Hermes: a Scalable Event-Based Middleware
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Yuriy Brun Curriculum Vitae June 27, 2021 Page 1 of 32 Honors, Awards, Fellowships
Yuriy Brun College of Information and Computer Sciences +1-609-379-2786 University of Massachusetts [email protected] 140 Governors Dr., Amherst, MA 01003-9264 http://people.cs.umass.edu/brun/ Research Interests Software systems engineering, software fairness, self-adaptation, behavioral inference, and automated repair. Education UNIVERSITY OF SOUTHERN CALIFORNIA . Los Angeles, CA, USA 5/2008 Doctor of Philosophy in Computer Science Dissertation: Self-assembly for discreet, fault-tolerant, and scalable computation on Internet-sized distributed networks Advisor: Prof. Nenad Medvidovic´ 5/2006 Master of Science in Computer Science MASSACHUSETTS INSTITUTE OF TECHNOLOGY . Cambridge, MA, USA 9/2003 Master of Engineering in Electrical Engineering and Computer Science Thesis: Fault identification via dynamic analysis and machine learning Advisor: Prof. Michael D. Ernst 6/2003 Bachelor of Science in Computer Science and Engineering 6/2003 Bachelor of Science in Mathematics Employment History UNIVERSITY OF MASSACHUSETTS . Amherst, MA, USA 9/2021 – present Professor 9/2017 – 8/2021 Associate Professor 9/2012 – 8/2017 Assistant Professor Co-director: Laboratory for Advanced Software Engineering Research (LASER) Co-director: Programming Languages and Systems at Massachusetts (PLASMA) UNIVERSITY OF WASHINGTON . Seattle, WA, USA 9/2009 – 8/2012 NSF CRA Postdoctoral Computing Innovation Fellow UNIVERSITY OF SOUTHERN CALIFORNIA . Los Angeles, CA, USA 7/2008 – 9/2009 Postdoctoral Research Associate: Center for Systems and Software Engineering 8/2003 – -

ACM SIGCHI, SIGGRAPH, SIGPLAN and SIGSOFT, and in Cooperation
Software visualization encompasses the development and evaluation of methods for graphically representing different aspects of software, including its structure, its abstract and concrete execution, and its evolution. The goal of this symposium is to provide a forum for researchers from different backgrounds (HCI, software engineering, programming languages, visualization, computer science education) to discuss and present original research on software visualization. SoftVis '03 is the first meeting in a planned series of biennial conferences. Our objective is to make the SoftVis series the premier venue for presenting all types of research on software visualization. Papers June 11-13, 2003 We seek theoretical as well as practical papers on applications, techniques, tools and case studies. San Diego, USA Topics of interest include, but are not restricted to, the following: Sponsored by: · Visualization of algorithms, including numerical, geometric, genetic, distributed and graph algorithms ACM SIGCHI, SIGGRAPH, · Program visualization SIGPLAN and SIGSOFT, · Protocol and log visualization (security, trust) and in cooperation with ACM · Visualization of parallel programs SIGCSE. · Visualization in software engineering, e.g. UML diagrams · Visualization of the software development process Deadlines · Visualization of data and processes in applications · Educational software in computer science, in particular visualization of computational models · Graph drawing algorithm for software visualization Paper submission: · Visualization of data base schemes December 16, 2002 · Visual debugging · 3D software visualization Tutorial submission: · Software visualization on the internet January 15, 2003 · Program analyses and visualization · Integration of software visualization tools and development environments · Empirical evaluation of software visualization system effectiveness Notification of acceptance: January 27, 2003 Papers should represent original, unpublished results and will be rigorously reviewed by the international Program Committee. -

