3 Local Area Networks
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Life Cycle of Municipal Wi-Fi
A Service of Leibniz-Informationszentrum econstor Wirtschaft Leibniz Information Centre Make Your Publications Visible. zbw for Economics Tseng, Chien-Kai; Huang, Kuang-Chiu Conference Paper Life Cycle of Municipal Wi-Fi 14th Asia-Pacific Regional Conference of the International Telecommunications Society (ITS): "Mapping ICT into Transformation for the Next Information Society", Kyoto, Japan, 24th-27th June, 2017 Provided in Cooperation with: International Telecommunications Society (ITS) Suggested Citation: Tseng, Chien-Kai; Huang, Kuang-Chiu (2017) : Life Cycle of Municipal Wi- Fi, 14th Asia-Pacific Regional Conference of the International Telecommunications Society (ITS): "Mapping ICT into Transformation for the Next Information Society", Kyoto, Japan, 24th-27th June, 2017, International Telecommunications Society (ITS), Calgary This Version is available at: http://hdl.handle.net/10419/168493 Standard-Nutzungsbedingungen: Terms of use: Die Dokumente auf EconStor dürfen zu eigenen wissenschaftlichen Documents in EconStor may be saved and copied for your Zwecken und zum Privatgebrauch gespeichert und kopiert werden. personal and scholarly purposes. Sie dürfen die Dokumente nicht für öffentliche oder kommerzielle You are not to copy documents for public or commercial Zwecke vervielfältigen, öffentlich ausstellen, öffentlich zugänglich purposes, to exhibit the documents publicly, to make them machen, vertreiben oder anderweitig nutzen. publicly available on the internet, or to distribute or otherwise use the documents in public. Sofern die Verfasser die Dokumente unter Open-Content-Lizenzen (insbesondere CC-Lizenzen) zur Verfügung gestellt haben sollten, If the documents have been made available under an Open gelten abweichend von diesen Nutzungsbedingungen die in der dort Content Licence (especially Creative Commons Licences), you genannten Lizenz gewährten Nutzungsrechte. may exercise further usage rights as specified in the indicated licence. -

Lab Report: 2.1.3 Connect to an Ethernet Network
Lab Report: 2.1.3 Connect to an Ethernet Network Performance Your Score: 0 of 2 (0%) Elapsed Time: 9 seconds Task Summary Actions you were required to perform: In In Office 1, connect the twisted pair cable between the workstation and the wall plate In In Office 1, confirm that the workstation has a connection to the local network and the Internet Explanation To complete this lab, use twisted pair cable with RJ45 connectors to connect to a wired Ethernet network. RJ45 connectors have eight wires (as seen below) and are larger than RJ11 connectors. Complete the following steps: 1. Under Office 1, select Hardware to go to the workstation. 2. Above the computer, select Back to switch to the back view of the computer. 3. On the Shelf, expand the Cables category. 4. Select the RJ45 cable. 5. In the Selected Component window, drag and drop the connector to the Ethernet port on the computer. 6. In the Selected Component window, drag the other connector to the Ethernet port on the wall outlet. 7. Select Click to view Windows 10 on the monitor to confirm that the workstation has a connection to the local network and the internet. 8. In the notification area, right-click the Network icon and select Open Network and Sharing Center. The diagram should indicate an active connection to the network and the internet. Lab Report: 2.2.3 Connect a Cable Modem Performance Your Score: 0 of 4 (0%) Elapsed Time: 6 seconds Task Summary Actions you were required to perform: In Connect the cable modem to the Internet using the RG-6 cable In Connect the computer to the cable modem using the Ethernet cable In Plug in the cable modem In Confirm that the computer is properly connected to the Internet Explanation In this lab, your task is to complete the following: Connect the components to make the internet connection. -

High-Speed Internet Connection Guide Welcome
High-Speed Internet Connection Guide Welcome Welcome to Suddenlink High-Speed Internet Thank you for choosing Suddenlink as your source for quality home entertainment and communications! There is so much to enjoy with Suddenlink High-Speed Internet including: + Easy self-installation + WiFi@Home availability + Easy access to your Email + Free access to Watch ESPN This user guide will help you get up and running in an instant. If you have any other questions about your service please visit help.suddenlink.com or contact our 24/7 technical support. Don’t forget to register online for a Suddenlink account at suddenlink.net for great features and access to email, billing statements, Suddenlink2GO® and more! 1 Table of Contents Connecting Your High Speed Internet Connecting Your High-Speed Internet Your Suddenlink Self-Install Kit includes Suddenlink Self-Install Kit ..................................................................................... 3 Connecting your computer to a Suddenlink modem ....................................... 4 the following items: Connecting a wireless router or traditional router to Suddenlink ................. 5 Getting Started Microsoft Windows XP or Higher ......................................................................... 6 Cable Modem Power Adapter Mac OS X ................................................................................................................. 6 Register Your Account Online ................................................................................7 Suddenlink WiFi@Home -

