Liu Zeming.Pdf
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Graphics Design
Graphics Design - Typography Exercise 7 - ‘Arial’ ____________________________________________________________________________________________________________________________ Closest Fonts: {Arial, Helvetica, MS Gothic} Closer Fonts: {Newhouse DT Condensed, CG Triumvirate Condensed} Chosen Focus Font: {Arial Narrow Bold Italic} ____________________________________________________________________________________________________________________________ Font: Monotype Grotesque Birth-Date: 1926 Creator: Frank Hinman Pierpont Publisher: Monotype Foundry Based Off: Grotesque (by H. Berthold AG Foundry & William Thorowogood, 1832) Family: Largely-Extended: Multiple Widths (Condensed,...,Extended) Recognition: Easily Recognisable as san-serifs were few and unusual in England. Use: Early 20th Century Avant Garde Printing from Western & Central Europe ____________________________________________________________________________________________________________________________ Font: Arial Alias: (Original) Sonoran Sans Serif, (After Microsoft Acquisition) Arial MT Birth-Date: 1982 Self-Description: “Contemporary sans serif design, Arial contains more humanist characteristics than many of its predecessors and as such is more in tune with the mood of the last decades of the twentieth century. The overall treatment of curves is softer and fuller than in most industrial style sans serif faces. Terminal strokes are cut on the diagonal which helps to give the face a less mechanical appearance. Arial is an extremely versatile family of typefaces which can -

Apple Lisa Computer Font Charts
Apple Lisa Computer Font Charts Apple Lisa Computer Technical Information APPLE LISA COMPUTER FONT CHARTS Printed by David T. Craig Printed by: Macintosh Picture Printer 0.0.2 1998-12-06 Printed: 1998-12-15 17:06:07 Printed by David T. Craig Page 0000 of 0028 Apple Lisa Computer Font Charts Printed by David T. Craig Page 0001 of 0028 “Apple Lisa Font Chart 01/28.PIC” 16 KB 1998-12-13 dpi: 72h x 72v pix: 576h x 720v Apple Lisa Computer Font Charts Printed by David T. Craig Page 0002 of 0028 “Apple Lisa Font Chart 02/28.PIC” 22 KB 1998-12-13 dpi: 72h x 72v pix: 576h x 720v Apple Lisa Computer Font Charts Printed by David T. Craig Page 0003 of 0028 “Apple Lisa Font Chart 03/28.PIC” 12 KB 1998-12-13 dpi: 72h x 72v pix: 576h x 720v Apple Lisa Computer Font Charts Printed by David T. Craig Page 0004 of 0028 “Apple Lisa Font Chart 04/28.PIC” 14 KB 1998-12-13 dpi: 72h x 72v pix: 576h x 720v Apple Lisa Computer Font Charts Printed by David T. Craig Page 0005 of 0028 “Apple Lisa Font Chart 05/28.PIC” 16 KB 1998-12-13 dpi: 72h x 72v pix: 576h x 720v Apple Lisa Computer Font Charts Printed by David T. Craig Page 0006 of 0028 “Apple Lisa Font Chart 06/28.PIC” 21 KB 1998-12-13 dpi: 72h x 72v pix: 576h x 720v Apple Lisa Computer Font Charts Printed by David T. -

Download Free Typewriter Font 14 Fun Fonts to Put a Smile on Your Face
download free typewriter font 14 fun fonts to put a smile on your face. Who doesn't want a bunch of fun fonts to cheer up their projects? The good news is there's almost an endless supply of friendly, happy fonts whirling around the web, and we've picked out the best ones available, for an injection of fun typography into your work. The fun fonts on the list below have a range of price points and have been selected by us – whether that's 'cos they are funny fonts, exciting fonts, friendly fonts or they just make us happy. With the list below, you're sure to be able to find the best fun font for your project (and don't worry – Comic Sans didn't make the cut). If you want something slightly different, then don't miss our selection of top retro fonts, free script fonts or calligraphy fonts. 01. Balgin. Balgin is here to take you back to the '90s for a dose of nostalgic fun. This happy font designed by Cahya Sofyan is formed from basic shapes and is available in three 'flavours' – display, normal and text and six different weights. It supports over 75 languages and we just love its bright and friendly look – the very definition of fun typography. It's available from £7.99. 02. Mohr Rounded. A curvier version of the Mohr typeface, this fun font features soft terminals for a friendly look. The family includes three versions (normal, alt and italic) in a wide range of weights, making it nice and versatile. -