Central Library: IIT GUWAHATI
Central Library, IIT GUWAHATI BACK VOLUME LIST DEPARTMENTWISE (as on 20/04/2012) COMPUTER SCIENCE & ENGINEERING S.N. Jl. Title Vol.(Year) 1. ACM Jl.: Computer Documentation 20(1996)-26(2002) 2. ACM Jl.: Computing Surveys 30(1998)-35(2003) 3. ACM Jl.: Jl. of ACM 8(1961)-34(1987); 43(1996);45(1998)-50 (2003) 4. ACM Magazine: Communications of 39(1996)-46#3-12(2003) ACM 5. ACM Magazine: Intelligence 10(1999)-11(2000) 6. ACM Magazine: netWorker 2(1998)-6(2002) 7. ACM Magazine: Standard View 6(1998) 8. ACM Newsletters: SIGACT News 27(1996);29(1998)-31(2000) 9. ACM Newsletters: SIGAda Ada 16(1996);18(1998)-21(2001) Letters 10. ACM Newsletters: SIGAPL APL 28(1998)-31(2000) Quote Quad 11. ACM Newsletters: SIGAPP Applied 4(1996);6(1998)-8(2000) Computing Review 12. ACM Newsletters: SIGARCH 24(1996);26(1998)-28(2000) Computer Architecture News 13. ACM Newsletters: SIGART Bulletin 7(1996);9(1998) 14. ACM Newsletters: SIGBIO 18(1998)-20(2000) Newsletters 15. ACM Newsletters: SIGCAS 26(1996);28(1998)-30(2000) Computers & Society 16. ACM Newsletters: SIGCHI Bulletin 28(1996);30(1998)-32(2000) 17. ACM Newsletters: SIGCOMM 26(1996);28(1998)-30(2000) Computer Communication Review 1 Central Library, IIT GUWAHATI BACK VOLUME LIST DEPARTMENTWISE (as on 20/04/2012) COMPUTER SCIENCE & ENGINEERING S.N. Jl. Title Vol.(Year) 18. ACM Newsletters: SIGCPR 17(1996);19(1998)-20(1999) Computer Personnel 19. ACM Newsletters: SIGCSE Bulletin 28(1996);30(1998)-32(2000) 20. ACM Newsletters: SIGCUE Outlook 26(1998)-27(2001) 21. -

Richard Newton Taylor
Richard Newton Taylor Contact School of Information and Computer Sciences Information University of California, Irvine E-mail: [email protected] Irvine, CA 92697-3440 www.ics.uci.edu/∼taylor Citizenship USA Research Software engineering, software architecture, Web technologies, decentralized systems, Interests design, system engineering, development environments Education University of Colorado, Boulder, CO USA Ph.D., Computer Science, December 1980 Static Analysis of the Synchronization Structure of Concurrent Programs Advisor: Professor Leon J. Osterweil M.S., Computer Science, May 1976 University of Colorado, Denver, CO USA B.S., Applied Mathematics, May 1974 With Special Honors Minor in Distributed Engineering Awards & 1985 Presidential Young Investigator Award Honors 1998 ACM Fellow 2004 ICSE Distinguished Paper Award 2005 ACM SIGSOFT Distinguished Service Award 2008 ACM SIGSOFT/IEEE TCSE Most Influential Paper from ICSE 1998 Award 2009 Dean's Award for Graduate Student Mentoring 2009 ACM SIGSOFT Outstanding Research Award 2010 UC Irvine Chancellor's Professor 2012 Dean's Award for Excellence in Research 2017 Distinguished Engineering Alumni Award, University of Colorado Boulder 2017 ACM SIGSOFT Impact Paper Award (with Roy Fielding) 1 of 45 Professional 7/17-present Chancellor's Professor Emeritus, School of Information and Computer Experience Sciences, University of California, Irvine (UCI) 7/13-6/17 Chancellor's Professor Emeritus (Recalled status), School of Informa- tion and Computer Sciences, University of California, Irvine (UCI) 7/99{6/17 Director, Institute for Software Research, UCI. 1/03 -6/13 Professor (VIII), School of Information and Computer Sciences. Uni- versity of California, Irvine (UCI) 1/03{6/04 Chair, Department of Informatics, School of Information and Computer Sciences, UCI 7/91{12/02 Professor, Department of Information and Computer Science, UCI. -

