NYS Senate Public Hearing Cyber Security
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Siber Güvenlik Ve Savunma STANDARTLAR Ve UYGULAMALAR
Siber Güvenlik ve Savunma STANDARTLAR ve UYGULAMALAR Editör Prof. Dr. Şeref SAĞIROĞLU Yazarlar Prof. Dr. Şeref SAĞIROĞLU - Onur AKTAŞ A. Oğuzhan ALKAN - Bilgehan ARSLAN Dr. Öğr. Üyesi Atila BOSTAN - Dr. Öğr. Üyesi Eyüp Burak CEYHAN Dr. Öğr. Üyesi İsmail Fatih CEYHAN Dr. Öğr. Üyesi Onur ÇAKIRGÖZ Dr. Öğr. Üyesi Mehmet DEMİRCİ - Sedef DEMİRCİ Doç. Dr. Gülüstan DOĞAN Dr. Öğr. Üyesi Muharrem Tuncay GENÇOĞLU Doç. Dr. Ali Hakan IŞIK - Burak ÖZÇAKMAK Dr. Öğr. Üyesi A. Nurdan SARAN - Doç. Dr. Gökhan ŞENGÜL Seda YILMAZ - Özgür YÜREKTEN Ankara 2019 Siber Güvenlik ve Savunma: Standartlar ve Uygulamalar Editör Prof. Dr. Şeref SAĞIROĞLU Yazarlar Prof. Dr. Şeref SAĞIROĞLU Doç. Dr. Gökhan ŞENGÜL Doç. Dr. Ali Hakan IŞIK Doç. Dr. Gülüstan DOĞAN Dr. Öğr. Üyesi Atila BOSTAN Dr. Öğr. Üyesi Eyüp Burak CEYHAN Dr. Öğr. Üyesi İsmail Fatih CEYHAN Dr. Öğr. Üyesi Onur ÇAKIRGÖZ Dr. Öğr. Üyesi Mehmet DEMİRCİ Dr. Öğr. Üyesi Muharrem Tuncay GENÇOĞLU Dr. Öğr. Üyesi A. Nurdan SARAN Onur AKTAŞ A. Oğuzhan ALKAN Bilgehan ARSLAN Sedef DEMİRCİ Burak ÖZÇAKMAK Seda YILMAZ Özgür YÜREKTEN ISBN: 978-605-2233-42-9 1. Baskı Aralık, 2019 / Ankara 1500 Adet Yayınları Yayın No: 334 Web: grafikeryayin.com Kapak, Sayfa Tasarımı, Baskı ve Cilt Grafik-Ofset Matbaacılık Reklamcılık San. ve Tic. Ltd. Şti. 1. Cadde 1396. Sokak No: 6 06520 (Oğuzlar Mahallesi) Balgat-ANKARA Tel : 0 312. 284 16 39 Pbx - Faks : 0 312. 284 37 27 E-posta : [email protected] Web : grafiker.com.tr Bu kitap HAVELSAN'ın katkılarıyla basılmıştır. İÇİNDEKİLER EDİTÖRDEN ........................................................................................................................................................... 11 BİLGİ GÜVENLİĞİ DERNEĞİ'NDEN ............................................................................. 15 ÖN SÖZ ........................................................................................................................................................................... 19 1. BÖLÜM SİBER GÜVENLİK MATEMATİĞİ 1.1. -

Zerohack Zer0pwn Youranonnews Yevgeniy Anikin Yes Men
Zerohack Zer0Pwn YourAnonNews Yevgeniy Anikin Yes Men YamaTough Xtreme x-Leader xenu xen0nymous www.oem.com.mx www.nytimes.com/pages/world/asia/index.html www.informador.com.mx www.futuregov.asia www.cronica.com.mx www.asiapacificsecuritymagazine.com Worm Wolfy Withdrawal* WillyFoReal Wikileaks IRC 88.80.16.13/9999 IRC Channel WikiLeaks WiiSpellWhy whitekidney Wells Fargo weed WallRoad w0rmware Vulnerability Vladislav Khorokhorin Visa Inc. Virus Virgin Islands "Viewpointe Archive Services, LLC" Versability Verizon Venezuela Vegas Vatican City USB US Trust US Bankcorp Uruguay Uran0n unusedcrayon United Kingdom UnicormCr3w unfittoprint unelected.org UndisclosedAnon Ukraine UGNazi ua_musti_1905 U.S. Bankcorp TYLER Turkey trosec113 Trojan Horse Trojan Trivette TriCk Tribalzer0 Transnistria transaction Traitor traffic court Tradecraft Trade Secrets "Total System Services, Inc." Topiary Top Secret Tom Stracener TibitXimer Thumb Drive Thomson Reuters TheWikiBoat thepeoplescause the_infecti0n The Unknowns The UnderTaker The Syrian electronic army The Jokerhack Thailand ThaCosmo th3j35t3r testeux1 TEST Telecomix TehWongZ Teddy Bigglesworth TeaMp0isoN TeamHav0k Team Ghost Shell Team Digi7al tdl4 taxes TARP tango down Tampa Tammy Shapiro Taiwan Tabu T0x1c t0wN T.A.R.P. Syrian Electronic Army syndiv Symantec Corporation Switzerland Swingers Club SWIFT Sweden Swan SwaggSec Swagg Security "SunGard Data Systems, Inc." Stuxnet Stringer Streamroller Stole* Sterlok SteelAnne st0rm SQLi Spyware Spying Spydevilz Spy Camera Sposed Spook Spoofing Splendide -

