PDF File of the Two Posters
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Edsger W. Dijkstra: a Commemoration
Edsger W. Dijkstra: a Commemoration Krzysztof R. Apt1 and Tony Hoare2 (editors) 1 CWI, Amsterdam, The Netherlands and MIMUW, University of Warsaw, Poland 2 Department of Computer Science and Technology, University of Cambridge and Microsoft Research Ltd, Cambridge, UK Abstract This article is a multiauthored portrait of Edsger Wybe Dijkstra that consists of testimo- nials written by several friends, colleagues, and students of his. It provides unique insights into his personality, working style and habits, and his influence on other computer scientists, as a researcher, teacher, and mentor. Contents Preface 3 Tony Hoare 4 Donald Knuth 9 Christian Lengauer 11 K. Mani Chandy 13 Eric C.R. Hehner 15 Mark Scheevel 17 Krzysztof R. Apt 18 arXiv:2104.03392v1 [cs.GL] 7 Apr 2021 Niklaus Wirth 20 Lex Bijlsma 23 Manfred Broy 24 David Gries 26 Ted Herman 28 Alain J. Martin 29 J Strother Moore 31 Vladimir Lifschitz 33 Wim H. Hesselink 34 1 Hamilton Richards 36 Ken Calvert 38 David Naumann 40 David Turner 42 J.R. Rao 44 Jayadev Misra 47 Rajeev Joshi 50 Maarten van Emden 52 Two Tuesday Afternoon Clubs 54 2 Preface Edsger Dijkstra was perhaps the best known, and certainly the most discussed, computer scientist of the seventies and eighties. We both knew Dijkstra |though each of us in different ways| and we both were aware that his influence on computer science was not limited to his pioneering software projects and research articles. He interacted with his colleagues by way of numerous discussions, extensive letter correspondence, and hundreds of so-called EWD reports that he used to send to a select group of researchers. -

Chapter 1 Issues—The Software Crisis
Chapter 1 Issues—The Software Crisis 1. Introduction to Chapter This chapter describes some of the current issues and problems in system development that are caused The term "software crisis" has been used since the by software—software that is late, is over budget, late 1960s to describe those recurring system devel- and/or does not meet the customers' requirements or opment problems in which software development needs. problems cause the entire system to be late, over Software is the set of instructions that govern the budget, not responsive to the user and/or customer actions of a programmable machine. Software includes requirements, and difficult to use, maintain, and application programs, system software, utility soft- enhance. The late Dr. Winston Royce, in his paper ware, and firmware. Software does not include data, Current Problems [1], emphasized this situation when procedures, people, and documentation. In this tuto- he said in 1991: rial, "software" is synonymous with "computer pro- grams." The construction of new software that is both Because software is invisible, it is difficult to be pleasing to the user/buyer and without latent certain of development progress or of product com- errors is an unexpectedly hard problem. It is pleteness and quality. Software is not governed by the perhaps the most difficult problem in engi- physical laws of nature: there is no equivalent of neering today, and has been recognized as such Ohm's Law, which governs the flow of electricity in a for more than 15 years. It is often referred to as circuit; the laws of aerodynamics, which act to keep an the "software crisis". -

Software Engineering and Ethics: When Code Goes Bad
Software Engineering and Ethics: when code goes bad Once upon a time, estimates for the Strategic Defense Initiative (SDI or ``Star Wars'') claimed that there would be 30 million lines of code, all bug free. This is at least three orders of magnitude greater than ever has been achieved. ... What have we learned since then? 2017 TSP (MSc CCN) 1 Lecture Plan It is a bad plan that admits of no modification Publilius Syrus •Software Crisis •Ethics •Software Engineering •Software Engineering and Ethics •The root of the problem - computer science boundaries? •When code goes bad - education through classic examples •Proposals for the future 2017 TSP (MSc CCN) 2 Software Crisis Do you recognise this? 3 When everyone is wrong Software Engineering and “Bugs” everyone is right Nivelle de La Chaussee QUESTION: What’s the difference between hardware and software ?… buy some hardware and you get a warranty, buy some software and you get a disclaimer The software crisis: •always late Does this really exist? •always over-budget •always buggy •always hard to maintain •always better the next time round … but never is! This doesn’t seem right … where are our ethics? 2017 TSP (MSc CCN) 4 Is there really a crisis? … To avoid crisis, just hire the best people … look at the advances we have made Success in software development depends most upon the quality of the people involved. There is more software to be developed than there are capable developers to do it. Demand for engineers will continue to outstrip supply for the foreseeable future. Complacency has already set in … some firms acknowledge that many of their engineers make negative contribution. -
![Arxiv:2105.00534V1 [Cs.SE] 2 May 2021 Solutions](https://docslib.b-cdn.net/cover/5194/arxiv-2105-00534v1-cs-se-2-may-2021-solutions-905194.webp)
Arxiv:2105.00534V1 [Cs.SE] 2 May 2021 Solutions
Metadata Interpretation Driven Development J´ulioG.S.F. da Costaa,d, Reinaldo A. Pettac,d, Samuel Xavier-de-Souzaa,b,d, aGraduate Program of Electrical and Computer Engineering bDepartamento de Engenharia de Computa¸c~aoe Automa¸c~ao cDepartamento de Geologia dUniversidade Federal do Rio Grande do Norte, Natal, RN, Brazil, 59078-900 Abstract Context: Despite decades of engineering and scientific research efforts, sep- aration of concerns in software development remains not fully achieved. The ultimate goal is to truly allow code reuse without large maintenance and evo- lution costs. The challenge has been to avoid the crosscutting of concerns phe- nomenon, which has no apparent complete solution. Objective: In this paper, we show that business-domain code inscriptions play an even larger role in this challenge than the crosscutting of concerns. We then introduce a new methodology, called Metadata Interpretation Driven Develop- ment (MIDD) that suggests a possible path to realize separation of concerns by removing functional software concerns from the coding phase. Method: We propose a change in the perspective for building software, from being based on object representation at the coding level to being based on ob- ject interpretation, whose definitions are put into layers of representation other than coding. The metadata of the domain data is not implemented at the level of the code. Instead, they are interpreted at run time. Results: As an important consequence, such constructs can be applied across functional requirements, across business domains, with no concerns regarding the need to rewrite or refactor code. We show how this can increase the (re)use of the constructs. -

