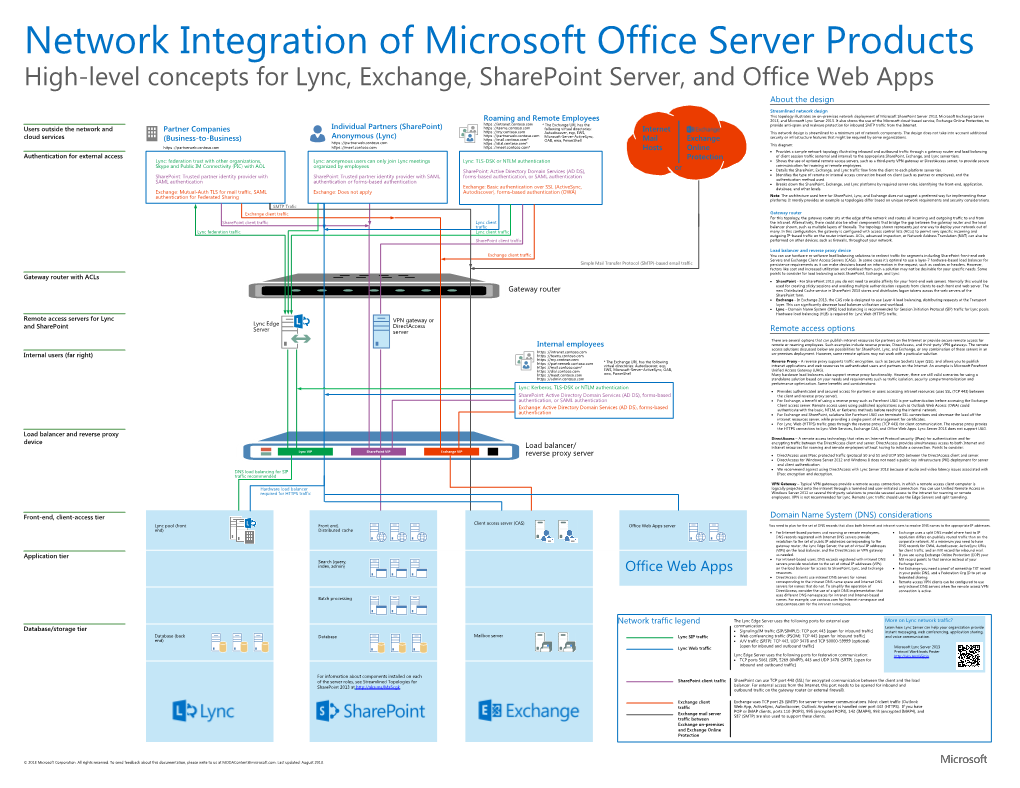
Office Web Apps About the Design
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Usporedba Linux I Microsoft Poslužiteljske Infrastrukture Kao Potpore Poslovanju Malih Tvrtki
USPOREDBA LINUX I MICROSOFT POSLUŽITELJSKE INFRASTRUKTURE KAO POTPORE POSLOVANJU MALIH TVRTKI Stanešić, Josip Undergraduate thesis / Završni rad 2020 Degree Grantor / Ustanova koja je dodijelila akademski / stručni stupanj: Algebra University College / Visoko učilište Algebra Permanent link / Trajna poveznica: https://urn.nsk.hr/urn:nbn:hr:225:716198 Rights / Prava: In copyright Download date / Datum preuzimanja: 2021-10-02 Repository / Repozitorij: Algebra Univerity College - Repository of Algebra Univerity College VISOKO UČILIŠTE ALGEBRA ZAVRŠNI RAD Usporedba Linux i Microsoft poslužiteljske infrastrukture kao potpore poslovanju malih tvrtki Josip Stanešić Zagreb, veljača 2020. Pod punom odgovornošću pismeno potvrđujem da je ovo moj autorski rad čiji niti jedan dio nije nastao kopiranjem ili plagiranjem tuđeg sadržaja. Prilikom izrade rada koristio sam tuđe materijale navedene u popisu literature, ali nisam kopirao niti jedan njihov dio, osim citata za koje sam naveo autora i izvor, te ih jasno označio znakovima navodnika. U slučaju da se u bilo kojem trenutku dokaže suprotno, spreman sam snositi sve posljedice, uključivo i poništenje javne isprave stečene dijelom i na temelju ovoga rada. U Zagrebu 1. veljače 2020. Josip Stanešić Predgovor Želio bih se zahvaliti svom mentoru i profesoru Vedranu Dakiću, profesorima Silviju Papiću i Jasminu Redžepagiću kao i svim ostalim profesorima na uloženom trudu, prenesenom znanju i odličnom preddiplomskom studiju. Također se želim zahvaliti obitelji na svoj podršci pruženoj tijekom studija. Prilikom uvezivanja rada umjesto ove stranice ne zaboravite umetnuti original potvrde o prihvaćanju teme završnog rada kojeg ste preuzeli u studentskoj referadi Sažetak Male tvrtke osnova su ekonomije Europe. U suvremenom poslovanju IT tehnologija i samim time IT infrastruktura nužni su za poslovanje čak i u tvrtkama kojima osnovna djelatnost nije u području informacijsko-komunikacijskih tehnologija. -