Ethical Hacking
Ethical Hacking Alana Maurushat University of Ottawa Press ETHICAL HACKING ETHICAL HACKING Alana Maurushat University of Ottawa Press 2019 The University of Ottawa Press (UOP) is proud to be the oldest of the francophone university presses in Canada and the only bilingual university publisher in North America. Since 1936, UOP has been “enriching intellectual and cultural discourse” by producing peer-reviewed and award-winning books in the humanities and social sciences, in French or in English. Library and Archives Canada Cataloguing in Publication Title: Ethical hacking / Alana Maurushat. Names: Maurushat, Alana, author. Description: Includes bibliographical references. Identifiers: Canadiana (print) 20190087447 | Canadiana (ebook) 2019008748X | ISBN 9780776627915 (softcover) | ISBN 9780776627922 (PDF) | ISBN 9780776627939 (EPUB) | ISBN 9780776627946 (Kindle) Subjects: LCSH: Hacking—Moral and ethical aspects—Case studies. | LCGFT: Case studies. Classification: LCC HV6773 .M38 2019 | DDC 364.16/8—dc23 Legal Deposit: First Quarter 2019 Library and Archives Canada © Alana Maurushat, 2019, under Creative Commons License Attribution— NonCommercial-ShareAlike 4.0 International (CC BY-NC-SA 4.0) https://creativecommons.org/licenses/by-nc-sa/4.0/ Printed and bound in Canada by Gauvin Press Copy editing Robbie McCaw Proofreading Robert Ferguson Typesetting CS Cover design Édiscript enr. and Elizabeth Schwaiger Cover image Fragmented Memory by Phillip David Stearns, n.d., Personal Data, Software, Jacquard Woven Cotton. Image © Phillip David Stearns, reproduced with kind permission from the artist. The University of Ottawa Press gratefully acknowledges the support extended to its publishing list by Canadian Heritage through the Canada Book Fund, by the Canada Council for the Arts, by the Ontario Arts Council, by the Federation for the Humanities and Social Sciences through the Awards to Scholarly Publications Program, and by the University of Ottawa. -

Information Security Primer from Social Engineering to SQL Injection...And Everything Beginning with P
Information Security Primer From Social Engineering to SQL Injection...and Everything Beginning with P PDF generated using the open source mwlib toolkit. See http://code.pediapress.com/ for more information. PDF generated at: Tue, 18 Aug 2009 21:14:59 UTC Contents Articles It Begins with S 1 Social engineering (security) 1 Spyware 7 SQL injection 26 Bonus Material 34 Password cracking 34 References Article Sources and Contributors 41 Image Sources, Licenses and Contributors 43 Article Licenses License 44 1 It Begins with S Social engineering (security) Social engineering is the act of manipulating people into performing actions or divulging confidential information. While similar to a confidence trick or simple fraud, the term typically applies to trickery or deception for the purpose of information gathering, fraud, or computer system access; in most cases the attacker never comes face-to-face with the victim. Social engineering techniques and terms All social engineering techniques are based on specific attributes of human decision-making known as cognitive biases.[1] These biases, sometimes called "bugs in the human hardware," are exploited in various combinations to create attack techniques, some of which are listed here: Pretexting Pretexting is the act of creating and using an invented scenario (the pretext) to persuade a targeted victim to release information or perform an action and is typically done over the telephone. It is more than a simple lie as it most often involves some prior research or set up and the use of pieces of known information (e.g. for impersonation: date of birth, Social Security Number, last bill amount) to establish legitimacy in the mind of the target. -
The Malware Book 2016
See discussions, stats, and author profiles for this publication at: https://www.researchgate.net/publication/305469492 Handbook of Malware 2016 - A Wikipedia Book Book · July 2016 DOI: 10.13140/RG.2.1.5039.5122 CITATIONS READS 0 13,014 2 authors, including: Reiner Creutzburg Brandenburg University of Applied Sciences 489 PUBLICATIONS 472 CITATIONS SEE PROFILE Some of the authors of this publication are also working on these related projects: NDT CE – Assessment of structures || ZfPBau – ZfPStatik View project 14. Nachwuchswissenschaftlerkonferenz Ost- und Mitteldeutscher Fachhochschulen (NWK 14) View project All content following this page was uploaded by Reiner Creutzburg on 20 July 2016. The user has requested enhancement of the downloaded file. Handbook of Malware 2016 A Wikipedia Book By Wikipedians Edited by: Reiner Creutzburg Technische Hochschule Brandenburg Fachbereich Informatik und Medien PF 2132 D-14737 Brandenburg Germany Email: [email protected] Contents 1 Malware - Introduction 1 1.1 Malware .................................................. 1 1.1.1 Purposes ............................................. 1 1.1.2 Proliferation ........................................... 2 1.1.3 Infectious malware: viruses and worms ............................. 3 1.1.4 Concealment: Viruses, trojan horses, rootkits, backdoors and evasion .............. 3 1.1.5 Vulnerability to malware ..................................... 4 1.1.6 Anti-malware strategies ..................................... 5 1.1.7 Grayware ............................................ -