Alexandra Meliou Curriculum Vitae October 5, 2020 Page 1 of 14 Honors, Awards, Fellowships
Alexandra Meliou College of Information and Computer Sciences +1-413-545-3788 University of Massachusetts [email protected] 140 Governors Dr., Amherst, MA 01003-9264 http://www.cs.umass.edu/∼ameli Research Interests My research augments data management with user-facing functionality that helps people make sense of their data and use it effectively, at a time when data becomes increasingly unpredictable, unwieldy, and unmanageable. I focus on issues of provenance, causality, explanations, data quality, usability, and data and algorithmic bias. In the past, I have worked on a variety of topics spanning data management, machine learning, and sensor networks. Education UNIVERSITY OF CALIFORNIA,BERKELEY: . Berkeley, CA, USA 2009 Doctor of Philosophy in Computer Science Dissertation: Querying uncertain data in resource-constrained settings Advisors: Joseph Hellerstein, Carlos Guestrin 2005 Master of Science in Computer Science Thesis: Data gathering tours in sensor networks Advisors: Joseph Hellerstein, Carlos Guestrin NATIONAL TECHNICAL UNIVERSITY OF ATHENS: . Athens, Greece 2003 Diploma in Electrical and Computer Engineering (5-year degree) Thesis: Modeling and exploring the algebraic properties of hierarchical structures Advisor: Timos Sellis Employment History UNIVERSITY OF MASSACHUSETTS: . Amherst, MA, USA 9/2019 – present Associate Professor 9/2012 – 8/2019 Assistant Professor UNIVERSITY OF WASHINGTON: . Seattle, WA, USA 9/2009 – 8/2012 Postdoctoral Research Associate Advisor: Dan Suciu UNIVERSITY OF CALIFORNIA,BERKELEY: . Berkeley, -

ACM Software Engineering Notes, Nov'14
Volume 39, Number 6 Published by the Association for Computing Machinery November 2014 Special Interest Group on Software Engineering SOFTWARE ENGINEERING notes TABLE OF CONTENTS LETTERS 1 From the Chair: If I Only Had a Brain – Will Tracz 2 From the Editor – Michael Wing 3 Top 10 Downloaded Articles 4 Top 10 Most Cited Articles 5 Bill Riddle, Past ACM SIGSOFT Chair, Dies – Jack Wileden 5 CAPS Award for ASE 2014 – Breno Miranda 6 CAPS ASE Experience – Tony Ohmann 6 New Guide to Computer Science Degrees – Dan Schuessler COLUMNS 6 Passages – Alex Groce 8 Surfing the Net for Software Engineering Notes – Mark Doernhoefer 17 Risks to the Public – Peter G. Neumann and contributors REPORTS & PAPERS 23 The list of Reports is found on page 3 28 The list of Papers is found on page 3 WORKSHOP & CONFERENCES 29 Calendar of Events – Daniela Castelluccia 32 ICSE 2015 38 FSE 2014 Software Engineering Notes is an informal publication of the ACM Special Interest Group on Software Engineering (SIGSOFT) concerned with the cost- effective, timely development and maintenance of high-quality software. Relevant topics include requirements, specification, design and implementation methods, software maintenance, reuse, and re-engineering, quality assurance, measurement and evaluation, software processes, automated tools, and practical experience, etc. SIGSOFT seeks to address research and development issues in these areas and to provide a common ground for both, through sponsorship of conferences, symposia and workshops, the publication of SEN, and the dissemination of information via the SIGSOFT member email distribution list. sponsors an annual conference, Foundations of Software Engineering www.sigsoft.org/SEN/ SIGSOFT (FSE), in the Fall and co-sponsors the International Conference of Software SIGSOFT EXECUTIVE COMMITTEE Engineering (ICSE) in the Spring, in addition to sponsoring several workshops and symposia each year on specialized and timely topics. -