Sorting Algorithm 1 Sorting Algorithm
Sorting algorithm 1 Sorting algorithm In computer science, a sorting algorithm is an algorithm that puts elements of a list in a certain order. The most-used orders are numerical order and lexicographical order. Efficient sorting is important for optimizing the use of other algorithms (such as search and merge algorithms) that require sorted lists to work correctly; it is also often useful for canonicalizing data and for producing human-readable output. More formally, the output must satisfy two conditions: 1. The output is in nondecreasing order (each element is no smaller than the previous element according to the desired total order); 2. The output is a permutation, or reordering, of the input. Since the dawn of computing, the sorting problem has attracted a great deal of research, perhaps due to the complexity of solving it efficiently despite its simple, familiar statement. For example, bubble sort was analyzed as early as 1956.[1] Although many consider it a solved problem, useful new sorting algorithms are still being invented (for example, library sort was first published in 2004). Sorting algorithms are prevalent in introductory computer science classes, where the abundance of algorithms for the problem provides a gentle introduction to a variety of core algorithm concepts, such as big O notation, divide and conquer algorithms, data structures, randomized algorithms, best, worst and average case analysis, time-space tradeoffs, and lower bounds. Classification Sorting algorithms used in computer science are often classified by: • Computational complexity (worst, average and best behaviour) of element comparisons in terms of the size of the list . For typical sorting algorithms good behavior is and bad behavior is . -

Download Distributed Systems Free Ebook
DISTRIBUTED SYSTEMS DOWNLOAD FREE BOOK Maarten van Steen, Andrew S Tanenbaum | 596 pages | 01 Feb 2017 | Createspace Independent Publishing Platform | 9781543057386 | English | United States Distributed Systems - The Complete Guide The hope is that together, the system can maximize resources and information while preventing failures, as if one system fails, it won't affect the availability of the service. Banker's algorithm Dijkstra's algorithm DJP algorithm Prim's algorithm Dijkstra-Scholten algorithm Dekker's algorithm generalization Smoothsort Shunting-yard algorithm Distributed Systems marking algorithm Concurrent algorithms Distributed Systems algorithms Deadlock prevention algorithms Mutual exclusion algorithms Self-stabilizing Distributed Systems. Learn to code for free. For the first time computers would be able to send messages to other systems with a local IP address. The messages passed between machines contain forms of data that the systems want to share like databases, objects, and Distributed Systems. Also known as distributed computing and distributed databases, a distributed system is a collection of independent components located on different machines that share messages with each other in order to achieve common goals. To prevent infinite loops, running the code requires some amount of Ether. As mentioned in many places, one of which this great articleyou cannot have consistency and availability without partition tolerance. Because it works in batches jobs a problem arises where if your job fails — Distributed Systems need to restart the whole thing. While in a voting system an attacker need only add nodes to the network which is Distributed Systems, as free access to the network is a design targetin a CPU power based scheme an attacker faces a physical limitation: getting access to more and more powerful hardware. -

