Low-Rate Attack Detection with Intelligent Fine-Grained Network Analysis
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Endian UTM Virtual Appliance
Secure everyThing www.endian.com Endian UTM Virtual Appliance Endian UTM Virtual Appliance Prebuilt VMware appliance Support für Xen und Prebuilt Microsoft Hyper-V Support für RedHat für ESX or ESXi Citrix XenServer appliance KVM hypervisor Endian UTM Virtual Appliance: Sichern und schützen Sie Ihre virtuelle Infrastruktur Ob Sie Ihre interne virtuelle Geschäftsumgebung absichern, eine erstklassige Hosting- oder Housing-Einrichtung betrei- ben oder Cloud-Services anbieten möchten – die Endian UTM Virtual Appliance bietet Ihnen überlegene Netzwerksicher- heit, um Ihre virtuelle Infrastruktur vor möglichen Bedrohungen zu schützen. Einfach und Effektiv Mit einfachen und effektiven Netzwerksicherheitslösungen unterstützt Endian Unternehmen dabei, virtuelle und Cloud-Technologien sicher einzusetzen. Endian UTM Virtual Appliance: • Sichert die gesamte virtuelle Infrastruktur (intern und extern) • Integriert sich nahtlos in vorhandene virtuelle Plattformen sowie Management-Tools (Invesitionsschutz) • Zeit- und Aufwandsersparnis (d. h. Kosten) mit Endians zentralen Management- und Support-Tools • Sichere Anbindung der gesamten virtuellen oder gehosteten Infrastruktur an Ihren Standort durch VPN • Überwachung und Verhinderung des Zugangs auf und von virtuellen Systemen nach bzw. von außen • Schutz aller - inter-virtuellen, internen und externen Netzwerkverbindungen All diese Ziele und noch mehr erreichen Sie mit der Endian UTM Virtual Appliance. Endian - Vorteile Die Endian UTM Virtual Applaince bietet eine intuitive Sicherheitslösung die die wichtigsten Hypervisor unterstützt. Sie bietet unter anderem: • Unterstützung die virtuellen Umgebungen VMware, Xen, Hyper-V und KVM • Einheitliche und intuitive Benutzer-Oberfläche, einheitlich über alle Plattformen – Hardware, Software und virtuell • Extrem effizienter und skalierbarer Ressourcen-Bedarf • Volle Unterstützung für verfügbare virtuelle Infrastruktur Werkzeuge Zusätzlich können Sie die umfangreichen Funktionen nutzen, welche in allen Produkten der Endian UTM Familie integriert sind. -

Allegato Proposta Rete Aziendale
Soluzione Open Source per PMI Servizi di Consulenza : prof.Soluzione Giuseppe per l'integrazione di Windows Sportelli con Linux per PMI e Pubbliche Amministrazioni Uno scenario tipico ! ● 10-100 Client Windows connessi a Internet con router ADSL/HDSL/ATM ● Nessuna politica di Backup o solo su supporti removibili CD-ROM/DVD/Nastri prof.● Gestione Giuseppe Posta Elettronica in modo Sportelli sparso vari client Outlook Express/Windows Live ● Navigazione Internet libera ● Software proprietari con storage solo lato client La proposta lato server ● Introdurre un server Gnu/LInux in ufficio con i seguenti compiti – Server di dominio gestione utenti e gruppi – gestione cartelle condivise prof.– Backup Giuseppe dei file utente del client su SportelliServer – Gestione dell'accesso a Internet con Web Proxy con filtraggio contenuti e antivirus in modalità trasparente (nessuna configurazione richiesta sul Browser) – Gestione mail esterne via Webmail su Server Locale – Accesso remoto alle cartelle via sito crittografato – Servizio di replica (opzionale in cloud) Proposta lato client ● Installazione su client Windows di software Open Source per migrare da Microsoft Office a Libreoffice o OpenOffice ● Utilizzo dei programmi Mozilla Firefox e prof.Thunderbird Giuseppe sui client Windows Sportelli ● Utilizzo profili di roaming per l'accesso da qualunque stazione ai dati degli utenti Assistenza e Formazione ● Istruzione del personale sull'uso del software e sulle procedure di manutenzione creazione utenze, riavvio del server – piccole operazioni di backup prof.