone Allview X3 Soul Smartphone Allview X5 Soul Smartphone Apple iPhone Smartphone Apple iPhone 3G / 3GS Smartphone Apple iPhone 4 / 4S Smartphone Apple iPhone 5 / 5S Smartphone Apple iPhone 5C Smartphone Apple iPhone 6 / 6S Smartphone Apple iPhone 6 Plus / 6S Plus Smartphone Apple iPhone 7 Smartphone Apple iPhone 7 Plus Smartphone Apple iPhone 8 Smartphone Apple iPhone 8 Plus Smartphone Apple iPhone SE Smartphone Apple iPhone X Smartphone Apple iPhone XR Smartphone Apple iPhone Xs Smartphone Apple iPhone Xs Max Smartphone Archos 50 Saphir Smartphone Archos Diamond 2 Plus Smartphone Archos Saphir 50x Smartphone Asus ROG Phone Smartphone Asus ZenFone 3 Smartphone Asus ZenFone 3 Deluxe Smartphone Asus ZenFone 3 Zoom Smartphone Asus Zenfone 5 Lite ZC600KL Smartphone Asus Zenfone 5 ZE620KL Smartphone Asus Zenfone 5z ZS620KL Smartphone Asus -

BPOD-H6423-Nokia Lumia 928-V7.Indd
Software Update for your NOKIA LUMIA 928. Software Version 3051.50009.1446.0093 Verizon Wireless is pleased to announce the Windows Phone 8.1 Updated 1 for your Nokia Lumia 928. Windows Phone 8.1 Update 1 brings a host of new features and capabilities to your Lumia 928, all designed to make your phone even more useful and personalized than ever before. CORTANA PERSONAL ASSISTANT • Set reminders, add appointments or reminders to your calendar • Search device and the web for content • Starts app makes calls or texts • Intuitive UI learns you and provides personal updates -When to leave work, flight delays or location-based reminders NOKIA LUMIA 928 | For step-by-step instructions on how to perform the download, please visit www.vzw.com/lumia928support | Data Usage Applies. LTE is a trademark of ETSI. © 2014 Verizon Wireless. 1214-H6423 1 2 3 4 NOKIA LUMIA 928 START SCREEN ENHANCEMENTS WORD FLOW KEYBOARD • Add a background image with translucent tiles • Features shape-writing—just glide your finger • Change the tile layout from two to three column layout across the keyboard • Lock screen orientation in settings (screen won’t rotate) • Respond more quickly to text messages • Continues to learn your writing style -Auto completes words while you’re typing ACTION CENTER CUSTOM VOLUME LEVELS • Customizable from the Notifications setting screen • Select volumes for different activities • Quickly access Wi-Fi, email, Flight Mode and Notifications (e.g.: ringer, media playback) • Switch to silent or vibrate mode | For step-by-step instructions on how to perform the download, please visit www.vzw.com/lumia928support | Data Usage Applies. -

Magneticspy: Exploiting Magnetometer in Mobile Devices for Website and Application Fingerprinting
MagneticSpy: Exploiting Magnetometer in Mobile Devices for Website and Application Fingerprinting NIKOLAY MATYUNIN∗, TU Darmstadt, CYSEC, Germany YUJUE WANG†, TU Darmstadt, Germany TOLGA ARUL∗, TU Darmstadt, CYSEC, Germany KRISTIAN KULLMANN†, TU Darmstadt, Germany JAKUB SZEFER‡, Yale University, USA STEFAN KATZENBEISSER‡, Chair of Computer Engineering, University of Passau, Germany Recent studies have shown that aggregate CPU usage and power consumption traces on smartphones can leak information about applications running on the system or websites visited. In response, access to such data has been blocked for mobile applications