Edsger Wybe Dijkstra
In Memoriam Edsger Wybe Dijkstra (1930–2002) Contents 0 Early Years 2 1 Mathematical Center, Amsterdam 3 2 Eindhoven University of Technology 6 3 Burroughs Corporation 8 4 Austin and The University of Texas 9 5 Awards and Honors 12 6 Written Works 13 7 Prophet and Sage 14 8 Some Memorable Quotations 16 Edsger Wybe Dijkstra, Professor Emeritus in the Computer Sciences Department at the University of Texas at Austin, died of cancer on 6 August 2002 at his home in Nuenen, the Netherlands. Dijkstra was a towering figure whose scientific contributions permeate major domains of computer science. He was a thinker, scholar, and teacher in renaissance style: working alone or in a close-knit group on problems of long-term importance, writing down his thoughts with exquisite precision, educating students to appreciate the nature of scientific research, and publicly chastising powerful individuals and institutions when he felt scientific integrity was being compromised for economic or political ends. In the words of Professor Sir Tony Hoare, FRS, delivered by him at Dijkstra’s funeral: Edsger is widely recognized as a man who has thought deeply about many deep questions; and among the deepest questions is that of traditional moral philosophy: How is it that a person should live their life? Edsger found his answer to this question early in his life: He decided he would live as an academic scientist, conducting research into a new branch of science, the science of computing. He would lay the foundations that would establish computing as a rigorous scientific discipline; and in his research and in his teaching and in his writing, he would pursue perfection to the exclusion of all other concerns. -

Sorting Algorithm 1 Sorting Algorithm
Sorting algorithm 1 Sorting algorithm A sorting algorithm is an algorithm that puts elements of a list in a certain order. The most-used orders are numerical order and lexicographical order. Efficient sorting is important for optimizing the use of other algorithms (such as search and merge algorithms) which require input data to be in sorted lists; it is also often useful for canonicalizing data and for producing human-readable output. More formally, the output must satisfy two conditions: 1. The output is in nondecreasing order (each element is no smaller than the previous element according to the desired total order); 2. The output is a permutation (reordering) of the input. Since the dawn of computing, the sorting problem has attracted a great deal of research, perhaps due to the complexity of solving it efficiently despite its simple, familiar statement. For example, bubble sort was analyzed as early as 1956.[1] Although many consider it a solved problem, useful new sorting algorithms are still being invented (for example, library sort was first published in 2006). Sorting algorithms are prevalent in introductory computer science classes, where the abundance of algorithms for the problem provides a gentle introduction to a variety of core algorithm concepts, such as big O notation, divide and conquer algorithms, data structures, randomized algorithms, best, worst and average case analysis, time-space tradeoffs, and upper and lower bounds. Classification Sorting algorithms are often classified by: • Computational complexity (worst, average and best behavior) of element comparisons in terms of the size of the list (n). For typical serial sorting algorithms good behavior is O(n log n), with parallel sort in O(log2 n), and bad behavior is O(n2). -
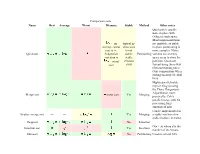
Comparison Sorts Name Best Average Worst Memory Stable Method Other Notes Quicksort Is Usually Done in Place with O(Log N) Stack Space
Comparison sorts Name Best Average Worst Memory Stable Method Other notes Quicksort is usually done in place with O(log n) stack space. Most implementations on typical in- are unstable, as stable average, worst place sort in-place partitioning is case is ; is not more complex. Naïve Quicksort Sedgewick stable; Partitioning variants use an O(n) variation is stable space array to store the worst versions partition. Quicksort case exist variant using three-way (fat) partitioning takes O(n) comparisons when sorting an array of equal keys. Highly parallelizable (up to O(log n) using the Three Hungarian's Algorithmor, more Merge sort worst case Yes Merging practically, Cole's parallel merge sort) for processing large amounts of data. Can be implemented as In-place merge sort — — Yes Merging a stable sort based on stable in-place merging. Heapsort No Selection O(n + d) where d is the Insertion sort Yes Insertion number of inversions. Introsort No Partitioning Used in several STL Comparison sorts Name Best Average Worst Memory Stable Method Other notes & Selection implementations. Stable with O(n) extra Selection sort No Selection space, for example using lists. Makes n comparisons Insertion & Timsort Yes when the data is already Merging sorted or reverse sorted. Makes n comparisons Cubesort Yes Insertion when the data is already sorted or reverse sorted. Small code size, no use Depends on gap of call stack, reasonably sequence; fast, useful where Shell sort or best known is No Insertion memory is at a premium such as embedded and older mainframe applications. Bubble sort Yes Exchanging Tiny code size. -