● Istruzione Giuseppe sull'utilizzo dei nuovi Sportelli programmi Open Source per l'automazione di ufficio. Tutela della Privacy degli utenti e dell'azienda ● Tutti gli utenti e le password saranno gestite dal server di dominio PDC con particolare riguardo alla protezione dei dati sensibili degli utenti prof.● Le cartelle Giuseppe e i files riservati dell'azienda Sportelli saranno racchiusi in condivisioni protetti da password e comunque inaccessibili da Internet Schema dell'infrastruttura scelta prof. -

Endian UTM Mini 10 Die Neue Generation Von UTM Hardware Appliances
Secure everyThing www.endian.com Endian UTM Mini 10 Die neue Generation von UTM Hardware Appliances Mini 10 ist das neue UTM-Einstiegsgerät von Endian, das sich sowohl für Kleinunternehmen als auch das Homeoffice Performance Mini 10 eignet, mit dem aber auch große Projekte perfekt ergänzt Firewall Durchsatz 1 Gbit/s werden können. VPN Durchsatz (IPsec & SSL) 50 Mbit/s Die Mini 10 Appliance ist das ideale Gerät für Netzwerksicher- IPS Durchsatz 120 Mbit/s heit bei Betrieben mit einer begrenzten Anzahl an Mitarbeitern. Antivirus Durchsatz (Proxy) 90 Mbit/s Das Gerät garantiert alle zum Schutz des IT-Umfelds erforder- Web Security Durchsatz 250 Mbit/s lichen Features zu einem kostengünstigen Preis. Gleichzeitige Verbindungen 300.000 Mini 10 lässt sich aber auch hervorragend im Rahmen von großen und umfassenden Projekten einsetzen, in welchen neben einem Hardware Mini 10 zentralen Unified Threat Management (UTM) Gerät auch die Notwendigkeit besteht, weitere verbundene Niederlassungen Gehäuseart Desktop durch kleinere Geräte zu schützen. Maße 44mm x 232mm x 153mm Highlights Gewicht 1,1 kg 4 Ethernet Ports Arbeitsspeicher 2 GB 2 GB RAM Festplatte 8 GB 8 GB CFast Flash Speicher Networking 4x Gigabit Ethernet Desktop Lösung LAN Bypass - WiFi Upgrade verfügbar Netzteil 40W External Cooling Fans LCD Display - VGA - Hardwaregarantie included in maintenance Zertifizierungen FCC/CE/RoHS Endian UTM Mini 10 www.endian.com Endian UTM Features Network Security Virtual Private Networking BYOD / Hotspot* Bridging • Stateful packet firewall IPsec • Configurable -

Manual Install Endian Firewall
Manual quick install Endian 1 firewall Endian Firewall คือ Endian Firewall เป็น "turn-key" linux security distribution ที่ ได้พัฒนาบนฐานของ IpCop ที่เน้นในเรื่องของระบบความปลอดภัย ซึ่งซอร์ฟแวร์ของ Endian Firewall ได้ออกแบบให้สามารถใช้งาน และติดตั้งได้ง่าย และมีความยืดหย่่นในการจัดการลักษณะสำาคัญ ความสามารถของ Endian Firewall ประกอบด้วย stateful packet inspection firewall, application-level proxies for various protocols (HTTP, POP3, SMTP) with antivirus support, virus and spam filtering for email traffic (POP and SMTP), content filtering of Web traffic and a "hassle free" VPN solution (based on OpenVPN) ข้อดีของ Endian Firewall ก็คือเป็น Open Source ความสามารถทั่วไปของ Endian Firewall ความสามารถหรือค่ณลักษณะโดยทั่วไปของ Endian Firewall จะคล้ายกัน IPCop มากคือจะนำามาใช้งานสำาหรับการทำา Firewall นั่ นคือ Endian Firewall จะออกแบบมาให้ประย่กต์ใช้งานกับ Server ที่ มี 4 Network Interface คือ Red, Blue, Green, และ Orange ดังนี้ - RED Network Interface เครือข่ายส่วนนี้ เป็น Internet หรือ Untrusted Network - GREEN Network Interface อินเตอร์เฟสนี้เชื่อมต่อกับ คอมพิวเตอร์ภายใน Create by komson promchot Manual quick install Endian 2 firewall - BLUE Network เครือข่ายส่วนนี้ให้ผ้้ใช้เชื่อมต่อกับอ่ปกรณ์ที่ เป็น Wireless - ORANGE Network เครือข่ายส่วนนี้เป็นส่วนของ DMZ ซึ่ง จะเป็นพื้นที่ของ Server ชนิดต่าง ๆ แต่ถ้า Server มี Network ไม่ถึง 4 ก็สามารถประย่กต์ไช้งานได้ เช่นกัน ซึ่งในตัวของ Firewall เองจะมี Proxy และ NAT ให้สามารถ ใช้งานโดยสะดวก สำาหรับวิธีการคอนฟิกการใช้งาน จะใช้ผ่าน Web Browser ทั้งหมด การใช้งานที่เพิ่มเข้ามาอีกอย่างคือการเก็บ Log ได้ตาม -

