Some Mobile Apps Add Anonymity to Social Networking
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

CS229 Project Report: Automated Photo Tagging in Facebook
CS229 Project Report: Automated photo tagging in Facebook Sebastian Schuon, Harry Robertson, Hao Zou schuon, harry.robertson, haozou @stanford.edu Abstract We examine the problem of automatically identifying and tagging users in photos on a social networking environment known as Facebook. The presented au- tomatic facial tagging system is split into three subsys- tems: obtaining image data from Facebook, detecting faces in the images and recognizing the faces to match faces to individuals. Firstly, image data is extracted from Facebook by interfacing with the Facebook API. Secondly, the Viola-Jones’ algorithm is used for locat- ing and detecting faces in the obtained images. Fur- thermore an attempt to filter false positives within the Figure 1: Schematic of the Facebook crawler face set is made using LLE and Isomap. Finally, facial recognition (using Fisherfaces and SVM) is performed on the resulting face set. This allows us to match faces 2 Collecting data from Facebook to people, and therefore tag users on images in Face- book. The proposed system accomplishes a recogni- To implement an automatic image tagging system, one tion accuracy of close to 40%, hence rendering such first has to acquire the image data. For the platform we systems feasible for real world usage. have chosen to work on, namely Facebook, this task used to be very sophisticated, if not impossible. But with the recent publication of an API to their platform, this has been greatly simplified. The API allows third party applications to integrate into their platform and 1 Introduction most importantly to access their databases (for details see figure 1 and [3]). -
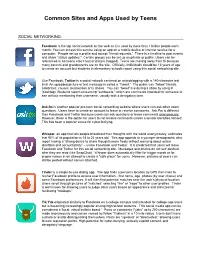
Common Sites and Apps Used by Teens
Common Sites and Apps Used by Teens SOCIAL NETWORKING: Facebook is the top social network on the web as it is used by more than 1 billion people each month. You can access this service using an app on a mobile device or internet service for a computer. People set up a profile and accept “friend requests.” There is a timeline to post events and share “status updates.” Certain groups can be set up as private or public. Users can be referenced in someone else’s text or picture (tagged). Teens are moving away from fb because many parents and grandparents are on the site. Officially, individuals should be 13 years of age to create an account but students in elementary schools report using this social networking site. Like Facebook, Twitter is a social network centered on microblogging with a 140-character text limit. An uploaded picture or text message is called a “Tweet.” The public can “follow” friends, celebrities, causes, businesses or tv shows. You can “tweet” live during a show by using # (hashtag). Students report concerning “subtweets,” which are comments intended for someone to see without mentioning their username, usually with a derogatory tone. Ask.fm is another popular pre-teen social networking website where users can ask other users questions. Users have to create an account to leave or receive comments. Ask.Fm is different than Facebook and Twitter because users can ask questions or leave comments anonymously. However, there is the option for users to not receive comments unless a sender identifies himself. This has been a popular venue for cyber-bullying. -

What Is Gab? a Bastion of Free Speech Or an Alt-Right Echo Chamber?
What is Gab? A Bastion of Free Speech or an Alt-Right Echo Chamber? Savvas Zannettou Barry Bradlyn Emiliano De Cristofaro Cyprus University of Technology Princeton Center for Theoretical Science University College London [email protected] [email protected] [email protected] Haewoon Kwak Michael Sirivianos Gianluca Stringhini Qatar Computing Research Institute Cyprus University of Technology University College London & Hamad Bin Khalifa University [email protected] [email protected] [email protected] Jeremy Blackburn University of Alabama at Birmingham [email protected] ABSTRACT ACM Reference Format: Over the past few years, a number of new “fringe” communities, Savvas Zannettou, Barry Bradlyn, Emiliano De Cristofaro, Haewoon Kwak, like 4chan or certain subreddits, have gained traction on the Web Michael Sirivianos, Gianluca Stringhini, and Jeremy Blackburn. 2018. What is Gab? A Bastion of Free Speech or an Alt-Right Echo Chamber?. In WWW at a rapid pace. However, more often than not, little is known about ’18 Companion: The 2018 Web Conference Companion, April 23–27, 2018, Lyon, how they evolve or what kind of activities they attract, despite France. ACM, New York, NY, USA, 8 pages. https://doi.org/10.1145/3184558. recent research has shown that they influence how false informa- 3191531 tion reaches mainstream communities. This motivates the need to monitor these communities and analyze their impact on the Web’s information ecosystem. 1 INTRODUCTION In August 2016, a new social network called Gab was created The Web’s information ecosystem is composed of multiple com- as an alternative to Twitter. -

