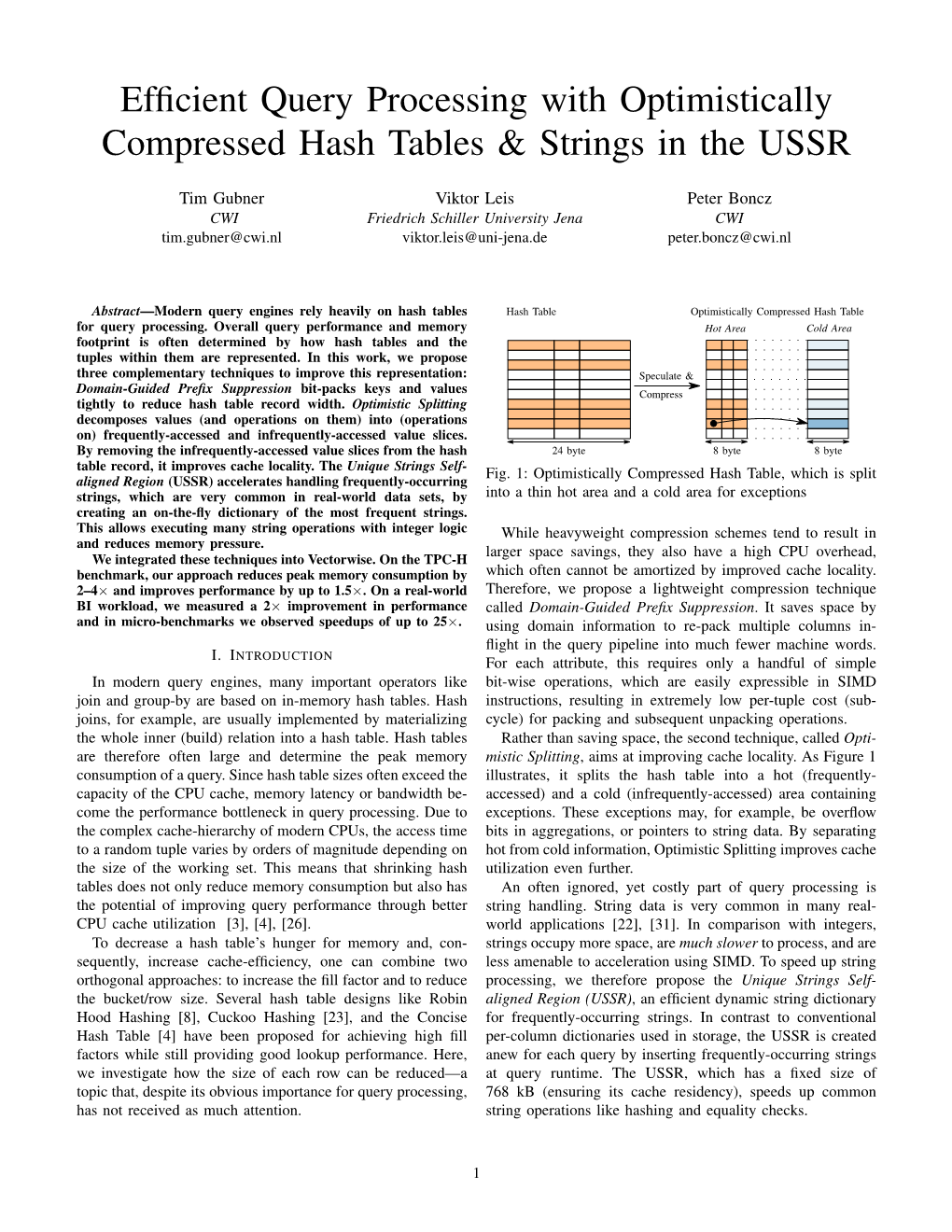
Efficient Query Processing with Optimistically Compressed Hash
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