Analysis of Wifi and Wimax and Wireless Network Coexistence
International Journal of Computer Networks & Communications (IJCNC) Vol.6, No.6, November 2014 ANALYSIS OF WIFI AND WIMAX AND WIRELESS NETWORK COEXISTENCE Shuang Song and Biju Issac School of Computing, Teesside University, Middlesbrough, UK ABSTRACT Wireless networks are very popular nowadays. Wireless Local Area Network (WLAN) that uses the IEEE 802.11 standard and WiMAX (Worldwide Interoperability for Microwave Access) that uses the IEEE 802.16 standard are networks that we want to explore. WiMAX has been developed over 10 years, but it is still unknown to most people. However compared to WLAN, it has many advantages in transmission speed and coverage area. This paper will introduce these two technologies and make comparisons between WiMAX and WiFi. In addition, wireless network coexistence of WLAN and WiMAX will be explored through simulation. Lastly we want to discuss the future of WiMAX in relation to WiFi. KEY WORDS WiMAX, WiFi, wireless network, wireless coexistence, network simulation 1. INTRODUCTION With the development of multimedia communication, people need wireless broadband access with higher speed, larger coverage and mobility. The emergence of WiMAX (Worldwide Interoperability for Microwave Access) technology met the people's demand for wireless Internet to some extent. If wireless LAN technology (WLAN) solves the access problem of the "last one hundred meters", then WiMAX technology is the best access solution of the "last mile". Though WiMAX is an emerging and extremely competitive wireless broadband access technology, the development prospects of its market is still unknown. Hybrid networks as a supplement to cell based or IP packet based services, can fully reflect the characteristics of wide network coverage. -

The Future of Personal Area Networks in a Ubiquitous Computing World
Copyright is owned by the Author of the thesis. Permission is given for a copy to be downloaded by an individual for the purpose of research and private study only. The thesis may not be reproduced elsewhere without the permission of the Author. The Future of Personal Area Networks in a Ubiquitous Computing World A thesis presented in partial fulfillment of the requirements for the degree of Master of Information Sciences in Information Systems at Massey University, Auckland New Zealand Fei Zhao 2008 ABSTRACT In the future world of ubiquitous computing, wireless devices will be everywhere. Personal area networks (PANs), networks that facilitate communications between devices within a short range, will be used to send and receive data and commands that fulfill an individual’s needs. This research determines the future prospects of PANs by examining success criteria, application areas and barriers/challenges. An initial set of issues in each of these three areas is identified from the literature. The Delphi Method is used to determine what experts believe what are the most important success criteria, application areas and barriers/challenges. Critical success factors that will determine the future of personal area networks include reliability of connections, interoperability, and usability. Key application areas include monitoring, healthcare, and smart things. Important barriers and challenges facing the deployment of PAN are security, interference and coexistence, and regulation and standards. i ACKNOWLEDGEMENTS Firstly, I would like to take this opportunity to express my sincere gratitude to my supervisor – Associate Professor Dennis Viehland, for all his support and guidance during this research. Without his advice and knowledge, I would not have completed this research. -

Performance of Light Fidelity and Wireless Fidelity Networks in a WLAN
DOI : https://dx.doi.org/10.26808/rs.re.v4i1.02 International Journal of Research in Engineering & Science ISSN:(P) 2572-4274 (O) 2572-4304 Available online on http://rspublication.com/IJRES/IJRE.html volume 4 Issue 1 Jan.-Feb 2020 Performance of Light Fidelity and Wireless Fidelity Networks in a WLAN S.N. Arinze, G.N. Onoh and D.O. Abonyi Abstract Wireless Fidelity utilizes radio waves. Radio waves have limited bandwidth, fully exploited, and low speed. Light fidelity is a visible light communication used as a medium to carry high-speed data. It can complement the wireless fidelity in accessing the internet, thereby reducing congestion. In this work, a hybrid of light fidelity and wireless fidelity was carried out in an indoor environment. The geometry of the light fidelity access point and wireless fidelity access point was analyzed in the MatLab environment to know the highest power received by the user. Some ranges of received power considered for good reception wereassigned for each of the wireless access points in the MatLab program. Visual Basic, an object-oriented computer programming language, reads the signal coming from the communication port of light fidelity and wireless fidelity. It mimics the analyzed MatLab program of a hybrid network of light fidelity and wireless fidelity and connects to any of the wireless access points based on the set conditions of the satisfied received power. With these, the light fidelity can complement the limited available radio frequency. Index Terms—Light Fidelity, MatLab, Visual Basic, Wireless Fidelity. I. INTRODUCTION Wireless Fidelity network allows more than one device to communicate and share information within defined regions like office, home, and campus. -

