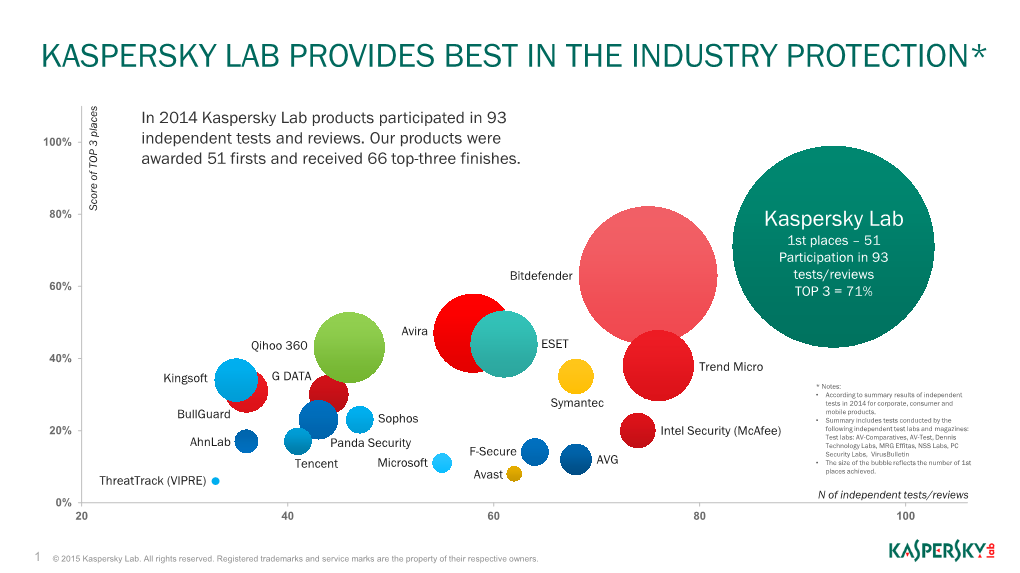
Kaspersky Lab Provides Best in the Industry Protection*
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

360 Antivirus for Pc Free Download Full Version
360 Antivirus For Pc Free Download Full Version 360 Antivirus For Pc Free Download Full Version 1 / 3 2 / 3 Windows Defender is improving, but you still shouldn't rely on Windows 10's security ... Kaspersky Security Cloud Free offers full-scale malware protection and even some ... Bitdefender Antivirus Free Edition includes the same core antivirus ... The free Qihoo 360 Total Security 8.6 comes with a ton of bonus tools, but its core .... Integrating award winning antivirus systems including 360 QVMII, 360 Cloud Engine, Avira or BitDefender to offer you with the ultimate in virus detection and .... 360 Total Security Download Free Antivirus Cloud-based technology this software can detect most of the new virus ... Total Security Download Full Version ... This software is a complete security package for your PC, laptop or mobile device.. Download 360 Total Security 10.6.0.1223. Keep your PC safe with five antivirus engines. Protecting your PC is a day-to-day essential, as it's becoming ever .... 360 Total Security is an unified solution for your PC security and performance. ... 360 Total Security - Free Antivirus & Internet Security Software for PC 8.0.0.1046 ... With Full Check, you can examine the overall condition of your computer within ... Starting from version 9, users of 360 Total Security are able to upgrade to .... Download 360 Total Security Premium 10.6.0.1223 for Windows. Fast downloads of the latest free software! ... QIHU 360(Full Version) ... edge antivirus protection, which is powered by 360 Heuristic Engine, 360 Cloud Engine .... Download 360 Total Security 2020 offline installers for free and safe for your Windows PC. -

Cost of a Cyber Incident)
CO ST OF A CYBER INCIDENT: S YSTEMATIC REVIEW AND C ROSS-VALIDATION OCTOBER 26, 2020 1 Acknowledgements We are grateful to Dr. Allan Friedman, Dr. Lawrence Gordon, Jay Jacobs, Dr. Sasha Romanosky, Matthew Shabat, Kelly Shortridge, Steven Surdu, David Tobar, Brett Tucker and Sounil Yu for the review comments and helpful feedback on the earlier draft of the report. The authors would like to thank CISA staff for support and advice on this project. 2 Table of Contents 1. Objectives .................................................................................................................................................................... 7 2. Results in Brief .......................................................................................................................................................... 8 3. Analysis ...................................................................................................................................................................... 16 3.1. Per-Incident Cost and Loss Estimates .............................................................................................. 18 3.1.1. Cross-Validation: Primary Loss Data for Large and Small Incidents .................................. 20 3.1.2. Reconciliation of Per-Incident Cost Studies .................................................................................. 26 3.1.3. Per-Record Estimates ............................................................................................................................. 29 3.2. Aggregate -