Windows Server 2012 R2 Directaccess
Windows Server 2012 R2 DirectAccess Deployment Guide UPDATED: 25 March 2021 Windows Server 2012 R2 DirectAccess Copyright Notices Copyright © 2002-2021 Kemp Technologies, Inc. All rights reserved. Kemp Technologies and the Kemp Technologies logo are registered trademarks of Kemp Technologies, Inc. Kemp Technologies, Inc. reserves all ownership rights for the LoadMaster and Kemp 360 product line including software and documentation. Used, under license, U.S. Patent Nos. 6,473,802, 6,374,300, 8,392,563, 8,103,770, 7,831,712, 7,606,912, 7,346,695, 7,287,084 and 6,970,933 kemp.ax 2 Copyright 2002-2021, Kemp Technologies, All Rights Reserved Windows Server 2012 R2 DirectAccess Table of Contents 1 Introduction 5 1.1 Document Purpose 5 1.2 Intended Audience 5 1.3 Related Firmware Version 5 1.4 About the Author 6 1.5 Assumptions 6 2 Load Balancing DirectAccess 7 2.1 Example Environment Setup 8 2.2 Prerequisites 9 3 Virtual Service Configuration 10 3.1 Enable Subnet Originating Requests Globally 10 3.2 Configure DirectAccess for Load Balancing 11 3.3 Configure the Servers Virtual Services 11 3.3.1 Configure a DirectAccess Server Virtual Service 12 3.3.2 Configure an Additional Virtual Service for the DirectAccess Server 13 3.3.3 Configure a Network Location Server (NLS) Virtual Service 14 3.3.4 Configure an NLS (Offloaded) Virtual Service 15 3.4 Configure DirectAccess to use a Load-Balanced NLS 17 3.5 Configure Geographic Load Balancing for NLS 18 4 Multisite Configuration and Load Balancing 22 4.1 Configure DirectAccess for Multisite 22 kemp.ax -

WINDOWS® 8.1 in DEPTH Copyright © 2014 by Pearson Education, Inc
Windows® 8.1 Brian Knittel Paul McFedries 800 East 96th Street Indianapolis, Indiana 46240 WINDOWS ® 8.1 IN DEPTH Copyright © 2014 by Pearson Education, Inc. All rights reserved. No part of this book shall be reproduced, stored in a Editor-in-Chief retrieval system, or transmitted by any means, electronic, mechanical, photo- Greg Wiegand copying, recording, or otherwise, without written permission from the publisher. No patent liability is assumed with respect to the use of the information con- Executive Editor tained herein. Although every precaution has been taken in the preparation of Rick Kughen this book, the publisher and author assume no responsibility for errors or omis- sions. Nor is any liability assumed for damages resulting from the use of the Development Editor information contained herein. Todd Brakke ISBN-13: 978-0-7897-5281-9 Managing Editor ISBN-10: 0-7897-5281-6 Sandra Schroeder Library of Congress Control Number: 2014930138 Printed in the United States of America Senior Project Editor Tonya Simpson First Printing: March 2014 Trademarks Copy Editor All terms mentioned in this book that are known to be trademarks or service Cheri Clark marks have been appropriately capitalized. Que Publishing cannot attest to the Senior Indexer accuracy of this information. Use of a term in this book should not be regarded as affecting the validity of any trademark or service mark. Cheryl Lenser Windows is a registered trademark of Microsoft Corporation. Technical Editor Warning and Disclaimer Karen Weinstein Every effort has been made to make this book as complete and as accurate as Editorial Assistant possible, but no warranty or fitness is implied. -

