Shadow Sensor Configuration Policy
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Implementing Cisco Cyber Security Operations
2019 CLUS Implementing Cisco Cyber Security Operations Paul Ostrowski / Patrick Lao / James Risler Cisco Security Content Development Engineers LTRCRT-2222 2019 CLUS Cisco Webex Teams Questions? Use Cisco Webex Teams to chat with the speaker after the session How 1 Find this session in the Cisco Live Mobile App 2 Click “Join the Discussion” 3 Install Webex Teams or go directly to the team space 4 Enter messages/questions in the team space Webex Teams will be moderated cs.co/ciscolivebot#LTRCRT-2222 by the speaker until June 16, 2019. 2019 CLUS © 2019 Cisco and/or its affiliates. All rights reserved. Cisco Public 3 Agenda • Goals and Objectives • Prerequisite Knowledge & Skills (PKS) • Introduction to Security Onion • SECOPS Labs and Topologies • Access SECFND / SECOPS eLearning Lab Training Environment • Lab Evaluation • Cisco Cybersecurity Certification and Education Offerings 2019 CLUS LTRCRT-2222 © 2019 Cisco and/or its affiliates. All rights reserved. Cisco Public 4 Goals and Objectives: • Today's organizations are challenged with rapidly detecting cybersecurity breaches in order to effectively respond to security incidents. Cybersecurity provides the critical foundation organizations require to protect themselves, enable trust, move faster, add greater value and grow. • Teams of cybersecurity analysts within Security Operations Centers (SOC) keep a vigilant eye on network security monitoring systems designed to protect their organizations by detecting and responding to cybersecurity threats. • The goal of Cisco’s CCNA Cyber OPS (SECFND / SECOPS) courses is to teach the fundamental skills required to begin a career working as an associate/entry-level cybersecurity analyst within a threat centric security operations center. • This session will provide the student with an understanding of Security Onion as an open source network security monitoring tool (NSM). -

Securing Infrastructure-As-A-Service Public Clouds Using Security Onion
Securing Infrastructure-as-a-Service Public Clouds Using Security Onion MIKAIL, Abdullahi and PRANGGONO, Bernardi <http://orcid.org/0000-0002- 2992-697X> Available from Sheffield Hallam University Research Archive (SHURA) at: http://shura.shu.ac.uk/23927/ This document is the author deposited version. You are advised to consult the publisher's version if you wish to cite from it. Published version MIKAIL, Abdullahi and PRANGGONO, Bernardi (2019). Securing Infrastructure-as-a- Service Public Clouds Using Security Onion. Applied System Innovation, 2 (1). Copyright and re-use policy See http://shura.shu.ac.uk/information.html Sheffield Hallam University Research Archive http://shura.shu.ac.uk Article Securing Infrastructure-as-a-Service Public Clouds Using Security Onion Abdullahi Mikail and Bernardi Pranggono * Department of Engineering and Mathematics, Sheffield Hallam University, Howard Street, Sheffield S1 1WB, UK; [email protected] * Correspondence: [email protected] Received: 17 December 2018; Accepted: 23 January 2019; Published: 30 January 2019 Abstract: The shift to Cloud computing has brought with it its specific security challenges concerning the loss of control, trust and multi-tenancy especially in Infrastructure-as-a-Service (IaaS) Cloud model. This article focuses on the design and development of an intrusion detection system (IDS) that can handle security challenges in IaaS Cloud model using an open source IDS. We have implemented a proof-of-concept prototype on the most deployed hypervisor—VMware ESXi—and performed various real-world cyber-attacks, such as port scanning and denial of service (DoS) attacks to validate the practicality and effectiveness of our proposed IDS architecture. -