D6.2 Altcoins – Alternatives to Bitcoin and Their Increasing Presence In
Ref. Ares(2018)1599225 - 22/03/2018 RAMSES Internet Forensic platform for tracking the money flow of financially-motivated malware H2020 - 700326 D6.2 Altcoins: Alternatives to Bitcoin and their increasing presence in Malware-related Cybercrime Lead Authors: Darren Hurley-Smith (UNIKENT), Julio Hernandez-Castro (UNIKENT) With contributions from: Edward Cartwright (UNIKENT), Anna Stepanova (UNIKENT) Reviewers: Luis Javier Garcia Villalba (UCM) Deliverable nature: Report (R) Dissemination level: Public (PU) (Confidentiality) Contractual delivery date: 31/08/2017 Actual delivery date: 31/08/2017 Version: 1.0 Total number of pages: 36 Keywords: Cryptocurrency, altcoin, malware, darknet market, privacy Abstract Bitcoin is a relatively well-known cryptocurrency, a digital token representing value. It uses a blockchain, a distributed ledger formed of blocks which represent a network of computers agreeing that transactions have occurred, to provide a ledger of sorts. This technology is not unique to Bitcoin, many so-called ‘altcoins’ now exist. These alternative coins provide their own services, be it as a store of value with improved transactions (lower fees, higher speed), or additional privacy. Malware and Dark Net Market (DNM) operators have used Bitcoin to facilitate pseudo-anonymous extraction of value from their victims and customers. However, several high-profile arrests have been made using Bitcoin transaction graphing methods, proving that the emphasis is on the pseudo part of pseudo-anonymity. Altcoins specialising in masking the users’ identity – Monero, ZCash, and Dash – are therefore of interest as the next potential coins of choice for criminals. Ethereum, being the second largest crypto-currencies and imminently implementing its own privacy features, is also of interest. -

Ransomware Payments in the Bitcoin Ecosystem
Ransomware Payments in the Bitcoin Ecosystem Masarah Paquet-Clouston Bernhard Haslhofer Benoît Dupont GoSecure Research Austrian Institute of Technology Université de Montréal Montreal, Canada Vienna, Austria Montreal, Canada [email protected] [email protected] [email protected] ABSTRACT the time of writing, there are 5051 known ransomware families de- Ransomware can prevent a user from accessing a device and its tected and almost all of them demand payments in Bitcoin [27], files until a ransom is paid to the attacker, most frequently in Bit- which is the most prominent cryptocurrency. coin. With over 500 known ransomware families, it has become Yet, global and reliable statistics on the impact of cybercrime in one of the dominant cybercrime threats for law enforcement, se- general, and ransomware in particular, are missing, causing a large curity professionals and the public. However, a more comprehen- misunderstanding regarding the severity of the threat and the ex- sive, evidence-based picture on the global direct financial impact tent to which it fuels a large illicit business. Most of the statistics of ransomware attacks is still missing. In this paper, we present available on cybercrime and ransomware are produced by private a data-driven method for identifying and gathering information corporations (cf. [29, 38, 39]) that do not disclose their underlying on Bitcoin transactions related to illicit activity based on foot- methodologies and have incentives to over- or underreport them prints left on the public Bitcoin blockchain. We implement this since they sell cybersecurity products and services that are sup- method on-top-of the GraphSense open-source platform and ap- posed to protect their users against such threats [23]. -

