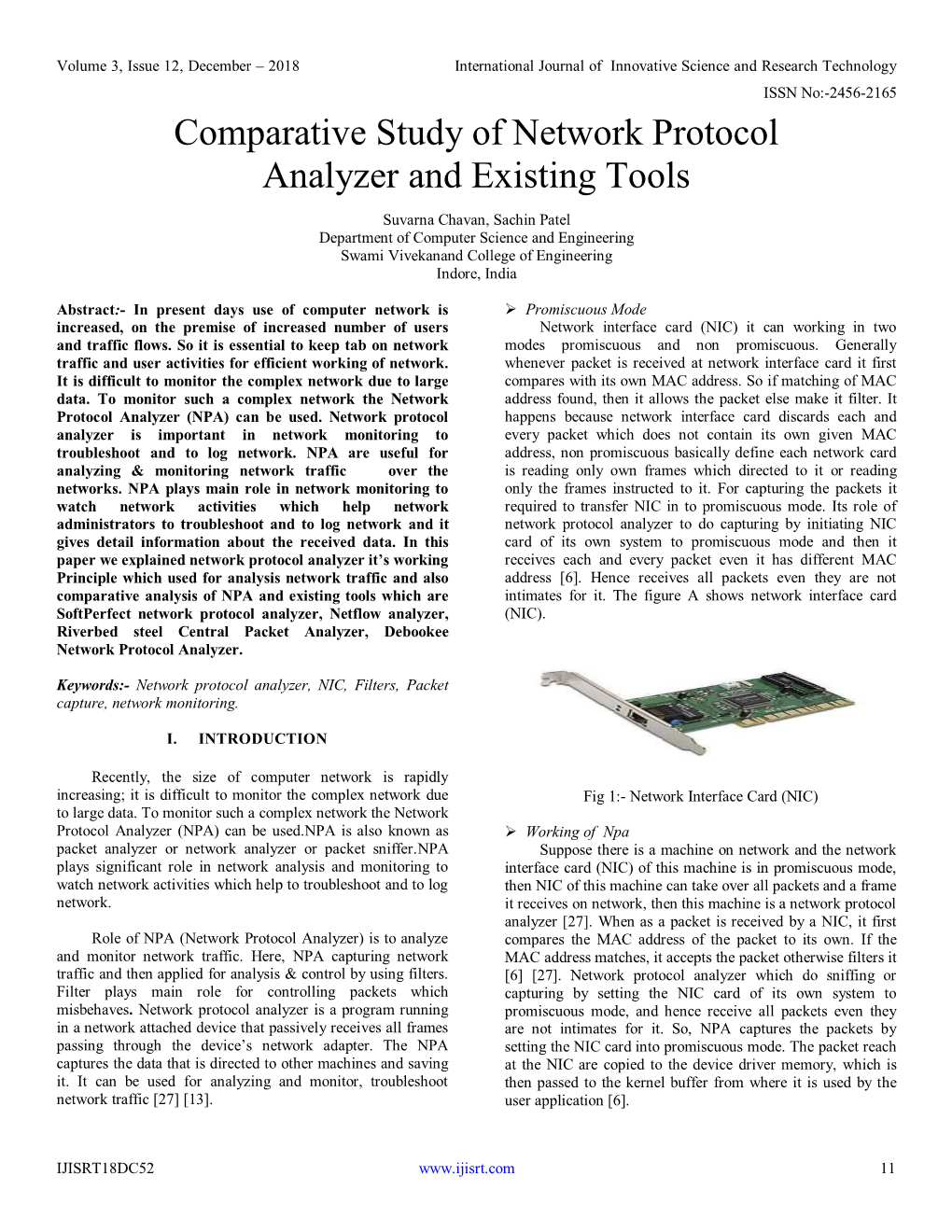
Comparative Study of Network Protocol Analyzer and Existing Tools
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Getting Started with Ethereal
Ethereal: Getting Started Computer Networking: A Top- down Approach Featuring the Internet, 3rd edition. Version: July 2005 © 2005 J.F. Kurose, K.W. Ross. All Rights Reserved ªTell me and I forget. Show me and I remember. Involve me and I understand.º Chinese proverb One's understanding of network protocols can often be greatly deepened by ªseeing protocols in actionº and by ªplaying around with protocolsº ± observing the sequence of messages exchanged between two protocol entities, delving down into the details of protocol operation, and causing protocols to perform certain actions and then observing these actions and their consequences. The basic tool for observing the messages exchanged between executing protocol entities is called a packet sniffer. As the name suggests, a packet sniffer captures (ªsniffsº) messages being sent/received from/by your computer; it will also typically store and/or display the contents of the various protocol fields in these captured messages. A packet sniffer itself is passive. It observes messages being sent and received by applications and protocols running on your computer, but never sends packets itself. Similarly, received packets are never explicitly addressed to the packet sniffer. Instead, a packet sniffer receives a copy of packets that are sent/received from/by application and protocols executing on your machine. Figure 1 shows the structure of a packet sniffer. At the right of Figure 1 are the protocols (in this case, Internet protocols) and applications (such as a web browser or ftp client) that normally run on your computer. The packet sniffer, shown within the dashed rectangle in Figure 1 is an addition to the usual software in your computer, and consists of two parts. -