List of Related Organizations and Conferences
List of Related Organizations and Conferences Organization/Event Name Sponsor Description # of days With approx. 80,000 members, ACM delivers resources that advance computing as a science and a profession. ACM provides the computing field's premier Digital ACM Library and serves its members and the computing profession with leading-edge publications, conferences, and career resources. With nearly 85,000 members, the IEEE Computer Society is the world’s leading organization of computing professionals. Founded in 1946, and the largest of the IEEE Computer Society 39 societies of the Institute of Electrical and Electronics Engineers (IEEE), the CS is dedicated to advancing the theory and application of computer and information- processing technology. ASPLOS is a multi-disciplinary conference for research that spans the boundaries of hardware, computer architecture, compilers, languages, operating systems, networking, and applications. ASPLOS provides a high quality forum for scientists and engineers to present their latest research findings in these rapidly changing ASPLOS XIII ACM SIGARCH, SIGPLAN, SIGOPS 3 days fields. It has captured some of the major computer systems innovations of the past two decades (e.g., RISC and VLIW processors, small and large-scale multiprocessors, clusters and networks-of-workstations, optimizing compilers, RAID, and network-storage system designs). BSDCan, a BSD conference held in Ottawa, Canada, has quickly established itself as the technical conference for people working on and with 4.4BSD based operating BSDCanada 4 days systems and related projects. The organizers have found a fantastic formula that appeals to a wide range of people from extreme novices to advanced The Federated Computer Research Conference (FCRC) assembles a spectrum of affiliated research conferences and workshops into a week long coordinated meeting 7 day mix of held at a common time in a common place. -
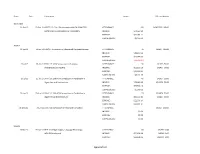
Appendix C SURPLUS/LOSS: $291.34 SIGCSE 0.00 Sigada 100.00 SIGAPP 0.00 SIGPLAN 0.00
Starts Ends Conference Actual SIGs and their % SIGACCESS 21-Oct-13 23-Oct-13 ASSETS '13: The 15th International ACM SIGACCESS ATTENDANCE: 155 SIGACCESS 100.00 Conference on Computers and Accessibility INCOME: $74,697.30 EXPENSE: $64,981.11 SURPLUS/LOSS: $9,716.19 SIGACT 12-Jan-14 14-Jan-14 ITCS'14 : Innovations in Theoretical Computer Science ATTENDANCE: 76 SIGACT 100.00 INCOME: $19,210.00 EXPENSE: $21,744.07 SURPLUS/LOSS: ($2,534.07) 22-Jul-13 24-Jul-13 PODC '13: ACM Symposium on Principles ATTENDANCE: 98 SIGOPS 50.00 of Distributed Computing INCOME: $62,310.50 SIGACT 50.00 EXPENSE: $56,139.24 SURPLUS/LOSS: $6,171.26 23-Jul-13 25-Jul-13 SPAA '13: 25th ACM Symposium on Parallelism in ATTENDANCE: 45 SIGACT 50.00 Algorithms and Architectures INCOME: $45,665.50 SIGARCH 50.00 EXPENSE: $39,586.18 SURPLUS/LOSS: $6,079.32 23-Jun-14 25-Jun-14 SPAA '14: 26th ACM Symposium on Parallelism in ATTENDANCE: 73 SIGARCH 50.00 Algorithms and Architectures INCOME: $36,107.35 SIGACT 50.00 EXPENSE: $22,536.04 SURPLUS/LOSS: $13,571.31 31-May-14 3-Jun-14 STOC '14: Symposium on Theory of Computing ATTENDANCE: SIGACT 100.00 INCOME: $0.00 EXPENSE: $0.00 SURPLUS/LOSS: $0.00 SIGAda 10-Nov-13 14-Nov-13 HILT 2013:High Integrity Language Technology ATTENDANCE: 60 SIGBED 0.00 ACM SIGAda Annual INCOME: $32,696.00 SIGCAS 0.00 EXPENSE: $32,404.66 SIGSOFT 0.00 Appendix C SURPLUS/LOSS: $291.34 SIGCSE 0.00 SIGAda 100.00 SIGAPP 0.00 SIGPLAN 0.00 SIGAI 11-Nov-13 15-Nov-13 ASE '13: ACM/IEEE International Conference on ATTENDANCE: 195 SIGAI 25.00 Automated Software Engineering -