F5 and Windows Server 2012 Directaccess/Remote Access Services
White Paper F5 and Windows Server 2012 DirectAccess/Remote Access Services The F5 BIG-IP platform provides high availability, performance, and scalability when used to deliver traffic management and load balancing for the Microsoft Windows Server 2012 Remote Access Solutions: DirectAccess and Remote Access Services. by Ryan Korock Technical Director, Microsoft Solutions White Paper F5 and Windows Server 2012 Direct Access/Remote Access Services Contents Introduction 3 Benefits of Using F5 Products with DirectAccess and VPN 3 Architecture 4 A DirectAccess/VPN Server Front End 5 A Layered Approach with DirectAccess/VPN Servers 5 Dual Interface Vs. Single Interface DirectAccess/VPN Deployments 6 Single Site Vs. Multisite Deployment 8 Conclusion 9 2 White Paper F5 and Windows Server 2012 Direct Access/Remote Access Services Introduction For Windows 8 and Windows Server 2012, Microsoft has taken two remote access technologies found in previous versions of Windows Server, DirectAccess and VPN Server, and pulled them under the same management umbrella called simply Remote Access. F5 technologies can be deployed to manage traffic and balance loads on these services. Originally introduced in Windows Server 2008 R2 and Windows 7, DirectAccess shifted previous remote access technology. Unlike traditional VPNs, in which connections have been manually initiated at the user level, DirectAccess makes use of a seamless, system-level connection. This means that remote, domain-joined systems will automatically and securely build a corporate network presence upon boot. VPN, formerly known as Remote Access Services (RAS), was introduced in Windows NT and includes the traditional Windows VPN technologies, including IKEv2, SSTP, PPTP, and L2TP. Windows Server 2012 customers can deploy DirectAccess, VPN, or both, and it is often beneficial to deploy both. -

AWS Site-To-Site VPN User Guide AWS Site-To-Site VPN User Guide
AWS Site-to-Site VPN User Guide AWS Site-to-Site VPN User Guide AWS Site-to-Site VPN: User Guide Copyright © Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks and trade dress may not be used in connection with any product or service that is not Amazon's, in any manner that is likely to cause confusion among customers, or in any manner that disparages or discredits Amazon. All other trademarks not owned by Amazon are the property of their respective owners, who may or may not be affiliated with, connected to, or sponsored by Amazon. AWS Site-to-Site VPN User Guide Table of Contents What is Site-to-Site VPN ..................................................................................................................... 1 Concepts ................................................................................................................................... 1 Working with Site-to-Site VPN ..................................................................................................... 1 Site-to-Site VPN limitations ......................................................................................................... 2 Pricing ...................................................................................................................................... 2 How AWS Site-to-Site VPN works ........................................................................................................ 3 Site-to-Site VPN Components ..................................................................................................... -