Wireshark & Ethereal Network Protocol Analyzer
377_Eth2e_FM.qxd 11/14/06 1:23 PM Page i Visit us at www.syngress.com Syngress is committed to publishing high-quality books for IT Professionals and delivering those books in media and formats that fit the demands of our cus- tomers. We are also committed to extending the utility of the book you purchase via additional materials available from our Web site. SOLUTIONS WEB SITE To register your book, visit www.syngress.com/solutions. Once registered, you can access our [email protected] Web pages. There you may find an assortment of value-added features such as free e-books related to the topic of this book, URLs of related Web sites, FAQs from the book, corrections, and any updates from the author(s). ULTIMATE CDs Our Ultimate CD product line offers our readers budget-conscious compilations of some of our best-selling backlist titles in Adobe PDF form. These CDs are the perfect way to extend your reference library on key topics pertaining to your area of exper- tise, including Cisco Engineering, Microsoft Windows System Administration, CyberCrime Investigation, Open Source Security, and Firewall Configuration, to name a few. DOWNLOADABLE E-BOOKS For readers who can’t wait for hard copy, we offer most of our titles in download- able Adobe PDF form. These e-books are often available weeks before hard copies, and are priced affordably. SYNGRESS OUTLET Our outlet store at syngress.com features overstocked, out-of-print, or slightly hurt books at significant savings. SITE LICENSING Syngress has a well-established program for site licensing our e-books onto servers in corporations, educational institutions, and large organizations. -

Packet Capture and Analysis in Hybrid Environments
Packet Capture and Analysis in Hybrid Environments Lawrence Miller Inside the Guide • Discover why packet capture and analysis of on- premises and cloud applications in modern hybrid environments is so challenging • Learn how to analyze packets at the Transport and Application Layers to uncover the root cause of issues • Explore how putting the right tools in the hands of the right people can help make your entire IT team more effective THE GORILLA GUIDE TO... Packet Capture and Analysis in Hybrid Environments Express Edition By Lawrence Miller Copyright © 2020 by ActualTech Media All rights reserved. This book or any portion thereof may not be reproduced or used in any manner whatsoever without the express written permission of the publisher except for the use of brief quotations in a book review. Printed in the United States of America. ACTUALTECH MEDIA 6650 Rivers Ave Ste 105 #22489 North Charleston, SC 29406-4829 www.actualtechmedia.com PUBLISHER’S ACKNOWLEDGEMENTS EDITOR Keith Ward, ActualTech Media PROJECT MANAGER Wendy Hernandez, ActualTech Media EXECUTIVE EDITOR James Green, ActualTech Media LAYOUT AND DESIGN Olivia Thomson, ActualTech Media WITH SPECIAL CONTRIBUTIONS FROM Paul R. Dietz, Riverbed Stephen Creel, Riverbed Heidi Gabrielson, Riverbed Kowshik Bhat, Riverbed TABLE OF CONTENTS Introduction 7 Chapter 1: A Primer on Packets 8 Looking at Packets and Packet-Switched Networks 8 Understanding the Open Systems Interconnection (OSI) Model and Packet Encapsulation 11 Addressing Modern Packet Capture and Analysis Challenges 13 -