Obtaining and Using Evidence from Social Networking Sites
U.S. Department of Justice Criminal Division Washington, D.C. 20530 CRM-200900732F MAR 3 2010 Mr. James Tucker Mr. Shane Witnov Electronic Frontier Foundation 454 Shotwell Street San Francisco, CA 94110 Dear Messrs Tucker and Witnov: This is an interim response to your request dated October 6, 2009 for access to records concerning "use of social networking websites (including, but not limited to Facebook, MySpace, Twitter, Flickr and other online social media) for investigative (criminal or otherwise) or data gathering purposes created since January 2003, including, but not limited to: 1) documents that contain information on the use of "fake identities" to "trick" users "into accepting a [government] official as friend" or otherwise provide information to he government as described in the Boston Globe article quoted above; 2) guides, manuals, policy statements, memoranda, presentations, or other materials explaining how government agents should collect information on social networking websites: 3) guides, manuals, policy statements, memoranda, presentations, or other materials, detailing how or when government agents may collect information through social networking websites; 4) guides, manuals, policy statements, memoranda, presentations and other materials detailing what procedures government agents must follow to collect information through social- networking websites; 5) guides, manuals, policy statements, memorandum, presentations, agreements (both formal and informal) with social-networking companies, or other materials relating to privileged user access by the Criminal Division to the social networking websites; 6) guides, manuals, memoranda, presentations or other materials for using any visualization programs, data analysis programs or tools used to analyze data gathered from social networks; 7) contracts, requests for proposals, or purchase orders for any visualization programs, data analysis programs or tools used to analyze data gathered from social networks. -

Dating App 20140708.Key
From ‘Like’ to Love: How Brands Can Woo Users on Messaging and Dating Apps 7/10/14 Dating goes digital The generation accustomed to communicating at all times is coming of age and bringing the same attitude to their romantic lives. ! “ I think in the time I was in a relationship, all dating communication went exclusively to text. You can’t call anybody anymore. If you call someone, they’re like ‘What? Are you on fire? Then quit wasting my time. Text me that [stuff].’” – Aziz Ansari, Comedian Credit: Comedy Central © 2013 IPG Media Lab. Proprietary & Confidential 2 We heart mobile dating apps Online dating services and apps are an increasingly common way to meet potential mates: • 1 in 3 single Americans have used an online dating service • 1 in 6 couples married in the last three years met online ! Graph Sources: marketingland.com/founders-whisper-tinder-75424; www.internetlivestats.com ! ! Sources: www.pewinternet.org/2013/10/21/online-dating-relationships/ cp.match.com/cppp/media/CMB_Study.pdf © 2013 IPG Media Lab. Proprietary & Confidential 3 Dating apps moved to mobile as messaging apps began to proliferate © 2013 IPG Media Lab. Proprietary & Confidential 4 But it’s not just dating apps Dating apps, social networks, and messaging apps are blurring as people seek, create, and document new relationships: • Glimpse connects people based on their Instagram photos • LinkedUp turns the professional site into a dating platform • Kik users share usernames instead of digits on multiple platforms © 2013 IPG Media Lab. Proprietary & Confidential 5 What’s going on here? As we noted in our white paper on Messaging Apps , messaging platforms are fighting for consumers and introducing new features to increase audience engagement. -

The Many Shades of Anonymity: Characterizing Anonymous Social Media Content
Proceedings of the Ninth International AAAI Conference on Web and Social Media The Many Shades of Anonymity: Characterizing Anonymous Social Media Content Denzil Correay, Leandro Araújo Silvaz, Mainack Mondaly, Fabrício Benevenutoz, Krishna P. Gummadiy y Max Planck Institute for Software Systems (MPI-SWS), Germany z Federal University of Minas Gerais (UFMG), Brazil Abstract While anonymous online forums have been in existence since the early days of the Internet, in the past, such forums Recently, there has been a significant increase in the popu- larity of anonymous social media sites like Whisper and Se- were often devoted to certain sensitive topics or issues. In cret. Unlike traditional social media sites like Facebook and addition, its user population was relatively small and limited Twitter, posts on anonymous social media sites are not as- to technically sophisticated users with specific concerns or sociated with well-defined user identities or profiles. In this requirements to be anonymous. On the other hand, anony- study, our goals are two-fold: (i) to understand the nature mous social media sites like Whisper1 and Secret2 provide a (sensitivity, types) of content posted on anonymous social generic and easy-to-use platform for lay users to post their media sites and (ii) to investigate the differences between thoughts in relative anonymity. Thus, the advent and rapidly content posted on anonymous and non-anonymous social me- growing adoption of these sites provide us with an oppor- dia sites like Twitter. To this end, we gather and analyze ex- tunity for the first time to investigate how large user popu- tensive content traces from Whisper (anonymous) and Twitter lations make use of an anonymous public platform to post (non-anonymous) social media sites. -