starting from Android 8. In this work, we explore a new source of side-channel leakage for this class of attacks. Our method is based on the fact that electromagnetic activity caused by mobile processors leads to noticeable disturbances in magnetic sensor measurements on mobile devices, with the amplitude being proportional to the CPU workload. Therefore, recorded sensor data can be analyzed to reveal information about ongoing activities. The attack works on a number of devices: we evaluated 80 models of modern smartphones and tablets and observed the reaction of the magnetometer to the CPU activity on 56 of them. On selected devices we were able to successfully identify which application has been opened (with up to 90% accuracy) or which web page has been loaded (up to 91% accuracy). The presented side channel poses a significant risk to end users’ privacy, as the sensor data can be recorded from native apps or even from web pages without user permissions. Finally, we discuss possible countermeasures to prevent the presented information leakage. ACM Reference Format: Nikolay Matyunin, Yujue Wang, Tolga Arul, Kristian Kullmann, Jakub Szefer, and Stefan Katzenbeisser. -

Device VOLTE SUNRISE VOWIFI SUNRISE Apple Iphone 11
Device VOLTE_SUNRISE VOWIFI_SUNRISE Apple iPhone 11 (A2221) Supported Supported Apple iPhone 11 Pro (A2215) Supported Supported Apple iPhone 11 Pro Max (A2218) Supported Supported Apple iPhone 5c (A1532) NotSupported Supported Apple iPhone 5S (A1457) NotSupported Supported Apple iPhone 6 (A1586) Supported Supported Apple iPhone 6 Plus (A1524) Supported Supported Apple iPhone 6S (A1688) Supported Supported Apple iPhone 6S Plus (A1687) Supported Supported Apple iPhone 7 (A1778) Supported Supported Apple iPhone 7 Plus (A1784) Supported Supported Apple iPhone 8 (A1905) Supported Supported Apple iPhone 8 Plus (A1897) Supported Supported Apple iPhone SE (A1723) Supported Supported Apple iPhone SE 2020 (A2296) Supported Supported Apple iPhone X (A1901) Supported Supported Apple iPhone XR (A2105) Supported Supported Apple iPhone XS (A2097) Supported Supported Apple iPhone XS Max (A2101) Supported Supported Apple Watch S3 (38mm) (A1889) Supported Supported Apple Watch S3 (42mm) (A1891) Supported Supported Apple Watch S4 (40mm) (A2007) Supported Supported Apple Watch S4 (44mm) (A2008) Supported Supported Apple Watch S5 (40mm) (A2156) Supported Supported Apple Watch S5 (44mm) (A2157) Supported Supported Caterpillar CAT B35 Supported Supported Huawei Honor 10 Supported Supported Huawei Honor 20 (YAL-L21) Supported Supported Huawei Honor 7x (BND-L21) Supported Supported Huawei Honor V10 Supported Supported Huawei Mate 10 Lite (RNE-L21) Supported Supported Huawei Mate 10 pro (BLA-L29) Supported Supported Huawei Mate 20 lite (SNE-LX1) Supported Supported -

In the United States District Court for the Northern District of Texas Dallas Division