Steelcentral Packet Analyzer Reference Manual, Personal Edition
SteelCentral Packet Analyzer Reference Manual Personal Edition Version 10.9 October 2015 © 2015 Riverbed Technology. All rights reserved. Riverbed®, SteelApp™, SteelCentral™, SteelFusion™, SteelHead™, SteelScript™, SteelStore™, Steelhead®, Cloud Steelhead®, Virtual Steelhead®, Granite™, Interceptor®, Stingray™, Whitewater®, WWOS™, RiOS®, Think Fast®, AirPcap®, BlockStream™, FlyScript™, SkipWare®, TrafficScript®, TurboCap®, WinPcap®, Mazu®, OPNET®, and Cascade® are all trademarks or registered trademarks of Riverbed Technology, Inc. (Riverbed) in the United States and other countries. Riverbed and any Riverbed product or service name or logo used herein are trademarks of Riverbed. All other trademarks used herein belong to their respective owners. The trademarks and logos displayed herein cannot be used without the prior written consent of Riverbed or their respective owners. F5, the F5 logo, iControl, iRules, and BIG-IP are registered trademarks or trademarks of F5 Networks, Inc. in the U.S. and certain other countries. Linux is a trademark of Linus Torvalds in the United States and in other countries. VMware, ESX, ESXi are trademarks or registered trademarks of VMware, Incorporated in the United States and in other countries. Portions of SteelCentral™ products contain copyrighted information of third parties. Title thereto is retained, and all rights therein are reserved, by the respective copyright owner. PostgreSQL is (1) Copyright © 1996-2009 The PostgreSQL Development Group, and (2) Copyright © 1994-1996 the Regents of the University -

Wireshark Lab1, Part A: Getting Started
Wireshark Lab1, part a: Getting Started Version: 2.0 © 2007 J.F. Kurose, K.W. Ross. All Rights Reserved “Tell me and I forget. Show me and I remember. Involve me and I understand.” Chinese proverb One’s understanding of network protocols can often be greatly deepened by “seeing protocols in action” and by “playing around with protocols” – observing the sequence of messages exchanged between two protocol entities, delving down into the details of protocol operation, and causing protocols to perform certain actions and then observing these actions and their consequences. In these Wireshark labs we will observe the operation of real network protocols. You will be running various network applications in different scenarios using a computer in the lab or your own computer, if you prefer. You will observe the network protocols in your computer “in action,” interacting and exchanging messages with protocol entities executing elsewhere in the Internet. The basic tool for observing the messages exchanged between executing protocol entities is called a packet sniffer. As the name suggests, a packet sniffer captures (“sniffs”) messages being sent/received from/by your computer. It will also typically store and/or display the contents of the various protocol fields in these captured messages. A packet sniffer itself is passive. It observes messages being sent and received by applications and protocols running on your computer, but never sends packets itself. Similarly, received packets are never explicitly addressed to the packet sniffer. Instead, a packet sniffer receives a copy of packets that are sent/received from/by application and protocols executing on your machine. -

Qualitative Assessment of Digital Forensic Tools
Asian Journal of Electrical Sciences ISSN: 2249- 6297, Vol. 9, No. 1, 2020, pp. 25-32 © The Research Publication, www.trp.org.in Qualitative Assessment of Digital Forensic Tools Sakshi Singh and Suresh Kumar Department of Computer Science and Engineering, Ambedkar Institute Of Advanced Communication Technologies & Research New Delhi, Delhi, India. E-mail: [email protected], [email protected] Abstract - Forensic science is a study of science to criminals and A. Network Forensics: Network forensics is a branch of civil laws. Digital forensics is the part of forensic science relating advanced digital forensic identifying with the observing and to proof found in computers and advanced storage media. investigation of computer system traffic to collect network Forensic examiners gather, protect and break down logical traffic data, legitimate proof or interruption recognition. The confirmations over the span of examination. Digital information significant objective of the forensics of the network is to contains data as content, pictures, sound, video and so on. These days numerous cybercrime cases, for example, hacking, banking gather proof from the network traffic. It attempts to investigate cheats, phishing, email spamming, etc., have developed which are traffic information collected from various websites and connected with a computerized information. Since the digital network equipment, for example, IDS and firewalls. It screens investigation is turning into an expanding concern, numerous on the system to distinguish assaults and examine the idea of digital forensic tools have been created to manage the difficulties attacks. It is also the way of distinguishing interruption of exploring computerized wrongdoings. The motivation behind examples concentrating on attackers' exercises. -