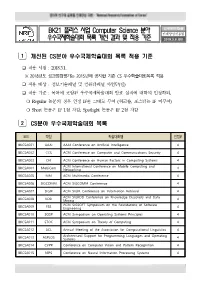
BK21 플러스 사업 Computer Science 분야 우수국제학술대회 목록 개선
BK21 플러스 사업 Computer Science 분야 인재양성지원실 인재양성진흥팀 우수국제학술대회 목록 개선 결과 및 적용 기준 2018.3.6.(화) 1 개선된 CS분야 우수국제학술대회 목록 적용 기준 ❑ 적용 시점 : 2018.3.1. ※ 2018년도 성과점검평가는 2015년에 공지한 기존 CS 우수학술대회목록 적용 ❑ 적용 대상 : 정보기술패널 및 컴퓨터패널 사업단(팀) ❑ 적용 기준 : 목록에 포함된 우수국제학술대회 발표 실적에 대하여 인정하되, ❍ Regular 논문의 경우 인정 IF를 그대로 부여 (워크숍, 포스터는 IF 미부여) ❍ Short 논문은 IF 1점 차감, Spotlight 논문은 IF 2점 차감 2 CS분야 우수국제학술대회 목록 코드 약칭 학술대회명 인정IF BKCSA001 AAAI AAAI Conference on Artificial Intelligence 4 BKCSA002 CCS ACM Conference on Computer and Communications Security 4 BKCSA003 CHI ACM Conference on Human Factors in Computing Systems 4 ACM International Conference on Mobile Computing and BKCSA004 MobiCom Networking 4 BKCSA005 MM ACM Multimedia Conference 4 BKCSA006 SIGCOMM ACM SIGCOMM Conference 4 BKCSA007 SIGIR ACM SIGIR Conference on Information Retrieval 4 ACM SIGKDD Conference on Knowledge Discovery and Data BKCSA008 KDD 4 Mining ACM SIGSOFT Symposium on the Foundations of Software BKCSA009 FSE Engineering 4 BKCSA010 SOSP ACM Symposium on Operating Systems Principles 4 BKCSA011 STOC ACM Symposium on Theory of Computing 4 BKCSA012 ACL Annual Meeting of the Association for Computational Linguistics 4 Architectural Support for Programming Languages and Operating BKCSA013 ASPLOS 4 Systems BKCSA014 CVPR Conference on Computer Vision and Pattern Recognition 4 BKCSA015 NIPS Conference on Neural Information Processing Systems 4 1 코드 약칭 학술대회명 인정IF BKCSA016 OOPSLA Conference on Object-Oriented Programming, System, Languages, 4 and Applications BKCSA017 INFOCOM IEEE Conference on Computer Communications -

Curriculum Vitae Matthew B
Curriculum Vitae Matthew B. Dwyer Business Address: Department of Computer Science University of Virginia PO Box 400740 Charlottesville, VA 22901 phone: (434) 982-2200 email: [email protected] Research Interests Specification and automated validation and verification of software systems. Education PhD (computer science) 1995, University of Massachusetts at Amherst. Advisor: Lori A. Clarke; disserta- tion title: \Data Flow Analysis for Verifying Correctness Properties of Distributed Systems". MS (computer science), 1989, University of Massachusetts at Boston. BS (electrical engineering), 1985, University of Rochester, Rochester, NY. Positions Held Professor, Department of Computer Science, University of Virginia, August 2018 - present. Professor, Department of Computer Science and Engineering, University of Nebraska - Lincoln, July 2004 - July 2018. Chair, Department of Computer Science and Engineering, University of Nebraska - Lincoln, July 2013 - June 2018. Extraordinary Professor, Department of Mathematical Sciences - Computer Science Division, Stellenbosch University, Sep. 2011 - Dec. 2017. Associate Professor, Department of Computing and Information Sciences, Kansas State University, July 1999 - June 2004. Assistant Professor, Department of Computing and Information Sciences, Kansas State University, Aug 1995 - July 1999. Research Assistant, Department of Computer Science, University of Massachusetts at Amherst, Sept 1990 - July 1995. Lecturer, Department of Mathematics and Computer Science, University of Massachusetts at Boston. -