IN THE UNITED STATES DISTRICT COURT FOR THE NORTHERN DISTRICT OF TEXAS DALLAS DIVISION MOBILE ENHANCEMENT SOLUTIONS LLC, Civil Action No. 3:13-cv-3977 Plaintiff, v. JURY TRIAL DEMANDED NOKIA CORPORATION AND NOKIA INC., Defendants. ORIGINAL COMPLAINT FOR PATENT INFRINGEMENT Plaintiff Mobile Enhancement Solutions LLC (“MES” or “Plaintiff”) files this Complaint against Nokia Corporation and Nokia Inc. (together, “Nokia” or “Defendants”) for infringement of U.S. Patent No. 6,415,325 (“the ’325 patent”) and U.S. Patent No. 6,148,080 (“the ’080 patent”). THE PARTIES 1. Mobile Enhancement Solutions LLC (“MES”) is a limited liability company organized and existing under the laws of the State of Texas, having a principal place of business in Plano, Texas. 2. Nokia Corporation is a corporation organized and existing under the laws of Finland, having a principal place of business in Espoo, Finland. 3. Defendant Nokia, Inc. is a corporation organized and existing under the laws of Delaware, having a principal place of business in Irving, Texas. 1 JURISDICTION AND VENUE 4. MES brings this action for patent infringement under the patent laws of the United States, namely 35 U.S.C. §§ 271, 281, and 284-285, among others. 5. This Court has subject matter jurisdiction over the claims in this action pursuant to 28 U.S.C. §§ 1331, 1338(a), and 1367. 6. Venue is proper in this judicial district pursuant to 28 U.S.C. §§ 1391(c) and 1400(b). On information and belief, each Defendant is deemed to reside in this judicial district, has committed acts of infringement in this judicial district, has purposely transacted business in this judicial district, and/or has regular and established places of business in this judicial district. -
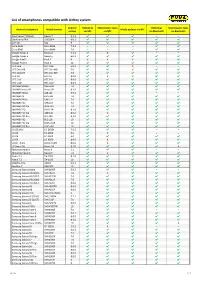
List of Smartphones Compatible with Airkey System
List of smartphones compatible with AirKey system Android Unlocking Maintenance tasks Unlocking Maintenance tasks Android smartphone Model number Media updates via NFC version via NFC via NFC via Bluetooth via Bluetooth Asus Nexus 7 (Tablet) Nexus 7 5.1.1 ✔ ✔ ✔ – – Blackberry PRIV STV100-4 6.0.1 ✔ ✔ ✔ ✔ ✔ CAT S61 S61 9 ✔ ✔ ✔ ✔ ✔ Doro 8035 Doro 8035 7.1.2 – – – ✔ ✔ Doro 8040 Doro 8040 7.0 – – – ✔ ✔ Google Nexus 4 Nexus 4 5.1.1 ✔ X ✔ – – Google Nexus 5 Nexus 5 6.0.1 ✔ ✔ ✔ ✔ ✔ Google Pixel 2 Pixel 2 9 X X X ✔ ✔ Google Pixel 4 Pixel 4 10 ✔ ✔ ✔ ✔ ✔ HTC One HTC One 5.0.2 ✔ ✔ X – – HTC One M8 HTC One M8 6.0 ✔ ✔ X ✔ ✔ HTC One M9 HTC One M9 7.0 ✔ ✔ ✔ ✔ ✔ HTC 10 HTC 10 8.0.0 ✔ X X ✔ ✔ HTC U11 HTC U11 8.0.0 ✔ ✔ ✔ ✔ ✔ HTC U12+ HTC U12+ 8.0.0 ✔ ✔ ✔ ✔ ✔ HUAWEI Mate 9 MHA-L09 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI Nexus 6P Nexus 6P 8.1.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P8 lite ALE-L21 5.0.1 ✔ ✔ ✔ – – HUAWEI P9 EVA-L09 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P9 lite VNS-L21 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P10 VTR-L09 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P10 lite WAS-LX1 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P20 EML-L29 8.1.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P20 lite ANE-LX1 8.0.0 ✔ X ✔ ✔ ✔ HUAWEI P20 Pro CLT-L29 8.1.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P30 ELE-L29 10 ✔ ✔ ✔ ✔ ✔ HUAWEI P30 lite MAR-LX1A 10 ✔ ✔ ✔ ✔ ✔ HUAWEI P30 Pro VOG-L29 10 ✔ ✔ ✔ ✔ ✔ LG G2 Mini LG-D620r 5.0.2 ✔ ✔ ✔ – – LG G3 LG-D855 5.0 ✔ X ✔ – – LG G4 LG-H815 6.0 ✔ ✔ ✔ ✔ ✔ LG G6 LG-H870 8.0.0 ✔ X ✔ ✔ ✔ LG G7 ThinQ LM-G710EM 8.0.0 ✔ X ✔ ✔ ✔ LG Nexus 5X Nexus 5X 8.1.0 ✔ ✔ ✔ ✔ X Motorola Moto X Moto X 5.1 ✔ ✔ ✔ – – Motorola Nexus 6 Nexus 6 7.0 ✔ X ✔ ✔ ✔ Nokia 7.1 TA-1095 8.1.0 ✔ ✔ X ✔ ✔ Nokia 7.2 TA-1196 10 ✔ ✔ ✔