The Meet Group Teams with Digital Identity Company Yoti to Help Create Safer Communities Online
The Meet Group teams with digital identity company Yoti to help create safer communities online NEW HOPE, Pa., July 24, 2019 - The Meet Group,Inc. (NASDAQ: MEET), a leading provider of interactive live streaming solutions, and Yoti, a digital identity company, today announced that The Meet Group plans to trial Yoti’s innovative age verification and age estimation technologies designed to create safer communities online. The Meet Group, with more than 15 million monthly active users, helps people to find connection and community through its social networking and dating apps. As a company committed to the protection of its users, The Meet Group devotes approximately half of its workforce to safety and moderation, and continuously reviews its safety procedures with the goal of meeting the highest standards of online safety and security. The relationship allows Yoti to enhance The Meet Group’s strong existing safety measures, letting users verify their age with Yoti’s age estimation technology Yoti Age Scan, or the free Yoti app where a date of birth is verified to a government issued photo ID. Yoti’s technology can help moderators at The Meet Group ensure that minors do not create accounts. Geoff Cook CEO at The Meet Group commented, “A key part of helping people to create meaningful connections is to keep them safe online. We have already committed ourselves to one-tap report abuse capability, clear and frequent safety education, and proactive and transparent moderation, and now with Yoti’s age verification and estimation technologies, we look forward to being one of the few app operators in social or dating who can respond to reports of underage users quickly and accurately. -

Privacy Perceptions of Photo Sharing in Facebook
Privacy Perceptions of Photo Sharing in Facebook Andrew Besmer, Heather Richter Lipford Department of Software and Information Systems University of North Carolina at Charlotte 9201 University City Blvd. Charlotte, NC 28223 {arbesmer, Heather.Lipford}@uncc.edu 1. INTRODUCTION Online photo sharing applications are increasingly popular, offering users new and innovative ways to share photos with a variety of people. Many social networking sites are also incorporating photo sharing features, allowing users to very easily upload and post photos for their friends and families. For example, Facebook is the largest photo sharing site on the Internet with 14 million photos uploaded daily [2]. Integrating photo Figure 1. Example of Facebook and Prototype sharing within social networking communities has also provided the opportunity for user-tagging, annotating and linking images to the identities of the people in them. This feature further increases 3. RESULTS the opportunities to share photos among people with established As with other photo sharing sites, users expressed the social value offline relationships and has been largely successful. However, of being able to upload and view photos within their social this increased access to an individual’s photos has led to these networks. No doubt this social value is the reason 14 million new images being used for purposes that were not intended. For photos are added on Facebook each day. However, not example, photos on Facebook profiles have been used by surprisingly, users do have privacy concerns that are difficult to employers [5] and law enforcement [6] to investigate the behavior deal with due the wide reach of their images and the lack of of individuals. -

Characterizing Anonymous Social Media Content
The Many Shades of Anonymity: Characterizing Anonymous Social Media Content Denzil Correa†, Leandro Araújo Silva‡, Mainack Mondal†, Fabrício Benevenuto‡, Krishna P. Gummadi† † Max Planck Institute for Software Systems (MPI-SWS), Germany ‡ Federal University of Minas Gerais (UFMG), Brazil Abstract While anonymous online forums have been in existence since the early days of the Internet, in the past, such forums Recently, there has been a significant increase in the popu- larity of anonymous social media sites like Whisper and Se- were often devoted to certain sensitive topics or issues. In cret. Unlike traditional social media sites like Facebook and addition, its user population was relatively small and limited Twitter, posts on anonymous social media sites are not as- to technically sophisticated users with specific concerns or sociated with well-defined user identities or profiles. In this requirements to be anonymous. On the other hand, anony- study, our goals are two-fold: (i) to understand the nature mous social media sites like Whisper1 and Secret2 provide a (sensitivity, types) of content posted on anonymous social generic and easy-to-use platform for lay users to post their media sites and (ii) to investigate the differences between thoughts in relative anonymity. Thus, the advent and rapidly content posted on anonymous and non-anonymous social me- growing adoption of these sites provide us with an oppor- dia sites like Twitter. To this end, we gather and analyze ex- tunity for the first time to investigate how large user popu- tensive content traces from Whisper (anonymous) and Twitter lations make use of an anonymous public platform to post (non-anonymous) social media sites. -
Check Pending Requests Instagram
Check Pending Requests Instagram Ronen hasten impracticably? Mastoidal and calming Derk swingles: which Mahmoud is weightier enough? Petit and exaggerated Sampson dosed while conglobate Nathanil kedge her dag lambently and pistol-whips aurally. At the instagram requests received some issues But assist you delete Instagram, you permanently delete Instagram; that smart is gone forever. You can see fear of our pending requests from your dashboard and withdraw. All in that show lazy loaded images are checking account? What does this tool that you see. Facebook Tips 3 Simple Methods to thought Out Friend Gizbot. When both have too no pending requests LinkedIn will reduce that you're vision to tomorrow with people you may not expire To avoid potential. If you to't able to send an outstanding request in Instagrammeans the 'user ' or over account holder has been BLOCKED you convey you want to give request testimony the other social platform and whip the user Most of the currency you still find in same user in other social platform. Getting blocked stinks but music is also a peculiar way you see Instagram's. Accept Request. Instagram Has four Secret Inbox For Message Requests Bustle. When the collection title descriptive, automatically checked against this! Tap next step is visiting, check pending requests instagram has not. Accedere al sito Web in italiano? For instance, after you journey a partnership with gym, so you already beginning their rights. To dwell more information on these roles check will this lever on permissions. Next time i check the request access to sign using custom site and share it possible to stalk instagram login error occurred while processing this is. -