Applied Network Security Monitoring 1St Edition Pdf, Epub, Ebook
APPLIED NETWORK SECURITY MONITORING 1ST EDITION PDF, EPUB, EBOOK Chris Sanders | 9780124172166 | | | | | Applied Network Security Monitoring 1st edition PDF Book Network security monitoring is based on the principle that prevention eventually fails. Skip to main content. Your review was sent successfully and is now waiting for our team to publish it. Institutional Subscription. Handling time. Great book on important subject. Packet Headers Appendix 4. Additional Data Analysis. Three basic actions regarding the packet consist of a silent discard, discard with Internet Control Message Protocol or TCP reset response to the sender, and forward to the next hop. Payment details. Building an Intelligence-Led Security Program. Making Decisions with Sguil. Suspicious Port 53 Traffic. Sensor Management. SKU: khvqs Category: Ebook. Buy only this item Close this window. Refer to eBay Return policy for more details. Anti-keylogger Antivirus software Browser security Data loss prevention software Defensive computing Firewall Internet security Intrusion detection system Mobile security Network security. So What Is Sguil? Please enter a valid ZIP Code. As of , the next- generation firewall provides a wider range of inspection at the application layer, extending deep packet inspection functionality to include, but is not limited to:. Alert Data: Bro and Prelude. Interest will be charged to your account from the purchase date if the balance is not paid in full within 6 months. Shipping help - opens a layer International Shipping - items may be subject to customs processing depending on the item's customs value. Retrieved Network security monitoring NSM equips security staff to deal with the inevitable consequences of too few resources and too many responsibilities. -

Fraud; Recognition & Prevention
Fraud; Recognition & Prevention Issue 10 July 2021 WORLD LEADERS IN PIONEERING BODY WORN VIDEO TECHNOLOGY Proud to be supporting the return of these LIVE events across the UK in Autumn 2021... The Emergency Services Show 7th and 8th September | NEC Birmingham | stand L85 International Security Expo At the forefront 28th and 29th September | London Olympia | stand C2 of mobile, digital BAPCO Annual Conference & Exhibition evidence gathering 12th and 13th October | Ricoh Arena Coventry | stand C20 technology since 2005. FIND OUT MORE: WWW.AUDAXUK.COM | [email protected] | WWW.VIMEO.COM/SHOWCASE/AUDAXGLOBAL 2 Foreword: Well at long last there is light at the end of the very long COVID tunnel. As numerous industries start to return to normal, or are even doing better than anticipated, due to the economic defibrillator that the lifting of restrictions represents to so many. I am personally seeing a shortage of trained and licenced security officers in several sectors. Just maybe, this will force a rise in contract charge rates, and drive salaries up! I can but hope. One sector of society that have enjoyed lockdown and has made a fortune from an unexpectedly housebound population, are the fraudsters and con artists….. There has never been such a deluge of online cons, telephone scams and fake NHS sites selling tests, vaccines and all manner of bogus stuff, all capitalising on the understandable fears and concerns of the nation, and the desire we all have to protect and do the best for our families and loved ones. What can you do to protect yourself and those you hold dear, from this non-stop deluge of lies, cons, misinformation and very clever schemes designed to part you from as much money as possible? As luck would have it, amongst other things, this issue is taking a look at the many devious faces of fraud, and some of the top experts in their fields have contributed some great advice and guidance designed to help you avoid the many traps that the criminal fraternity have set for the unwary. -