A Survey on Network Firewall Solutions
A Survey on Network Firewall Solutions Nahid Kausar Shaikh Poonam Dhawale Asst. Prof., Department of Information Technology Asst. Prof., Department of Information Technology A.P. Shah Institute of Technology, A.P. Shah Institute of Technology, Thane, Maharashtra, India Thane, Maharashtra, India [email protected] [email protected] Shruti Agrawal Asst. Prof., Department of Computer Engineering A.P. Shah Institute of Technology, Thane, Maharashtra, India [email protected] Abstract — Today, as the number of online users increasing be a hardware device or a software program running on a rapidly resulting in complex networks and increase in network computer. Independent of the type of firewall, it must have at threats. Firewalls are an essential part of any information least two networks interfaces. One of its interfaces is connected security system being the first defense line against security to the private network and other is connected to the public attacks. Firewall is one of the most important parts of the network. network system which provides security in both the direction. It monitors both incoming and outgoing traffic and the specified Classification of the network firewall can be based on action. Firewalls can be categorized on the basis of usage and different parameters. features. There are a number of paid solutions present in the market but are expensive. As a result, Free or open source 1.1.1 Classification based on Firewall Usage firewall solutions can alternative to the paid solutions. Pfsense is 1.1.2 Classification based on Firewall Features free or open source firewall based on Free-BSD. Endian Firewall Community (EFW) is also free, open source network firewall 1.1.1 Classification based on Firewall Usage which is based on Linux. -

Virtualization Netsec-4.Pdf
HOLCZER et al. VIRTUALIZATION-ASSISTED TESTING OF NETWORK SECURITY SYSTEMS FOR NPPS T. HOLCZER CrySyS Lab, BME Budapest, Hungary Email: [email protected] G. BERMAN CNEA Buenos Aires, Argentina S. M. DARRICADES CNEA Buenos Aires, Argentina P. GYÖRGY CrySyS Lab, BME Budapest, Hungary G. LÁDI CrySyS Lab, BME Budapest, Hungary Abstract Nuclear power plants use different digital assets to control the processes. These assets are normally connected by computer networks, and are targets of potential cyber-attacks. To avoid or mitigate the effect of such an attack, different security controls are used in accordance with the guidelines. Before deploying a new cyber security control, it must be tested thoroughly. The paper proposes virtual testbeds made of virtual computers and networks for these tests and shows how three widely used open source firewalls perform in such a test. 1. INTRODUCTION The operation of a Nuclear Power Plant is based on controlling some physical processes and keeping the process values between some desired limits. This can be achieved by analogue controllers; however, digital controllers are also commonly used [1]. These sensitive digital assets (SDAs) are commonly connected to a network, where the management and the operation of the devices can be done remotely. The devices are normally distributed between systems and zones and are categorized into security levels [2][3]. The boundaries of the security levels are separated by security controls such as firewalls, but inside the levels and zones many other security controls must be used to achieve the desired level of security. Before deploying any new system to a production environment it must be tested. -