LDBC Introduction and Status Update
8th Technical User Community meeting - LDBC Peter Boncz [email protected] ldbcouncil.org LDBC Organization (non-profit) “sponsors” + non-profit members (FORTH, STI2) & personal members + Task Forces, volunteers developing benchmarks + TUC: Technical User Community (8 workshops, ~40 graph and RDF user case studies, 18 vendor presentations) What does a benchmark consist of? • Four main elements: – data & schema: defines the structure of the data – workloads: defines the set of operations to perform – performance metrics: used to measure (quantitatively) the performance of the systems – execution & auditing rules: defined to assure that the results from different executions of the benchmark are valid and comparable • Software as Open Source (GitHub) – data generator, query drivers, validation tools, ... Audience • For developers facing graph processing tasks – recognizable scenario to compare merits of different products and technologies • For vendors of graph database technology – checklist of features and performance characteristics • For researchers, both industrial and academic – challenges in multiple choke-point areas such as graph query optimization and (distributed) graph analysis SPB scope • The scenario involves a media/ publisher organization that maintains semantic metadata about its Journalistic assets (articles, photos, videos, papers, books, etc), also called Creative Works • The Semantic Publishing Benchmark simulates: – Consumption of RDF metadata (Creative Works) – Updates of RDF metadata, related to Annotations • Aims to be -

Stisummit-Boncz-Final Fixed.Pptx
DB vs RDF: structure vs correlation +comments on data integration & SW Peter Boncz Senior Research Scientist @ CWI Lecturer @ Vrije Universiteit Amsterdam Architect & Co-founder MonetDB Architect & Co-founder VectorWise STI Summit, July 6, 2011 Riga. DB vs RDF: structure vs correlation 1 Correlations Real data is highly correlated } (gender, location) ó firstname } (profession,age) ó income But… database systems assume attribute independence } wrong assumption leads to suboptimal query plan STI Summit, July 6, 2011 Riga. DB vs RDF: structure vs correlation 2 Example: co-authorship query DBLP “find authors who published in VLDB, SIGMOD and Bioinformatics” SELECT author FROM publications p1, p2, p3 WHERE p1.venue = VLDB and p2.venue = SIGMOD and p3.venue = Bioinformatics and p1.author = =p2.author p2.author and and p1.author = =p3.author p3.author and and p2.author = =p3.author p3.author STI Summit, July 6, 2011 Riga. DB vs RDF: structure vs correlation 3 Correlations: RDBMS vs RDF Schematic structure in RDF data hidden in correlations, which are everywhere SPARQL leads to plans with } many self-joins } whose hit-ratio is correlated (with eg selections) Relational query optimizers do not have a clue è all self-joins look the same to it è random join order, bad query plans L STI Summit, July 6, 2011 Riga. DB vs RDF: structure vs correlation 4 RDF Engines to the Next Level Challenge: solving the correlation problem. Ideas? } Interleave optimization and execution } Run-time sampling to detect true selectivities } Run-time query (re-)planning } Tackling when there are long join chains } Creating partial path indexes } Graph “cracking”: index build as side-effect of query } . -

Designing Engines for Data Analysis Peter Boncz
Designing Engines For Data Analysis Peter Boncz Inaugural Lecture for the Special Chair “Large-Scale Analytical Data Management” Vrije Universiteit Amsterdam 17 October 2014 15:45-16:30 The age of Big Data An internet minute Designing Engines for Data Analysis - Inaugural Lecture - 17/10/2014 1 ` The age of Big Data. As the world turns increasingly digital, and all individuals and organizations interact more and more via the internet, for instance in social networks such as Facebook and Twitter, as they look for information online with Google, and watch movies or TV on YouTube and Netflix, the amount of information flying around is huge. Slide 1 depicts what happens on the internet during one minute [1]. The numbers are staggering, and are expected to keep growing. For instance, the amount of information being sent corresponds to a thousand full large disk drives, per minute. This is a hard disk drive stack of 20 meters high. All stored digital information together is estimated currently at 3 billion full disk drives, that is 4 zettabytes (when you start with a megabyte, a 1000 times that is a gigabyte, by multiplying again you get a petabyte, and then a zettabyte) Big Data. All this data is being gathered, kept and analyzed. Not only by the NSA ;-), it is spread over many organizations. The question for all of them, including the NSA, is: how to make use of it? “Big Data” Designing Engines for Data Analysis - Inaugural Lecture - 17/10/2014 2 This problem is called Big Data, and is characterized by the “three V-s”: The data comes in high Volume, The data comes at high Velocity, The data has high Variety, it consists of web pages, form, but also images, or any kind of text messages such as an email, Tweet or Facebook post. -