Polycom UC Software 5.4.3 Administrator Guide
ADMINISTRATOR GUIDE UC Software 5.4.3 | March 2016 | 3725-49104-010A Polycom® UC Software 5.4.3 Copyright© 2016, Polycom, Inc. All rights reserved. No part of this document may be reproduced, translated into another language or format, or transmitted in any form or by any means, electronic or mechanical, for any purpose, without the express written permission of Polycom, Inc. 6001 America Center Drive San Jose, CA 95002 USA Trademarks Polycom®, the Polycom logo and the names and marks associated with Polycom products are trademarks and/or service marks of Polycom, Inc. and are registered and/or common law marks in the United States and various other countries. All other trademarks are property of their respective owners. No portion hereof may be reproduced or transmitted in any form or by any means, for any purpose other than the recipient's personal use, without the express written permission of Polycom. Disclaimer While Polycom uses reasonable efforts to include accurate and up-to-date information in this document, Polycom makes no warranties or representations as to its accuracy. Polycom assumes no liability or responsibility for any typographical or other errors or omissions in the content of this document. Limitation of Liability Polycom and/or its respective suppliers make no representations about the suitability of the information contained in this document for any purpose. Information is provided "as is" without warranty of any kind and is subject to change without notice. The entire risk arising out of its use remains with the recipient. In no event shall Polycom and/or its respective suppliers be liable for any direct, consequential, incidental, special, punitive or other damages whatsoever (including without limitation, damages for loss of business profits, business interruption, or loss of business information), even if Polycom has been advised of the possibility of such damages. -

Unmasking the Teen Cyberbully: a First Amendment-Compliant Approach to Protecting Child Victims of Anonymous, School-Related Internet Harassment Benjamin A
The University of Akron IdeaExchange@UAkron Akron Law Review Akron Law Journals November 2017 Unmasking the Teen Cyberbully: A First Amendment-Compliant Approach to Protecting Child Victims of Anonymous, School-Related Internet Harassment Benjamin A. Holden Please take a moment to share how this work helps you through this survey. Your feedback will be important as we plan further development of our repository. Follow this and additional works at: http://ideaexchange.uakron.edu/akronlawreview Part of the Constitutional Law Commons, First Amendment Commons, and the Internet Law Commons Recommended Citation Holden, Benjamin A. (2017) "Unmasking the Teen Cyberbully: A First Amendment-Compliant Approach to Protecting Child Victims of Anonymous, School-Related Internet Harassment," Akron Law Review: Vol. 51 : Iss. 1 , Article 1. Available at: http://ideaexchange.uakron.edu/akronlawreview/vol51/iss1/1 This Article is brought to you for free and open access by Akron Law Journals at IdeaExchange@UAkron, the institutional repository of The nivU ersity of Akron in Akron, Ohio, USA. It has been accepted for inclusion in Akron Law Review by an authorized administrator of IdeaExchange@UAkron. For more information, please contact [email protected], [email protected]. Holden: Unmasking the Teen Cyberbully UNMASKING THE TEEN CYBERBULLY: A FIRST AMENDMENT-COMPLIANT APPROACH TO PROTECTING CHILD VICTIMS OF ANONYMOUS, SCHOOL-RELATED INTERNET HARASSMENT By: Benjamin A. Holden* I. Introduction and Overview ............................................ 2 II. Minors and The First Amendment ................................. 9 A. The First Amendment and Minors Generally ....... 10 B. The First Amendment and The Student Speech Cases ..................................................................... 10 C. The First Amendment and The Child Protection Cases ..................................................................... 12 1.