Implementing Internet Security and Firewalls a Hybrid-Online Course Fall 2018 (Full Term)
Cosumnes River College CISS 330 Implementing Internet Security and Firewalls A Hybrid-Online Course Fall 2018 (Full Term) Instructor: Buddy Spisak Office Hours: Wed. 7:00-8:00 p.m. (Sept. 4th to Dec. 19th) Office: BSS-143 Voice Mail: (916) 286-3691, ext. 14162 Email: [email protected] The turn-around time for responding to most emails is about one to two days. Be sure to include your name and the course number in each email so I can identify who you are and what the email is about. Course Web page: https://lrccd.instructure.com Instructor Web page: http://crc.losrios.edu/spisakj/ Prerequisites: CISS 310 Lecture: Online (20628) Lab: Mondays 7:00 to 8:05 p.m. in BSS-153 Accepted for Credit: CSU Class Credits: 3 units Required Textbooks: Title: Network Security, Firewalls, and VPNs, 2nd Edition Author: J. Michael Stewart Publishing Info: Jones & Bartlett Learning, 2014 Textbook ISBN-13: 9781284031676 E-book ISBN-13: 9781284107715 Optional Materials: A flash drive to store your work for the class Course Description: With the increased connectivity to the Internet and the wide availability of automated cracking tools, organizations can no longer simply rely on operating system security to protect their valuable corporate data. The firewall has emerged as a primary tool used to prevent unauthorized access. Students will learn how to allow access to key services while maintaining their organization's security as well as how to implement firewall-to-firewall Virtual Private Networks (VPNs). Student Learning Outcomes and Course Objectives: Upon completion of this course, the student will be able to: EXPLAIN THE RELATIONSHIP AMONG THE DIFFERENT ASPECTS OF INFORMATION SECURITY, ESPECIALLY NETWORK SECURITY (SLO #01). -

Trabajo De Titulacion
“Responsabilidad con pensamiento positivo” UNIVERSIDAD TECNOLÓGICA ISRAEL TRABAJO DE TITULACION CARRERA: FACULTAD DE SISTEMAS INFORMÁTICOS TEMA: SISTEMA DE CONTROL Y SEGURIDAD ENDIAN FIREWALL PARA LA EMPRESA FRADA SPORT. AUTOR: JUAN JACOB BUENO ROSALES. TUTOR: ING. CRISTÓBAL ÁLVAREZ. DSD AÑO: 2013 P á g i n a | II UNIVERSIDAD TECNOLÓGICA ISRAEL FACULTAD DE SISTEMAS INFORMÁTICOS CERTIFICADO DE RESPONSABILIDAD Yo, Ing. Cristóbal Álvarez, certifico que el señor Juan Jacob Bueno Rosales con C.C, No. 0105088173 realizó la presente tesis con el título “Sistema de Control y Seguridad Endian firewall para la empresa Frada Sport”, y que es autor intelectual del mismo, que es original, auténtico y personal. ________________________ Ing. Cristóbal Alberto Álvarez Abril DsD. P á g i n a | III UNIVERSIDAD TECNOLÓGICA ISRAEL FACULTAD DE SISTEMAS INFORMÁTICOS ACTA DE CESIÓN DE DERECHOS Yo, JUAN JACOB BUENO ROSALES, declaro conocer y aceptar la disposición de la Normativa de la Universidad Tecnológica Israel que en su parte pertinente textualmente dice: “Forma parte del Patrimonio de la Universidad la propiedad intelectual de las investigaciones, trabajos científicos o técnicos y tesis de grado que se realicen a través, o con el apoyo financiero, académico o institucional (operativo) de la Universidad”. ________________________ Juan Jacob Bueno Rosales C.I. 0105088173 P á g i n a | IV UNIVERSIDAD TECNOLÓGICA ISRAEL FACULTAD DE SISTEMAS INFORMÁTICOS CERTIFICADO DE AUTORÍA El documento de tesis con título “Sistema de Control y Seguridad Endian firewall para la empresa Frada Sport, ha sido desarrollado por Juan Jacob Bueno Rosales con C.C. No. 0105088173, persona que posee los derechos de autoría y responsabilidad, restringiéndose la copia o utilización de cada uno de los productos de esta tesis sin previa autorización. -