Catalogue-2020.Pdf
2020 "#$$%&'(! 5%$>- 5 7289-&!:';!<'*=%>'$ 189 *+ ! ! ! "*->8.' CCNA CCNP CCIE ... !"#$%&' ! 66 (%&#)*+"',&)-)!./. ( 195 ( 82 56-#.'*8 ! 227 54'>@A-%&, 231 ! 156 ( +'$,%-&!.'!/*-0',$!1!23,4-.'$ !233 - 5%,*%B ! 176 !!!"elianistech"com 2 +,-./0. !"#$%&'()*+&,#$-"$,+.")/$-01/*),*$+,-+2/",*$2/"$3"/'$4&,*",/$()'2/"$35+,*'&-/4*+&,$ 6$/,$*78("$&/$/,"$*"47,&3&9+":$;,$35&44/''",4"<$"33"#$,"$,04"##+*",*$=)#<$&/$*'8#$ ="/<$ -"$ 4&,,)+##),4"#$ ='0)3)13"#$ -"$ 3)$ =)'*$ -/$ =)'*+4+=),*:$ ;,$ &/*'"<$ 4"#$ #*)9"#$ !"$ ='&9')(("$ -"$ 3)$ %&'()*+&, $ )$ 0.&3/0$ -),#$ /,"$ ."'#+&,$ =3/#$ '04",*": -0."3&=="'$-"$,&/."33"#$4&(=0*",4"#$6$=)'*+'$-5)42/+#$#&3+-"#: >"**"$%&'()*+&,$+,43/* ) $3"$=)##)9"$ >&,4"',",*$3"#$='&9')(("#$,04"##+*),*$/,$,+.")/$='0)3)13"$-"$4&,,)+##),4"#$"*$ !"#$%&%'213%)*+662 97 15 85%1%23456elianistech$com 3 ELIANIS TECH ELIANIS TECH e . !"#$ %&#'()*'+)(#$ ,-('-.+&'$ /+)($ '+0,#$ +&'(+$ /1-&%0-'%"&$ 2+$ #9*)(%'9>$ /-$ '9/9,7"&%+>$ /+$ 296+/",,+0+&'$ 21-,,/%*-'%"&#>$ /+#$ ,")($ +&*-2(+($ /-$ .+#'%"&$ 2+#$ ,("@+'#$ +'$ 0+''(+$ +&$ G)6(+$ )&+$ 4"(0-'%"&#$)'%/%#-'+)(#$-)'")($2+#$-,,/%*-'%"&#$3)(+-)'%8)+#$+'$2+$ *"//-3"(-'+)(#$+&$4"(0-'%"&5 '(-6-%/$*"//-3"(-'%4 $ 21)&$+&6%("&&+0+&'$'+*7&"/".%8)+5 ,("*+##)#$09'%+(#>$")$+&*"(+$/-$'(-"(0-'%"&$2+#$"(.-&%#-'%"&#>$ &"'(+$*-'-/".)+$#1+#'$296+/",,9$-6+*$2+#$0"2)/+#$+'$,-(*")(#$2+$ 4"(0-'%"&$"(%+&'9#$0-&-.+0+&'>$-&-/A#+$+'$09'7"2"/".%+5 -

Directaccess-Rmv6tf-26Apr11-Public
1. Introduction to DirectAccess 2. Technical Introduction 3. Technical Details within Demo 4. Summary Section 2: Technical Introduction Solution Overview Compliant Compliant Client Client Internet NAP/NPS Health Servers IPv6 tunnel over IPv4 Then IPv6 IPsec tunnel inside DirectAccess Thin Edge, Low Cost Clients have transparent IPv6 corpnet connectivity from CORPNET User anywhere with IPsec security Data Center and Business Critical Traffic to corporate network is routed through a Direct Access Resources Server (Windows 2008 R2 Server role) CORPNET User CORPNET Integrates with NAP IPsec enforcement for policy-based Compliant Network perimeter (optional) Forefront UAG and DirectAccess: Better Together Supports many non-DA clients Enables DA client access to Windows Server Windows 2008 IPv4-only internal hosts with 7 DNS64/NAT64 Windows Server 2008 R2 Enhances DA scalability Windows Always On Windows Server Managed 7 and management 2008 R2 IPv4 or IPv6 High avail, load balancing IPv6 SSL-VPN Monitoring, Reports Windows Vista/ Windows Server 2003 Provides OTP user auth Windows XP Legacy Application Non- Server Simplifies deployment and Windows DirectAccess Server administration Non Windows Unmanaged PDA + Server Easy Setup Wizard IPv6 IPv4 or IPv4 Auto GPO, script gen DA Connectivity Assistant Delivers a hardened, edge- ready solution using Forefront Threat Management Gateway firewall core Remote Client Management Only Only the first IPsec infrastructure tunnel is established. Clients have access only to specific infrastructure servers Remote management includes: Active Directory Group Policy, login scripts Pull or push* software updates, AV updates – using same internal mgmt servers Client health checking, reporting and remediation Client monitoring, vulnerability scanning; software inventories Help desk connect out* via Remote Assistance, Remote Desktop * Internally initiated connections outbound to remote DA client requires IPv6 path (e.g. -