Scouts: Improving the Diagnosis Process Through Domain-Customized Incident Routing
Scouts: Improving the Diagnosis Process Through Domain-customized Incident Routing Jiaqi Gao¢, Nofel Yaseen⋄, Robert MacDavid∗, Felipe Vieira Frujeri◦, Vincent Liu⋄, Ricardo Bianchini◦ Ramaswamy Adityax, Xiaohang Wangx, Henry Leex, David Maltzx, Minlan Yu¢, Behnaz Arzani◦ ¢Harvard University ⋄University of Pennsylvania ∗Princeton University ◦Microsoft Research xMicrosoft ABSTRACT service-level objectives. When incidents are mis-routed (sent to the Incident routing is critical for maintaining service level objectives wrong team), their time-to-diagnosis can increase by 10× [21]. in the cloud: the time-to-diagnosis can increase by 10× due to mis- A handful of well-known teams that underpin other services routings. tend to bear the brunt of this effect. The physical networking team Properly routing incidents is challenging because of the complex- in our large cloud, for instance, is a recipient in 1 in every 10 mis- ity of today’s data center (DC) applications and their dependencies. routed incidents (see §3). In comparison, the hundreds of other For instance, an application running on a VM might rely on a possible teams typically receive 1 in 100 to 1 in 1000. These findings functioning host-server, remote-storage service, and virtual and are common across the industry (see Appendix A). physical network components. It is hard for any one team, rule- Incident routing remains challenging because modern DC ap- based system, or even machine learning solution to fully learn the plications are large, complex, and distributed systems that rely complexity and solve the incident routing problem. We propose a on many sub-systems and components. Applications’ connections different approach using per-team Scouts. -

Chair's Message This Is My First Chair's Message
Chair's Message This is my ¯rst Chair's Message, having taken over from Rick Snodgrass as SIGMOD Chair only a couple of weeks ago. As you can imagine, I am struggling somewhere along the upward slope of the learning curve and the peak is not yet in sight. I want to ¯rst thank the previous SIGMOD Executive, Rick Snodgrass, Meral OzsoÄ yo·glu, and Joachim Hammer, for the extraordinary service they have performed for our community. Rick and Meral are still dealing with SIGMOD matters, trying to bring me and Marianne Winslett (Vice Chair) up to speed. Joachim Hammer is re-elected as Secretary/Treasurer, which gives me great comfort since I don't have to learn the budget issues immediately. On behalf of the three of us, I would like to thank the SIGMOD community for their trust. I want to use my ¯rst message to take stock of where SIGMOD is at this point. First let me comment on SIGMOD membership { we are in a healthy state. Even though many SIGs are experiencing membership decreases, SIGMOD has experienced a healthy increase over the last couple of years. According to the latest o±cial ACM statistics, we are the fourth largest SIG, with 3,288 members, behind SIGGRAPH, SIGCHI, and SIGPLAN. Perhaps more interesting is the trend. Table 1 gives the starting and ending membership numbers over the six-year interval between 1995 and 2001 for some sample SIGs, while Figure 1 depicts the trend. Note how SIGMOD's membership starts below all the other SIGs in 1995, but by 2001 has exceeded all of them.