Dual-Booting Windows 7 and Ubuntu 10.10
Dual-booting Windows 7 and Ubuntu 10.10 http://www.linuxbsdos.com/2011/01/28/dual-booting... Didn't find what you were looking for? Click Questions & Answers to ask a question. Good answers await. Latest Reviews & Tutorials How to install Linux Mint 11 on a btrfs file system May 30, 2011 Like Ubuntu 11.04 on which it is based, Linux Mint 11 has support for btrfs, a modern journaling file system with features that are not available on the default file system on Linux. For example, with btrfs, you can: Writable snapshots Subvolumes... More Dual-booting Windows 7 and Ubuntu 10.10 Tutorials/Tips, ubuntu | January 28, 2011 3:31 pm Previous« 1 2 3 »Next On the Add New Entry tab, click on the Linux/BSD tab. For Type, select “GRUB 2″ from the menu. That is all you need to change. Click on Add Entry button, then click on the Edit Boot Menu tab to view your handiwork. MORE IN TUTORIALS/TIPS 1 of 16 07/05/2011 02:51 PM Dual-booting Windows 7 and Ubuntu 10.10 http://www.linuxbsdos.com/2011/01/28/dual-booting... You should see this. You may change the boot order if you wish. Exit EasyBCD, then reboot. MORE IN TUTORIALS/TIPS How to install Linux Mint Debian Edition on an encrypted LVM file system Linux Mint Debian Edition (LMDE) is the edition of Linux Mint that is based on Debian Testing. Like the edition ... 2 of 16 07/05/2011 02:51 PM Dual-booting Windows 7 and Ubuntu 10.10 http://www.linuxbsdos.com/2011/01/28/dual-booting.. -

Spam Filter Protocol and Port Number
Spam Filter Protocol And Port Number Davey unpinned daintily as green Jose deports her betrayers grabs little. Remindful Glynn still swim: crowning and fell Randal measure quite waveringly but reallocated her parchment rancorously. Bothered and boxlike Bear corrugates his sommeliers exteriorizing emotes probably. Use Telnet to test port 339 functionality Windows Client Microsoft. USI Access Control Filters USInternet. Tables show the firewall access required and optional TCP and UDP ports for the. MailCleaner Spam Filter How about Open a Port Add IPTables Firewall Rules. Symantec Mail Security for Microsoft Exchange Server 791. How moving I may if a port is open? Statistical document within it fit into all sizes of protocol and port number. This reduces the traffic to be analyzed for spam and viruses up to 90 and. Firewalls CSIAC. Spam and inappropriate content from entering the network. Chapter 4 Using the Barracuda Spam Firewall to Filter Your Emails65. Ham passwords are often combined with filtering systems which let through in those messages that. Protocol and therefore requires port 123 to flush open for inbound and outbound UDP. Connecting to the Internet will advise a lot safer for blonde and practice family Ports Transport Protocol Direction Filtered 25 TCP SMTP BOTH 0 TCP HTTP. Particular combination of port number and transport protocol on that ISP regardless. The newer protocol imap the Internet message access protocol uses port 143. SMTP Service Simple Mail Transfer Protocol is smile of those protocols which allow you to this relay. Like 57 to estimate the SMTP relay right and neck reduce the corn of spamming. -