Wireshark Network Security
Wireshark Network Security A succinct guide to securely administer your network using Wireshark Piyush Verma BIRMINGHAM - MUMBAI Wireshark Network Security Copyright © 2015 Packt Publishing All rights reserved. No part of this book may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, without the prior written permission of the publisher, except in the case of brief quotations embedded in critical articles or reviews. Every effort has been made in the preparation of this book to ensure the accuracy of the information presented. However, the information contained in this book is sold without warranty, either express or implied. Neither the author, nor Packt Publishing, and its dealers and distributors will be held liable for any damages caused or alleged to be caused directly or indirectly by this book. Packt Publishing has endeavored to provide trademark information about all of the companies and products mentioned in this book by the appropriate use of capitals. However, Packt Publishing cannot guarantee the accuracy of this information. First published: July 2015 Production reference: 1240715 Published by Packt Publishing Ltd. Livery Place 35 Livery Street Birmingham B3 2PB, UK. ISBN 978-1-78439-333-5 www.packtpub.com Credits Author Project Coordinator Piyush Verma Nidhi Joshi Reviewers Proofreader David Guillen Fandos Safis Editing Mikael Kanstrup Jaap Keuter Indexer Priya Sane Tigran Mkrtchyan Production Coordinator Commissioning Editor Shantanu N. Zagade Amarabha Banerjee Cover Work Acquisition Editor Shantanu N. Zagade Larissa Pinto Content Development Editor Siddhesh Salvi Technical Editor Madhunikita Sunil Chindarkar Copy Editor Dipti Mankame About the Author Piyush Verma currently serves as a senior security analyst at NII Consulting, India, and enjoys hacking his way into organizations (legally) and fixing the vulnerabilities encountered. -

Network Packet Analyzer Free
Network packet analyzer free Here are 20 of the best free tools for monitoring devices, services, ports or Microsoft Network Monitor is a packet analyzer that allows you to. Freeware Network Protocol Analyzer. Free Software Packet Sniffer, LAN and Internet Traffic Monitor. Network Data Capture Tool for Developers. Wireshark is the world's foremost and widely-used network protocol analyzer. It lets you see what's happening on your network at a microscopic level and is the. Wireshark is one of the most powerful network protocol analyzers on the market (free or paid). In fact, Wireshark is often considered the de facto. Download NetworkMiner packet analyzer for free. The Network Forensics Tool. NetworkMiner is a Network Forensic Analysis Tool (NFAT) for. Check out these top free network monitoring tools to improve your network Screenshot of Wireshark Open Source Network Packet Analyzer. A network sniffer (also known as a network analyzer, protocol analyzer or packet analyzer) is a software or hardware tool that can intercept and. Capsa Free network analyzer (packet sniffer) software for Windows platform, sniffer packets and analyze protocols, best FREE Network Analysis tool for network. Free network sniffer on a monitoring port. Traffic report by protocolls with a packet sniffer sensor. You can use the network sniffer for data acquisition, connection. The Ethereal network protocol analyzer has changed its name to Wireshark. The name might be new, but the software is the same. Wireshark's powerful. Packet Analyzer, free and safe download. Packet Analyzer latest version: Thoroughly capture and analyse all network communications. Packet Analyzer is a. Network Protocol Analyzer is a free and powerful network sniffer for capturing traffic and reconstructing TCP sessions, with filters and packet builder. -

Qualitative Assessment of Digital Forenisc Tools S
Vidyabharati International Interdisciplinary Research Journal 10(1) 12 - 2 3 ISSN 2319-4979 ___________________________________________________________________________ QUALITATIVE ASSESSMENT OF DIGITAL FORENISC TOOLS S. Singh1 and S. Kumar2 Ambedkar Institute of Advanced Communication Technologies& Research, Delhi, India [email protected], [email protected] ___________________________________________________________________________ ABSTRACT Forensic science is a study of science to criminals and civil laws. Digital forensics is the part of forensic science relating to proof found in computers and advanced storage media. Forensic examiners gather, protect and break down logical confirmations over the span of examination. Digital information contains data as content, pictures, sound, video and so on. These days numerous cybercrime cases, for example, hacking, banking cheats, phishing, email spamming, etc., have developed which are connected with a computerized information. Since the digital investigation is turning into an expanding concern, numerous digital forensic tools have been created to manage the difficulties of exploring computerized wrongdoings. The motivation behind digital forensics strategies is to look, protect and extract data on advanced frameworks to discover potential confirmations to exhibit them in the courtroom. In this paper, we have discussed five kinds of forensics namely Network Forensics, Live Forensics, Cyber Forensics, Database Forensics, and Mobile Forensics. The paper depicts a list of digital forensic tools in detail and looks at them based on the characterized parameters to figure out which tool suits better for any investigation. The paper looks at network, database and mobile forensic tools and examines the silent features and uniqueness of each of the tools along with their functionalities. __________________________________________________________________________________________ Keywords: Database forensics, Digital forensic tools, Forensic phases, Mobile forensics and Network forensics Introduction 5. -