White Paper How to Remotely Access Ethernet I/O Over the Internet
White Paper How to Remotely Access Ethernet I/O Over the Internet ACROMAG INCORPORATED Tel: (248) 295-0880 30765 South Wixom Road Fax: (248) 624-9234 P.O. BOX 437 Wixom, MI 48393-7037 U.S.A. Copyright 2009, Acromag, Inc., Printed in the USA. Data and specifications are subject to change without notice. 8400-517 How to Remotely Access Ethernet I/O Over Internet This white paper details the steps needed to access your I/O module remotely over the internet. This can be done with Ethernet-enabled I/O modules that have the capability to display built-in webpage-based output monitoring. In other words, if your I/O module can serve a webpage over Ethernet, and the network it is connected to has internet access, then you can set it up to view your I/O from any internet connection around the world. Getting Started This white paper makes a few assumptions to simplify the steps needed to connect an Ethernet-enabled I/O module to the internet: You are connecting your I/O module to your company’s existing LAN network, which has access to the internet. Your company’s server or router, also connected to the network and internet, with either static or dynamic IP address assigned by the Internet Service Provider The Layers between Your I/O and the Internet To make an Ethernet-enabled module accessible from the internet, a rudimentary understanding is required of basic network architecture. A basic understanding of the structure of the internet is also very helpful. HTTP communicates over public IP Communicates over private IP addresses through port 80 by default addresses (10.x.x.x, 192.168.x.x, or port 443 for secure HTTPS 172.16.x.x-172.32.x.x) User Browser Internet Server Corporate Ethernet Network I/O or Module Router Firewall *firewall may be software installed on the router or a separate hardware Software Hardware Figure 1: The path from the module to the user 1 The Internet The internet is essentially a group of servers all connected together in a mesh configuration, each serving files, usually in HTML format, to the network. -

Use Case Possibilities with Bluetooth Low Energy in Iot Applications White Paper
Use case possibilities with Bluetooth low energy in IoT applications White paper Author Mats Andersson Senior Director Technology, Product Center Short Range Radio, u-blox Abstract With yearly shipments of more than 10 billion microcontrollers that all can exchange information locally or through the Internet, a huge variety of so called “intelligent devices” are enabled. All these devices can be accessed over the Internet and this evolution is commonly referred to as Internet of Things (IoT). IoT typically requires a local low power wireless connection along with the Internet connection. For most such applications and solutions, a gateway is required to connect sensor nodes to the Internet via a local infrastructure or using a cellular connection. Gateways are important components of the IoT vision. These gateways can be used to connect Bluetooth low energy devices to the Internet and can also be used as "repeaters" to extend the system range. This whitepaper describes how Bluetooth low energy technology works and how it can be used to connect devices to Internet-based services and applications. A significant feature in Bluetooth low energy compared to other IoT wireless technologies is the support for smartphones and tablets. The whitepaper thus also describes how a smartphone or tablet can be used in IoT. www.u-blox.com UBX-14054580 - R01 Use case possibilities with Bluetooth low energy in IoT applications - White paper Contents Contents ............................................................................................................................. -

Online Web Server Management System Using Li-Fi Technology Ben Daryl Christian, V.Prabhakaran, S.Pavithra
International Journal of Scientific & Engineering Research, Volume 5, Issue 10, October-2014 862 ISSN 2229-5518 Online Web Server Management System Using Li-Fi Technology Ben Daryl Christian, V.Prabhakaran, S.Pavithra Abstract— This paper focuses on using Li-fi technology in an online web server management system using Visible Light Communication system which is based on using of LED lights, their ability to behave at multiple degrees of freedom helps them operate in different ways by using multiple hopping technology. We are proposing an idea to use Li-Fi technology for the purpose of sending in more data at greater bandwidth using a server, processor and GPS/GSM device. The idea is that we use Li-Fi which enables in sending data at a greater speed from a user module to the destination work module, we use two modules where the lifi is connected to computer systems connected to a server and a GPS/GSM network. The focus of our work is to know how by using lifi, information can be sent and received by multi-hop wireless networks and that easy communication occurs between the user module and the work module. Index Terms— Li-Fi, Visible Light Communication, GPS/GSM, LED. —————————— —————————— 1 INTRODUCTION uring this modern times of wireless technology which is To make up for the Wi-Fi disadvantages a new system is used D been used commonly for the transfer of data from one called Light-based wireless communication, coined as Li-Fi. It place to another place is one of the most important day to is a method of internet connectivity which doesn’t use cables day activities, number of devices accessing the internet is be- or radio waves, instead flickering light from a special LED to coming greater every time. -