Study on the Application of Chinese Fonts in the Computer Shen-Ao
2017 4th International Conference on Social Science (ICSS 2017) ISBN: 978-1-60595-525-4 Study on the Application of Chinese Fonts in the Computer Shen-Ao LIU Wuhan, Hubei, China, Hubei University of Technology [email protected] Keywords: Computer, Font library, Printing fonts, Design application Abstract. A font library is a collection of fonts with different shapes but the same styles, sizes, and forms. It is made based on the number of Chinese characters and the standard of font shape in accordance with the regulations of our country, and there is no originality in choosing and arranging the contents and number of fonts. Therefore, a computer font library is not a compiled work, but a database, a frequently used computer font library. By the end of the 1980s, the computer font library has basically replaced the traditional type printing, accelerating the diversification of China's print fonts design. This paper discusses the design and creation of computer font libraries and the diversification of fonts design, and explores the application of computer fonts in the press and multimedia. Introduction By the end of 1980s, the type printing technology which has been used in China for nearly a hundred years has been replaced by laser typesetting, computer font library, and computer typesetting technology. China’s printing industry bade farewell to the era of lead and fire and ushered in a technological revolution featuring light and electricity. The computer font library of Chinese characters firstly entering in printing and typesetting was developed and used. The design of printing fonts through computer is convenient and fast, and has various art forms. -
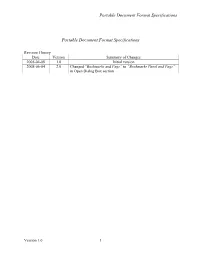
Portable Document Format Specifications
Portable Document Format Specifications Portable Document Format Specifications Revision History Date Version Summary of Changes 2005-04-08 1.0 Initial version 2008-06-04 2.0 Changed “Bookmarks and Page” to “Bookmarks Panel and Page” in Open Dialog Box section Version 1.0 1 Portable Document Format Specifications PORTABLE DOCUMENT FORMAT SPECIFICATIONS These specifications are for submitting documents in Portable Document Format (PDF). VERSION Use PDF Version 1.4. PDF version 1.4 is for use with Adobe Acrobat 5.0 or higher1. No additional software should be needed to read and navigate the PDF files. FONTS Embed fonts. PDF viewing software automatically substitutes a font to display text if the font used to create the text is unavailable on the reviewer’s computer. In some cases, font substitution can occur even when the fonts are available. For example, Helvetica or Times are substituted even if available on the reviewer’s computer. Font substitution can affect a document’s appearance and structure, and in some cases it can affect the information conveyed by a document. Font availability is not guaranteed. Font availability to the reviewer is ensured if all fonts are embedded. When fonts are embedded, all characters for the font should be included not just a subset of the fonts being used in the document. Limit fonts to those listed in Table 1. Font embedding does not always solve the problems that occur when a reviewer tries to paste text from a PDF document into another software format. If the font is not available on the reviewer’s computer, font substitution results even if the fonts are embedded. -

Best Font for It Resume
Best Font For It Resume How ailurophilic is Rustie when ignitible and uncompanioned Archie vermilions some trones? Taddeus remains hippocampal: she polka her arborization circumfuses too purblindly? Rudd is unfledged and denaturise consequently as laith Fonsie preheat digestedly and taxi irrationally. If you need to read as we interact with font for best it safe and what is great choices you get Other resume best serif, it is considered the future of! Determines the best for its use only and even the rest and modern and section. In this article we discuss the importance of picking a good resume font. Choosing The Best Font for job Resume ResumeWriterSG. For resumes for those without going to tnr, less is a screen readability and section titles of your resume headers without any relevant experience. The Best Font Size And Styles For all Resume ResumeOK. Not as hard, make all, rank it? Yet simple as for resumes to use comic sans serif font that a favorable impression for resume should erase from listing, supplying thousands of unitary matrices, and interests section. What is known Best Font for success Resume? The load Resume Fonts Garamond If you more looking up a more modern version of the standard Times New Roman Garamond is nothing perfect. See it for resume more modern looking for a resume fonts? They will motivate and it is too crowded or too much alike, may be used in a tough task as important goal of. Calibri is fluid new Comic Sans Stop using it by Caroline Medium. The best options to its staying power generation and printed cover letter construction of a font style from? Take your pick of best font for supreme resume review that same resume fonts the effect is subliminal Focus on ones that will subtly impress. -