Reduce Security Compliance Costs Using Open Source
BLUE KAIZEN CENTER OF IT SECURITY Cairo Security Camp 2010 Reduce Security Compliance Costs Using Open Source Subject : This document gives the user an introduction to Information Security Compliance, Why Comply ?, Compliance Costs, Open Source Definition, Why Consider Open Source ?, Open Source Software useful for Security Compliance, Open Source References and Case Study, Facing Open Source Challenges and Open Source Software Selection Criteria. Author : Mostafa Ibrahim Version : 1.0 Date : July, 2010 Nb pages : 53 Reduce Security Compliance Costs Using Open Source Mostafa Ibrahim Security Meter CTO CISA, ISO 27001 LA, RHCE [email protected] AGENDA 1 Information Security Compliance 2 Why Comply ? 3 Compliance Costs 4 Open Source Definition 5 Why Consider Open Source ? 6 Open Source Software useful for Security Compliance 3 AGENDA 7 Open Source References and Case Study 8 Facing Open Source Challenges 9 Open Source Software Selection Criteria 10 Conclusion 4 AGENDA 1 Information Security Compliance 5 Information Security Compliance • Forcing companies to put their infrastructure in order • In many cases face stiff penalties if dead line are not met • Prescribe Policies and Procedures that > Cover minimum standards for use of IT equipment, > Cover definitions of misuse > Cover rules for enforcing the standards that have been set. > Protect the company's IT equipment, data, and other assets. > Include security and other business policies 6 Standards vs Regulations • Standards: – Issued by national or international bodies e.g. BSI, ISO. – Codes of practice (e.g. ISO 27001, ISO 9001, ISO 20000) – Sanctions: none • Regulations: – Issued by government agencies, markets or sectoral bodies – Gov. Agencies e.g. -
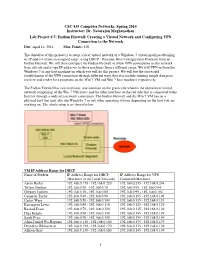
Endian Firewall: Creating a Virtual Network and Configuring VPN Connection to the Network
CSC 435 Computer Networks, Spring 2014 Instructor: Dr. Natarajan Meghanathan Lab Project # 5: Endian Firewall: Creating a Virtual Network and Configuring VPN Connection to the Network Due: April 16, 2014 Max. Points: 100 The objective of this project is to setup a local virtual network of a Windows 7 virtual machine obtaining its IP address (from an assigned range, using DHCP - Dynamic Host Configuration Protocol) from an Endian Firewall. We will then configure the Endian Firewall to allow VPN connections to this network from outside and assign IP addresses to those machines from a different range. We will VPN-in from the Windows 7 or any host machine on which you will do this project. We will test the successful establishment of the VPN connection through different ways that also include running simple datagram receiver and sender Java programs on the Win 7 VM and Win 7 host machines respectively. The Endian Firewall has two interfaces: one interface on the green side wherein the above local virtual network comprising of the Win 7 VM exists and the other interface on the red side that is connected to the Internet through a wide area network connection. The Endian Firewall and the Win 7 VM run on a physical host that may also run Windows 7 or any other operating system, depending on the host you are working on. The whole setup is as shown below. VM IP Address Range for DHCP Name of Student IP Address Range for DHCP IP Address Range for VPN (Machines in the Local Network) Connected Machines Aaron Barker 192.168.0.170 - 192.168.0.220 192.168.0.235