A Survey of Tools for Monitoring and Visualization of Network Traffic
MASARYK UNIVERSITY FACULTY}w¡¢£¤¥¦§¨ OF I !"#$%&'()+,-./012345<yA|NFORMATICS A Survey of Tools for Monitoring and Visualization of Network Traffic BACHELOR’S THESIS Jakub Šk ˚urek Brno, Fall 2015 Declaration Hereby I declare, that this paper is my original authorial work, which I have worked out by my own. All sources, references and literature used or excerpted during elaboration of this work are properly cited and listed in complete reference to the due source. Jakub Šk ˚urek Advisor: doc. Ing. JiˇríSochor, CSc. ii Abstract The main goal of this thesis is to survey and categorize existing tools and applications for network traffic monitoring and visualization. This is accomplished by first dividing these into three main cate- gories, followed by additional subdivision into subcategories while presenting example tools and applications relevant to each category. iii Keywords network monitoring, network visualization, survey, traffic, monitor- ing iv Acknowledgement I would like to thank my advisor doc. Sochor for his advice and help- ful tips. A big thank you also goes to my family for the continued support and kind words given, and mainly for being understanding of my reclusive behaviour during the writing process. v Contents 1 Introduction ............................3 2 Computer Network Monitoring and Visualization .....5 2.1 Simple Network Management Protocol .........5 2.2 NetFlow/IPFIX Protocol ..................6 2.3 Internet Control Message Protocol ............6 2.4 Windows Management Instrumentation .........7 2.5 Packet Capture .......................7 3 Tools for Local Network Visualization ............9 3.1 Local Traffic and Performance Visualization .......9 3.1.1 NetGrok . .9 3.1.2 EtherApe . 11 3.2 Packet Capture and Visualization ............ -

Packet Analysis for Network Forensics: a Comprehensive Survey
Edith Cowan University Research Online ECU Publications Post 2013 1-1-2020 Packet analysis for network forensics: A comprehensive survey Leslie F. Sikos Edith Cowan University Follow this and additional works at: https://ro.ecu.edu.au/ecuworkspost2013 Part of the Physical Sciences and Mathematics Commons 10.1016/j.fsidi.2019.200892 Sikos, L. F. (2020). Packet analysis for network forensics: a comprehensive survey. Forensic Science International: Digital Investigation, 32, Article 200892. https://doi.org/10.1016/j.fsidi.2019.200892 This Journal Article is posted at Research Online. https://ro.ecu.edu.au/ecuworkspost2013/7605 Forensic Science International: Digital Investigation 32 (2020) 200892 Contents lists available at ScienceDirect Forensic Science International: Digital Investigation journal homepage: www.elsevier.com/locate/fsidi Packet analysis for network forensics: A comprehensive survey Leslie F. Sikos Edith Cowan University, Australia article info abstract Article history: Packet analysis is a primary traceback technique in network forensics, which, providing that the packet Received 16 May 2019 details captured are sufficiently detailed, can play back even the entire network traffic for a particular Received in revised form point in time. This can be used to find traces of nefarious online behavior, data breaches, unauthorized 27 August 2019 website access, malware infection, and intrusion attempts, and to reconstruct image files, documents, Accepted 1 October 2019 email attachments, etc. sent over the network. This paper is a comprehensive survey of the utilization of Available online xxx packet analysis, including deep packet inspection, in network forensics, and provides a review of AI- powered packet analysis methods with advanced network traffic classification and pattern identifica- Keywords: Packet analysis tion capabilities. -

Network Monitoring and Detecting Packets Using Packet Sniffing Method
International Journal of Scientific & Engineering Research, Volume 8, Issue 4, April-2017 ISSN 2229-5518 41 Network Monitoring And Detecting Packets Using Packet Sniffing Method S.Nagalakshmi ABSTRACT In the past five decades computer network have kept up growing in size, complexity, overall in the number of its users as well as being in a permanent evolution. Hence the amount of network traffic flowing at each node has increased drastically. With the development and popularization of network Technology, the management, maintenance and monitoring of network is important to keep the network smooth and improve economic efficiency. So to keep a track on these nodes a packet sniffer is used. Packet sniffers are useful for analyzing network traffic over wired or wireless networks. Sometimes a packet sniffer is called a network monitor or network analyzer. Many system administrator or network administrator use it for monitoring and troubleshooting network traffic. This paper focuses on the basics of packet sniffer; it’s working Principle which used for analysis Network traffic, how it works in both switched and non switched environment, its practical approach, its positive vs negative aspects and its safe guards. KEYWORDS: Packet Filter, Promiscuous mode, Spoofing and Intrusion, Network Monitoring, Network analyzer. —————————— —————————— I. INTRODUCTION with new switches. The replacement of hub with new Packet sniffing is the process of capturing the switches that makes switched environment is widely used information transmitted across network. In this process because it increases security. However, the thinking NIC capture all traffic that is flow inside or outside behind is somewhat flawed. It cannot be said that packet network.