Wilink8 Use Case Guide
www.ti.com Table of Contents Technical White Paper WiLinkTM8 Use Case Guide Sudharshan K Nagarathnam ABSTRACT With the growing trends in IoT, wireless connectivity is becoming increasingly important for a multitude of applications including but not limited to industrial, medical, building automation and automotive sectors. There are several connectivity options available including IEEE 802.11 WLAN/Wi-Fi® and Bluetooth®/Bluetooth low energy. Due to interoperability of Wi-Fi devices with internet infrastructure and native internet protocol support, Wi-Fi is replacing the other connectivity options in many applications. With a very active technology development ecosystem Wi-Fi is evolving to meet emerging challenges like data security, power management, data throughput and range. These generic requirements along with Wi-Fi specific features make the technology an attractive option for system designers and infrastructure developers. With the cost of Wi-Fi devices becoming more affordable, Wi-Fi is becoming the choice connectivity technology in many applications. Texas Instruments WiLink8™ family of devices, offer a wide range of solutions that support industry leading features that are required in IoT and related applications to meet the end equipment design needs in the IEEE 802.11 a/b/g/n segment. With the integration of Bluetooth/Bluetooth low energy and Wi-Fi into a single SoC, WiLink™8 devices offer a wide range of choices for end equipment realization and universal connectivity. With a proven track record and feature rich offering, WiLink8 devices are a good choice for certain segments that count on long term component availability to support products that will be manufactured for many years. -
Leveraging Physical Locality to Integrate Smart Appliances in Non-Residential Buildings with Ultrasound and Bluetooth Low Energy
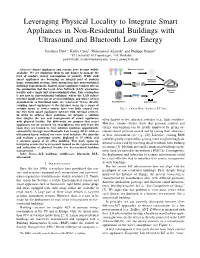
Leveraging Physical Locality to Integrate Smart Appliances in Non-Residential Buildings with Ultrasound and Bluetooth Low Energy Jonathan Furst¨ ∗, Kaifei Cheny, Mohammed Aljarrah∗ and Philippe Bonnet∗ ∗IT University of Copenhagen, yUC Berkeley [email protected], [email protected], fmoal, [email protected] Abstract—Smart appliances and sensors have become widely Manufactor Potocols available. We are deploying them in our homes to manage the level of comfort, energy consumption or security. While such smart appliances are becoming an integral part of modern Manufactor home automation systems, their integration into non-residential Gateways buildings is problematic. Indeed, smart appliance vendors rely on the assumption that the Local Area Network (LAN) guarantees Manufactor locality and a single unit of use/administration. This assumption Clouds is not met in non-residential buildings, where the LAN infras- tructure might cover one or several buildings, and where several organizations or functional units are co-located. Worse, directly Smart Appliances Manufactor Apps coupling smart appliances to the Internet opens up a range of security issues as device owners have very little control over Fig. 1. Current Home Appliance IoT State the way their smart appliances interact with external services. In order to address these problems, we propose a solution that couples the use and management of smart appliances often limited to few, physical switches (e.g., light switches). with physical locality. Put differently, we propose that smart appliances can be accessed via smartphones, but only from the However, various studies show that personal comfort and room they are located in. Our solution combines opportunistic energy consumption can be greatly improved by giving oc- connectivity through local Bluetooth Low Energy (BLE) with an cupants direct personal control and by raising their awareness ultrasound-based method for room level isolation. -

Components and Means of Communication Within the Local Area Network: an Analytical Study
74 IJCSNS International Journal of Computer Science and Network Security, VOL.18 No.3, March 2018 Components and means of communication within the Local Area Network: An analytical study Yaser Mohammed Mohammed Al Sawy Assistant Professor of Library and Information Technology Advisor to the Deanship of Scientific Research for Publishing, Quality and Academic Accreditation Director of Quality Assurance and Accreditation Unit-DSR Northern Border University – Kingdom of Saudi Arabia Abstract into: The Local Area Network (LAN) is one of the most important Peer-to-peer networks. types of information networks in providing communication - Client and server networks. within a limited community such as universities and institutions. The followed structure that is divided into: The LAN consists of an interconnected group of computers and other communication devices, which are connected to each other - Physical structural networks. through an integrated engineering system. They are distributed - Point-to-point structural networks. within relatively small geographical areas and characterized by - Star Structure Networks. high speed and lack of errors in communication. Thus, the local - Ring structure networks. area networks are a mixture of interrelated devices, equipment - Complete structure networks. and institutions, where they form a fabric called networks, these - Hybrid Structure Networks. networks mainly rely on essential physical components and software to operate efficiently. The present analytical study seeks This study tackled the main concepts, terminology, basic to understand both the basic components of the operation of local components, software and means of communication networks and to recognize and define the role of each of the within the LAN, which nowadays has become the main means of communication adopted within the local network in focus for obtaining information and making it available to order to construct and operate the LAN.