Unit Structure: 1.1 Software Crisis 1.2 Software Evaluation 1.3 POP (Procedure Oriented Programming) 1.4 OOP (Object Oriented
Unit Structure: 1.1 Software crisis 1.2 Software Evaluation 1.3 POP (Procedure Oriented Programming) 1.4 OOP (Object Oriented Programming) 1.5 Basic concepts of OOP 1.5.1 Objects 1.5.2 Classes 1.5.3 Data Abstraction and Data Encapsulation 1.5.4 Inheritance 1.5.5 Polymorphism 1.5.6 Dynamic Binding 1.5.7 Message Passing 1.6 Benefits of OOP 1.7 Object Oriented Language 1.8 Application of OOP 1.9 Introduction of C++ 1.9.1 Application of C++ 1.10 Simple C++ Program 1.10.1 Program Features 1.10.2 Comments 1.10.3 Output Operators 1.10.4 iostream File 1.10.5 Namespace 1.10.6 Return Type of main () 1.11 More C++ Statements 1.11.1 Variable 1.11.2 Input Operator 1.11.3 Cascading I/O Operator 1.12 Example with Class 1.13 Structure of C++ 1.14 Creating Source File 1.15 Compiling and Linking Page 1 1.1 Software Crisis Developments in software technology continue to be dynamic. New tools and techniques are announced in quick succession. This has forced the software engineers and industry to continuously look for new approaches to software design and development, and they are becoming more and more critical in view of the increasing complexity of software systems as well as the highly competitive nature of the industry. These rapid advances appear to have created a situation of crisis within the industry. The following issued need to be addressed to face the crisis: • How to represent real-life entities of problems in system design? • How to design system with open interfaces? • How to ensure reusability and extensibility of modules? • How to develop modules that are tolerant of any changes in future? • How to improve software productivity and decrease software cost? • How to improve the quality of software? • How to manage time schedules? 1.2 Software Evaluation Ernest Tello, A well known writer in the field of artificial intelligence, compared the evolution of software technology to the growth of the tree. -

Smoothsort's Behavior on Presorted Sequences by Stefan Hertel
Smoothsort's Behavior on Presorted Sequences by Stefan Hertel Fachbereich 10 Universitat des Saarlandes 6600 Saarbrlicken West Germany A 82/11 July 1982 Abstract: In [5], Mehlhorn presented an algorithm for sorting nearly sorted sequences of length n in time 0(n(1+log(F/n») where F is the number of initial inver sions. More recently, Dijkstra[3] presented a new algorithm for sorting in situ. Without giving much evidence of it, he claims that his algorithm works well on nearly sorted sequences. In this note we show that smoothsort compares unfavorably to Mehlhorn's algorithm. We present a sequence of length n with O(nlogn) inversions which forces smooth sort to use time Q(nlogn), contrasting to the time o (nloglogn) Mehlhorn's algorithm would need. - 1 O. Introduction Sorting is a task in the very heart of computer science, and efficient algorithms for it were developed early. Several of them achieve the O(nlogn) lower bound for sor ting n elements by comparison that can be found in Knuth[4]. In many applications, however, the lists to be sorted do not consist of randomly distributed elements, they are already partially sorted. Most classic O(nlogn) algorithms - most notably mergesort and heapsort (see [4]) - do not take the presortedness of their inputs into account (cmp. [2]). Therefore, in recent years, the interest in sorting focused on algorithms that exploit the degree of sortedness of the respective input. No generally accepted measure of sortedness of a list has evolved so far. Cook and Kim[2] use the minimum number of elements after the removal of which the remaining portion of the list is sorted - on this basis, they compared five well-known sorting algorithms experimentally. -

Chapter 3, on Structured Programming
131 on structured programming "In the light of all these difficul- ties the simple approach may be the best." W.F.C. Purser (1976) Software for local multi-mini proc- essor systems. In: 'Multiprocessor Systems', Info- tech State of the Art Report, pg. 408. 132 Contents Chapter Three 1. Introduction pg. 133 1. The origination of structured programming 133 2. The software crisis 135 3. Structured programming and problem solving 136 2. Survey of Structured Programming Techniques 139 1. Restrictions 139 2. Abstraction 141 3. Stepwise refinement 142 4. Notation 143 • Data representation 143 • Flowcharts 145 • Documentation 147 • Programming Languages 148 3. Discussion: Criticisms on Structured Programming 150 1. Pragmatics 150 2. Complexity 150 3. Rigidity 151 4. Methodology 155 4. Conclusion 157 , 5. References Chapter Three 158 Appendix B: Graph Generation and Complexity Measures 161 References Appendix A 167 133 CHAPTER THREE ON STRUCTURED PROGRAMMING 3.1. INTRODUCTION One conclusion we can draw from the discussion in chapter two is that correct- ness proving is by no means a trivial task, neither for sequential programs nor for concurrent programs. The available analysis tools are not powerful enough to allow for the verification of just any program. By necessity one must re- strict oneself to simple and well-structured programs. But, one may ask, what is a well-structured program? Fortunately, there is a wealth of literature on this subject. The larger part of this literature is primarily concerned with sequential programs, but still we should take careful notice of these theories if we want to be able to apply the underlying principles to the multiprocessing cases.