Microsoft® Official Academic Course: Networking Fundamentals, Exam
Microsoft® Official Academic Course Networking Fundamentals, Exam 98-366 VP & PUBLISHER Barry Pruett SENIOR EXECUTIVE EDITOR Jim Minatel MICROSOFT PRODUCT MANAGER Microsoft Learning SENIOR EDITORIAL ASSISTANT Devon Lewis TECHNICAL EDITOR Ron Handlon CHANNEL MARKETING MANAGER Michele Szczesniak CONTENT MANAGEMENT DIRECTOR Lisa Wojcik CONTENT MANAGER Nichole Urban PRODUCTION COORDINATOR Nicole Repasky PRODUCTION EDITOR Umamaheswari Gnanamani COVER DESIGNER Tom Nery COVER PHOTO: © shutterstock/wavebreakmedia Copyright © 2017 by John Wiley & Sons, Inc. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, Inc. 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for permission should be addressed to the Permissions Department, John Wiley & Sons, Inc., 111 River Street, Hoboken, NJ 07030-5774, (201) 748-6011, fax (201) 748-6008. To order books or for customer service, please call 1-800-CALL WILEY (225-5945). Microsoft, Active Directory, AppLocker, Bing, BitLocker, Hyper-V, Internet Explorer, Microsoft Intune, Microsoft Office 365, SQL Server, Visual Studio, Windows Azure, Windows, Windows PowerShell, and Windows Server are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries. Other product and company names mentioned herein may be the trademarks of their respective owners. The example companies, organizations, products, domain names, e-mail addresses, logos, people, places, and events depicted herein are fictitious. -

A: Directaccess Provides Seamless and Transparent, Always On, Bi-Directional Remote Network Connectivity for Managed Windows Clients
Q: What is DirectAcces (DA)? A: DirectAccess provides seamless and transparent, always on, bi-directional remote network connectivity for managed Windows clients. Administrators can manage clients when they are outside the network, and remote users can access internal network resources whenever they have an Internet connection. Q: What's the difference between DirectAccess and VPN? A: DA and traditional VPN's both allow remote access to the internal network, but DA also allows remote management to maintain client compliance with security policies. Also, client-based VPN requires the user to initiate a connection to the corporate network where DirectAccess does not. Q: What are the requirements to deploy DirectAccess? A: The minimum DA infrastructure requires: Server running Windows Server 2012 R2 for current full functionality Active Directory DNS Clients and servers must be domain joined Public key infrastructure (PKI) is required to support Windows 7 clients, in addition to advanced features like OTP authentication, NAP integration, and multi-site deployments. Required certificate: SSL certificate – an SSL certificate issued from a trusted third-party public CA is recommended, but an internal CA can be used. If an internal CA is used, the certificate revocation list (CRL) must be publicly available. Recommended: Computer certificate – a computer certificate issued to the DirectAccess server and clients from internal CA. Q: How do I determine hardware needs? A: It's recommended to run DA on its own hardware, with supporting technologies running on separate servers. Each deployment will have its own needs for hardware components. Q: What clients are supported? A: Windows 7 Enterprise and Ultimate, Windows 8 and later Enterprise. -