Evaluating the Availability of Forensic Evidence from Three Idss: Tool Ability
Evaluating the Availability of Forensic Evidence from Three IDSs: Tool Ability EMAD ABDULLAH ALSAIARI A thesis submitted to the Faculty of Design and Creative Technologies Auckland University of Technology in partial fulfilment of the requirements for the degree of Masters of Forensic Information Technology School of Engineering, Computer and Mathematical Sciences Auckland, New Zealand 2016 i Declaration I hereby declare that this submission is my own work and that, to the best of my knowledge and belief, it contains no material previously published or written by another person nor material which to a substantial extent has been accepted for the qualification of any other degree or diploma of a University or other institution of higher learning, except where due acknowledgement is made in the acknowledgements. Emad Abdullah Alsaiari ii Acknowledgement At the beginning and foremost, the researcher would like to thank almighty Allah. Additionally, I would like to thank everyone who helped me to conduct this thesis starting from my family, supervisor, all relatives and friends. I would also like to express my thorough appreciation to all the members of Saudi Culture Mission for facilitating the process of studying in a foreign country. I would also like to express my thorough appreciation to all the staff of Saudi Culture Mission for facilitating the process of studying in Auckland University of Technology. Especially, the pervious head principal of the Saudi Culture Mission Dr. Satam Al- Otaibi for all his motivation, advice and support to students from Saudi in New Zealand as well as Saudi Arabia Cultural Attaché Dr. Saud Theyab the head principal of the Saudi Culture Mission. -

Part Iii Network Security Monitoring Processes
Bejtlich_book.fm Page 345 Thursday, June 17, 2004 8:40 AM PART III NETWORK SECURITY MONITORING PROCESSES 345 Bejtlich_book.fm Page 346 Thursday, June 17, 2004 8:40 AM Bejtlich_book.fm Page 347 Thursday, June 17, 2004 8:40 AM Best11 Practices In Parts I and II we explored NSM theory and some tools for conducting NSM. Part III is intended for people who manage NSM operations. It presents best practices for assess- ment, protection, detection, and response, as far as NSM is concerned. While elements of NSM best practices appear throughout the book, this chapter focuses exclusively on the mind-set needed to conduct NSM operations. Chapter 12 brings these principles to life in several case studies. Chapter 1 introduced the security process in general. In this chapter, I explain the NSM-specific aspects of each security process step (see Figure 11.1). First, I describe the benefits of developing a well-defined security policy during assessment. Then I explain protection with respect to access control, traffic scrubbing, and proxies. Next, detection is expanded to include collection, identification, validation, and escalation of suspicious events. I elaborate on response within the context of short-term incident containment and emergency NSM. Finally, I conclude by returning to the assessment phase by high- lighting analyst feedback as a component of planning for the next cycle. ASSESSMENT Assessment involves taking steps to ensure the probability of successfully defending an enterprise. Within the NSM model, assessment means implementing products, people, and processes most conducive to accurately identifying and mitigating intrusions. Part II illustrated NSM tools, and Part IV will offer suggestions for training people. -

Prototype Open-Source Software Stack for the Reduction of False
CYBER 2018 : The Third International Conference on Cyber-Technologies and Cyber-Systems Prototype Open-Source Software Stack for the Reduction of False Positives and Negatives in the Detection of Cyber Indicators of Compromise and Attack Hybridized Log Analysis Correlation Engine and Container-Orchestration System Supplemented by Ensemble Method Voting Algorithms for Enhanced Event Correlation Steve Chan Decision Engineering Analysis Laboratory San Diego, California U.S.A. email: [email protected] Abstract—A prototypical solution stack (Solution Stack #1) black boxed commercial offering itself. Accordingly, with chosen Open-Source Software (OSS) components for an MSSPs are endeavoring to put forth their own offerings experiment was enhanced by hybridized OSS amalgams (e.g., (also for market differentiation), in a white box fashion; for Suricata and Sagan; Kubernetes, Nomad, Cloudify and Helios; the purposes of adhering to Joyce’s recommendation, the MineMeld and Hector) and supplemented by select modified white box approach can be, in some cases, more effective algorithms (e.g., modified N-Input Voting Algorithm [NIVA] modules and a modified Fault Tolerant Averaging Algorithm than the black box approach, but it is a much more difficult [FTAA] module) leveraged by ensemble method machine pathway in terms of the sophistication needed to understand learning. The preliminary results of the prototype solution and appropriately orchestrate the various involved stack (Stack #2) indicate a reduction, with regards to cyber subsystems. By way of example, a Verizon Data Breach Indicators of Compromise (IOC) and indicators of attack Report had articulated that those with robust log analysis (IOA), of false positives by approximately 15% and false and correlation were least likely to be a cyber victim; yet, negatives by approximately 47%. -