Dynamic Resource Management in Vectorwise on Hadoop
Vrije Universiteit, Amsterdam Faculty of Sciences, Computer Science Department Cristian Mihai Bârcă, student no. 2514228 Dynamic Resource Management in Vectorwise on Hadoop Master Thesis in Parallel and Distributed Computer Systems Supervisor / First reader: Prof. Dr. Peter Boncz, Vrije Universiteit, Centrum Wiskunde & Informatica Second reader: Prof. Dr. Henri Bal, Vrije Universiteit Amsterdam, August 2014 Contents 1 Introduction 1 1.1 Background and Motivation..............................1 1.2 Related Work......................................2 1.2.1 Hadoop-enabled MPP Databases.......................4 1.2.2 Resource Management in MPP Databases..................7 1.2.3 Resource Management in Hadoop Map-Reduce...............8 1.2.4 YARN Resource Manager (Hadoop NextGen)................9 1.3 Vectorwise........................................ 11 1.3.1 Ingres-Vectorwise Architecture........................ 12 1.3.2 Distributed Vectorwise Architecture..................... 13 1.3.3 Hadoop-enabled Architecture......................... 16 1.4 Research Questions................................... 19 1.5 Goals.......................................... 20 1.6 Basic ideas....................................... 20 2 Approach 21 2.1 HDFS Local Reads: DataTransferProtocol vs Direct I/O.............. 22 2.2 Towards Data Locality................................. 24 2.3 Dynamic Resource Management........................... 26 2.4 YARN Integration................................... 28 2.5 Experimentation Platform............................... 31 3 -

VU Research Portal
VU Research Portal Vectorwise: Beyond Column Stores Boncz, P.A.; Zukowski, M. published in IEEE Data Engineering Bulletin 2012 document version Peer reviewed version Link to publication in VU Research Portal citation for published version (APA) Boncz, P. A., & Zukowski, M. (2012). Vectorwise: Beyond Column Stores. IEEE Data Engineering Bulletin, 35(1), 21-27. http://oai.cwi.nl/oai/asset/19953/19953B.pdf General rights Copyright and moral rights for the publications made accessible in the public portal are retained by the authors and/or other copyright owners and it is a condition of accessing publications that users recognise and abide by the legal requirements associated with these rights. • Users may download and print one copy of any publication from the public portal for the purpose of private study or research. • You may not further distribute the material or use it for any profit-making activity or commercial gain • You may freely distribute the URL identifying the publication in the public portal ? Take down policy If you believe that this document breaches copyright please contact us providing details, and we will remove access to the work immediately and investigate your claim. E-mail address: [email protected] Download date: 29. Sep. 2021 This is a postprint of Vectorwise: Beyond Column Stores Boncz, P.A., Zukowski, M. IEEE Data Engineering Bulletin, 35(1), 21-27 Published version: no link available Link VU-DARE: http://hdl.handle.net/1871/39785 (Article begins on next page) Vectorwise: Beyond Column Stores Marcin Zukowski, Actian, Amsterdam, The Netherlands Peter Boncz, CWI, Amsterdam, The Netherlands Abstract This paper tells the story of Vectorwise, a high-performance analytical database system, from multiple perspectives: its history from academic project to commercial product, the evolution of its technical architecture, customer reactions to the product and its future research and development roadmap. -