Forescout Counteract® Endpoint Support Compatibility Matrix Updated: October 2018
ForeScout CounterACT® Endpoint Support Compatibility Matrix Updated: October 2018 ForeScout CounterACT Endpoint Support Compatibility Matrix 2 Table of Contents About Endpoint Support Compatibility ......................................................... 3 Operating Systems ....................................................................................... 3 Microsoft Windows (32 & 64 BIT Versions) ...................................................... 3 MAC OS X / MACOS ...................................................................................... 5 Linux .......................................................................................................... 6 Web Browsers .............................................................................................. 8 Microsoft Windows Applications ...................................................................... 9 Antivirus ................................................................................................. 9 Peer-to-Peer .......................................................................................... 25 Instant Messaging .................................................................................. 31 Anti-Spyware ......................................................................................... 34 Personal Firewall .................................................................................... 36 Hard Drive Encryption ............................................................................. 38 Cloud Sync ........................................................................................... -

CODASPY'17 ~ Decompression Quines and Anti-Viruses
Decompression Quines and Anti-Viruses Margaux Canet Amrit Kumar Cédric Lauradoux Inria Inria Inria Univ. Grenoble Alpes Univ. Grenoble Alpes Mary-Andréa Reihaneh Safavi-Naini Rakotomanga University of Calgary Inria Univ. Grenoble Alpes ABSTRACT compression bombs also known as the zip of death exploit Data compression is ubiquitous to any information and com- the efficiency of compression algorithms to mount denial- munication system. It often reduces resources required to of-service (DoS) attacks. They often target web servers store and transmit data. However, the efficiency of com- and anti-viruses. Unfortunately, despite the fact that these pression algorithms also makes them an obvious target for threats have been known for years, some security products hackers to mount denial-of-service attacks. In this work, still remain vulnerable [9, 13]. we consider decompression quines, a specific class of com- The common definition of a decompression bomb found in pressed files that decompress to themselves. We analyze all the NIST guide [10] or the textbook [11] considers a small innocuous compressed file that decompresses to a gigantic the known decompression quines by studying their struc- 1 tures, and their impact on anti-viruses. Our analysis reveals file. A typical example of a decompression bomb is 42.zip that most of the anti-viruses do not have a suitable architec- (≈ 42 Kilobytes) that expands to 4.5 Petabytes. When a ture in place to detect decompression quines. Even worse, software attempts to naively decompress such a file, it con- some of them are vulnerable to denial-of-service attacks ex- sumes all the available memory and eventually crashes. -

Hostscan 4.8.01064 Antimalware and Firewall Support Charts
HostScan 4.8.01064 Antimalware and Firewall Support Charts 10/1/19 © 2019 Cisco and/or its affiliates. All rights reserved. This document is Cisco public. Page 1 of 76 Contents HostScan Version 4.8.01064 Antimalware and Firewall Support Charts ............................................................................... 3 Antimalware and Firewall Attributes Supported by HostScan .................................................................................................. 3 OPSWAT Version Information ................................................................................................................................................. 5 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.890.0 for Windows .................................................. 5 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.890.0 for Windows ........................................................ 44 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.824.0 for macos .................................................... 65 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.824.0 for macOS ........................................................... 71 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.730.0 for Linux ...................................................... 73 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.730.0 for Linux .............................................................. 76 ©201 9 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. -

Kaspersky Managed Service Providers Program
Kaspersky for Business MOBILE CONTROLS CLOUD ENDPOINT NETWORK SECURITY REPORTING VIRTUALIZATION SIEM SUPPORT SERVERS SERVICES CLOUD APPS Kaspersky Managed Service Providers Program Technical Reference Guide www.kaspersky.com #truecybersecurity Table of contents Program benefits 1 MSP program requirements 1 Products 2 Training and certification 5 Professional services 5 Technical designs 6 Kaspersky Endpoint Security Cloud 6 Kaspersky Endpoint Security for Business Select 6 Kaspersky Endpoint Security for Business Advanced 6 Kaspersky Hybrid Cloud Security 7 Kaspersky Security for Microsoft Office 365 8 Kaspersky Security for Mail Server 8 Kaspersky Security for Internet Gateways 9 Customer onboarding checklist 10 Appendix A 11 Appendix B 12 Appendix C 13 Appendix D 17 Program benefits • Flexible licensing allow you to choose between a monthly subscription and an annual license. Because you own the product license, there’s no need to spend time administrating contract renewals with customers — extending licenses is easy; no special action is required. • Increase sales revenues with volume-based discounts — the more customers you have, the less you pay. Pricing depends on the total number of devices of all customers. Sell more and gain bigger discounts. • Be even more efficient and grow your client base without having to hire additional engineers. With built-in best practices that drive operational efficiency, you’ll improve your tech-to-device ratio and boost your bottom line. Increase your scalability and protect more endpoints with fewer headaches. • Improved usability. Kaspersky Lab understands the importance of ease of use when it comes to security, and our design and usability specialists are closely involved in product development. -