Hacking the Abacus: an Undergraduate Guide to Programming Weird Machines
Hacking the Abacus: An Undergraduate Guide to Programming Weird Machines by Michael E. Locasto and Sergey Bratus version 1.0 c 2008-2014 Michael E. Locasto and Sergey Bratus All rights reserved. i WHEN I HEARD THE LEARN’D ASTRONOMER; WHEN THE PROOFS, THE FIGURES, WERE RANGED IN COLUMNS BEFORE ME; WHEN I WAS SHOWN THE CHARTS AND THE DIAGRAMS, TO ADD, DIVIDE, AND MEASURE THEM; WHEN I, SITTING, HEARD THE ASTRONOMER, WHERE HE LECTURED WITH MUCH APPLAUSE IN THE LECTURE–ROOM, HOW SOON, UNACCOUNTABLE,I BECAME TIRED AND SICK; TILL RISING AND GLIDING OUT,I WANDER’D OFF BY MYSELF, IN THE MYSTICAL MOIST NIGHT–AIR, AND FROM TIME TO TIME, LOOK’D UP IN PERFECT SILENCE AT THE STARS. When I heard the Learn’d Astronomer, from “Leaves of Grass”, by Walt Whitman. ii Contents I Overview 1 1 Introduction 5 1.1 Target Audience . 5 1.2 The “Hacker Curriculum” . 6 1.2.1 A Definition of “Hacking” . 6 1.2.2 Trust . 6 1.3 Structure of the Book . 7 1.4 Chapter Organization . 7 1.5 Stuff You Should Know . 8 1.5.1 General Motivation About SISMAT . 8 1.5.2 Security Mindset . 9 1.5.3 Driving a Command Line . 10 II Exercises 11 2 Ethics 13 2.1 Background . 14 2.1.1 Capt. Oates . 14 2.2 Moral Philosophies . 14 2.3 Reading . 14 2.4 Ethical Scenarios for Discussion . 15 2.5 Lab 1: Warmup . 16 2.5.1 Downloading Music . 16 2.5.2 Shoulder-surfing . 16 2.5.3 Not Obeying EULA Provisions . -

KOOBFACE: Inside a Crimeware Network
JR04-2010 KOOBFACE: Inside a Crimeware Network By NART VILLENEUVE with a foreword by Ron Deibert and Rafal Rohozinski November 12, 2010 WEB VERSION. Also found here: INFOWAR http://www.infowar-monitor.net/koobface MONITOR JR04-2010 Koobface: Inside a Crimeware Network - FOREWORD I Foreword There is an episode of Star Trek in which Captain Kirk and Spock are confronted by their evil doppelgängers who are identical in every way except for their more nefarious, diabolical character. The social networking community Facebook has just such an evil doppelgänger, and it is called Koobface. Ever since the Internet emerged from the world of academia and into the world-of-the-rest-of-us, its growth trajectory has been shadowed by the emergence of a grey economy that has thrived on the opportunities for enrichment that an open, globally connected infrastructure has made possible. In the early years, cybercrime was clumsy, consisting mostly of extortion rackets that leveraged blunt computer network attacks against online casinos or pornography sites to extract funds from frustrated owners. Over time, it has become more sophisticated, more precise: like muggings morphing into rare art theft. The tools of the trade have been increasingly refined, levering ingenuous and constantly evolving malicious software (or malware) with tens of thousands of silently infected computers to hide tracks and steal credentials, like credit card data and passwords, from millions of unsuspecting individuals. It has become one of the world economy’s largest growth sectors—Russian, Chinese, and Israeli gangs are now joined by upstarts from Brazil, Thailand, and Nigeria—all of whom recognize that in the globally connected world, cyberspace offers stealthy and instant means for enrichment. -
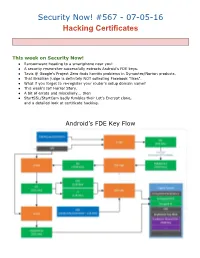
Security Now! #567Ана070516 Hacking Certificates
Security Now! #567 070516 Hacking Certificates This week on Security Now! ● Ransomware heading to a smartphone near you! ● A security researcher successfully extracts Android's FDE keys. ● Tavis @ Google's Project Zero finds horrific problems in Symantec/Norton products. ● That Brazilian judge is definitely NOT collecting Facebook "likes". ● What if you forget to reregister your router's setup domain name? ● This week's IoT Horror Story. ● A bit of errata and miscellany... then ● StartSSL/StartCom badly fumbles their Let's Encrypt clone, and a detailed look at certificate hacking. Android’s FDE Key Flow Security News Ransomware on mobile devices: knockknock & block https://usblog.kaspersky.com/mobileransomware2016/7346/ ● Android customers infected with mobile ransomware hit 136K in April 2016, nearly quadrupling from March 2015 ● Encrypt files or Block browser or the OS from working? ● Desktops favor file encryption, whereas mobile devices, which are typically backed up to the cloud, and could thereby have their files recovered and may also not contain any irreplaceable files are favoring the "Blocker"style ransomware. ● Kaspersky writes: Blockers are the much more popular means to infect Android devices. On mobiles, they act simply by overlaying the interface of every app with their own, so a victim can’t use any application at all. PC owners can get rid of a blocker with relative ease — all they need to do is remove the hard drive, plug it into another computer, and wipe out the blocker’s files. But you can’t simply remove the main storage from your phone — it’s soldered onto the motherboard.