Everything You Always Wanted to Know About Compiled and Vectorized Queries but Were Afraid to Ask
Everything You Always Wanted to Know About Compiled and Vectorized Queries But Were Afraid to Ask Timo Kersten Viktor Leis Alfons Kemper Thomas Neumann Andrew Pavlo Peter Boncz? Technische Universitat¨ Munchen¨ Carnegie Mellon University Centrum Wiskunde & Informatica? fkersten,leis,kemper,[email protected] [email protected] [email protected] ABSTRACT Like the Volcano-style iteration model, vectorization uses pull- The query engines of most modern database systems are either based iteration where each operator has a next method that produces based on vectorization or data-centric code generation. These two result tuples. However, each next call fetches a block of tuples state-of-the-art query processing paradigms are fundamentally dif- instead of just one tuple, which amortizes the iterator call over- ferent in terms of system structure and query execution code. Both head. The actual query processing work is performed by primitives paradigms were used to build fast systems. However, until today it that execute a simple operation on one or more type-specialized is not clear which paradigm yields faster query execution, as many columns (e.g., compute hashes for a vector of integers). Together, implementation-specific choices obstruct a direct comparison of ar- amortization and type specialization eliminate most of the overhead chitectures. In this paper, we experimentally compare the two mod- of traditional engines. els by implementing both within the same test system. This allows In data-centric code generation, each relational operator imple- us to use for both models the same query processing algorithms, the ments a push-based interface (produce and consume). -

Vectorwise: Beyond Column Stores
Vectorwise: Beyond Column Stores Marcin Zukowski, Actian, Amsterdam, The Netherlands Peter Boncz, CWI, Amsterdam, The Netherlands Abstract This paper tells the story of Vectorwise, a high-performance analytical database system, from multiple perspectives: its history from academic project to commercial product, the evolution of its technical architecture, customer reactions to the product and its future research and development roadmap. One take-away from this story is that the novelty in Vectorwise is much more than just column-storage: it boasts many query processing innovations in its vectorized execution model, and an adaptive mixed row/column data storage model with indexing support tailored to analytical workloads. Another one is that there is a long road from research prototype to commercial product, though database research continues to achieve a strong innovative influence on product development. 1 Introduction The history of Vectorwise goes back to 2003 when a group of researchers from CWI in Amsterdam, known for the MonetDB project [5], invented a new query processing model. This vectorized query processing approach became the foundation of the X100 project [6]. In the following years, the project served as a platform for further improvements in query processing [23, 26] and storage [24, 25]. Initial results of the project showed impressive performance improvements both in decision support workloads [6] as well as in other application areas like information retrieval [7]. Since the commercial potential of the X100 technology was apparent, CWI spun-out this project and founded Vectorwise BV as a company in 2008. Vectorwise BV decided to combine the X100 processing and storage components with the mature higher-layer database components and APIs of the Ingres DBMS; a product of Actian Corp. -

VU Research Portal
VU Research Portal Designing engines for data analysis Boncz, P.A. 2014 document version Publisher's PDF, also known as Version of record Link to publication in VU Research Portal citation for published version (APA) Boncz, P. A. (2014). Designing engines for data analysis. Vrije Universiteit Amsterdam. General rights Copyright and moral rights for the publications made accessible in the public portal are retained by the authors and/or other copyright owners and it is a condition of accessing publications that users recognise and abide by the legal requirements associated with these rights. • Users may download and print one copy of any publication from the public portal for the purpose of private study or research. • You may not further distribute the material or use it for any profit-making activity or commercial gain • You may freely distribute the URL identifying the publication in the public portal ? Take down policy If you believe that this document breaches copyright please contact us providing details, and we will remove access to the work immediately and investigate your claim. E-mail address: [email protected] Download date: 01. Oct. 2021 Designing Engines For Data Analysis Peter Boncz Inaugural Lecture for the Special Chair “Large-Scale Analytical Data Management” Vrije Universiteit Amsterdam 17 October 2014 15:45-16:30 The age of Big Data An internet minute Designing Engines for Data Analysis - Inaugural Lecture - 17/10/2014 1 ` The age of Big Data. As the world turns increasingly digital, and all individuals and organizations interact more and more via the internet, for instance in social networks such as Facebook and Twitter, as they look for information online with Google, and watch movies or TV on YouTube and Netflix, the amount of information flying around is huge.