2016 SIEM Content and Parsing Updates Table of Contents
2016 SIEM Content and Parsing Updates Table of Contents Table of Contents 2 SIEM Data Sources 5 January 21, 2016 5 February 10, 2016 5 February 16, 2016 5 February 26, 2016 5 March 25, 2016 5 June 2, 2016 6 June 8, 2016 6 July 19, 2016 6 August 04, 2016 6 August 11, 2016 6 August 15, 2016 6 September 1, 2016 6 September 2, 2016 7 September 26, 2016 7 October 12, 2016 7 October 13, 2016 7 November 7, 2016 7 November 10, 2016 8 November 11, 2016 8 December 2, 2016 8 SIEM Custom Types 9 October 13, 2016 9 October 25, 2016 9 SIEM Parsing Rules 10 January 8, 2015 10 January 12, 2016 10 January 13, 2016 10 January 21, 2016 10 January 22, 2016 11 January 25, 2016 11 January 29, 2016 11 January 29, 2016 11 February 4, 2016 11 February 8, 2016 12 February 10, 2016 12 February 11, 2016 12 February 16, 2016 12 February 17, 2016 12 February 19, 2016 13 February 23, 2016 13 February 24, 2016 13 February 25, 2016 13 February 26, 2016 13 February 29, 2016 14 March 2, 2016 14 March 3, 2016 14 March 7, 2016 15 March 8, 2016 15 March 9, 2016 15 March 11, 2016 15 March 14, 2016 15 March 16, 2016 15 March 17, 2016 16 March 18, 2016 16 March 21, 2016 16 March 24, 2016 17 March 25, 2016 17 March 29, 2016 17 March 30, 2016 18 March 31, 2016 18 April 01, 2016 18 April 04, 2016 18 April 07, 2016 18 April 08, 2016 18 April 21, 2016 18 2 April 26, 2016 19 May 3, 2016 19 May 5, 2016 19 May 5, 2016 19 May 9, 2016 19 May 11, 2016 19 May 16, 2016 19 May 18, 2016 19 May 23, 2016 19 May 24, 2016 20 May 25, 2016 20 May 26, 2016 21 May 27, 2016 21 June 2, 2016 21 June 06, -

Security Survey 2014
Security Survey 2014 www.av-comparatives.org IT Security Survey 2014 Language: English Last Revision: 28th February 2014 www.av-comparatives.org - 1 - Security Survey 2014 www.av-comparatives.org Overview Use of the Internet by home and business users continues to grow in all parts of the world. How users access the Internet is changing, though. There has been increased usage of smartphones by users to access the Internet. The tablet market has taken off as well. This has resulted in a drop in desktop and laptop sales. With respect to attacks by cyber criminals, this means that their focus has evolved. This is our fourth1 annual survey of computer users worldwide. Its focus is which security products (free and paid) are employed by users, OS usage, and browser usage. We also asked respondents to rank what they are looking for in their security solution. Survey methodology Report results are based on an Internet survey run by AV-Comparatives between 17th December 2013 and 17th January 2014. A total of 5,845 computer users from around the world anonymously answered the questions on the subject of computers and security. Key Results Among respondents, the three most important aspects of a security protection product were (1) Low impact on system performance (2) Good detection rate (3) Good malware removal and cleaning capabilities. These were the only criteria with over 60% response rate. Europe, North America and Central/South America were similar in terms of which products they used, with Avast topping the list. The share of Android as the mobile OS increased from 51% to 70%, while Symbian dropped from 21% to 5%. -

Herein After a Reasonable Opportunity for Discovery
Case 1:21-cv-06013 Document 1 Filed 07/13/21 Page 1 of 29 UNITED STATES DISTRICT COURT SOUTHERN DISTRICT OF NEW YORK PEDRO BALDERAS, Individually and On Case No. Behalf of All Others Similarly Situated, Plaintiff, CLASS ACTION COMPLAINT v. JURY TRIAL DEMANDED 360 DIGITECH, INC., HAISHENG WU, JIANG WU, and ZUOLI XU, Defendants. Plaintiff Pedro Balderas (“Plaintiff”), individually and on behalf of all others similarly situated, by Plaintiff’s undersigned attorneys, for Plaintiff’s complaint against Defendants, alleges the following based upon personal knowledge as to Plaintiff and Plaintiff’s own acts, and information and belief as to all other matters, based upon, inter alia, the investigation conducted by and through Plaintiff’s attorneys, which included, among other things, a review of the Defendants’ public documents, conference calls and announcements made by Defendants, United States (“U.S.”) Securities and Exchange Commission (“SEC”) filings, wire and press releases published by and regarding 360 DigiTech, Inc. (“360 DigiTech” or the “Company”), analysts’ reports and advisories about the Company, and information readily obtainable on the Internet. Plaintiff believes that substantial additional evidentiary support will exist for the allegations set forth herein after a reasonable opportunity for discovery. NATURE OF THE ACTION 1. This is a federal securities class action on behalf of a class consisting of all persons and entities other than Defendants that purchased or otherwise acquired 360 DigiTech securities between April 30, 2020 and July 7, 2021, both dates inclusive (the “Class Period”), seeking to 1 Case 1:21-cv-06013 Document 1 Filed 07/13/21 Page 2 of 29 recover damages caused by Defendants’ violations of the federal securities laws and to pursue remedies under Sections 10(b) and 20(a) of the Securities Exchange Act of 1934 (the “Exchange Act”) and Rule 10b-5 promulgated thereunder, against the Company and certain of its top officials. -