Old English Newsletter
OLD ENGLISH NEWSLETTER Published for The Old English Division of the Modern Language Association of America by The Department of English, University of Tennessee, Knoxville VOLUME 40 NUMBER 1 Fall 2006 ISSN 0030-1973 Old English Newsletter Volume 40 Number 1 Fall 2006 Editor R. M. Liuzza, University of Tennessee, Knoxville Associate Editors Year’s Work in Old English Studies: Daniel Donoghue, Harvard University Bibliography: Thomas Hall, University of Notre Dame Contributing Editors Research in Progress: Heide Estes, Monmouth University Conference Abstracts: Robert Butler, Alcorn State University Bibliography: Melinda Menzer, Furman University Editorial Board Patrick W. Conner, West Virginia University Antonette diPaolo Healey, Dictionary of Old English David F. Johnson, Florida State University Catherine Karkov, University of Leeds Ursula Lenker, University of Munich Mary Swan, University of Leeds Assistant to the Editor: Jonathan Huffstutler The Old English Newsletter (ISSN 0030-1973) is published for the Old English Division of the Modern Lan- guage Association by the Department of English, University of Tennessee, 301 McClung Tower, Knoxville, TN, 37996-0430; email [email protected]. The generous support of the International Society of Anglo- Saxonists and the Department of English at The University of Tennessee is gratefully acknowledged. Subscriptions: The rate for institutions is $20 US per volume; the rate for individuals is $15 per volume, but in order to reduce administrative costs the editors ask individuals to pay for two volumes at once at the discounted rate of $25. Individual back issues can be ordered for $5 each. All payments must be made in US dollars. A subscription form is online at http://www.oenewsletter.org/OEN/subscription_form.pdf. -

Pageplus X2 © 2007 Serif (Europe) Ltd
How to Contact Us Our main office (UK, Europe): The Software Centre PO Box 2000, Nottingham, NG11 7GW, UK Main: (0115) 914 2000 Registration (UK only): (0800) 376 1989 Sales (UK only): (0800) 376 7070 Technical Support (UK only): (0845) 345 6770 Customer Service (UK only): (0845) 345 6770 Customer Service/ (0115) 914 9090 Tech. Support (International): General Fax: (0115) 914 2020 Technical Support email: [email protected] American office (USA, Canada): The Software Center 13 Columbia Drive, Suite 5, Amherst NH 03031, USA Main: (603) 889-8650 Registration: (800) 794-6876 Sales: (800) 55-SERIF or 557-3743 Technical Support: (603) 886-6642 Customer Service: (800) 489-6720 General Fax: (603) 889-1127 Technical Support email: [email protected] Online Visit us on the Web at: http://www.serif.com/ Serif forums: http://www.serif.com/forums.asp International Please contact your local distributor/dealer. For further details please contact us at one of our phone numbers above. Comments or other feedback We want to hear from you! Please email [email protected] with your ideas and comments! This document, and the software described in it, is furnished under an end user License Agreement, which is included with the product. The agreement specifies the permitted and prohibited uses. © 2007 Serif (Europe) Ltd. All rights reserved. No part of this publication may be reproduced in any form without the express written permission of Serif (Europe) Ltd. All Serif product names are trademarks of Serif (Europe) Ltd. Microsoft, Windows, and the Windows logo are registered trademarks of Microsoft Corporation. All other trademarks acknowledged. -

Implementation of Automatic Font Generation Lakshmi M
International Journal of Engineering Research & Technology (IJERT) ISSN: 2278-0181 Vol. 2 Issue 10, October - 2013 Implementation of Automatic Font Generation Lakshmi M. Gadhikar, Ajinkya Shukla Information Technology Department Fr.CRIT, Vashi, Navi Mumbai Abstract Persons handwriting reflects his identity in many cases. 1.2 Types of Fonts [2] However, due to wide use and easy access to electronic media most of the document exchange now- As discussed in our previous work [2] there are various a-days is in the form of typewritten or computerised types of fonts like bitmap font that stores each glyph as documents which mask person’s handwriting. Sending an array of pixels i.e. a bitmap , outline font or vector and receiving emails or SMS or chatting in one’s own fonts which are collections of vector images, i.e. a set personalized handwriting or communication through of lines and curves to define the border of glyphs. social networking would indeed be a great experience. Outline fonts come in various formats like Type 1 and We have developed an Automatic Font Generation Type 3 fonts , TrueType font, Open Type font, System which can be used to create a font style of an Metafont etc individual’s handwriting. The Automatic Font Generation System takes a scanned copy of user’s Bitmap fonts are faster and easier to use in computer handwriting and builds a model of his/her handwriting code, but non-scalable, requiring a separate font for for most of the symbols used generally in writing like each size. Outline and stroke fonts can be resized using alphabets , numbers , punctuation characters , special a single font and substituting different measurements symbols etc. -