Intrusion Detection System and Intrusion Prevention System with Snort Provided by Security Onion
Bezborodov Sergey Intrusion Detection System and Intrusion Prevention System with Snort provided by Security Onion. Bachelor’s Thesis Information Technology May 2016 DESCRIPTION Date of the bachelor's thesis 06.05.2016 Author(s) Degree programme and option Bezborodov Sergey Information Technology Name of the bachelor's thesis Intrusion Detection Systems and Intrusion Prevention System with Snort provided by Security Onion. Abstract In this thesis I wanted to get familiar with Snort IDS/IPS. I used the Security Onion distribution with a lot of security tools, but I concentrated on Snort. Also I needed to evaluate Security Onion environment and check what features it provides for processing with Snort. During the work I needed to figure out the pros and cons of using Security Onion with Snort as a security system for network. I compared it with alternatives and briefly describe it. As result I installed Security Onion, work with the environment, configured different features, created and modified rules and so on. I think this thesis will be helpful for people who want to use IDS/IPS for their network, it should help them to choose IDS/IPS vendor, make Security Onion and Snort installation, make comparison with another one and just get familiar with the network security tools. Also, this thesis can be a part of big research of network security tools, because now is impossible to find such detailed guides and literatures about any IDS/IPS tools. It is a good idea to combine many researches about it and make a good library. This thesis can be used for further development of Snort and Security Onion as it only on the development phase now, it will provide base for new researching with new versions. -

Analyzing Offensive and Defensive Networking Tools in a Laboratory Environment
NIKO HEIKURA ANALYZING OFFENSIVE AND DEFENSIVE NETWORKING TOOLS IN A LABORATORY ENVIRONMENT Master of Science thesis Examiners: prof. Jarmo Harju and M.Sc. Markku Vajaranta Examiners and topic approved by the Faculty Council of the Faculty of Computing and Electrical Engineer- ing on 8th October 2014 i ABSTRACT NIKO HEIKURA : Analyzing Offensive and Defensive Networking Tools in a La- boratory Environment Tampere University of Technology Master of Science Thesis, 93 pages March 2015 Master’s Degree Programme in Signal Processing and Communications Engi- neering Major: Communications Networks and Protocols Examiners: Professor Jarmo Harju and M.Sc. Markku Vajaranta Keywords: denial of service, network security, network security monitoring, ex- ploits, vulnerabilities The safest way of conducting network security testing is to do it in a closed laboratory environment that is isolated from the production network, and whose network configu- ration can be easily modified according to needs. Such an environment was built to the Department of Pervasive Computing in the fall of 2014 as part of TUTCyberLabs. In addition to the networking hardware, computers and servers, two purchases were made: Ruge, a traffic generator, and Clarified Analyzer, a network security monitor. Open source alternatives were researched for comparison and the chosen tools were Ostinato and Security Onion respectively. A hacking lab exercise was created for Computer Network and Security course employing various tools found in Kali Linux that was in- stalled on the computers. Different attack scenarios were designed for the traffic genera- tors and Kali Linux, and they were then monitored on the network security monitors. Finally a comparison was made between the monitoring applications. -