Consumer Security Products Performance Benchmarks (Edition 2) Antivirus & Internet Security Windows 10
Consumer Security Products Performance Benchmarks (Edition 2) Antivirus & Internet Security Windows 10 January 2020 Document: Consumer Security Products Performance Benchmarks (Edition 2) Authors: J. Han, D. Wren Company: PassMark Software Date: 13 January 2020 Edition: 2 File: Consumer_Security_Products_Performance_Benchmarks_2020_Ed_2.docx Consumer Security Performance Benchmarks 2019 PassMark Software Table of Contents TABLE OF CONTENTS ......................................................................................................................................... 2 REVISION HISTORY ............................................................................................................................................ 3 REFERENCES ...................................................................................................................................................... 3 EXECUTIVE SUMMARY ...................................................................................................................................... 4 OVERALL SCORE ................................................................................................................................................ 5 PRODUCTS AND VERSIONS ............................................................................................................................... 6 PERFORMANCE METRICS SUMMARY ................................................................................................................ 7 TEST RESULTS ................................................................................................................................................ -

Nessus and Antivirus
Nessus and Antivirus January 31, 2014 (Revision 4) Table of Contents Introduction ......................................................................................................................................... 3 Standards and Conventions........................................................................................................................... 3 Overview .............................................................................................................................................. 3 A Note on SCAP Audits ................................................................................................................................. 4 Microsoft Windows Defender ............................................................................................................. 4 Kaspersky Internet Security 2012 ...................................................................................................... 4 AVG 2012 ............................................................................................................................................. 7 Norton Internet Security 2012 .......................................................................................................... 10 Norton 360 ......................................................................................................................................... 14 Panda Internet Security 2012 ........................................................................................................... 18 Trend Micro Titanium -

Accomplished and Certified IT Security Professional with Experience Assisting Organizations Successfully Complete Enterprise-Wide Security Projects
ROHIT BANKOTI Accomplished and certified IT security professional with experience assisting organizations successfully complete enterprise-wide security projects. Experience in finance, technology, healthcare, telecom industries and a proven track record of streamlining security processes, design and implement efficient security solutions, lead and assist multi-disciplined, multi-national teams in achieving security efficiency. Professional Qualifications: • Degree Bachelor of Technology (Computer Science ) • CGPA 6.36/10 • Institute University Institute of Engg. & Tech. (MDU), Rohtak Academic Qualifications: • Completed XII standard from Hamdard Public School (CBSE) in with 79% • Completed X standard from Amrita Public School (CBSE) in with 81% CERTIFICATIONS • Sophos Certified Architect for UTM by RED Education. • Sophos Certified Engineer for Endpoint, MDM, Email protection, Encryption. • GFI (Languard, FAX maker, Mail essential & Cloud, Endpoint security • CEH version 7 training from net hub. • ECSA (E-council) 412-79 complete training from net hub. • Smooth Wall Certified engineer and Operator Certified. • McAfee certified for McAfee VSE, EPO, Mobile Management, HIPS and Mail. • Symantec Partner certification and Advanced Threat Protection. • Certified Information Security and Ethical hacking (C.I.S.E) from innobuzz. • Infowatch (DLP) training on endpoint and network level. • Qualys Vulnerability Expert. • C++ and .NET certification from Aptech, South Extension (Delhi) Professional Synopsis: Currently:- Working with Mckinsey & Company, Gurgaon, India as Security Engineer. - Mainly working with ATP projects. - Anti-phishing program - Other Operations 2015 to 2016 with CSC (Computer Science & Corporation), Noida - Sandboxing and Malware clean-up process - Identify Malware Domain and Phishing Attack vector. • Dec 2014 to Aug 2015 with ASIT, Delhi as Security Consultant. Working as UTM, SIEM, MDM and DLP architect.