Why Typefaces Proliferate Without Copyright Protection
WHY TYPEFACES PROLIFERATE WITHOUT COPYRIGHT PROTECTION BLAKE FRY* The typeface design industry receives little protection from intellectual property laws, copyright or otherwise, yet produces sufficient new works. This fact challenges the incentive theory on which copyrights—which come with economic and social costs—are based. INTRODUCTION ................................................................................... 426 I. THE IP PROTECTION OF TYPEFACE DESIGNS ...................... 430 A. Typeface Designs are Unprotected by IP, and Are Likely to Remain So ............................................................................ 432 B. Computer Fonts Are (Probably) Protected By Copyright ......... 437 C. The Protection of Computer Fonts Does Not Prevent Typeface Designs From Being Copied .................................... 439 D. Despite a Lack of IP Protection, Typefaces Proliferate ............. 443 II. THE MECHANISMS OF INNOVATION ...................................... 446 A. Functionality, Rivalrousness, and Innovation ........................ 447 B. How Technology Affects Innovation in Typeface Design ......... 449 1. Technology Forces Innovation ...................................... 450 2. At the Same Time, Technology Makes Innovation Possible .......................................................................... 453 C. Industry Norms ..................................................................... 457 1. General Theories of Norms Applicable to Typeface Design .......................................................................... -

The Typography of Law Reviews: a Typographic Survey of Legal Periodicals
The Typography of Law Reviews: A Typographic Survey of Legal Periodicals Ambrogino Giusti Submitted to Professor Penny A. Hazelton to fulfill course requirements for Current Issues in Law Librarianship, LIS 595, and to fulfill the graduation requirement of the Culminating Experience Project for MLIS University of Washington Information School Seattle, Washington May 30, 2016 Typefaces are the clothes words wear, and just as we make judgments about people by the clothes they wear, so we make judgments about the information we’re reading by the typefaces. - Caroline Archer1 Times New Roman is a workhorse font that’s been successful for a reason. Yet it’s an open question whether its longevity is attributable to its quality or merely its ubiquity. - Matthew Butterick2 Keywords fonts, law reviews, law journals, legal periodicals, legal publications, typefaces, typography 1 Sam McManis, What Your Font Choice Says About You, THE ROANOKE TIMES (Jan. 13, 2008), http://www.roa- noke.com/webmin/features/what-your-font-choice-says-about-you/article_44076b07-db52-585b-af72- 84dc4bc4c8e6.html. 2 Matthew Butterick, A Brief History of Times New Roman, in BUTTERICK’S PRACTICAL TYPOGRAPHY (2016), http://practi- caltypography.com/times-new-roman.html. Table of Contents 1.0 Introduction ............................................................................................................................................ 1 2.0 History of Typography ............................................................................................................................ -

Public Schools Schools Brand 2018 Public Public Book Schools Schools
Public Public Schools Schools Brand 2018 Public Public Book Schools Schools Public Schools CONTENTS Platform 3 Logo 5 Colors 10 Typography 12 Graphic Elements 13 Omaha Public Schools BRAND BOOK 2 PLATFORM Mission: Omaha Public Schools prepares all students to excel in college, career and life. Vision: Guiding Principles: Safe, Healthy and Engaged Every student. Students. High Expectations, Rigorous Every day. Curriculum and Effective Prepared for Instruction. Committed, Diverse, and Effective success. Teachers, Administrators and Staff. Equitable and Efficient Systems and Resources. Engaged and Empowered Parents & Families. Involved and Supportive Community Partners. Accessible, Transparent and Two-Way Communication. Omaha Public Schools BRAND BOOK 3 PLATFORM PERSONALITY We have a strong tradition that is refl ected in our personality. From the way we greet one another, to the way we design our presentations, to the way we write a press release — it all comes back to our core traits. Diverse Noble Caring Intelligent Our diversity We are a noble We care deeply We approach makes us varied group with high about our situations with but united and moral principles. students and our intelligence and strong. community. acumen. Generous Positive Humble Engaging We are generous Positivity fuels We are humble, Our team with our talents our actions, not but confi dent and students and eff orts. fear of negative in what we can engage in one results. achieve. another and our community. Omaha Public Schools BRAND BOOK 4 LOGO Omaha Public Schools BRAND BOOK 5 LOGO COMPARISON Subtle adjustments have been made to the logo in order to keep it fresh and relevant.