Logging and Monitoring at Home Who Am I
Defending the Homeland Logging and Monitoring at home Who am I @nullthreat Offensive Red Team for a major company I break stuff Started security @ CNDSP ADT for networks @ DOD Designed and Deployed NSM on DOD net Talking Points Perimeter Firewall Central Logging Host IDS Network IDS Basic Honeypots Deployment Strategies Disclaimer: The ideas and solutions presented are my opinion, feel free to disagree. OS'es I use all Linux and Macs at home I will not be talking about Windows at all, deal with it Won't matter once we are talking NIDS Firewalls on the Cheap As I see it there is only one good solution in this space PFSense http://www.pfsense.org ● Fork of MonoWall ● Robust Firewall based on PF(FreeBSD) ● Multiple VPN Support built-in ○ OpenVPN, IPSec, L2TP, PPTP ● Package based add-ons ○ pfBlocker(block netblocks), Snort, Squid ● Runs on almost anything, Full PC or Embedded Embedded Solutions ALIX 2D3/2D13 ~ 200$ @ store.netgate.com PFsense on Alix Setup Pauldotcom.com tech segement from episode 220 Google "alix pfsense pauldotcom" and you'll find the show notes Spark notes: Download IMG, Write to CF Card, Boot, Use Serial Terminal to do initial setup PFSense on Alix Setup Pro Tip: Don't put the box together until you flash the OS onto the card, You have to take the entire box apart to get the CF Card in and out. PFSense Demo Other Options Surplus Cisco/Juniper/Checkpoint Hardware Consumer Firewall Solutions http://en.wikipedia. org/wiki/List_of_router_or_firewall_distributions Firewalls Questions? Central Logging I do this on my servers and VPSs Could do on clients but....meh Usually the same box that hosts my NIDS stuff Lots of options syslogd Ol' reliable Been around since the dawn of freaking time originally part of sendmail circa 1980s UDP Only(in most cases) Easy-ish to configure but hard to really dial in syslogd Server: set -r flag in /etc/sysconfig/syslog ex. -
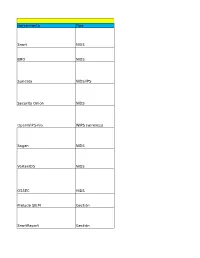
Herramienta Tipo Snort NIDS BRO NIDS Suricata NIDS/IPS Security Onion NIDS Openwips-NG WIPS (Wireless) Sagan NIDS Vortexids NIDS
Open source y freeware Herramienta Tipo Snort NIDS BRO NIDS Suricata NIDS/IPS Security Onion NIDS OpenWIPS-NG WIPS (wireless) Sagan NIDS VortexIDS NIDS OSSEC HIDS Prelude SIEM Gestión SnortReport Gestión OSSIM Gestión SGUIL Gestión SIDSC Gestión IRDM-HTN IRS OrBAC IRS Comerciales (ordenados por top sellings y cuadrante mágico de gartner) Herramienta Tipo Sourcefire Cisco NGIPS TippingPoint IPS IPS Check Point IPS IPS HP-UX HIDS McAfee Network Security Platform IPS RealSecure Server Sensor HIDS RealSecure Network Sensor NIDS ISA Server HIDS Cisco Secure Intrusion Detection System NIDS Dragon NIDS ArcSight SIEM platform Gestión GFI Events Mananger Gestión Cisco Security Information Event Gestión McAfee Enterprise Log Manager Gestión Management Gestión Open source y freeware URL https://www.snort.org/ https://www.bro.org/ http://suricata-ids.org/ http://securityonion.net http://openwips-ng.org/ http://sagan.quadrantsec.com/ https://github.com/jandre/vortex-ids http://www.ossec.net/ https://www.prelude-ids.org/ http://freecode.com/projects/snortreport http://trac.osgeo.org/ossim/ sguil.sourceforge.net/ http://sourceforge.net/projects/sidsc/ Cita:Mu, C., & Li, Y. (2010). An intrusion response decision-making model based on hierarchical task network planning. Expert systems with applications, 37(3), 2465-2472. http://orbac.org/ Comerciales (ordenados por top sellings y cuadrante mágico de gartner) URL http://www.sourcefire.com/ www8.hp.com/ https://www.checkpoint.com/ https://h20392.www2.hp.com/ http://www.mcafee.com/ ibm.com/services/us/iss -