Using Directaccess to Provide Secure Access to Corporate Resources from Anywhere
Using DirectAccess to Provide Secure Situation In the past few years, advances in Access to Corporate Resources from mobile computers and wireless broadband have enabled users to be Anywhere more productive while away from the office. According to IDC†, the third Published: May 2009 quarter of 2008 marked the point at which computer manufacturers began Although broadband services and Wi-Fi have dramatically improved, shipping more mobile computers than desktop computers worldwide. In 2008, the connectivity experience for remote corporate users remains largely remote workers will represent 26.8 % of unchanged. Microsoft Information Technology (Microsoft IT) is the total workforce, and that number will adopting the DirectAccess feature in Windows® 7 and in increase to 30.4% by 2011‡. Clearly, users are becoming more mobile, and IT Windows Server® 2008 R2 to enable employees to gain seamless professionals must provide an remote access to corporate applications and data. The solution, which infrastructure to allow them to remain only requires Internet connectivity and credentials, significantly productive. improves productivity and can be an important cost-saving The changing structure of business puts mechanism. more pressure on IT professionals to provide a high-performance and secure infrastructure for connecting remote Situation users while managing remote users and Today’s workforce is more mobile than ever. In order to maximize productivity, employees minimizing costs. need to have access to intranet resources wherever they travel. Providing this level of connectivity in a secure, manageable, and seamless way has been difficult with traditional Solution virtual private networks (VPNs). Connecting to a VPN requires multiple steps, which causes Microsoft IT is implementing delays while users wait for authentication. -

Security Assessment of Microsoft Directaccess
Security Assessment of Microsoft DirectAccess A thesis for the completion of Master of Science in Communication and Media Engineering CME By Ali Hardudi Supervised by Prof. Dr. rer. nat. habil. Dirk Westhoff M. Sc. Enno Rey ERNW GmbH. Agenda ¬ Introduction . Objective . A Quick Look into DirectAccess ¬ DirectAccess Lab ¬ Assessment . Scenarios and Attacker . IPv6 Attacks . TLS and IPSEC Default Configuration ¬ Conclusion 14.03.2016 Security Assessment of Microsoft DirectAccess #2 ERNW GmbH. Introduction 14.03.2016 Security Assessment of Microsoft DirectAccess #3 ERNW GmbH. Thesis Objective ¬ Thesis objective . Study the DirectAccess . Performing a security evaluation 14.03.2016 Security Assessment of Microsoft DirectAccess #4 ERNW GmbH. DirectAccess Features Pure IPv6 No user interaction Remote management and administration Bidirectional access Enhanced security features Working over IPv4 Internet infrastructure 14.03.2016 Security Assessment of Microsoft DirectAccess #5 ERNW GmbH. DirectAccess Limitations Not all Windows OS’s are supported The following options are not always possible: End to End encryption Force tunneling Performance degradation when IP-HTTPS tunneling is used Complex technology 14.03.2016 Security Assessment of Microsoft DirectAccess #6 ERNW GmbH. Technologies and Protocols IKE, HTTPS, DNS64, ISAKMP, Kerberos, ¬ Active Directory Domain Controller (AD DC). PKI, NTLM, DHCPV6 ¬ IPSEC ¬ Public Key Infrastructure (PKI) ¬ HTTPS server as Network Location Service (NLS) TCP, UDP ¬ Name Resolution Policy Table (NRPT) ¬ IPv6 tunneling technologies ¬ NAT64/DNS64 IPv6, IPv6 Tunneling, ICMPv6 ¬ Others (e.g. Forefront Unified Access Gateway IPsec (ESP, AH), NAT64 (UAG), Network Access Protection (NAP)) Figure 1 DirectAccess stack of main protocols 14.03.2016 Security Assessment of Microsoft DirectAccess #7 ERNW GmbH. TLS handshake HTTPS service DirectAccess C lie n t DirectAccess S e rv e r Figure 2 DirectAccess connection steps using IP-HTTPS 14.03.2016 Security Assessment of Microsoft DirectAccess #8 ERNW GmbH. -

Load Balancing Microsoft Directaccess V1.2.2
DEPLOYMENT GUIDE Load Balancing Microsoft DirectAccess v1.2.2 Deployment Guide Contents 1. About this Guide................................................................................................................................................................................................................................................................ 4 2. Loadbalancer.org Appliances Supported................................................................................................................................................................................................... 4 3. Loadbalancer.org Soft are !ersions Supported................................................................................................................................................................................. 4 4. Microsoft "indo s !ersions Supported................................................................................................................................................................................................... 4 5. Microsoft 2012 DirectAccess.............................................................................................................................................................................................................................. 4 Introduction.......................................................................................................................................................................................................................................................................................4