Open Source Network Security Monitoring with Sguil
Open Source Network Security Monitoring With Sguil David J. Bianco Cybersecurity Analyst Jeferson Lab [email protected] Thomas Jefferson National Accelerator Facility Cyber Security Review, April 23-24, 2002, Operated by Jefferson Science Associates, LLC. for the U.S. Depart. Of Energy 1 Table of Contents • Intro to Network Security Monitoring (NSM) • NSM with Sguil • Sguil architecture • Working with Sguil • Sguil in action • Try it yourself! • Summary • More Information • Questions Thomas Jefferson National Accelerator Facility Cyber Security Review, April 23-24, 2002, Operated by Jefferson Science Associates, LLC. for the U.S. Depart. Of Energy 2 Network Monitoring • Most mid/large-sized organizations perform network monitoring • Intrusion Detection Systems (IDS) • Syslogs/Event Logs • NetFlow/SFlow • Other sources(?) • Lots of information but no coherence • Hard to correlate into usable intelligence • Difficult to reassemble the puzzle • Research & analysis takes lots of analyst time Thomas Jefferson National Accelerator Facility Cyber Security Review, April 23-24, 2002, Operated by Jefferson Science Associates, LLC. for the U.S. Depart. Of Energy 3 Network Security Monitoring The collection, analysis and escalation of indications and warnings to detect and respond to intrusions. Thomas Jefferson National Accelerator Facility Cyber Security Review, April 23-24, 2002, Operated by Jefferson Science Associates, LLC. for the U.S. Depart. Of Energy 4 NSM in a Nutshell • NSM is a methodology, not a product • An extension/evolution of traditional network monitoring • Integrates different sources into a single view • Easier to understand • Speeds the research process Thomas Jefferson National Accelerator Facility Cyber Security Review, April 23-24, 2002, Operated by Jefferson Science Associates, LLC. -
Logging and Monitoring to Detect Network Intrusions and Compliance Violations in the Environment
Interested in learning more about security? SANS Institute InfoSec Reading Room This paper is from the SANS Institute Reading Room site. Reposting is not permitted without express written permission. Logging and Monitoring to Detect Network Intrusions and Compliance Violations in the Environment Log Management and Intrusion Detection solutions have been evolving for years. Yet, it remains a challenge for organizations of all sizes to meet the operational, audit and security needs using these solutions. This paper presents a solution to bridge logging, log based intrusion detection and network based intrusion detection using well known free open source tools available on the Security Onion Linux Distribution. It walks through the logging, monitoring and alerting approach necessary for security, compliance and q... Copyright SANS Institute Author Retains Full Rights AD Logging and Monitoring to Detect Network Intrusions and Compliance Violations in the Environment . ts h g ri GIAC (GCIA) Gold Certification ll u f Author: Sunil Gupta, [email protected] s Advisor: Dr. Kees Leune in ta re r Accepted: July 4, 2012o th u , A te tu ti Abstract s n Log Management and Intrusion I Detection solutions have been evolving for years. Yet, it remains a challenge for organizationsS of all sizes to meet the operational, audit and security needs using these solutions. ThisN paper presents a solution to bridge logging, log based intrusion detection A and network Sbased intrusion detection using well known free open source tools available on the Security Onion Linux Distribution. It walks through the logging, monitoring and alerting 12 approach0 necessary for security, compliance and quality of service. -

Webové Rozhraní IDS Systému Snort Snort IDS Web Interface
VŠB – Technická univerzita Ostrava Fakulta elektrotechniky a informatiky Katedra informatiky Webové rozhraní IDS systému Snort Snort IDS Web Interface 2019 Dominik Raška Na tomto místˇebych rád podˇekoval hlavnˇeMgr. Ing. Michalu Krumniklovi, Ph.D. za jeho rady a pˇri- pomínky, které mi pomohly pˇritéto práci, a ještˇepom˚užou pˇripracích budoucích. Abstrakt Úˇcelem této práce je vytvoˇritnástavbu aplikace Snort umožˇnující pˇrehlednouanalýzu log˚uprostˇred- nictvím webového rozhraní, které bude schopné provozu i na routerech s relativnˇemalým výkonem. V úvodu práce je ˇctenáˇrseznámen s nejznámˇejšími systémy pro odhalení pr˚uniku, jejich funkcemi a konfigurací. Následuje porovnání již existujících rozhraní pro systém Snort a návrh vlastní imple- mentace webové rozhraní. Vlastní implementace je potom ˇrádnˇezdokumentovaná a otestovaná na více zaˇrízeních. Klíˇcová slova: IDS, Snort rozhraní, webové rozhraní, sít’ové zabezpeˇcení Abstract This thesis objective was to implement a Snort extension allowing for convenient analysis of Snort alerts through a web interface. At first, reader is being presented with the theory of intrusion detec- tion systems, how they work and what are some commonly used alternatives. After that, the existing Snort interfaces are being compared while proposing the vision for my own implementation. My application is then thorougly documented and deployed in a couple of testing enviroments. Key Words: IDS, Snort interface, web interface, network security Obsah Seznam použitých zkratek a symbol˚u 9 Seznam obrázk˚u 10 Seznam tabulek 11 Seznam výpis˚uzdrojového kódu 12 1 Úvod 13 2 Co je to intrusion detection system? 14 2.1 NIDS ................................................. 14 2.2 HIDS ................................................. 14 2.3 Intrusion prevention system . 15 2.4 IDS Snort . 15 2.5 IDS Suricata .